- Compliance Matters: Compliance for SaaS is critical for enterprise adoption, covering frameworks like SOC 2 and GDPR.
- Checklists Save Time: A structured compliance checklist reduces audit preparation time and ensures control maturity.
- SOC 2 Certification: Valuable for enterprise targeting, handling sensitive data, and demonstrating a mature security posture.
- White-Label VPN: Secures data in transit, centralizes access control, provides audit-friendly logs, and supports global compliance.
- Automation + VPN: Combining VPN infrastructure with compliance software streamlines evidence collection, improves audit readiness, and strengthens overall security posture.
Scaling a SaaS business introduces new responsibilities, particularly around compliance and security. As you onboard more customers, especially enterprise clients, external audits, regulatory demands, and customer trust converge on one critical area: compliance for SaaS.
Yet, the burden of meeting frameworks like SOC 2 and GDPR can slow growth and distract from product innovation.
Enter a white-label VPN: when architected well, it is not just a way to secure data in transit, it helps unify controls, strengthen audit readiness, and provide transparency toward customers.
This blog walks you through what compliance for SaaS looks like in 2025, key checklists and frameworks, and how a white-label VPN can simplify your compliance journey.
What Is SaaS and Why Its Compliance Is Unique
SaaS, or Software-as-a-Service, delivers software over the internet rather than through local installation. Users access applications via browser or thin clients, while providers run infrastructure in data centers or cloud platforms.
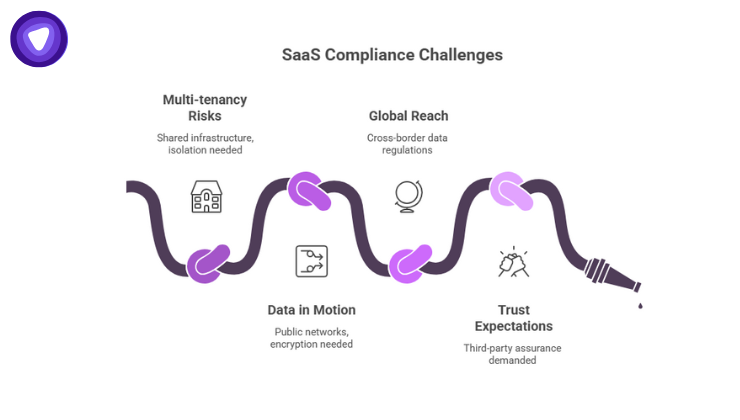
That delivery model brings distinct compliance challenges:
- Multi-tenancy risks: Shared infrastructure demands stringent isolation
- Data in motion: Traffic traverses public networks, raising encryption and transit concerns
- Global reach: SaaS often serves customers in multiple jurisdictions, triggering cross-border data regulations like GDPR
- Trust expectations: Enterprises increasingly demand third-party assurance, for example SOC 2, before signing contracts
In short, compliance for SaaS is not optional if you want to play at the enterprise level.
According to Gartner, 64% of SaaS companies reported regulatory concerns as a top barrier to enterprise adoption in 2024.
Top SaaS Regulations and Frameworks You Should Know
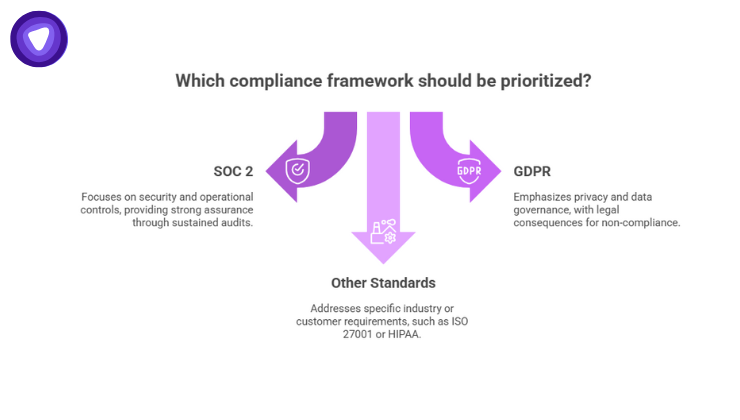
When we talk about compliance for SaaS, some frameworks are especially common and influential:
- SOC 2 (System and Organization Controls, Type II)
- Developed by AICPA, it assesses internal controls across five Trust Services Criteria: security, availability, processing integrity, confidentiality, and privacy.
- A SOC 2 Type II audit covers a sustained period of 6–12 months, providing stronger proof than a one-time snapshot.
