- Incident: Unauthorized access to a third-party customer support platform used by Discord.
- Affected Users: People who contacted Discord Support or Trust & Safety.
- Exposed Data: Names, usernames, email addresses, support ticket content, partial billing details, and a limited number of ID images.
- Safe: Passwords, full credit card numbers, CVV codes, and chat history outside of support remain secure.
- Response: Discord revoked the vendor’s access, launched a cybersecurity investigation, and notified affected users.
Discord is used by hundreds of millions of users to build communities, communicate, and run businesses. In early 2025, the platform confirmed a Discord data breach linked to one of its third-party service providers. While Discord’s core servers were not compromised, the breach still exposed sensitive personal details for users who interacted with its support teams.
This incident highlights how attackers now target supply chain integrations instead of attacking primary systems directly. It is a critical case study for businesses that rely on outside vendors to handle support, analytics, or customer data.
What Happened – Timeline Of Events
Here is the timeline of Discord data breach from start to end:
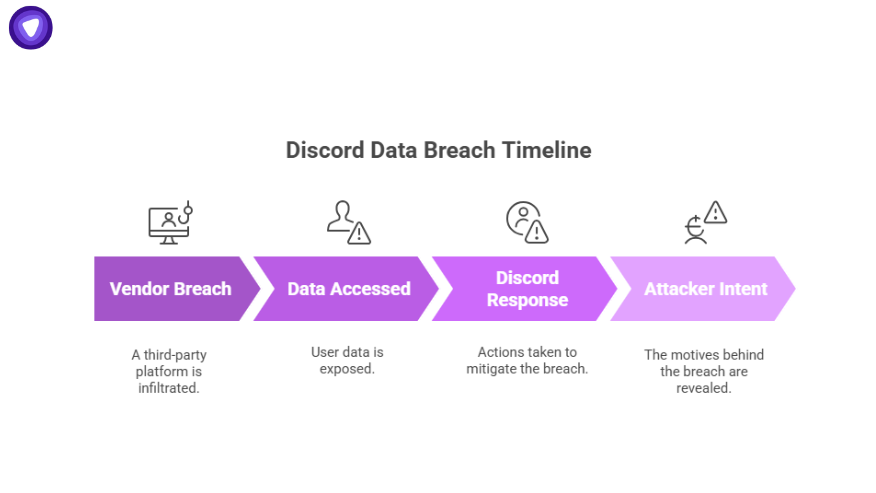
- Vendor breach
A third-party help desk platform used by Discord was infiltrated. Reports suggest it may have been a provider such as Zendesk.
- Data accessed
- Full names and Discord usernames.
- Email addresses and contact details.
- Complete support ticket conversations.
- Partial billing data (payment method and last four card digits).
- A small number of government IDs used for age verification.
- Full names and Discord usernames.
This confirms that the Discord customer support data breach exposes user information including scanned photo IDs.
- Discord response
- Vendor access was revoked.
- Users received direct notifications.
- Cybersecurity investigators were engaged.
- Authorities were informed.
- Vendor access was revoked.
- Attacker intent
Evidence shows the goal was ransom and extortion. Exposed IDs create risk for phishing and identity theft.
Why Only Support Users Were Impacted?
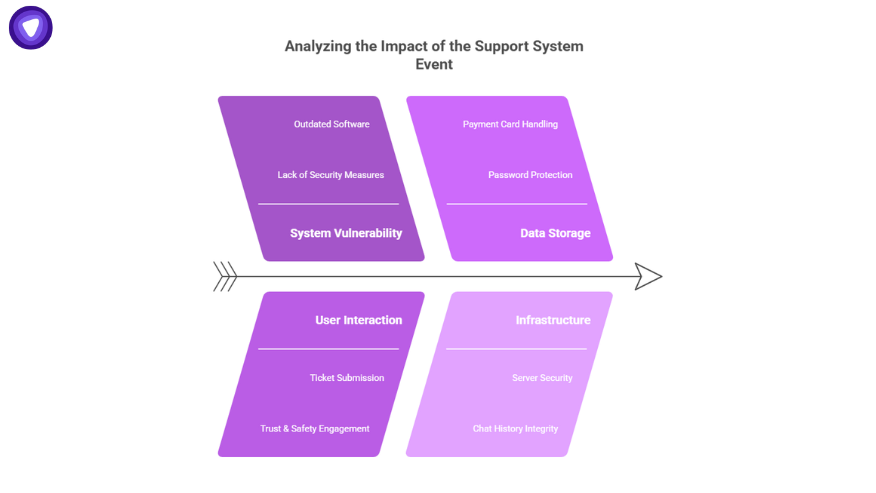
The event involved the support system, not Discord’s main servers.
