How eSIM for IoT Devices Solves Connectivity Challenges and Avoids MVNO Limits?
The IoT market is scaling faster than any other sector of connectivity. 34.7 billion devices...
How to Ensure Secure Internal Communication Across Platforms?
When a team grows beyond a single room, communication changes. When a company starts handling...
Why Offer VPN for eSIM Users in Restricted Internet Environments?
If you’re leading an eSIM business—whether as a telco, a reseller, or a tech-driven MVNO—then...
What Is a VPN Tunnel? Why It Matters Before Launching Your VPN Brand
If you’re preparing to launch a VPN brand or expand your digital product portfolio with...
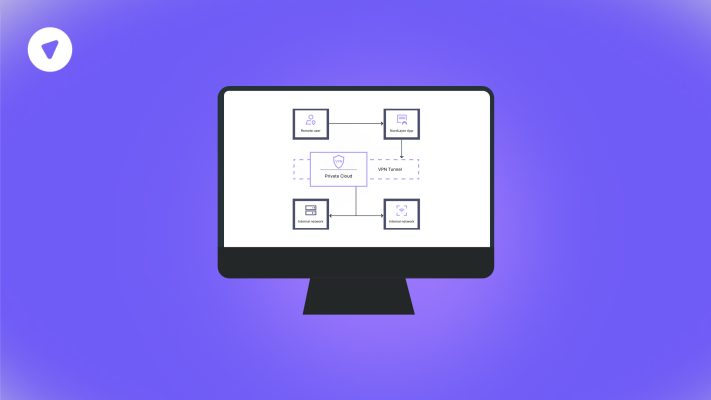
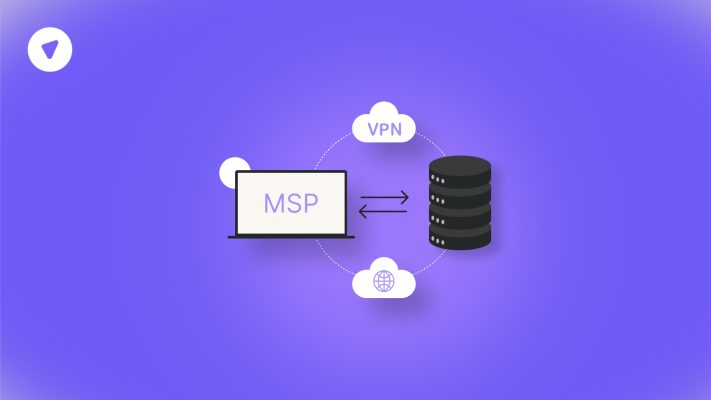
What Is a Client to Site VPN? Complete Breakdown for Businesses and MSPs
Client to Site VPNs provide a secure tunnel between individual user devices and corporate networks....
How to Launch a VPN-Powered SaaS Product Fast with a Custom SDK?
Speed matters. If you’re building a SaaS product today, users expect more than just good...
What Is a Point-to-Site VPN and How Does It Work?
Remote access used to be a bonus. Now, it’s core infrastructure. Teams work from anywhere....
Is VPN Gate-Client Safe to Use? Key Security Considerations Explained
VPN Gate-Client often pops up on forums and software download sites, especially for people looking...
What Is Traceroute VPN? A Deep Dive into VPN Routing and Diagnostics
When a VPN is up and running, most people don’t think about what’s happening behind...
Synology VPN Configuration Guide: Fixing the Most Common Setup Mistakes
Setting up a VPN should be simple. But if you’ve ever tried configuring one on...