147 Million Personal Data Exposed: The Equifax Data Breach That Changed Everything
In 2017, an unpatched software vulnerability allowed attackers to infiltrate Equifax, one of the largest...
How User Authentication Works in White Label VPN Services?
TL;DR VPN protocols determine speed, security, stability, and overall user experience in white label VPN...
Conduent Data Breach: Exposed 25 Million Americans
For millions of Americans, the first sign of a problem was a letter from a...
VPN Protocols Used in White Label VPN Platforms
TL;DR VPN protocols determine speed, security, stability, and overall user experience in white label VPN...
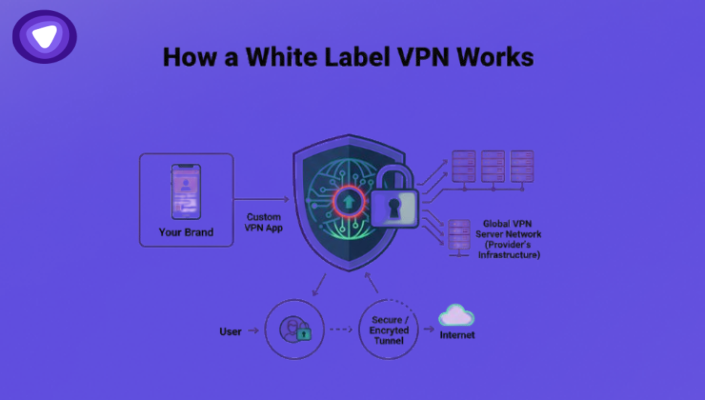
How a White Label VPN Works
Launching a VPN from scratch means building a global server network, implementing secure tunneling protocols,...
VPN API vs VPN SDK: A Practical Decision Guide for CTOs and Dev Teams
Integrating VPN functionality into your product no longer requires a complex infrastructure overhaul. VPN APIs...
Integrating White Label VPN Services into Your Existing Business Infrastructure
What actually breaks when a white label VPN is added to an existing business infrastructure?For...
Complete White Label VPN Business Guide
TL;DR White Label Simplifies Launch: A white label VPN business lets you launch a fully...
White Label VPN Offerings Breakdown
A slow connection, a security breach, or a confusing app can turn your brand into...
API-First VPN Integration – Developer’s Guide
APIs are the backbone of modern software integration. They let you extend your app’s functionality...