- Align with Risk: Start SOC planning by matching security goals to your organization’s specific business risks.
- Build in Phases: Define the SOC mission, design flexible architecture, and hire analysts in tiered roles.
- Smart Log Collection: Gather logs from identity, endpoint, network, and cloud sources—while avoiding excessive noise.
- Automate Early: Use SIEM, SOAR, and EDR from the start to handle repetitive alerts efficiently.
- Measure & Improve: Track KPIs like MTTD, MTTR, and alert accuracy to guide operational improvements.
- Scale Wisely: Consider managed SOC services or hybrid models to expand without overwhelming resources.
- Secure Remote Ops: A white-label VPN can encrypt analyst access, protect investigation environments, and safeguard SOC infrastructure.
Cybersecurity isn’t static. As a business grows, so do the attack surfaces, compliance obligations, and customer expectations for data protection. That’s why many companies choose to build SOC capabilities that aren’t just functional today, but ready to expand tomorrow.
This isn’t about throwing money at the biggest tech stack you can find. A scalable SOC is built with clear priorities, smart staffing, and a roadmap that matches your business trajectory. In this guide, you’ll learn exactly how to set up a Security Operations Center that starts lean, stays effective, and grows with your needs.
How to Build a SOC That Scales
Start lean and iterate. Define your mission, instrument what matters, and expand automation and coverage as the business grows.
- Set mission & scope: what you protect, hours, and services.
- Flexible architecture: cloud-ready data lake + SIEM, SOAR, EDR integrations.
- Tiered staffing: Tier-1/2/3 analysts with clear escalation paths.
- Playbooks: documented, automatable IR runbooks for common incidents.
- Visibility: ingest cloud, identity, endpoint, network, and SaaS logs.
- KPIs/OKRs: track MTTD, MTTR, alert quality, coverage, and false-positive rate.
- Continuous improvement: monthly reviews, purple-team exercises, tuning & automation.
Understanding the Basics — What is SOC?
A SOC, or Security Operations Center, is the nerve center of an organization’s cybersecurity defense. It’s where teams monitor, detect, investigate, and respond to security threats around the clock.
SOC full form: Security Operations Center.
When building a SOC, it’s important to understand that it’s not just a room with screens; it’s a combination of people, processes, and technology working in harmony. This is why businesses serious about cybersecurity don’t just “set up a SOC”; they design one that’s operationally sustainable.
See how it fits
- Integrates with SIEM, SOAR, and EDR workflows
- Individual VPN profiles for analysts (least privilege)
- Geo-distributed gateways for low-latency access
- Brandable VPN apps with SSO support
Why Scalability Matters in SOC Cybersecurity?
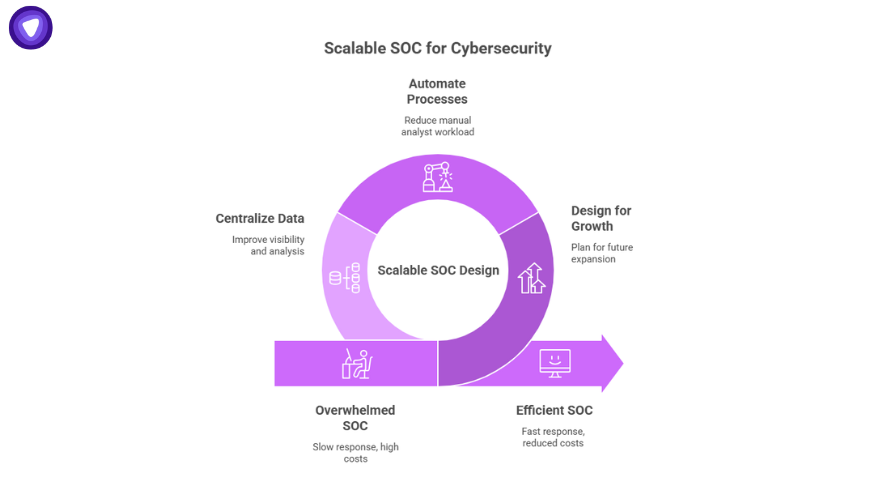
A small business may only need a handful of analysts and basic threat monitoring. A year later, after a product launch or acquisition, those same teams may face 5x the log volume, more regulatory pressure, and new attack vectors.
