- Assessment Focus: Data breach insurance companies assess security based on real access controls, visibility, and enforceability rather than written policies or self-reported questionnaires.
- Identity & Access: Identity, authentication, and remote access management are the first areas insurers evaluate because stolen credentials remain the leading cause of breaches.
- Continuous Monitoring: Recent cyber attacks on insurance companies have pushed insurers to adopt continuous monitoring instead of one-time security reviews.
- Security Gaps: Poor vendor access controls, shared credentials, and limited logging consistently lead to higher premiums, exclusions, or claim disputes.
- Network Architecture: Clear, network-level access architecture reduces uncertainty for insurers and plays a growing role in coverage approval and pricing.
A breach does not begin with malware or a stolen password. It begins months earlier, inside a security assessment spreadsheet that most companies never see.
Before coverage is approved, before premiums are set, and before exclusions are written into a policy, data breach insurance companies quietly evaluate how exposed an organization really is. The process is methodical, evidence-driven, and far less forgiving than many expect.
This article explains how data breach insurance companies assess security today, what changed after recent cyber attacks on insurance companies, and why the insurance company data breach 2025 trend is reshaping how risk is judged across every industry.
Why Insurers No Longer Rely on Questionnaires Alone?
For years, security assessments started and ended with self-reported questionnaires. That era is over.
Data breach insurance companies now treat written answers as only one data point among many. The shift accelerated after a series of high-impact insurance company breach incidents exposed how often internal controls looked good on paper and failed in practice.
According to IBM’s 2024 Cost of a Data Breach Report, organizations with weak access controls faced breach costs that were 29 percent higher on average than those with enforced access segmentation. Insurers absorbed a portion of those losses, which triggered tighter verification standards across the market.
Today, insurers assume gaps exist until proven otherwise.
The Core Security Areas Insurers Evaluate First
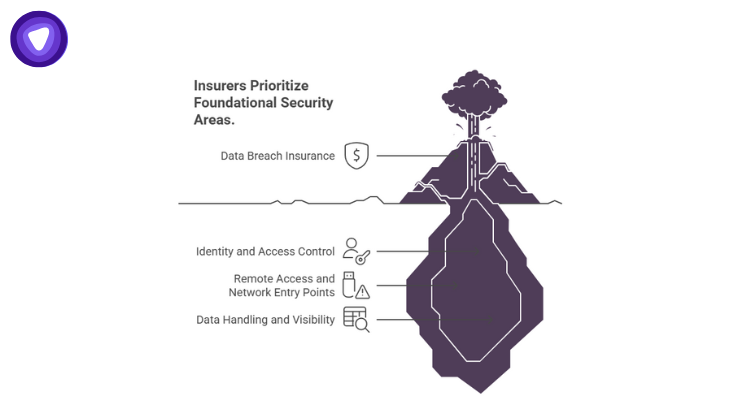
Data breach insurance companies follow a consistent priority order when assessing security posture. The focus is not on how advanced tools appear, but on whether failures can cascade quickly.
Identity and Access Control
This is the starting point for nearly every review.
Insurers assess:
- Whether multi-factor authentication is enforced across all remote access points
- How privileged accounts are assigned and monitored
- If shared credentials exist across teams or vendors
- Whether access is revoked immediately after role changes
The reason is simple. Reports found that stolen credentials were involved in 74 percent of breaches. Insurers see access mismanagement as a leading indicator of claim likelihood.
Remote Access and Network Entry Points
Remote access has become a risk multiplier, especially after recent cyber attacks on insurance companies exploited exposed VPN gateways and unmanaged endpoints.
Insurers look closely at:
- How remote workers authenticate
- Whether traffic is encrypted end to end
- If access is tied to static or shared IPs
- How third-party access is segmented
Open or poorly controlled access paths raise premiums fast.
Data Handling and Visibility
Insurers care less about how data is labeled and more about whether it can move undetected.
Key evaluation points include:
- Whether sensitive data is accessible from remote environments
- If outbound traffic is monitored
- How quickly unusual access patterns are flagged
- Whether logging is centralized and retained
A lack of visibility increases uncertainty, and uncertainty increases insurance cost.
How Recent Insurance Company Breaches Changed the Model?
Recent cyber attacks on insurance companies forced insurers to reassess their own assumptions.
Between 2023 and early 2025, multiple insurers disclosed breaches involving customer data, underwriting systems, or claims platforms. In several cases, attackers entered through third-party access paths that were trusted but weakly controlled.