- Users who never opened a ticket with Support or Trust & Safety were not exposed.
- Passwords, servers, chat history, and voice calls remained inside Discord’s protected infrastructure.
- Full payment card data was never stored in the affected system.
Some headlines described it as a Discord leak, but it was specifically a supply chain attack on a vendor.
Supply Chain Security Risks
Applications rely on many outside tools for support, analytics, billing, and messaging. Each connection adds exposure. The Discord data breach 2025 shows how a single weak vendor can compromise an otherwise well-protected platform.
Comparable events:
| Company | Year | Attack vector | Data exposed |
| Discord | 2025 | Customer support vendor | Emails, IDs, support tickets |
| Okta | 2023 | Support portal | Session tokens, admin data |
| Mailchimp | 2023 | Help desk | Customer email lists |
| MOVEit | 2023 | File transfer software | Corporate files |
Attackers now favor supply chain breaches because one entry point affects multiple organizations.
Practical Lessons for Businesses
Here are some of the lessons that you can take out from the Discord data breach:
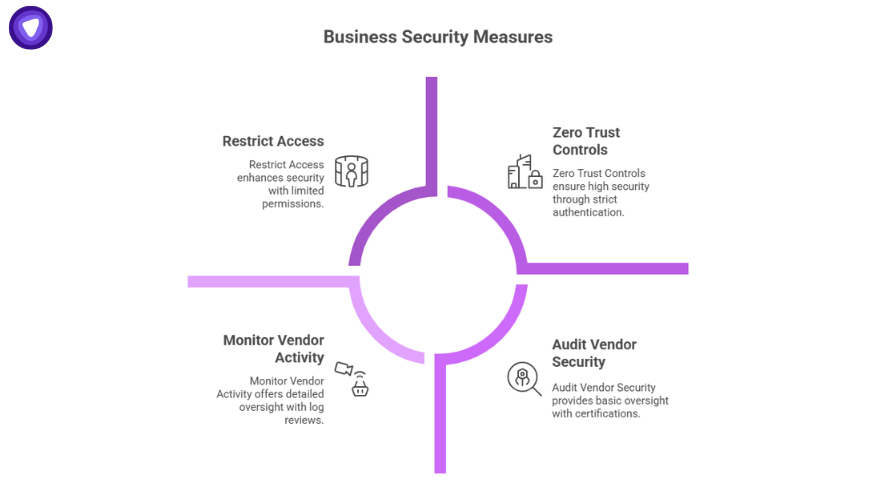
1. Audit Vendor Security
- Require SOC 2 Type II or ISO 27001 certification.
- Review encryption standards and data retention policies.
- Confirm that vendors run penetration tests and incident response drills.
2. Restrict Access
- Apply least-privilege permissions to API keys and admin accounts.
- Rotate credentials on a schedule.
- Remove inactive integrations.
3. Monitor Vendor Activity
- Centralize and review logs.
- Use security information and event management (SIEM) alerts for unusual access.
- Simulate vendor breach scenarios during incident response exercises.
4. Build Zero Trust Controls
- Authenticate every request, including those from external platforms.
- Segment data to prevent one vendor from exposing an entire system.
