The Hidden Cost of Managing Heavy VPN Gateways
It shows up months later in slowed deployments, growing cloud bills, frustrated teams, and infrastructure...
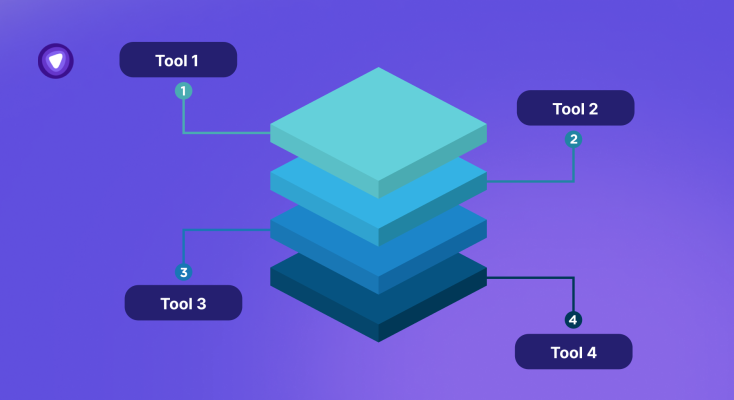
How to Consolidate 3–4 Security Tools Into One Routing Layer
Security teams rarely wake up planning to manage four dashboards before lunch. Yet that is...
The Real ROI of Integrating a VPN API in Your App Infrastructure
Some infrastructure decisions look small on paper but quietly shape the economics of an entire...
What’s Improving in Our VPN Experience: Exit Locations, Data Protection & Reliability
You may notice changes in your VPN experience over time — things like exit locations...
The Risks of Maintaining Custom VPN Infrastructure In-House
TL;DR Maintenance Risks: Maintaining custom VPN infrastructure in-house creates ongoing security, operational, and scaling challenges....
Connected but Nothing Loads? Your Easy Guide to DNS Issues — and How We’re Fixing Them
If your VPN says “Connected” but websites and apps won’t load, it’s frustrating — and...
MSP Onboarding Checklist: Rolling Out VPN for Clients
TL;DR Structured Checklist: A structured MSP onboarding checklist ensures secure, consistent, and efficient VPN deployment...
Why Privacy Products Sell Better Than Antivirus or Firewalls
TL;DR User Value: Privacy products are perceived as more user-focused, offering visible personal value compared...
A Simple Guide to Why Your VPN Shows Different Locations(And How It Gets More Accurate Over Time)
When you connect to a VPN, you expect websites and apps to recognize the country...
Cybersecurity Market Share by Company: What Startups Can Learn
TL;DR Market Concentration: Top-tier vendors control 45–50% of global cybersecurity revenue. Market Growth: Global cybersecurity...