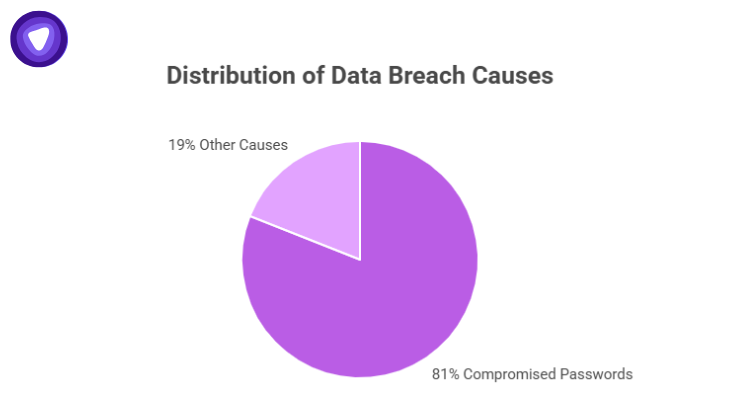
Cybersecurity incidents happen fast, spread quickly, and demand a disciplined response. A single weak or stolen credential can trigger a full-scale crisis. In fact, 81% of breaches involve compromised passwords. That makes password management not just convenient—it makes it a critical component of every Cybersecurity Incident Response Plan (CSIRP).
Security response playbooks form the backbone of CSIRPs. They provide consistency, reduce confusion, and help security teams react with speed and precision. This blog explores how password management strengthens each stage of an incident response playbook and how organizations can incorporate it in a scalable, future-ready way.
What is a Security Response Playbook?
A security response playbook is a step-by-step workflow that guides security teams through handling specific cyber incidents such as malware, ransomware, phishing, insider threats, or denial-of-service attacks. These playbooks:
- Outline roles and responsibilities.
- Establish communication channels.
- Ensure regulatory and internal policy requirements are followed.
- Reduce the cost and business disruption of incidents.
Think of them as your team’s pre-approved set of moves—like a sports playbook—ready to execute when the clock is ticking.
The Five Core Steps of Incident Response (and the Role of a Password Manager)
While every organization customizes playbooks to their structure, tools, and threat models, most follow a five-step framework. Here’s how a password manager strengthens each stage.
1. Preparation
By 2025, businesses will manage an average of 250,000 passwords.
Preparation is about laying the foundation: creating policies, assigning responsibilities, and assessing risks.
Password Manager’s Role:
- Identifies weak, reused, or compromised passwords before attackers exploit them.
- Centralizes credential storage and enforces strong password policies.
- Reduces shadow IT by offering employees and contractors a secure, easy-to-use vault.
A password manager builds a culture of cyber hygiene, lowering the chance of incidents even before they happen.
2. Detection and Reporting
The average time to identify a breach is still 204 days.
Organizations rely on monitoring tools, SIEM platforms, and anomaly detection to flag potential incidents. Timely detection and transparent reporting are critical.
Password Manager’s Role:
- Encourages employees to recognize phishing attempts and report them without fear.
- Provides alerts on exposed credentials through breach monitoring.
- Feeds access logs into SIEM systems for real-time analysis.
When employees are already using a password manager, they develop better judgment in spotting suspicious behavior.
3. Triage and Analysis
At this stage, teams evaluate reports, determine scope, and decide on containment actions.
Password Manager’s Role:
- Offers detailed credential usage data for forensic analysis.
- Integrates with SIEM to correlate unusual login behavior with other threat signals.
- Highlights potential insider misuse or compromised shared credentials.
Faster analysis means faster containment—and lower breach costs.
4. Containment and Neutralization
Organizations that deploy advanced IAM controls save $1.5M on average per breach.
Containment depends on the threat: revoking access, rotating credentials, or shutting down compromised systems.
Password Manager’s Role:
- Allows instant revocation of access to shared credentials.
- Enables role-based access so only authorized users can access sensitive accounts.
- Automates credential rotation to cut off attackers quickly.
Without centralized credential control, response teams risk losing hours while attackers remain inside.
5. Post-Incident Activity
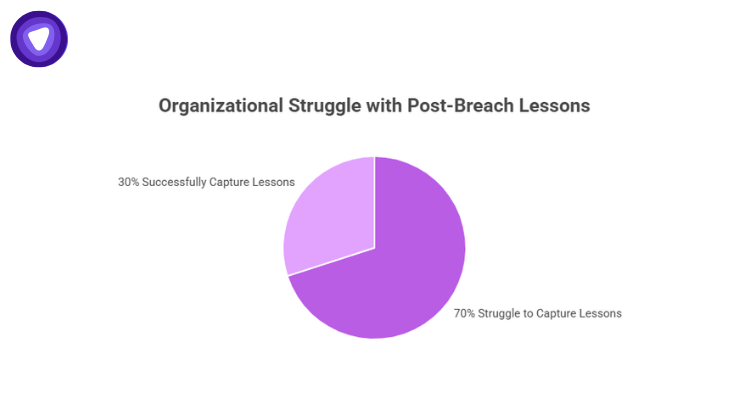
Nearly 70% of organizations struggle to capture lessons learned after a major breach.
