Reports about a massive Gmail data breach affecting more than 2.5 billion users have raised alarms across the internet. Many readers assumed that Google’s own systems were compromised, exposing emails, passwords, and private conversations.
But what actually happened paints a different picture.
This article explains the full story behind the Google Gmail data breach, clarifies what was really exposed, and outlines what individuals, IT teams, and Managed Service Providers (MSPs) can do to strengthen their login security.
- There was no direct Gmail system breach — leaked credentials came from external data dumps.
- The main risk is password reuse and phishing, not Gmail’s servers.
- Users should rotate passwords, enable MFA, and use a password manager.
- Businesses should combine VPN access and credential security for employees.
- MSPs can turn this need into opportunity through PureVPN’s White Label security bundle.
What the Headlines Got Wrong?
When social media exploded with posts claiming “2.5 billion Gmail users at risk,” the headlines created a sense of crisis but most of them lacked technical context. Many articles referenced a Google Gmail data breach warning without explaining that no evidence pointed to Gmail’s servers being directly hacked.
Instead, millions of login credentials associated with Gmail addresses appeared in large credential dumps compiled from earlier third-party leaks and infostealer malware campaigns. In other words, while Gmail users’ emails weren’t stolen from Google itself, their credentials had surfaced in old breaches linked to infected browsers or compromised websites.
This distinction matters. Google’s infrastructure remains secure, but password reuse across different services continues to create new risks, especially for organizations that rely on Google accounts for identity and access management.
The Real Story Behind the Breach
The so-called Gmail breach was not a single event. Rather, it was a chain reaction triggered by massive data compilations where leaked logins were combined, repackaged, and resold.
Cybercriminals often use Gmail accounts as identifiers in phishing campaigns because they are widely trusted. When credentials appear in these dumps, they become valuable for automated attacks against other platforms.
Many users received what appeared to be a Google Gmail data breach update through phishing emails. These messages imitated Google’s support tone, prompting users to “verify” their login details. This wave of social engineering made the incident look far more severe than it was.
In short:
- Google’s servers were not breached.
- Credential leaks came from third-party exposures.
- Phishing amplified the confusion.
For MSPs and SaaS providers, this highlights a recurring weakness: the human element. Most data breaches succeed not because encryption fails, but because users fall for engineered trust.
Was Gmail Actually Hacked?
The question appeared everywhere: “Was Gmail hacked?”
The short answer is no.
Google’s authentication and storage systems remain among the most secure in the world. The panic arose when hackers uploaded billions of previously stolen credentials and labeled them as “Gmail accounts.” Since many of these were linked to old Google logins, the story spread like wildfire.
What this means is that credential exposure occurred, not a system compromise. That’s an important distinction for security teams.
If a user’s credentials appear in such a dataset, attackers can still attempt credential stuffing (trying the same password on multiple services) or phishing to harvest new data. That’s where businesses should step in with preventive policies.
How to Know If Your Gmail Account Is Compromised?
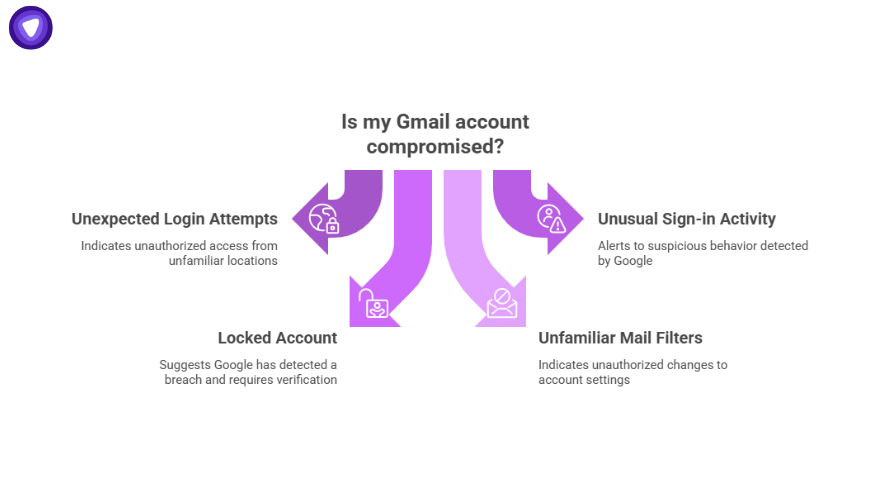
Google’s ecosystem is designed to flag suspicious behavior before it becomes a breach. Warning signs include:
- Unexpected login attempts from unfamiliar regions
- Notifications about “unusual sign-in activity”
- Locked accounts requesting verification
- Mail filters or forwarding rules you didn’t set
Business accounts on Google Workspace have even more control. Admins can review user access logs, audit connected third-party apps, and revoke compromised OAuth tokens.