- For SaaS companies, security is non-negotiable; other criteria can be chosen based on business model.
- Developed by AICPA, it assesses internal controls across five Trust Services Criteria: security, availability, processing integrity, confidentiality, and privacy.
- GDPR (General Data Protection Regulation)
- Governs personal data of EU residents. Key requirements include consent, data minimization, breach notification, and data subject rights
- Unlike SOC 2, GDPR is regulated by law, meaning non-compliance can lead to fines up to €20 million or 4% of global revenue, whichever is higher.
- GDPR focuses more on privacy and governance, while SOC 2 emphasizes technical and operational security.
- Governs personal data of EU residents. Key requirements include consent, data minimization, breach notification, and data subject rights
- Other Relevant Standards
Beyond SOC 2 and GDPR, SaaS companies might find themselves dealing with ISO 27001, HIPAA, NIS2, or PCI DSS, depending on industry or customer-set requirements.
Building a Compliance for SaaS Checklist
Here is a practical, prioritized SaaS compliance checklist to help set up and maintain control:
| Area | Key Activities / Controls |
| Governance & Risk | Perform a risk assessment; map data flows; define ownership of controls |
| Policy & Documentation | Draft clear policies (access, incident response, data retention); maintain a control inventory |
| Technical Controls | Encrypt data at rest and in transit; enforce RBAC (role-based access control); use MFA |
| Monitoring & Logging | Enable logging, SIEM, anomaly detection, alerting |
| Vendor Management | Audit third-party providers; ensure they meet your compliance standards |
| Incident Management | Create a security incident response plan; test it regularly |
| Audit Readiness | Maintain artifacts (e.g., change logs, training records); run internal readiness assessments |
| Privacy & Data Subject Rights | Provide data access, correction, deletion; build consent mechanisms; handle breach notifications |
| Continuous Improvement | Regularly reassess controls; refresh policies; patch vulnerabilities |
This checklist aligns with major frameworks, helping you build a unified compliance program. According to a report, organizations that follow a structured compliance checklist reduce audit preparation time by 30% on average.
When Is SaaS Compliance Certification Really Worth It?
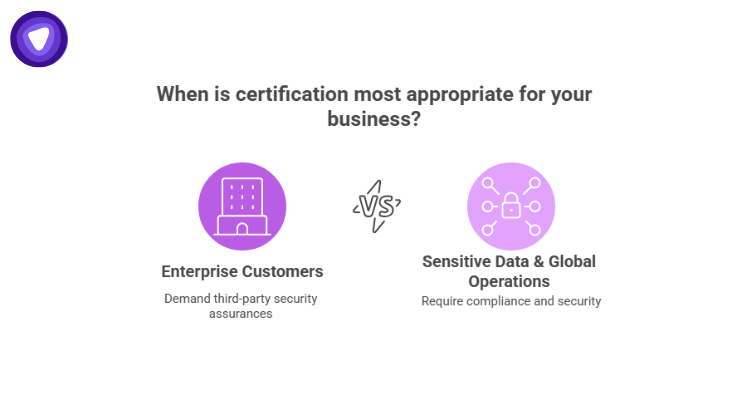
Certification, like a SOC 2 Type II, is not cheap or easy. But here are scenarios where it is most appropriate:
- You are targeting enterprise customers who demand third‑party security assurances
- You process sensitive or regulated data (e.g., financial, healthcare, personal identifiers)
- You operate globally and want to align with GDPR or other cross-border data laws
- You need to stand out from competitors by proving a mature security posture
If you are a very early-stage startup without enterprise ambitions, investing in certification right away might not be strictly necessary. But as scale-ups, many SaaS businesses find a well-executed SOC 2 audit unlocks strategic growth.
Compliance for SaaS Certification: What the Process Actually Looks Like
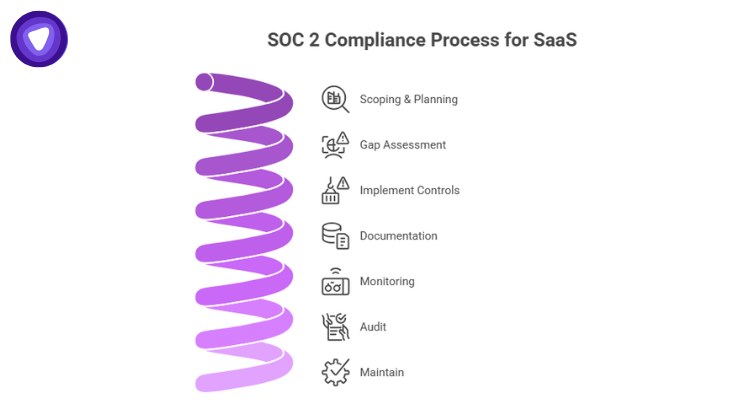
Here is a high-level SOC 2 compliance process for SaaS based on best practices:
- Scoping & Planning: Define which Trust Services Criteria to include. Decide between Type I vs. Type II.
