Not all breaches happen with firewalls falling or servers being popped. Some happen in quieter ways through the integrations that businesses use every day to keep operations smooth. In August 2025, Zscaler confirmed that it had been impacted by exactly this type of attack.
The Zscaler data breach was not about its Zero Trust Exchange collapsing or its secure web gateways being bypassed. Instead, attackers exploited a third-party integration used for marketing and support. OAuth tokens tied to Salesloft’s Drift app were stolen, granting attackers legitimate access to Salesforce. That’s all it took to get inside.
On the surface, it looks like a limited breach. No Zscaler core infrastructure was compromised. But the details, exposed contact data, licensing information, and support case text, show why supply-chain and SaaS risks can be just as dangerous as traditional exploits. For customers, partners, and resellers, the breach is a reminder: the weakest link often lives in the shadows of trusted integrations.
- Incident: Attackers exploited stolen OAuth tokens from the Salesloft Drift integration to access Zscaler’s Salesforce instance (Aug 8–18, 2025).
- Scope: No Zscaler core products or infrastructure compromised; exposure limited to customer contact data, licensing info, and some support case text.
- Hidden Risk: Support tickets sometimes contained plain-text credentials or API keys, raising the chance of follow-on compromise.
- Google Workspace: Drift Email tokens were abused on Aug 9 to access a few integrated mailboxes. Workspace itself was not breached.
- Tactics: Attackers deleted Salesforce jobs post-exfiltration to cover tracks. Attribution points to UNC6395 (not ShinyHunters).
- Response: Salesforce revoked all Drift tokens (Aug 20) and later suspended Drift/Salesloft integrations. Zscaler notified customers and advised vigilance.
- Business Impact: Data exposed could fuel spear-phishing, impersonation, and compliance risks under GDPR/CCPA.
- Takeaways: Audit OAuth apps, rotate/revoke stale tokens, avoid storing secrets in tickets, and monitor SaaS logs for anomalies.
Timeline of the Zscaler Data Breach
Timeline of the Zscaler Data Breach
Compromised OAuth & refresh tokens (Drift → Salesforce)
Attackers used Drift-issued tokens to access Salesforce environments (including Zscaler), run queries, pull records, and often delete jobs to cover tracks.
Drift Email → Google Workspace
Drift Email tokens were used to access a small number of Google Workspace mailboxes. Workspace itself wasn’t compromised.
Revocation of Drift tokens
Salesforce and Salesloft revoked all active Drift tokens to contain exposure.
Integrations disabled / suspended
Salesforce disabled the Drift connection and later suspended all Salesloft integrations. Attribution was contested (ShinyHunters vs UNC6395).
Let’s break down what investigators and Zscaler disclosed about the sequence of events:
- Aug 8–18, 2025: Attackers used compromised OAuth and refresh tokens tied to Drift. These tokens granted access to Salesforce environments, including Zscaler’s. Attackers ran queries, pulled records, and in many cases deleted jobs afterwards to cover their tracks.
- Aug 9, 2025: In a parallel move, Drift Email tokens were used to access a small number of Google Workspace mailboxes. Only tenants that had explicitly integrated Drift Email were affected. Workspace itself wasn’t compromised.
- Aug 20, 2025: Salesforce and Salesloft revoked all active Drift tokens to contain exposure.
- Aug 28, 2025: Salesforce disabled the Drift connection entirely, and later suspended all Salesloft integrations pending investigation.
Attribution is muddy. A group known as ShinyHunters claimed responsibility, but Google’s Threat Intelligence Group linked the campaign to UNC6395. Their forensic evidence pointed to the same token replay and Salesforce-focused activity seen across multiple enterprises in August.
What Data Was Exposed?
Zscaler confirmed that the attackers accessed:
- Contact details: Names, business emails, job titles, phone numbers, location data.
- Commercial/licensing information: Details tied to customer entitlements and product usage.
- Support case text: The riskiest category. Some tickets contained plain-text credentials, API keys, and cloud tokens pasted in by customers.
