Walk into any enterprise IT war room in 2025 and you’ll hear the same concern: “If our Salesforce instance is compromised, how fast can we respond?”
That fear isn’t theoretical anymore. In August, attackers quietly moved through trusted integrations and turned a routine SaaS connection into a wide-scale data exposure. The incident forced CISOs and compliance teams to rethink the entire idea of what a “secure” Salesforce deployment means.
This guide breaks down the Salesforce instance compromise story, why it happened, what data was exposed, and most importantly, what business leaders should do to protect themselves right now.
- Incident: Attackers stole OAuth tokens from Salesloft Drift to access Salesforce orgs (Aug 2025).
- Data Exposed: Contact info, licensing details, and risky support case text (sometimes containing secrets).
- Salesforce Impact: Core platform not hacked — compromise came via integrations.
- Attribution: Mandiant assisted; UNC6395 identified as likely threat actor.
- First Steps: Revoke tokens, rotate secrets, audit logs, and notify regulators if required.
- Lesson: Integrations expand your attack surface — treat them like sensitive credentials.
What Exactly Happened?
The Salesforce breach wasn’t a direct exploit of Salesforce servers. Instead, hackers compromised Salesforce instances by stealing OAuth tokens from Salesloft Drift, a sales engagement app connected to Salesforce. With those tokens, attackers accessed customer Salesforce orgs, ran queries, and in many cases pulled out contact records and support case data.
So when headlines screamed “Hackers Compromised Salesforce,” the reality was more nuanced. Salesforce itself wasn’t “hacked.” Instead, the compromise came through a trusted door left unlocked.
Timeline of the Breach
Timeline of the Breach
OAuth tokens abused to access Salesforce
Compromised OAuth & refresh tokens tied to Salesloft’s Drift app were used to run queries in Salesforce. In many cases, jobs were deleted afterward to hide activity.
Drift Email → limited Google Workspace access
Drift Email tokens accessed a small number of Workspace mailboxes in tenants that had integrated Drift Email. Workspace itself wasn’t compromised.
Salesforce & Salesloft revoke Drift tokens
Platform-wide revocation reduced attacker persistence across connected orgs. Tenants relying on Drift were prompted to re-authorize or replace integrations.
Salesforce disables Drift; Salesloft suspended
Salesforce fully disabled the Drift connection and later suspended Salesloft integrations pending investigation, impacting even tenants that never noticed Drift.
To understand what went wrong, it helps to line up the dates:
- Aug 8–18, 2025 → Attackers actively used stolen Drift tokens to query Salesforce instances.
- Aug 9, 2025 → Drift Email tokens exposed a handful of Google Workspace mailboxes linked through the app. Workspace wasn’t breached directly.
- Aug 20, 2025 → Salesforce revoked all Drift OAuth tokens at once.
- Aug 28, 2025 → Salesforce formally disabled Drift and Salesloft integrations across all tenants.
- Aftermath → Forensics firms, including Mandiant, were brought in to investigate attribution and assist victims.
Attribution is still debated. Some reports tied activity to UNC6395, while others speculated about ShinyHunters. Regardless, the tactics were clear: attackers deleted Salesforce jobs after exfiltration to hide their trail.
What Data Was Exposed?
The exposed data varied across organizations, but three buckets stand out. Expand each to see concrete risks and real-world examples.
- Examples: Names, job titles, phone numbers, business emails.
- Risk: Highly tailored spear-phishing & social-engineering campaigns (e.g., fake “account verification” emails targeting specific roles/regions).
- Tip: Add role-based anti-phishing training; enable DMARC, DKIM, SPF; require verbal/Slack back-channel verification for finance/IT requests.
- Examples: SKU names, usage tiers, product entitlements, renewal dates.
- Risk: Impersonation of account managers; fraudulent renewal/up-sell invoices aligned to your exact tier and renewal window.
- Tip: Enforce vendor-of-record allowlists; route all renewals through a single procurement mailbox; require PO numbers & portal-based payment only.
- Why it’s most dangerous: Tickets sometimes include plain-text credentials, API keys, and cloud tokens pasted by employees.
- Risk: Direct account takeovers, lateral movement into cloud systems, persistence via new tokens/refresh keys.
- Compliance angle: Turns the Salesforce/Drift incident into a compliance headache—secrets outside approved vaults.
- Tip: Block secrets in tickets with DLP; use vault links (expiring); rotate any keys found via regex hunts (e.g.,
AKIA,client_secret, JWT formats).
How Hackers Compromised Salesforce Instances?
