Connectivity gaps break teams. Dead spots in an office, unstable links on a remote site — the moment people can’t get online, productivity tanks. That’s why the idea of a mesh net is more relevant than ever. Instead of relying on a single router or access point, a mesh net spreads traffic across multiple nodes that talk to each other. It’s simple in theory, but when you get into real deployments — especially for remote teams or rugged sites — you see the flaws. Poor setup, weak security, and zero fallback planning turn a good idea into a support nightmare.
This guide explains what a mesh net really is, how a mesh network works, and what you need to do to secure it for serious business use. If you run remote teams, work in challenging regions, or plan to resell connectivity services, these lessons will save you time, money, and a lot of angry tickets.
What Is a Mesh Net?
A mesh net (or mesh network) is a network where every device (node) connects directly with the others around it. There’s no single hub that routes all the traffic. Instead, your data jumps from one point to another, picking the best path in real time. This approach means your connection doesn’t drop just because one router goes offline. If a node fails, your traffic reroutes itself. That’s the promise: better coverage, more reliability.
Mesh vs. Star Topology
You see the term “mesh net” everywhere now, mostly in the consumer WiFi world. Search for a mesh network router on Amazon and you’ll find pages of TP-Link mesh kits. But mesh isn’t just for homes. It’s a core idea behind IoT, rural broadband rollouts, and even temporary networks set up in disaster zones. The topology — how nodes connect — is what makes a mesh net special. Unlike a star topology (one central point), a mesh network topology is distributed, self-healing, and more flexible.
Types of Mesh Nets
Which Mesh Net Fits Your Needs?
Mesh networks come in different forms, each suited for specific use cases and scalability needs.
1. Full Mesh Network
In a full mesh network, every device links to all the others. This setup is highly reliable because if one connection breaks, data can still flow through other routes. That’s why it’s used in critical systems like military communications, where downtime isn’t an option. But there’s a downside. As you add more devices, the number of connections increases fast, making the network complex and costly to set up and manage.
2. Partial Mesh Network
Partial mesh networks are often used in businesses because they balance cost and reliability. In this setup, only important devices connect directly to each other. Other devices link through these main nodes.
A common example is in corporate branch networks. The main office has direct connections to key locations, while smaller branches connect through the main office. This way, the network stays reliable without the high cost and complexity of a full mesh.
3. Wireless Mesh Network
Wireless mesh networks use Wi-Fi or radio signals to connect devices. They’re popular in urban settings for public Wi-Fi coverage. For remote teams, setting up a wireless mesh means employees in a large building or campus can move freely without losing connection. Google’s Sidewalk Labs once piloted a wireless mesh network to offer city-wide internet.
4. Wired Mesh Network
Wired mesh networks use Ethernet or fiber-optic cables. Though less flexible than wireless, they offer higher speed and reliability. Financial institutions often use wired mesh networks to ensure low-latency and high-security communication between trading desks.
How Does a Mesh Network Work?
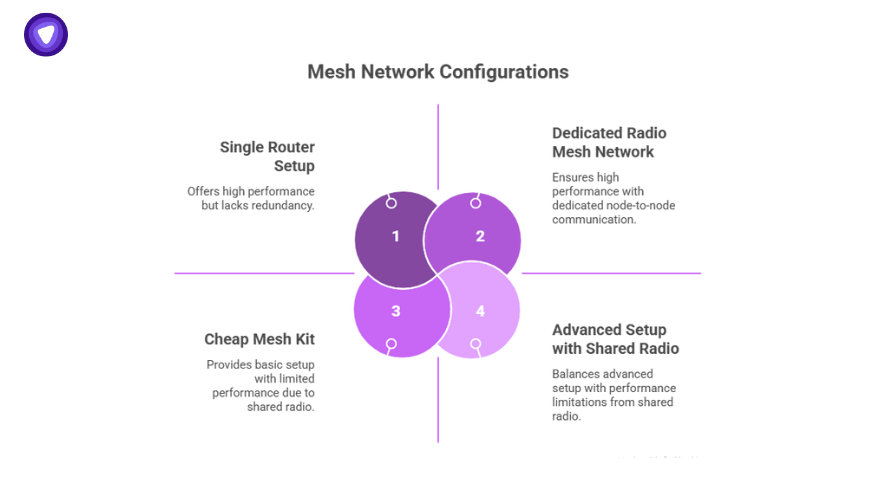
The main idea is redundancy. Each node can act as a relay. A good mesh network setup means that if your main node goes down, another picks up the traffic. This is different from a single router setup, where if that box dies, your whole site goes offline.