This wasn’t a case of credit card numbers spilling onto forums. Instead, it’s about information that makes targeted attacks easier. With job titles and regions, spear-phishing campaigns get sharper. With licensing info, attackers can pose as account managers or service reps. And with any secrets buried in case text, the path to lateral compromise gets shorter.
Why OAuth Supply-Chain Attacks Are Growing?
The breach is a masterclass in why OAuth tokens are such a tempting target.
Unlike passwords, tokens don’t require re-authentication once issued. They bypass MFA prompts and logins entirely. As long as the token is valid, the system trusts it. Attackers love them for that reason: they’re silent, persistent, and often overlooked until it’s too late.
In this case, Drift was the Trojan horse. Companies trusted the integration, granted permissions, and left the tokens in place. When attackers compromised Drift, they inherited all that trust.
This isn’t unique to Zscaler. SaaS-to-SaaS compromises are rising because enterprises rarely audit connected apps. Tokens sit unused but valid. Permissions are granted broadly. Once stolen, they work until revoked.
Zscaler’s Response
Financial Impact Estimator
Estimate potential revenue exposure if customer data is phished or abused post-breach.
Conservative
1% targeted succeed × 20% revenue impactExpected
3% targeted succeed × 30% revenue impactSevere
8% targeted succeed × 40% revenue impactExposure is an estimate for planning—actual impact varies by token scopes, detection speed, and incident response.
Zscaler’s public statement emphasized a few critical points:
- Hackers compromised Salesforce instance.
- Core products and infrastructure were not touched.
- Compromised tokens were revoked once discovered.
- Customers were notified and advised to watch for phishing.
The company also worked directly with Salesforce as the platform vendor, aligning on containment measures like revoking Drift tokens and later disabling integrations altogether.
From a communication standpoint, Zscaler moved quickly. The transparency helped, but for security buyers, the takeaway isn’t just about Zscaler’s speed; it’s about whether their own SaaS monitoring would catch a similar attack inside their environments.
Lessons for Businesses
Token Lifecycle Visualizer
User authorizes → token issued → trusted access (no MFA) → token stolen → attacker uses token.
User authorizes app
- Enterprises often approve integrations broadly to “unblock” teams.
If you’re running Salesforce, Google Workspace, or any other SaaS with third-party integrations, here’s what this breach tells you:
- Stop putting secrets in tickets. Support case text is not a password vault. If you need to share keys, use secure transfer mechanisms. Assume tickets may be exposed in a breach.
- Audit your OAuth tokens. Know which connected apps have access to your systems. If you don’t use them, revoke them.
- Rotate aggressively. Don’t wait for a breach to refresh API keys and tokens. Build it into your routine.
- Harden your permissions. Use least-privilege scopes. Avoid “API Enabled” on profiles that don’t need it. Enforce login IP ranges.
- Prepare for phishing waves. Expect attackers to reference real case numbers or product names in lures. Train staff and add verification steps.
What the Breach Reveals About Zscaler’s Own Stack?
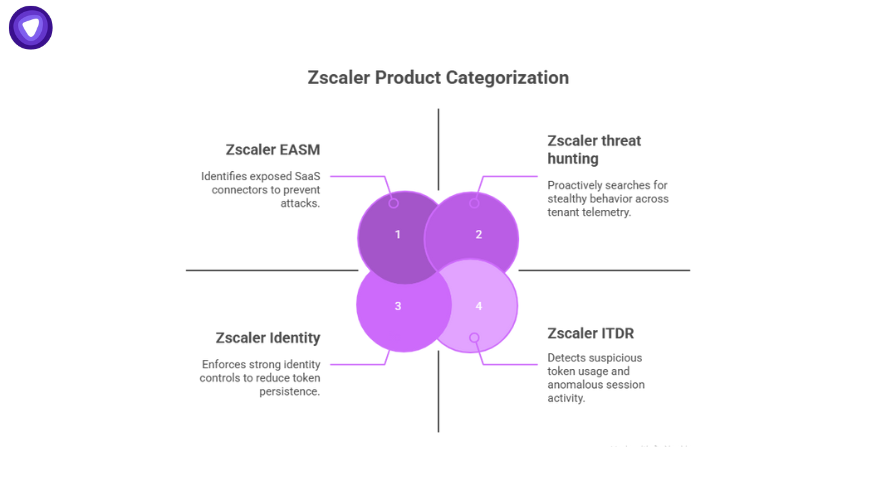
Ironically, Zscaler markets solutions that address some of these risks. The breach doesn’t invalidate their products, but it does highlight the importance of using them fully:
- Zscaler EASM (External Attack Surface Management): Helps identify exposed SaaS connectors, misconfigured apps, and shadow IT. A tool like this can catch risky integrations like Drift before they become attack paths.