The insurance sector saw a 67 percent increase in reported cyber incidents between 2022 and 2024. That spike directly influenced underwriting standards.
As a result, data breach insurance companies now apply the same scrutiny to their clients that they apply internally.
Continuous Monitoring Is Replacing One-Time Assessments
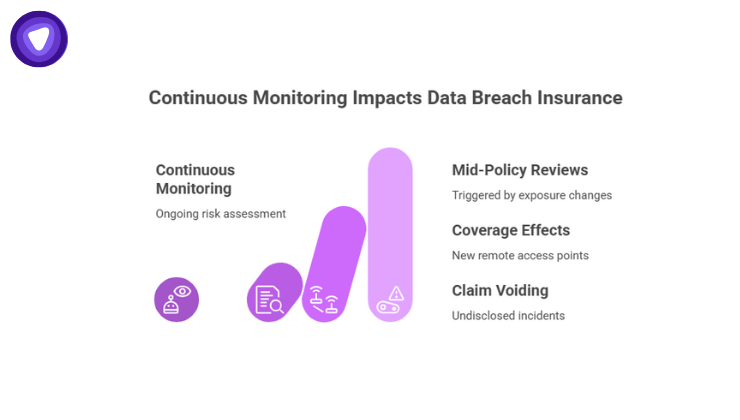
One of the most important shifts is timing.
Security reviews no longer end once coverage is approved. Many data breach insurance companies now use continuous risk monitoring through external scans, threat intelligence feeds, and breach reporting networks.
This means:
- Changes in exposure can trigger mid-policy reviews
- New remote access points can affect coverage
- Undisclosed incidents can void claims
The Role of Third Parties and Vendors
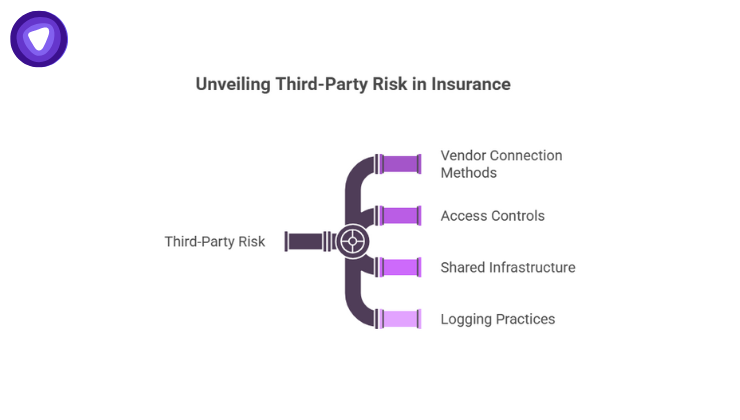
Third-party exposure has become a defining factor in insurance company breach investigations.
Insurers evaluate:
- How vendors connect to internal systems
- Whether access is time-bound and role-specific
- If shared infrastructure exists across clients
- How vendor activity is logged
A single unmanaged vendor connection can outweigh multiple internal controls. Insurers increasingly request architectural diagrams or access flow documentation to validate answers.
What Insurers Look for During Incident Response Reviews?
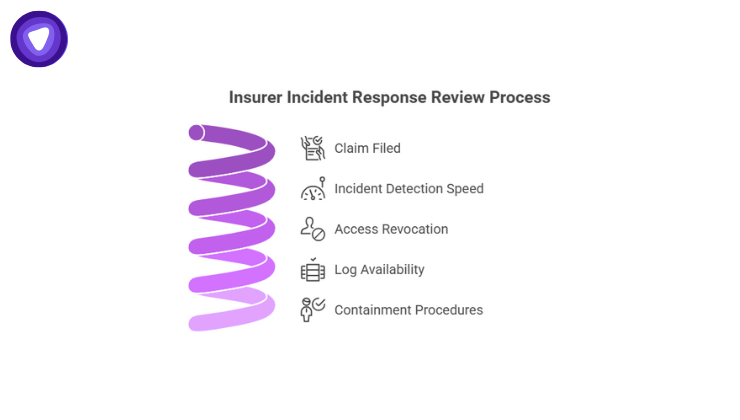
When a claim is filed, the assessment does not stop. It intensifies.
Data breach insurance companies review:
- How quickly the incident was detected
- Whether access was revoked immediately
- If logs were available and intact
- Whether containment followed documented procedures
Slow or improvised responses often result in reduced payouts.