- Gap Assessment: Map your current state against SOC 2 controls to identify deficiencies.
- Implement Controls: Introduce or strengthen policies, technical safeguards (encryption, access control), and response procedures.
- Documentation: Gather and document control evidence, such as logs, policy documents, training records.
- Monitoring: Set up continuous monitoring and internal audits to ensure control effectiveness.
- Audit: Bring in an independent auditor, a licensed CPA, to perform the formal SOC 2 audit.
- Maintain: SOC 2 is ongoing: repeat audits, often annually, and continuously optimize controls.
The Role of SaaS Compliance Software
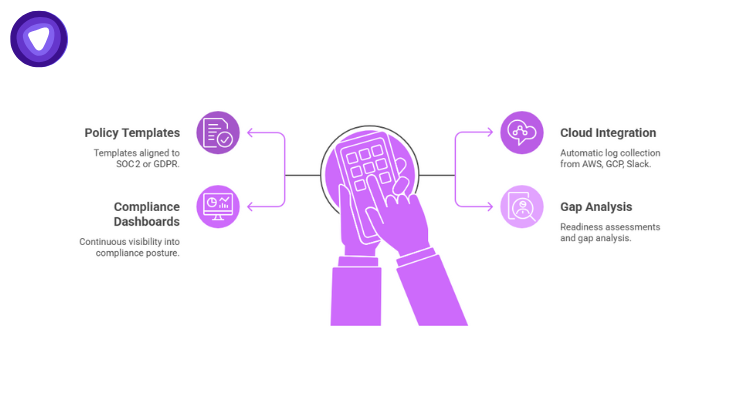
To make compliance manageable, many SaaS companies rely on compliance automation platforms. These tools automate evidence collection, risk mapping, control monitoring, and preparation for audits.
Popular features include:
- Policy templates aligned to SOC 2 or GDPR
- Integration with cloud tools, such as AWS, GCP, Slack, to collect logs automatically
- Dashboards that provide continuous visibility into compliance posture
- Gap analysis and readiness assessments
Automation eliminates much of the manual burden, reduces audit preparation time, and improves control maturity.
Why Integrating SOC 2 and GDPR Makes Sense and Is Challenging

Integrating SOC 2 controls with GDPR obligations can deliver powerful synergies, but it is not trivial.
Benefits of Integration:
- Shared controls: Access control, encryption, monitoring often serve both frameworks
- Unified evidence: Rather than separate audits or separate control sets, you can maintain one set of controls that satisfy both security and privacy demands
- Efficiency: Reduces redundant work and lowers long-term compliance costs
Challenges:
- Different drivers: GDPR is legal/regulatory, SOC 2 is voluntary but contractual
- Documentation complexity: You need both privacy policies for GDPR and control documentation for SOC 2
- Audit cycles differ: GDPR compliance is continuous, SOC 2 audits run on a cycle
Global SaaS Compliance: Special Considerations
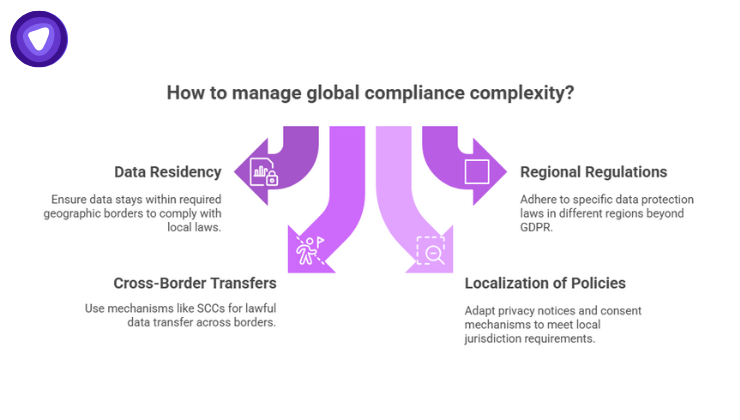
If your SaaS company serves customers around the globe, compliance complexity multiplies:
- Data Residency: Some countries require customer data to stay within geographic borders
- Regional Regulations: Beyond GDPR, other regions, including APAC and Latin America, have data protection laws
- Cross-Border Transfers: Mechanisms like Standard Contractual Clauses may be needed for lawful data transfer
- Localization of Policies: Privacy notices, data subject rights, and consent mechanisms may need localization based on jurisdiction
According to Statista, the global SaaS market reached $250 billion in 2024 and is projected to surpass $350 billion by 2026, making scalable compliance a critical factor for international operations.