Steps Discord Users Should Take
If you interacted with Discord Support:
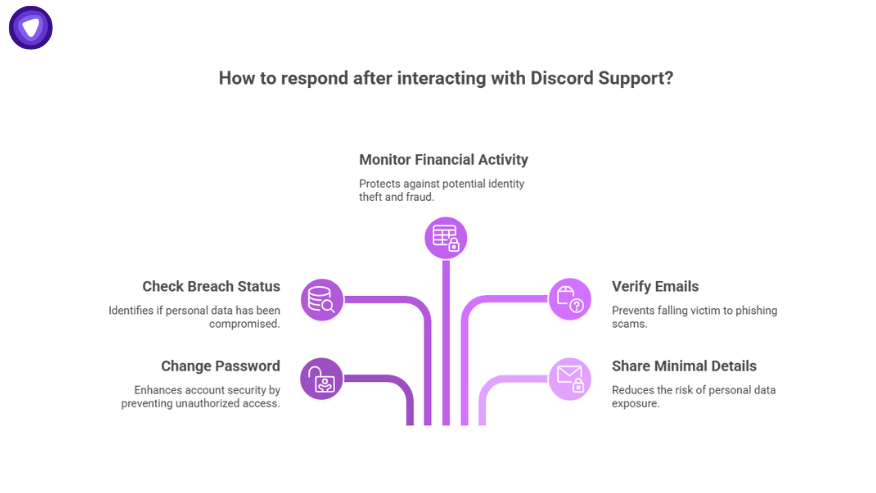
- Change your password and enable two-factor authentication.
- Check HaveIBeenPwned to see if your email appears in any breach database.
- Monitor bank and credit activity if you submitted an ID.
- Treat unexpected emails mentioning your support history as phishing until verified.
- Share only minimal personal details in future support tickets.
Many users perform a Discord data breach search or review a Discord data breach list to confirm whether their information was affected.
Supply Chain Attacks Are Increasing
Attackers favor vendors because:
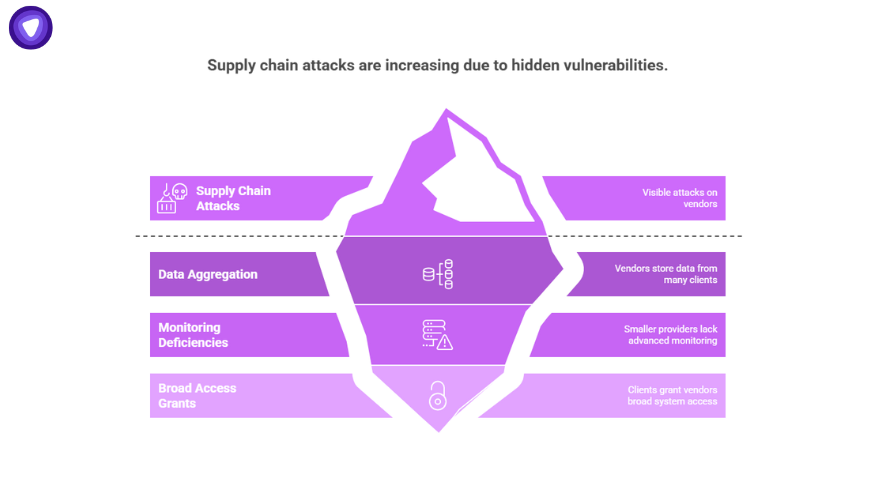
- Vendors store aggregated data from many clients.
- Smaller providers often lack advanced monitoring.
- Clients tend to grant broad access by default.
For SaaS providers and IT leaders, continuous vendor evaluation and strict access control have become essential.
Industry Comparison
| Breach | Target | Cause | User impact |
| Discord 2025 | Support vendor | Account compromise | Names, emails, IDs |
| Okta 2023 | Support portal | Social engineering | Session hijacking |
| MOVEit 2023 | File transfer | Zero-day exploit | Enterprise files |
| Mailchimp 2023 | Help desk | Internal account takeover | Email lists |
Discord acted quickly compared to some earlier incidents, but the shared lesson is clear: vendor risk equals organizational risk.
Final Takeaway
The Discord data breach 2025, larger and more severe than the Discord data breach 2024, shows how attackers now strike third-party vendors rather than primary systems. Users should protect their accounts, verify exposure with HaveIBeenPwned, and watch for phishing attempts.
For businesses, the message is clear: vendor security is part of your own security posture. Evaluate external tools, restrict their permissions, and monitor their activity continuously.
If your product handles sensitive communications or identity data, strong encryption and private network controls are critical.
PureVPN lets SaaS companies, MSPs, and digital platforms launch a fully branded VPN service built on proven security infrastructure. Offering a trusted VPN helps reduce data exposure risk, strengthens compliance readiness, and builds user trust without the cost of building your own network.


