Table of Contents
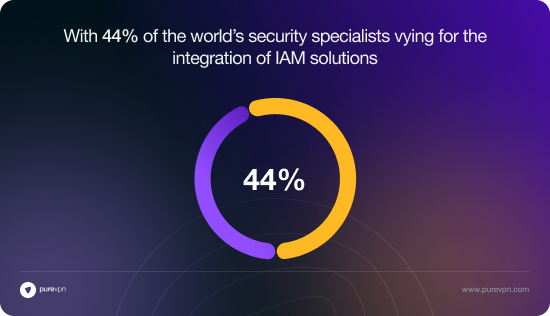
Identity and access management (IAM) enhances security for users accessing applications and data from their linked devices. Whether these devices are personal smartphones and tablets brought in by employees or newly deployed work laptops situated in unconventional settings, IAM enables businesses to strengthen their defense mechanisms against smarter cyberattacks. With 44% of the world’s security specialists vying for the integration of IAM solutions, here’s how they play a crucial role in ensuring each user possesses the appropriate access permission for secure and streamlined identity management.
What is Identity Access Management (IAM)?
It’s a system that ensures a unique, singular identity for every member of the organization with strong verification checks so these identities are not compromised.
How are identities commonly compromised?
Phishing Emails: Deceptive emails from trusted sources trick users into sharing credentials.
Weak Passwords: Easily guessable or common passwords enable unauthorized access.
Credential Theft: Malicious software captures login credentials on the user’s device.
Social Engineering: Attackers manipulate users through social interactions for sensitive information.
Brute Force Attacks: Systematic attempts of multiple password combinations, especially with weak passwords.
Man-in-the-Middle Attacks: Intercepting data in transit to capture login credentials.
Insider Threats: Users with insider access compromise identities by sharing credentials.
Security Misconfigurations: Users expose information or grant unintended access due to security misconfigurations.
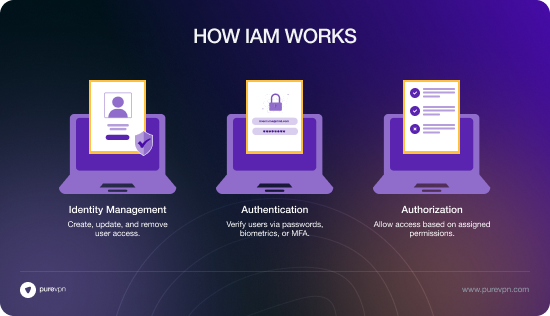
How does IAM work?
IAM operates by overseeing the identification, authentication, authorization, and auditing of users accessing a company’s systems and information. It serves to handle both internal and external user management.
Think of it as a smart keycard system in a company building.
Keycard Issuance: Smart keycards are issued to employees and they become users in a security system.
Role Assignment: In a smart keycard system, roles are assigned to employees based on their responsibilities.
Access Authorization: The smart keycards grants specific employees access to only specific rooms.
Role-Based Access Control (RBAC): Employees have access only to the areas relevant to their assigned roles. Entry to other rooms is restricted.
Continuous Monitoring: Regular monitoring of access permissions to ensure premium security.
Commonly Used Identity Providers
Popular IdPs enable you to provision a strong and unique identity for every member of your team.
- Okta
- Microsoft Azure Active Directory (Azure AD)
- Ping Identity
- OneLogin
- Google Cloud Identity
- AWS Identity and Access Management (IAM)
- Amazon Web Services (AWS)
- Auth0
- ForgeRock Identity Gateway
- IBM Security Verify
- Salesforce Identity
Core Capabilities of IAM
- A simpler and more consistent user login experience with Single Sign-on
- Multi-Factor Authentication to bolster security by requiring multiple forms of identification
- Privileged Access Management Centralized for limiting access to authorized users
- Efficient User Provisioning and Deprovisioning to streamline team onboarding and reduce security risks
- Audit Trail Reports provide a comprehensive record of user activities, ensuring transparency and compliance
How PureVPN for Teams Fits Into The Equation
- Seamless IDP Integration:
Begin with a secure login via our Identity Provider (IDP) integration, ensuring a centralized and authenticated entry point for users.
- Device Posture Check:
Prioritize security through Device Posture Check, where the health and compliance of devices are verified before granting access.
- Guarded Entry via Gateways:
Access the digital realm through advanced Gateways that permit only authorized and verified users, ensuring a secure pathway.
- Adaptive Team Management:
Navigate the digital landscape with ease through PureDome’s Team Management features, providing granular control over roles and permissions, tailoring access to specific team needs.
Bottom Line:
IAM is a structured set of rules, operational procedures, and utilities employed to oversee and facilitate the proper entry to an organization’s assets. Put simply, PureVPN for Team’s Identity and Access Management solution focuses on guaranteeing that only the right users can reach the right information at the right time, and for the right purposes.