A mesh network router is just a smart node — often they’re all identical hardware-wise. Software decides which node acts as a gateway to the wider internet. Behind the scenes, the routing protocols keep score of link quality. They find the fastest path for your data, reroute if a link degrades, and constantly adapt as devices join or leave.
Some advanced setups use a dedicated mesh network radio for node-to-node chatter, which means less congestion on your regular WiFi channels. That’s what you see in pro-grade mesh network WiFi hardware. For bigger teams or pop-up deployments, understanding this difference is key. Cheap mesh kits use the same radio for client and node traffic, which limits performance.
Mesh Net Use Cases: It’s More Than Home WiFi
Most people associate mesh with fixing WiFi dead zones at home — think mesh network TP-Link kits or “mesh network Amazon” best-sellers. But a robust mesh net can do much more:
All these examples rely on the same idea: no single point of failure, easy scaling, and self-healing connections. But they only work well when the mesh is set up correctly and secured properly.
Mesh Network Setup: Basics Done Right
Mesh Network Setup Health Check
- Node placement mapped
- Backhaul tested
- Separate admin VLAN configured
- Firmware up to date
If you’re rolling out a mesh network for a business site or remote crew, skip the consumer shortcut of “plug it in and forget it.” Here’s what to keep in mind:
- Node Placement: The biggest mistake? Thinking more nodes are always better. Too many nodes close together create interference and drop speeds.
- Backhaul Matters: Some higher-end mesh systems use wired backhaul between nodes, which drastically improves performance. If you can run cable, do it.
- Separate Admin Network: Always keep your management traffic on its own VLAN. Don’t mix it with user data.
For smaller sites, a mesh network setup can be simple. For larger areas, you’ll want pro-grade gear, possibly multiple bands, and someone watching node health.
Real-World Security Risks in a Mesh Net
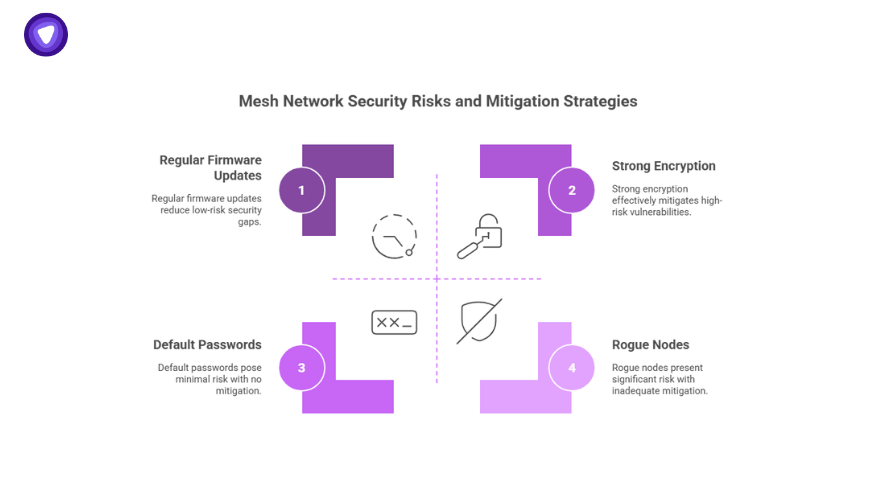
Here’s the side of mesh networking that most glossy router guides skip. Every node is an entry point. If someone compromises one, they can listen to traffic, attack the next hop, or pivot deeper into your network.