In Which Scenario Is a White‑Label VPN a Smart Move for SaaS Compliance
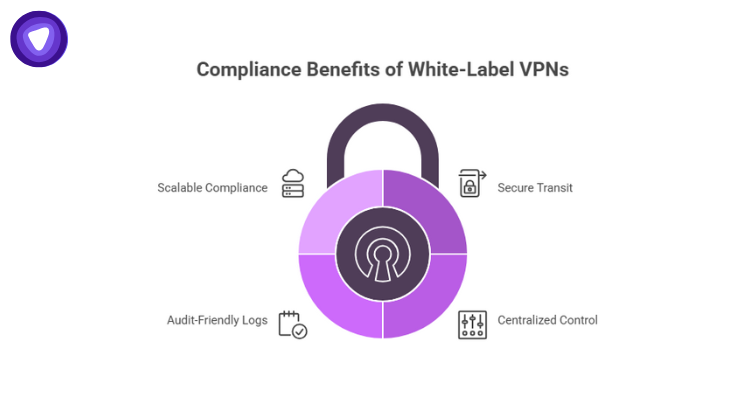
A white-label VPN, your own VPN infrastructure wrapped in your branding, is often overlooked, but it offers several compliance benefits for SaaS companies:
- Secure Transit by Default: All traffic between your users, your services, and your backend is encrypted. This mitigates risks in data transit, a key requirement in both SOC 2 and GDPR.
- Centralized Control: With a VPN under your control, you can enforce strict access policies, restrict which users or services can communicate, control geolocation routing, and audit access logs.
- Audit-Friendly Logs: You gain visibility into connection attempts, usage logs, and timing. This feeds directly into monitoring and continuous control requirements of SOC 2.
- Scalable Compliance: As you onboard new customers globally, you can deploy VPN endpoints in regions, helping address data residency and cross-border rules more effectively.
Why a White‑Label VPN Solves Real Pain for SaaS Compliance
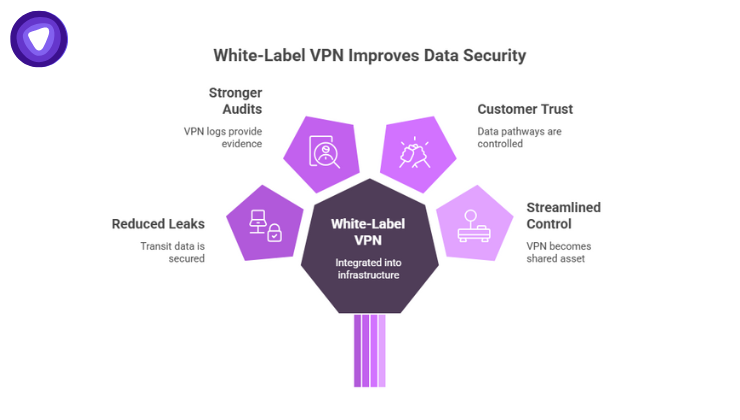
By integrating a white-label VPN into your infrastructure, you can:
- Reduce the risk surface for transit-related data leaks
- Provide stronger evidence during audits via VPN logs
- Demonstrate to customers that you control and isolate their data pathways
- Streamline your control architecture: the VPN becomes a shared compliance asset, not a silo
This does not replace SOC 2 or GDPR, but it significantly enhances your control posture and makes evidence gathering more robust.