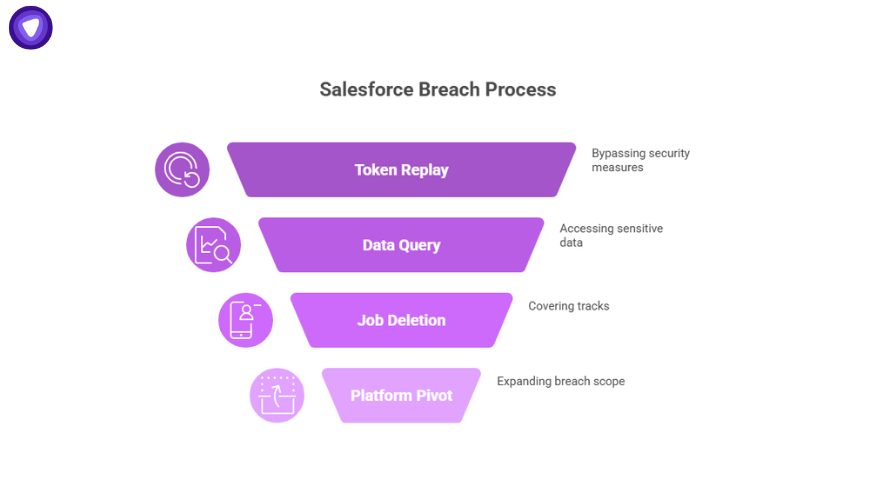
The breach shows how attackers chain together weak links:
- Step 1: Steal OAuth tokens from the Salesloft Drift integration.
- Step 2: Replay tokens to Salesforce APIs. Since OAuth bypasses MFA, attackers looked like legitimate apps.
- Step 3: Query data using SOQL or bulk API calls.
- Step 4: Delete jobs in Salesforce to erase traces of exfiltration.
- Step 5: Pivot using secrets found in support cases into other cloud platforms.
In short: hackers compromised Salesforce instance data by abusing trust, not breaking crypto.
Step-by-Step Response Guide
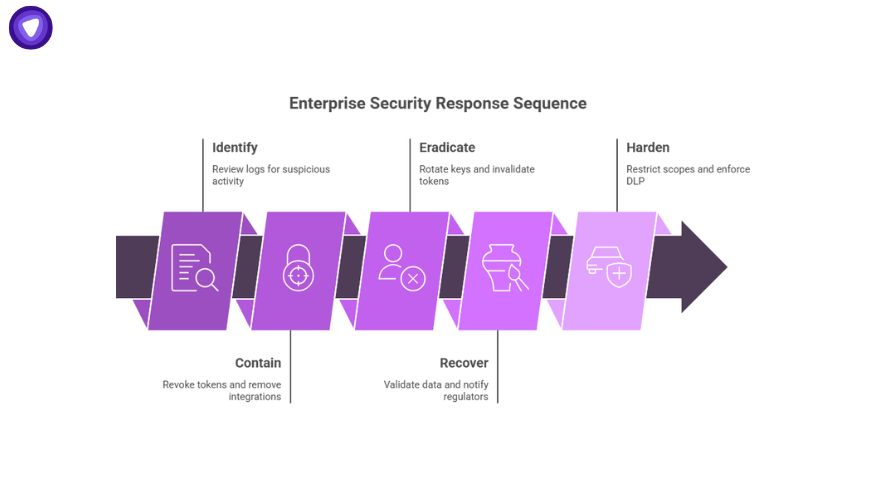
So what should an enterprise do the moment they suspect compromise? Here’s a practical playbook.
1. Identify
- Review Salesforce Event Monitoring logs for Aug 8–18.
- Look for unusual Connected App authorizations, bulk queries, and deleted jobs.
- Search support case text for sensitive strings like AKIA, password=, or client_secret.
2. Contain
- Revoke all Salesloft login tokens immediately.
- Remove Drift and Salesloft integrations until confirmed safe.
3. Eradicate
- Rotate any API keys or secrets exposed in support cases.
- Invalidate refresh tokens that may have been minted during compromise.
4. Recover
- Validate customer data integrity.
- Notify regulators if personal information is involved.
- Launch phishing awareness campaigns to warn employees and customers.
5. Harden
- Restrict OAuth scopes to least privilege.
- Apply Connected App IP restrictions.
- Enforce stronger DLP on ticketing systems to prevent credentials from being pasted in.
Vendor Roles and Integrations
Many companies asked: “Is Salesloft owned by Salesforce?” The answer is no. Salesloft is an independent sales engagement platform. But because it integrates deeply with Salesforce, its compromise became Salesforce’s problem too.
Salesloft Drift, specifically, was the weak link here. Its OAuth tokens were abused to gain access. The fact that Salesloft login could cascade into Salesforce compromise shows how fragile supply-chain security really is.
Mandiant’s role was to provide incident response muscle after the breach, helping organizations trace how far attackers moved and what secrets were taken.
Why Timing Made This Worse?
The incident also landed at a rough moment: Salesforce layoffs had already hit headlines, raising concerns about whether internal security and monitoring resources were stretched thin. Fair or not, perception matters. When a Salesforce breach story drops alongside layoffs, customers worry about vendor focus and stability.