The simplest approach is to regularly check your Google Account Security Dashboard, where you can view recent sign-ins, devices, and recovery options.
Checking If Your Data Was Breached
Even though the Google Gmail data breach wasn’t a direct attack on Google’s systems, users can still confirm whether their information was included in third-party leaks.

Here’s how:
- Use Google’s Dark Web Report to scan for leaked credentials associated with your Gmail address.
- Enable automatic alerts that notify you when your credentials appear in any known database.
- Regularly change passwords that are reused across multiple platforms.
- Avoid entering Gmail credentials on non-Google pages, even if they look official.
For organizations, this step should be part of routine risk assessments. MSPs should integrate these checks into client onboarding and account maintenance workflows.
What “Password Found in a Data Breach” Really Means?
When Google warns that your password was found in a data breach, it doesn’t necessarily mean Gmail was hacked. It means that the same password was seen in another compromised database somewhere else.
For example, if an employee uses the same password for both Gmail and a project management app, and that app gets breached, the Gmail credentials are automatically at risk.
The best practice here is to:
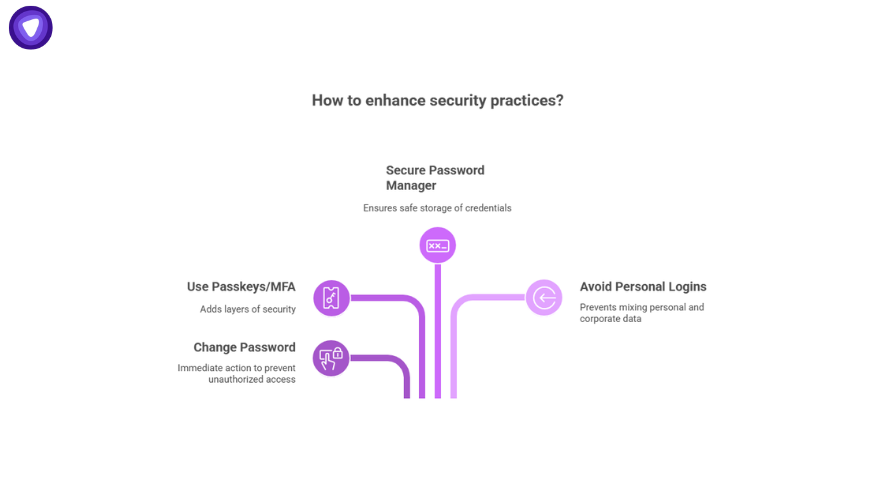
- Change the password immediately.
- Use passkeys or multi-factor authentication (MFA).
- Store new credentials in a secure password manager.
- Avoid using personal Gmail logins for corporate applications.
Businesses should also maintain internal policies that automatically enforce credential rotation every 90 days.
Why This Breach Still Matters for Businesses?
Even though Gmail itself remained secure, the ripple effects are significant for businesses and MSPs. The Google Gmail data breach showed how a single weak link in user behavior can expose entire ecosystems.
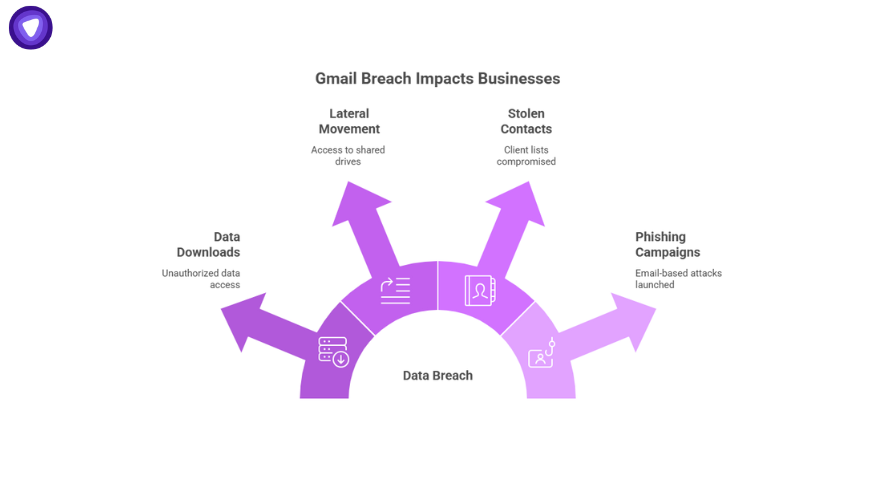
For companies relying on Google Workspace, a single compromised account can lead to:
- Unauthorized data downloads
- Lateral movement inside shared drives
- Stolen contacts and client lists
- Email-based phishing campaigns using trusted domains
This is why businesses must move beyond reactive security measures and build multi-layered defenses combining encryption, credential governance, and access monitoring.