How to Build Compliance for SaaS Using a White‑Label VPN and Automation
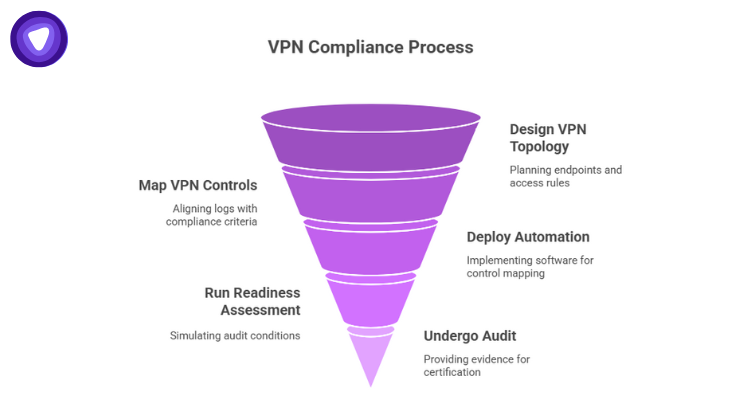
Here is a tactical roadmap to combine compliance software and your own white-label VPN into a unified compliance program:
- Design your VPN topology
- Plan endpoints in strategic regions
- Define access rules for users
- Implement logging and monitoring
- Plan endpoints in strategic regions
- Map VPN controls to Compliance Frameworks
- For SOC 2, tie VPN logs to Security and Availability criteria
- For GDPR, use VPN logs for detecting possible data access or movement
- For SOC 2, tie VPN logs to Security and Availability criteria
- Deploy Automation Platform
- Choose a compliance software that supports custom control mapping
- Ingest VPN logs as evidence streams
- Automate alerting for control deviations
- Choose a compliance software that supports custom control mapping
- Run Readiness Assessment
- Use compliance software to simulate audit conditions
- Verify that all necessary policies, logs, and controls are in place
- Use compliance software to simulate audit conditions
- Undergo Audit and Certification if needed
- Provide auditors with VPN logs, policy documentation, and control mappings
- Use continuous monitoring to demonstrate control effectiveness
- Provide auditors with VPN logs, policy documentation, and control mappings
- Maintain and Improve
- Regularly review VPN access, rotate credentials, test incident response
- Update policies and evidence streams as your architecture evolves
- Regularly review VPN access, rotate credentials, test incident response
Potential Pitfalls to Watch Out For
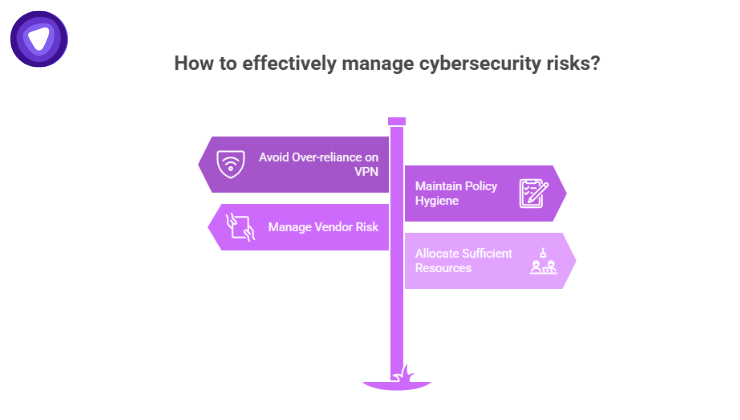
While a white‑label VPN and compliance software are powerful, you need to avoid:
- Over-reliance on VPN: A VPN protects data in transit but does nothing for insecure storage or misconfigured endpoints
- Poor policy hygiene: Even with logs, if your policies are not accurate, up-to-date, or enforced, auditors will spot gaps
- Neglecting vendor risk: If third-party services you use, such as databases or compliance tools, are not equally compliant, risk remains
- Under-resourcing: Running a VPN, logging, and compliance platform requires expertise, not just for setup but for ongoing management
How PureVPN’s White‑Label VPN Solution Makes Compliance Simpler
PureVPN’s White‑Label VPN solution gives SaaS companies full control over data traffic and encryption, making it easier to meet SOC 2 and GDPR requirements. By centralizing access and providing detailed logs, it helps demonstrate strong technical controls during audits while reducing the complexity of managing multiple compliance touchpoints.
With global deployment options and customizable endpoints, the solution supports data residency and cross-border compliance needs. When combined with compliance software, it streamlines evidence collection, improves audit readiness, and strengthens overall security posture without adding operational overhead.
Final Thoughts
Compliance for SaaS is no longer a checkbox. It is a strategic lever for trust, growth, and risk mitigation. As regulatory pressure intensifies and enterprise buyers demand more, pairing automation with a well-designed white‑label VPN gives you a competitive, technically strong, and audit-ready foundation.
Build it smart, log it thoroughly, and keep iterating, and you will not only meet compliance standards, you will build trust into every layer of your SaaS offering.