- Zscaler breach predictor: Uses modeling to simulate exploit paths and highlight weak links in identity or SaaS access.
- Zscaler ITDR (Identity Threat Detection and Response): Detects suspicious token usage, anomalous session activity, and identity abuse consistent with what happened here.
- Zscaler threat hunting: Provides proactive searches across tenant telemetry to spot stealthy behavior like job deletions.
- Zscaler UVM automation: Answers the classic training question: Which of the following action does Zscaler UVM automate? → UVM automates vulnerability posture updates and remediation workflows, so gaps get closed quickly.
- Zscaler Risk360: To the question How does Zscaler Risk360 help organizations allocate their cybersecurity budget?—it quantifies financial loss exposure across risk vectors, letting CISOs prioritize budget by business impact.
- Zscaler Identity: Enforces strong identity controls and ties SaaS access back to verified users, reducing the persistence of stolen tokens.
The irony is clear: tools exist to prevent or detect these attacks, but supply-chain trust remains a blind spot.
Minute Details Many Reports Missed
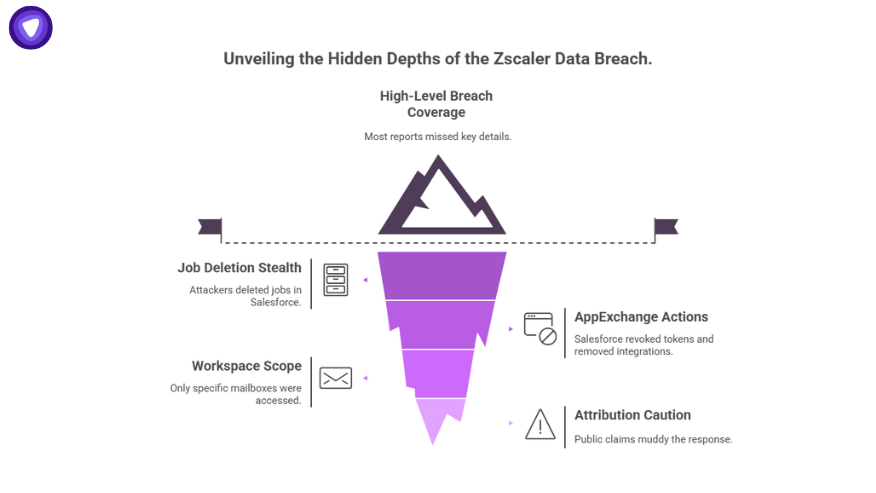
Most coverage of the Zscaler data breach was high level. Here are details that didn’t always make the cut, but matter:
- Job deletion as stealth: Attackers deleted jobs in Salesforce after running queries, so absence of jobs is itself a hunting indicator.
- AppExchange actions: Salesforce not only revoked tokens but fully removed Drift and later disabled all Salesloft integrations. That matters because even tenants who never noticed Drift were impacted by revocation.
- Workspace scope: Google Workspace wasn’t breached. Only mailboxes explicitly tied to Drift Email were accessed on Aug 9. Over-rotating your entire domain isn’t necessary unless you had that integration.
