Category Archives: Cyber Security
The 2025 ENISA Threat Landscape: Why Traditional Perimeters Keep Failing?
The European Union Agency for Cybersecurity (ENISA) is the EU’s centre of expertise for cyber-security...
Address Resolution Protocol Vulnerabilities Every Business Should Know in 2025
TL;DR ARP is critical but insecure: The Address Resolution Protocol translates IP addresses to MAC...
Why Bundled Privacy Keeps Subscribers From Churning?
TL;DR Privacy drives loyalty. Most users stay with a provider because they feel secure—not because...
Cybersecurity Spending Statistics Every CTO Should Know in 2025
Cybersecurity in 2025 is not about isolated tools. It’s about ecosystem resilience. Enterprises are no...
Cybersecurity Market Growth & Trends to Watch in 2025
Cybersecurity has become a board-level priority in 2025 as AI-driven attacks, ransomware-as-a-service, and strict data...
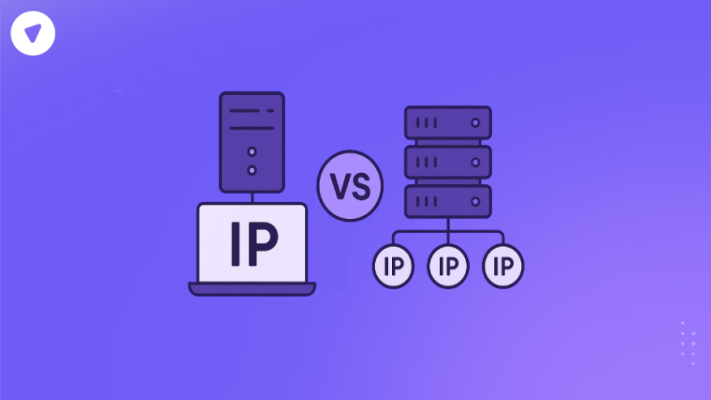
Dedicated IP vs Shared IP: How to Decide for Privacy, Speed, and Control?
Internet Protocol (IP) addresses are the foundation of how devices and services connect online. For...
Your Value Added Reseller Kit: Everything You Need to Resell White Label Cybersecurity
Value Added Resellers (VARs) remain critical to technology distribution. They act as trusted partners who...
White-Label Cyber Security Stack: The Next Big SaaS Differentiator
Security is no longer a feature reserved for large enterprise platforms. It is now a...
What Is White-Label Cybersecurity & Why It’s the Future of SaaS Growth?
For years, cybersecurity was seen only as risk mitigation. Today, it is a revenue and...
Why ISPs Are Becoming Security Companies?
Internet Service Providers (ISPs) once focused almost entirely on bandwidth and uptime. That model is...