Action Plan: What to Do Right Now?
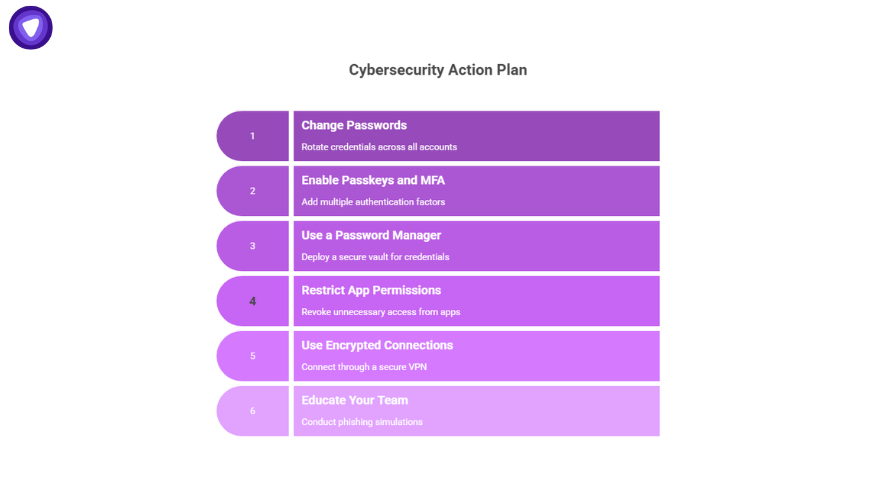
Every company and individual can strengthen their defenses using these steps:
- Change Passwords
Rotate credentials across all accounts linked to Gmail. Avoid using any password that’s been previously exposed.
- Enable Passkeys and MFA
Add multiple authentication factors, biometric, hardware, or token-based, for all admin-level accounts.
- Use a Password Manager
Deploy a secure vault to store and monitor employee credentials. Business-grade options let you detect if any password appears in future leaks.
- Restrict App Permissions
Revoke unnecessary access from apps connected to your Gmail or Workspace account.
- Use Encrypted Connections
Always connect to Gmail, Workspace, or any web-based admin panel through a secure VPN. This helps prevent man-in-the-middle attacks or credential sniffing.
- Educate Your Team
Conduct quarterly phishing simulations. Awareness remains the most affordable yet underused security control.
Turning Security Awareness Into Growth
For Managed Service Providers, the incident is not just a lesson. It’s an opportunity. Clients now expect proactive defense, not just reactive support.
Adding a white label VPN and password manager bundle to your service stack can help you:
- Provide real, tangible protection under your own brand.
- Build recurring revenue through subscription-based security add-ons.
- Strengthen long-term client trust by offering continuous protection.
PureVPN’s White Label platform allows MSPs to integrate VPN and password management tools seamlessly into their business offerings. It’s a fast, scalable way to give clients privacy, access control, and credential protection without building the infrastructure from scratch.
Beyond Gmail: The Larger Lesson
The Gmail incident is only one example of a much broader problem, the interconnected nature of credential exposure.
When people reuse the same email and password combination across different apps, every breach becomes everyone’s problem.
True prevention requires:
- Encrypted access to all endpoints
- Segregated credentials for every tool
- Continuous monitoring of credential exposure
- Transparent reporting for compliance and audits
For businesses offering digital products, embedding a security layer like a white label VPN and on-premise password manager can transform user trust and reduce support overhead.
Conclusion
The phrase “2.5 billion Gmail users at risk” may have made headlines, but it does not reflect an actual compromise of Gmail’s systems. What really happened is a global reminder that credential security defines organizational resilience.
For IT decision-makers and MSPs, the lesson is simple: invest in credential hygiene, access control, and encrypted connectivity.
Partnering with PureVPN White Label gives your business the tools to do exactly that a customizable VPN and password manager suite that protects your users, strengthens your reputation, and helps you monetize trust.
Security is no longer optional. It’s what separates businesses that react to breaches from those that prevent them.


