How to Configure EdgeRouter VPN Client for Secure Remote Access?
For many businesses, the Ubiquiti EdgeRouter is a workhorse that runs quietly behind the scenes. It’s not just a firewall or router; it can connect entire subnets to a secure VPN. That’s where your EdgeRouter VPN client comes in.
When you need your branch office, warehouse, or remote site to connect securely to an upstream VPN, your EdgeRouter acts as a dedicated client VPN. It handles the encryption and routing at the edge, not your user’s laptop.
So why do serious admins still pick this? Two reasons: control and uptime. When you control the tunnel from the router, you decide what traffic goes through it. You handle policy-based routing for VoIP, IoT, or failover. And when the tunnel drops, you see it fast — because your logs and status are in your hands.
Understanding EdgeRouter VPN Client vs. Server
A lot of Ubiquiti guides focus on server setups. But the EdgeRouter client VPN is just as important, especially for remote workers or branch sites.
In client mode, your Ubiquiti Edgerouter VPN client makes an outbound tunnel to your main VPN server. All the traffic you define — a single device, a VLAN, or the whole subnet — can flow through that secure link.
Use case: your main HQ runs an OpenVPN server. Your EdgeRouter X at a branch connects back using the Edgerouter x VPN client setup. Employees at the branch don’t need to install extra apps. They just connect devices to the LAN, and your policy routing does the rest.
EdgeRouter VPN Client Requirements & Prep
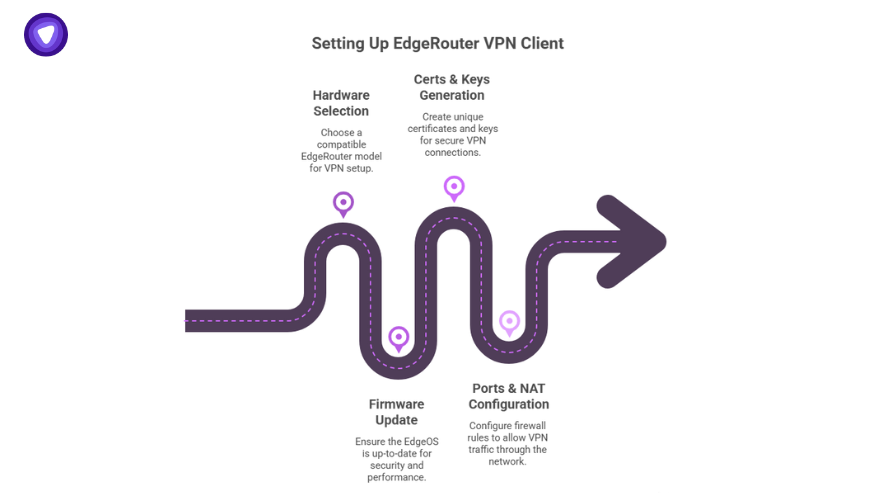
Before you start pushing config commands, get the basics right:
- Hardware — EdgeRouter X, EdgeRouter 4, or Ubiquiti EdgeRouter Lite all handle OpenVPN and WireGuard well with EdgeOS.
- Firmware — Keep EdgeOS updated. Vulnerabilities pop up fast.
- Valid Certs & Keys — Don’t use default example certs. Generate your own.
- Ports & NAT — Make sure your firewall rules won’t block your outbound tunnel.
And remember: unlike many cheap routers, Ubiquiti’s EdgeRouter VPN client download is built-in. No extra software. Just configure and test.
