Category Archives: Cyber Security
API-First VPN Integration – Developer’s Guide
APIs are the backbone of modern software integration. They let you extend your app’s functionality...
Instagram Data Breach: Did 17.5 Million Accounts Get Exposed?
Instagram Data Breach: Did 17.5 Million Accounts Get Exposed? Several days into January, a wave...
WormGPT and the Rise of AI-Driven Business Email Compromise (BEC): What Enterprises Need to Know
Enterprises today face an evolving threat landscape that no longer revolves solely around exploits of...
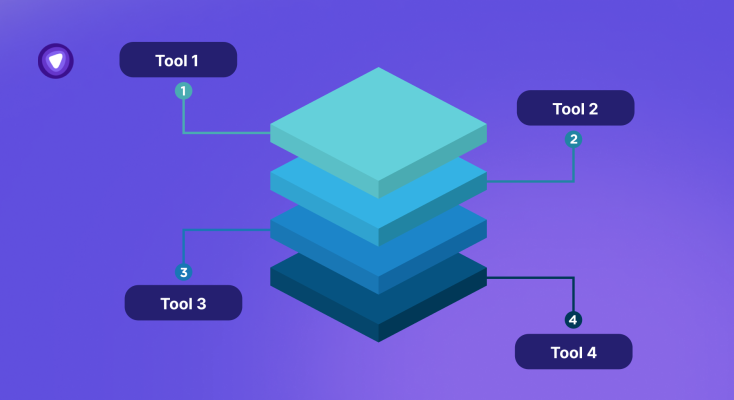
How to Consolidate 3–4 Security Tools Into One Routing Layer
Security teams rarely wake up planning to manage four dashboards before lunch. Yet that is...
Why Privacy Products Sell Better Than Antivirus or Firewalls
TL;DR User Value: Privacy products are perceived as more user-focused, offering visible personal value compared...
A Simple Guide to Why Your VPN Shows Different Locations(And How It Gets More Accurate Over Time)
When you connect to a VPN, you expect websites and apps to recognize the country...
Cybersecurity Market Share by Company: What Startups Can Learn
TL;DR Market Concentration: Top-tier vendors control 45–50% of global cybersecurity revenue. Market Growth: Global cybersecurity...
US Cybersecurity Market Size & 2025 Outlook
TL;DR US Cybersecurity Market Growth: The US cybersecurity market is projected to reach USD 86–89...
Why Privacy Services Are Easier to Sell Than Cyber Toolkits?
TL;DR Privacy services are simpler and easier to implement: They require minimal setup and management...
The New Age of Encryption Attacks (And What It Means for Enterprises)
TL;DR Encryption attacks target weaknesses in cryptography to access sensitive enterprise data. Key types of...