- Attribution caution: ShinyHunters claimed the breach, but Google’s analysis attributes it to UNC6395. For enterprises, attribution isn’t as important as IOCs, but it shows how public claims muddy response.
What Companies Should Do Now?
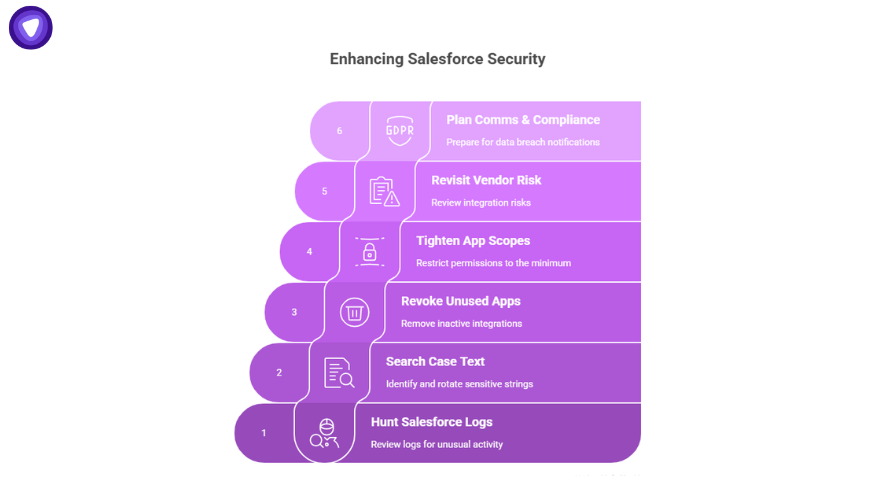
Here’s a step-by-step playbook:
- Hunt Salesforce logs: Review Connected App auth, unusual SOQL queries, bulk job activity, and deletions from Aug 8–18.
- Search case text: Look for strings like AKIA, SNOWFLAKE, client_secret, password. If found, rotate those secrets.
- Revoke unused apps: Remove Drift or other inactive integrations from Salesforce and Workspace.
- Tighten app scopes: Restrict permissions to the bare minimum.
- Revisit vendor risk policies: This wasn’t Salesforce’s bug, but their connected app ecosystem. Vendor risk reviews must cover integrations, not just the core platform.
- Plan comms and compliance: Personal data like names and emails may trigger GDPR/CCPA reporting. If secrets touch regulated systems, prepare notifications.
Beyond SaaS Controls: The Case for VPNs
While OAuth governance and SaaS monitoring are critical, there’s a gap that still needs coverage: data in transit. Once information leaves a device, it’s at risk. VPN encryption closes that hole.
PureVPN White Label - Extending SaaS Security
Resellers and MSPs using PureVPN White Label can add value by pairing SaaS controls with VPN security:
- Offer per-app or full-device VPN that aligns with mobile or EMM policies.
- Guarantee end-to-end encryption for sensitive traffic.
- Help clients demonstrate compliance with HIPAA, ISO 27001, GDPR, and similar frameworks.
- Create recurring revenue streams while solving a compliance requirement.
This is where resellers differentiate. SaaS vendors protect their platforms, but customers need end-to-end security. Pairing VPN encryption with SaaS security delivers layered defense.
Closing Thoughts
The Zscaler data breach didn’t compromise firewalls or VPN concentrators. It compromised trust, trust in the SaaS integrations businesses approve without much scrutiny. That’s where the real risk lies today.
If you run Salesforce, Workspace, or any other SaaS with third-party apps, treat this as your warning. Audit those tokens. Rotate them. Watch the logs. And don’t paste secrets into tickets.
Zscaler will move past this, but the breach leaves a clear message: SaaS integrations are part of your attack surface, whether you see them or not. Pair stronger SaaS governance with VPN encryption to keep both compliance and security intact.
For MSPs and resellers, the opportunity is obvious. With PureVPN White Label, you can help customers close the last mile of risk, protecting their data in transit while you grow your recurring revenue.