Long-Term Lessons for Enterprises
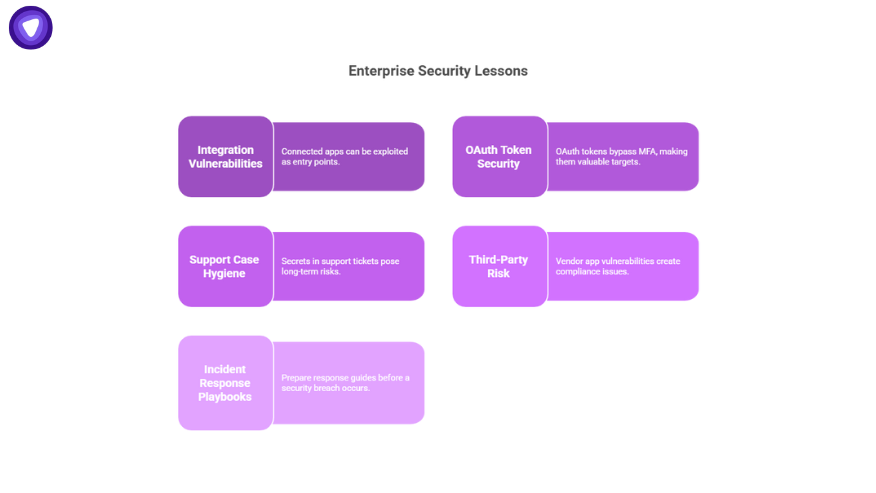
- Integrations are part of your attack surface. Every connected app is a potential doorway.
- OAuth tokens bypass MFA. That makes them gold for attackers. Treat them like credentials, not “just tokens.”
- Support case hygiene matters. Secrets in tickets create downstream risk for years.
- Third-party risk is compliance risk. GDPR and CCPA obligations apply even when the weak link is a vendor app.
- Prepare playbooks now. Don’t build your response guide during the breach.
How to Harden Against the Next Drift?
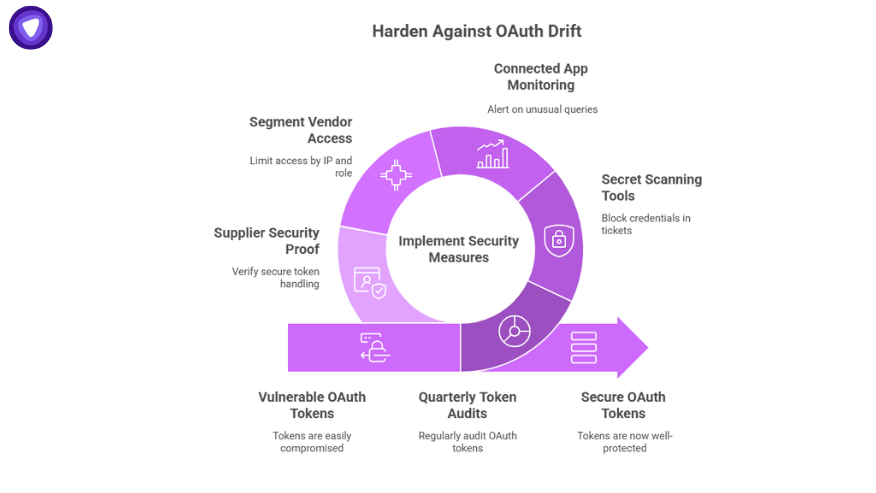
- Run quarterly OAuth token audits.
- Use secret-scanning tools to block credentials in tickets.
- Deploy Connected App monitoring with alerting for unusual queries.
- Segment vendor access by IP and role.
- Push suppliers to prove they can handle tokens securely.
Closing the Gaps With A VPN Layer
VPN ROI Calculator
ere’s what often gets ignored in post-mortems: most EMM and SaaS tools focus on data at rest and application control. But once data leaves the device, it’s only as secure as the connection.
That’s where PureVPN White Label comes in. For MSPs and resellers:
- Offer per-app or full-device VPN integrations alongside Salesforce and mobility solutions.
- Provide encryption for data in transit, closing compliance gaps left by SaaS vendors.
- Help clients tick off controls for HIPAA, ISO 27001, GDPR, and PCI DSS.
- Build recurring revenue streams by bundling VPN with compliance services.
Final Takeaway
The Salesforce instance compromise showed enterprises that trust in SaaS integrations can be dangerous. Attackers don’t need to break into Salesforce directly if they can steal a vendor’s tokens.
For businesses, the lesson is straightforward: treat integrations as critical infrastructure, build incident response muscle in advance, and secure data in transit with tools like PureVPN White Label. Doing so turns a chaotic breach story into proof of resilience—and a chance to keep trust intact when others lose it.