Choosing Your VPN Protocol on EdgeRouter
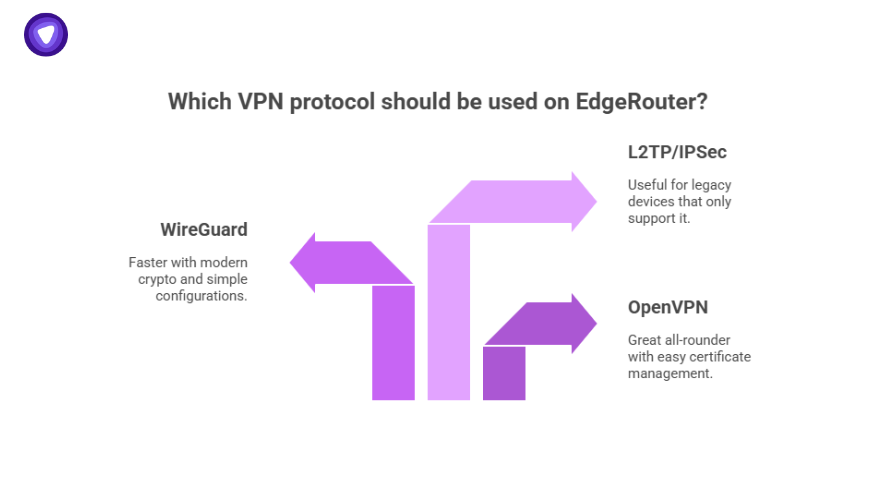
OpenVPN is still the standard, but WireGuard is winning fans for speed. L2TP/IPSec still works for legacy fallback.
Quick rule of thumb:
- OpenVPN: Great all-rounder, easy cert management.
- WireGuard: Faster, modern crypto, simple configs.
- L2TP/IPSec: Older but handy if some devices only support it.
Example: an Edgerouter Wireguard tunnel as primary with OpenVPN as a fallback. Some admins run both for redundancy.
Step-by-Step: EdgeRouter OpenVPN Client Setup
Most real-world setups use the CLI. Here’s a clean, tested flow:
1. Add the OpenVPN Interface
set interfaces openvpn vtun0 mode client set interfaces openvpn vtun0 remote-host vpn.example.com set interfaces openvpn vtun0 port 1194 set interfaces openvpn vtun0 tls ca-cert-file /config/auth/ca.crt set interfaces openvpn vtun0 tls cert-file /config/auth/client.crt set interfaces openvpn vtun0 tls key-file /config/auth/client.key
Adjust paths and filenames to match your EdgeRouter OpenVPN client certs.
2. NAT Masquerade & Firewall Rules
set service nat rule 5000 description 'NAT VPN' set service nat rule 5000 outbound-interface vtun0 set service nat rule 5000 type masquerade
Allow forwarding in your firewall. If you use the EdgeRouter VPN setup GUI, you’ll find these under Firewall/NAT.
3. Add Routes
Route all or some traffic:
set protocols static route 0.0.0.0/0 next-hop vtun0
Or do policy-based routing if you only want certain devices. See below.
| VLAN | Subnet | Next Hop | Route Example |
|---|---|---|---|
| VoIP | 192.168.10.0/24 | vtun0 | set firewall modify SOURCE_ROUTE rule 10 ... |
| IoT | 192.168.20.0/24 | ISP | set protocols static route 192.168.20.0/24 next-hop ISP |
| Guest | 192.168.30.0/24 | vtun0 | set firewall modify SOURCE_ROUTE rule 30 ... |
4. Commit & Verify
commit save show interfaces openvpn
Always check your logs for handshake errors. This is where most “my EdgeRouter VPN client won’t connect” issues pop up.
Advanced: Policy-Based Routing & Failover
Policy-Based Routing — Route only certain VLANs, IPs, or subnets over VPN. Everyone else uses your ISP line.
set firewall modify SOURCE_ROUTE rule 10 description 'VPN VLAN 10' set firewall modify SOURCE_ROUTE rule 10 source address 192.168.10.0/24 set firewall modify SOURCE_ROUTE rule 10 action modify set firewall modify SOURCE_ROUTE rule 10 modify table main
Multi-VPN Profiles & Failover
- Run multiple profiles. If OpenVPN drops, fallback to WireGuard.
- Keep certs and keys rotated for both.
- Test failover by dropping a tunnel and checking route status.
DNS & Leak Prevention
A sloppy DNS setup leaks your traffic, defeating your entire Ubiquiti Edgerouter VPN client.
- Push custom DNS resolvers:
set service dns forwarding system set service dns forwarding name-server 1.1.1.1 set service dns forwarding name-server 8.8.8.8
- Always run a DNS leak test from a test device. If you see your ISP’s DNS, fix it.