If you didn’t design your SOC for growth from day one, you risk:
- Overwhelmed analysts.
- Slower response times.
- Increased false positives.
- Higher security incident costs.
The cost of re-engineering later is always higher than starting with a scalable design.
Step-by-Step Build SOC Guide
The following roadmap is designed to work for startups through large enterprises, so whether you’re building a SOC from scratch or expanding an existing setup, you can use it as a framework.
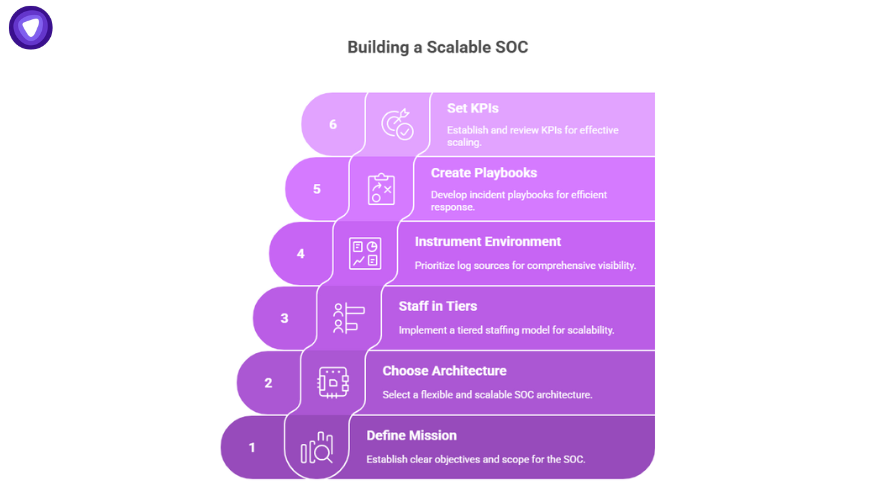
Phase 1: Define Your SOC Mission and Scope
Before tools, before headcount, you need clarity:
- What business assets are you protecting?
- What regulations must you comply with?
- What’s your acceptable risk tolerance?
Documenting this will prevent over-engineering in the early days and allow you to align SOC priorities with the company’s actual needs.
Phase 2: Choose Your Architecture
When designing and building security operations center capabilities, your architecture needs to be flexible. Consider:
- Centralized vs. distributed SOC setups.
- Cloud-native vs. on-premises log ingestion.
Integration points with identity, endpoint, and cloud platforms.
Even if you start with a single analyst station, use platforms that can scale to multiple analysts and integrate with more advanced tools later.
Phase 3: Staff in Tiers
A scalable SOC typically uses a tiered staffing model:
| Tier | Role | Focus |
| Tier 1 | SOC Analyst | Monitor alerts, initial triage |
| Tier 2 | Incident Responder | Deep investigation, containment |
| Tier 3 | Threat Hunter | Proactive threat detection |
| Engineering | SOC Engineer | Tool management, automation |
Starting lean? One person may wear multiple hats, but the structure should still exist so you can plug in more specialists as you grow.
Phase 4: Instrument Your Environment
Your SOC is only as good as its visibility. Prioritize log sources in this order:
- Identity systems (SSO, IAM).
- Endpoint detection & response (EDR).
- Cloud service logs.
- Network traffic.
This ensures your analysts see the full picture before an attacker can move laterally.
Phase 5: Create Incident Playbooks
Playbooks make your SOC efficient by giving analysts a clear “if X then Y” guide. Examples:
- Phishing email detected → Quarantine → Alert user → Update filters.
- Suspicious login from abroad → MFA challenge → Session termination → Review logs.
Automate playbooks with SOAR once you have a stable detection baseline.
Phase 6: Set KPIs and Review Monthly
To ensure you’re scaling effectively, track:
- MTTD (Mean Time to Detect).
- MTTR (Mean Time to Respond).
- False Positive Rate.
- Detection Coverage (percentage of assets monitored).
Review these every month and adjust resources or processes accordingly.