Common Security Gaps That Increase Premiums
Based on underwriting trends and claim disputes, the following gaps consistently raise red flags:
| Security Gap | Why Insurers Flag It | Impact on Coverage |
| Shared VPN credentials | No accountability or traceability | Higher premiums |
| Unrestricted remote access | Expanded attack surface | Coverage exclusions |
| No IP-based access controls | Difficult to verify access origin | Reduced limits |
| Weak vendor access controls | High lateral movement risk | Stricter terms |
| Limited logging retention | Poor breach reconstruction | Claim disputes |
These gaps appear frequently in insurance company data breach 2025 case reviews.
Why Network-Level Controls Matter More Than Ever?
Endpoint tools and user training still matter, but insurers increasingly prioritize controls that operate independently of user behavior.
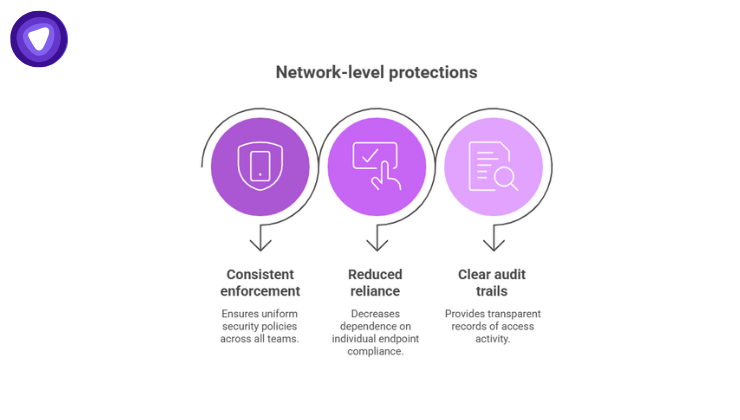
Network-level protections provide:
- Consistent enforcement across teams
- Reduced reliance on endpoint compliance
- Clear audit trails for access activity
Insurers favor controls that simplify verification and limit assumptions. Complex security stacks with overlapping tools often raise concerns rather than confidence.
Preparing for an Insurance Assessment Without Overengineering
The goal is not to impress underwriters with complexity. It is to remove ambiguity.
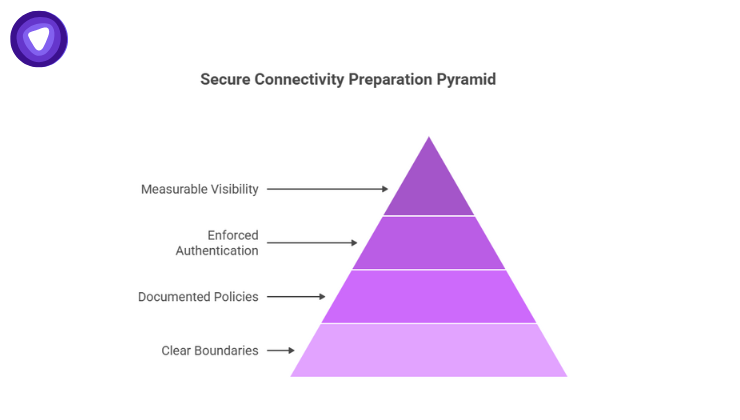
Strong preparation focuses on:
- Clear access boundaries
- Documented remote access policies
- Enforced authentication requirements
- Measurable visibility into network activity
Data breach insurance companies reward clarity, consistency, and enforceability.
Where PureVPN White Label Fits Into This Assessment Landscape?
As insurers place more weight on access control and remote connectivity, organizations are rethinking how they provide secure entry to internal resources.
PureVPN White Label VPN Solution supports this shift by enabling businesses to offer controlled, encrypted remote access under their own brand. It helps establish consistent authentication, fixed access points through Dedicated IP options, and centralized control without exposing broader network infrastructure.
For organizations managing distributed teams or clients, this approach aligns closely with what data breach insurance companies now expect to see during access reviews.
Why Access Architecture Is Becoming an Insurance Decision?
The insurance company data breach 2025 pattern shows a clear trend. Breaches are less about exotic exploits and more about basic access failures that scale fast.
Insurers no longer ask whether security tools exist. They assess whether access is contained, visible, and enforceable under pressure.
Data breach insurance companies have shifted from trust-based underwriting to evidence-based risk modeling. Organizations that adapt to this reality face fewer surprises, lower premiums, and stronger claims outcomes.
Security assessments now shape insurance decisions as much as insurance shapes security decisions. Those who understand that relationship early gain an advantage that extends far beyond coverage.