After the dust settles, security teams need to review what worked and what didn’t. This stage helps improve resilience for the future.
Password Manager’s Role:
- Provides timestamped event logs for every access attempt.
- Simplifies reporting for leadership and compliance reviews.
- Helps refine incident response playbooks with lessons learned.
A robust password manager ensures post-incident reviews are backed by verifiable data, not guesswork.
With vs. Without Password Manager in Incident Response
| Stage | Without Password Manager | With Password Manager |
| Preparation | Weak/reused passwords across the organization | Strong, unique passwords enforced and monitored |
| Detection | No visibility into credential-related anomalies | Breach monitoring and integration with SIEM tools |
| Triage & Analysis | Manual investigation of scattered login records | Centralized logs enable faster and accurate triage |
| Containment | Slow manual resets of individual accounts | One-click revocation and automated credential rotation |
| Post-Incident Review | Limited or missing forensic data | Timestamped logs available for reporting and audits |
This comparison highlights how password managers reduce both response time and business impact across every stage of incident response.
Beyond the Five Steps: Scaling for Modern Security
Traditional playbooks aren’t enough on their own. Remote work, SaaS sprawl, and global collaboration have stretched attack surfaces.
Password managers act as a force multiplier across your entire security stack:
- With VPNs: Credentials remain secure even in distributed, remote-access environments.
- With Zero Trust: Credential distribution aligns with least privilege principles.
- With DevOps: API keys, SSH credentials, and service accounts stay protected—not scattered in plain text.
As businesses move toward passwordless systems, password managers will serve as the bridge—supporting today’s credential-heavy systems while preparing for tomorrow’s authentication models.
Where PureVPN White Label Password Manager Fits
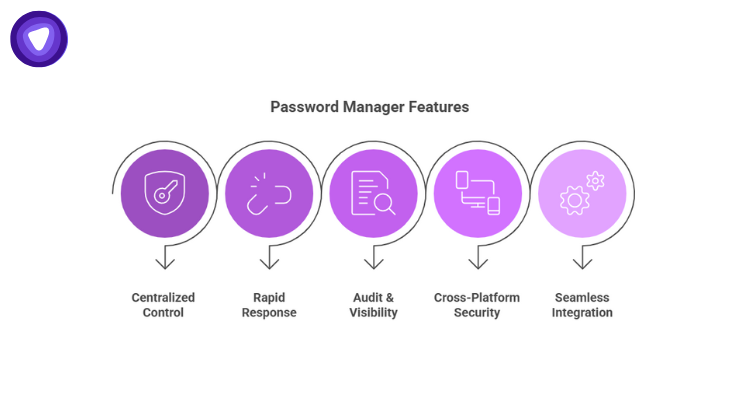
For organizations ready to enhance their incident response playbooks, PureVPN White Label Password Manager delivers key advantages:
- Centralized Control: One secure vault for employees, contractors, and partners.
- Rapid Response: Instantly revoke or rotate credentials during an incident.
- Audit & Visibility: Maintain detailed logs for forensic and leadership reviews.
- Cross-Platform Security: Browser, mobile, and desktop support for hybrid teams.
- Seamless Integration: Works smoothly with VPNs, IAM platforms, and remote access workflows.
With PureVPN Password Manager, your playbooks shift from reactive firefighting to proactive resilience.
Why PureVPN White Label Password Manager is the Right Fit
For partners and businesses looking to offer their own branded solution, the PureVPN White Label Password Manager delivers scalability and trust without the cost of building in-house. It allows you to:
- Launch your own secure password management solution under your brand.
- Add value to your security portfolio and strengthen client trust.
- Integrate seamlessly with existing VPN and remote access offerings.
- Scale instantly for SMBs or enterprise clients without infrastructure overhead.
This makes PureVPN White Label Password Manager not just a security tool, but a business growth opportunity.
Actionable Takeaways for IT Leaders
- Map credential management into every incident response exercise.
- Choose a password manager that integrates with your SIEM, IAM, and VPN stack.
- Leverage access reports to find weaknesses before attackers do.
- Train employees, but empower them with frictionless tools.
- Plan ahead for passwordless, but secure today’s credentials first.
Conclusion: Turning Playbooks into Real Protection
The faster you respond, the less damage an incident inflicts. Password managers ensure your playbooks have the tools to move fast, cut off compromised accounts, and maintain visibility throughout.
When you embed a password manager into your incident response strategy, you’re not just protecting passwords—you’re protecting your entire business.