Five Tips For Building A More Efficient SOC
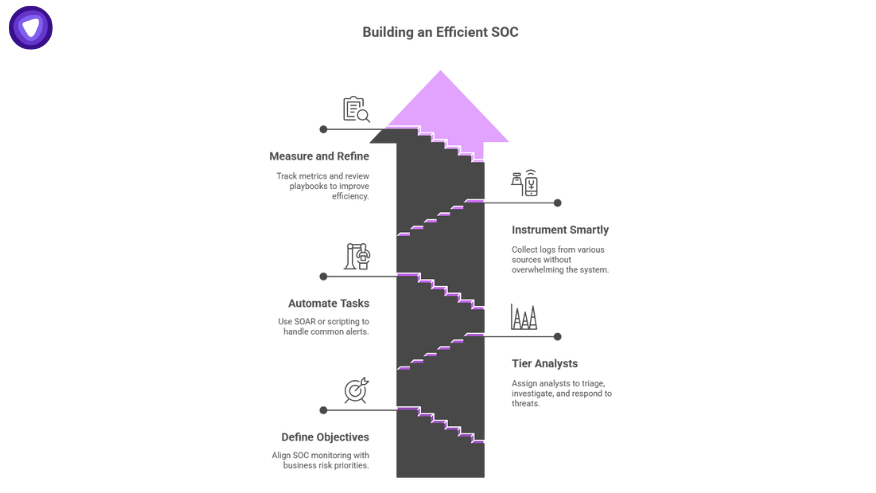
- Define clear objectives – Align SOC monitoring and response to business risk priorities.
- Tier your analysts – Assign Tier 1 for triage, Tier 2 for investigation, Tier 3 for threat hunting and response.
- Automate repeatable tasks – Use SOAR or scripting to handle common alerts.
- Instrument widely but smartly – Collect logs from identity, endpoint, cloud, and network without drowning in noise.
- Measure and refine – Track MTTD, MTTR, and false positives; review playbooks monthly.
Cost Considerations — How Much Does It Cost to Build a SOC?
SOC costs vary widely. Here’s a baseline:
| SOC Size | Staffing | Tools | Annual Cost Range |
| Small | 3–5 staff | Basic SIEM + EDR | $500k–$1M |
| Medium | 10–15 staff | SIEM + SOAR + Threat Intel | $2M–$5M |
| Large | 20+ staff | Full automation + MDR partners | $7M+ |
Starting small and scaling up is almost always more cost-effective than trying to build the “perfect” SOC from day one.
In-House SOC vs Managed SOC — Which Scales Better?
| Factor | In-House SOC | Managed SOC |
| Control | High | Moderate |
| Cost | High upfront | Predictable subscription |
| Expertise | Dependent on hires | Included in service |
| Scalability | Depends on hiring | Faster via provider capacity |
If you lack in-house expertise, a hybrid model (small in-house team + managed SOC) can be the most scalable.
Scaling Without Chaos
How a fintech startup scaled its SOC from 3 analysts to enterprise-grade operations—without doubling headcount.
Context & Challenge
A fintech startup launched with a 3-person SOC using an open-source SIEM. Within twelve months, user growth drove a 400% increase in log volume, overwhelming pipelines and analysts.
What They Did
- Migrated to a cloud-native SIEM with auto-scaling storage & compute.
- Brought in a Tier-2 contractor for surge investigations and complex triage.
- Automated repetitive alerts and enrichments with SOAR playbooks.
- Integrated a PureVPN White Label VPN into the SOC workflow to:
- Provide encrypted, least-privilege remote access for analysts.
- Secure cross-region log collection and tooling access.
- Reduce exposure when connecting to sensitive investigation environments.
Outcomes
By following the “Build a SOC That Scales” approach, the team delivered measurable improvements while keeping costs predictable.
Result: 30% faster incident resolution without doubling headcount, plus a measurable drop in network-based threats targeting SOC infrastructure.
Key Takeaways
- Start lean, choose cloud-ready tools, and automate early—then add people where it matters most.
- Use Tier-2/contract capacity to absorb surges instead of permanent over-staffing.
- Embed a white-label VPN to secure analyst access and sensitive investigative workflows at scale.
Building a SOC That Grows With You
A SOC is not a one-time project; it’s a living function. By starting with clear priorities, building scalable architecture, and measuring performance regularly, you avoid the expensive pitfalls of re-engineering later.
For businesses looking to protect their data, meet compliance, and scale security without unnecessary complexity, PureVPN’s White Label solutions can help. Our secure infrastructure can integrate into your SOC to provide encrypted remote access, threat visibility, and operational efficiency, all under your brand.