Common problems:
- Weak encryption between nodes.
- Default passwords that never get changed.
- Rogue nodes pretending to be trusted relays.
- Outdated firmware that leaves backdoors open.
A mesh network communication plan means you build zero-trust assumptions into every node. Authenticate, encrypt, monitor. Don’t assume the mesh topology alone keeps you safe.
How to Secure Mesh Networks for Remote Teams?
To secure mesh networks for remote teams, start with strong encryption protocols like WPA3. This protects data as it travels between nodes, safeguarding against man-in-the-middle attacks.
Mesh Net Self-Check
Tick what you already do — see your security score grow.
See PureVPN White Label →
Integrate A White Label VPN
One effective method of mesh network protection is a White Label VPN. It protects private information from hackers and prying eyes by encrypting all data traveling over the network. For example, remote developers accessing a company’s source code repository can use a White Label VPN to prevent data leaks and unauthorized access.
Use Strong Passwords
Every node in a mesh network can be an entry point for attackers. Implementing complex passwords and changing default credentials on all devices is critical. A real-world breach occurred when default passwords on IoT devices were exploited to create botnets like Mirai.
Enable Two-Factor Authentication (2FA)
Adding 2FA provides an extra security layer. Even if a hacker gains access to a password, they’ll need a second form of verification. For example, using a hardware token like YubiKey with 2FA can significantly reduce unauthorized access risks.
Regular Software Updates
Outdated firmware can leave mesh networks vulnerable. A well-known exploit, KRACK (Key Reinstallation Attack), targeted WPA2 vulnerabilities, affecting millions of Wi-Fi devices. Regular updates patch such vulnerabilities and keep the network secure.
Use Firewalls and Intrusion Detection Systems (IDS)
Implementing both hardware and software firewalls helps filter malicious traffic. Pairing this with IDS can help detect suspicious activities in real-time. In one case, a financial firm detected a slow data exfiltration attempt using IDS, preventing significant data loss.
Do You Still Need a VPN?
Short answer: Yes. A mesh net solves the coverage and redundancy problem. It doesn’t fully solve your encryption or privacy problem, especially if you’re sending business-critical data over multiple hops. A trusted VPN on top locks it down end-to-end.
Mesh Net Alone vs. Mesh Net with VPN
| Aspect | Mesh Net Alone | Mesh Net with VPN |
| Coverage | Wide | Wide |
| Self-Healing | Yes | Yes |
| Encryption | Varies by device setup | Encrypted end-to-end |
| Privacy Protection | Limited if node is breached | Stronger protection |
| Good For | General connectivity | Secure team comms, compliance |
Stay Connected & Learn With Us
Join our growing community and connect with peers who build secure networks and resell privacy tools worldwide.
Why Your Mesh Net Needs a Strong VPN Backbone?
A good mesh net gives your teams better coverage. But a secure mesh net keeps your data and business reputation intact when you’re working in regions with high risk or poor infrastructure. PureVPN’s White Label helps you sell branded, reliable VPN overlays that sit on top of any mesh network. That means you can deliver encrypted tunnels that protect every hop, whether your users are in an office or on a remote field site with a rugged mesh network setup.
With region-aware routing, fast exit pools, and tested protocols, your brand doesn’t just offer coverage. It offers trust when your clients need it most.
Final Takeaway
A mesh net is only as good as the security you build around it. Coverage and self-healing are great. But without encryption, device trust, and smart tunneling, you’re leaving gaps that can turn into real costs.
Ready to run a network that holds up under pressure? See how PureVPN White Label gives you the backbone to keep remote teams connected, private, and protected — on any mesh net they deploy.


