Cloud Computing Essentials Unlock Benefits for Your Business
Cloud computing is reshaping business at scale. In 2025 alone, global cloud spending is expected...
How to Configure the SFTP Port for Maximum Security?
As cyber threats continue to escalate, secure file transfer has become a foundational layer of...
FQDN vs Domain Name: What’s the Difference and Why It Matters?
In enterprise networks, accuracy is everything—especially in DNS. If you’re launching a branded VPN, deploying...
What Is a Residential Proxy? (And How It’s Different from a VPN)
When businesses try to access geo-restricted content, collect data at scale, or test user experiences...
Eisner Advisory Group LLC Data Breach: Everything You Need to Know
When news broke of the Eisner Advisory Group LLC data breach, most headlines summarized it...
Why More Companies Are Outsourcing to Cloud Managed Data Centers in 2025?
In 2025, companies aren’t looking to build massive server rooms anymore. They’re not interested in...
Pegasus Spyware via Email: Real Threat or Media Hype?
You’ve probably seen the headlines. Or maybe you’ve received one of those shady emails. “We’ve...
What is an Application Control Engine and How It Secures VPN Networks?
Cybersecurity isn’t just about putting up a firewall or buying a premium VPN anymore. Businesses...
What Is Adaptive Network Control and Why Your Business Needs It?
When your network slows down or crashes, users blame the VPN, IT blames the bandwidth,...
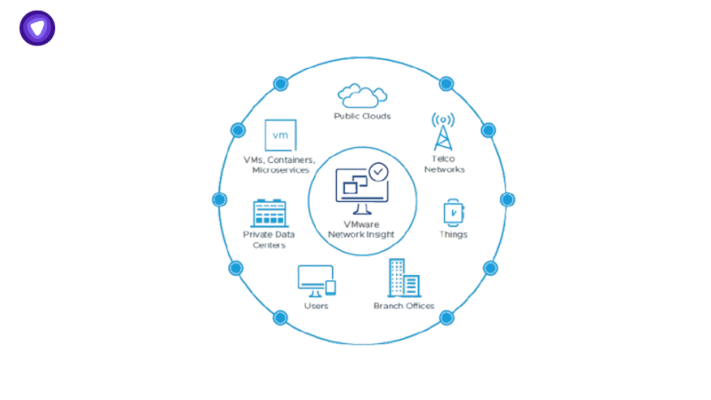
What is vRealize Infrastructure Navigator And How It Helps Understand VPN Traffic?
The complexity of today’s enterprise infrastructure isn’t in the hardware. It’s in the connections between...