- Rotate keys and certs at least every 6–12 months to stay ahead of exploits.
Setting Up EdgeRouter Site-to-Site VPN
Looking to connect two networks—like HQ and a branch office?
That’s where EdgeRouter site-to-site VPN comes in.
It’s basically the same OpenVPN setup, but you’ll use static routes to reach the remote subnet.
Basic Example:
- Site A subnet: 192.168.10.0/24
- Site B subnet: 192.168.20.0/24
On Site A’s EdgeRouter:
set protocols static route 192.168.20.0/24 next-hop vtun0
On Site B’s router:
set protocols static route 192.168.10.0/24 next-hop vtun0
</script>
And make sure firewall rules allow traffic between those subnets.
Troubleshooting EdgeRouter VPN Client
Why won’t my tunnel come up?
- Check your PSK and certs — 90% of failures are typos or expired certs.
- Use: tail -f /var/log/messages to see real-time errors.
- For stuck tunnels: check NAT-T settings if using IPSec.
- For authentication failures: make sure the CN matches on your cert.
When in doubt, jump on the EdgeRouter VPN client Reddit community for real fixes. Power admins share scripts that save you hours.
Common Errors and Fixes
Here’s what to check when it’s not working:
- No tunnel interface? Check file paths and OVPN config.
- No internet after VPN connects? You forgot to set NAT masquerade or default route.
- VPN won’t connect? Check credentials and verify TLS auth (if needed).
- Slow speed? Check CPU usage or offloading settings.
Always check logs:
cat /tmp/openvpn.log
Protocol Comparison: OpenVPN vs. WireGuard vs. L2TP/IPSec
Compare VPN Protocols
OpenVPN
Speed: Balanced performance with solid encryption. Well-optimized for most use cases.
Security: Mature, widely audited; supports AES-256 and advanced configs.
Setup: Requires certs & keys; some CLI work. Highly flexible.
Best for: Mixed remote workforces, BYOD, multi-device support.
| Protocol | Security | Speed | Setup | Best Use |
| OpenVPN | Strong | Moderate | Medium | General business |
| WireGuard | Very strong | Fast | Easy | Modern mobile use |
| L2TP/IPSec | Moderate | Moderate | Easy | Legacy fallback |
Use Edgerouter x VPN client or Edgerouter 4 VPN for multi-protocol. It keeps your sites up when one tunnel fails.
How Businesses Use EdgeRouter VPN Client?
- Branch Office Tunnel: An Ubiquiti EdgeRouter X VPN client connects a retail store to HQ. Sales data routes securely.
- IoT or CCTV: Only your IoT VLAN hits the VPN; regular traffic goes out the ISP line.
- Mobile Fallback: EdgeRouter VPN client Android scenario: when traveling, your staff use the same upstream VPN your router connects to.
Why Use EdgeRouter with a White-Label VPN?
If you’re serious about reselling VPN access or managing secure remote connections for clients, you already know the value of control at the network edge. Running an EdgeRouter VPN client means your tunnel starts where your devices live, not on a random endpoint. That gives you clean routing, policy controls, and reliable uptime.
But the router alone isn’t your business. You still need an upstream VPN backbone that’s stable, private, and ready to scale. That’s where a PureVPN White Label plan makes sense.
With PureVPN White Label:
- You get pre-tested OpenVPN, WireGuard, or L2TP/IPSec profiles that drop straight into EdgeOS.
- Your team skips weeks of server setup — you start selling secure connections with your branding on day one.
- You control user provisioning, usage caps, and billing — all while your tunnels stay protected with strong certs and fresh IPs.
This is what makes a mature white-label backbone different from stitching together “free” solutions. No stale exit IPs. No sudden blocklists. Just solid infrastructure that keeps your Ubiquiti EdgeRouter VPN client stable.
Stay Connected & Learn With Us
Join our growing community and connect with peers who build secure networks and resell privacy tools worldwide.
Final Thoughts
Getting your EdgeRouter VPN client right isn’t a quick toggle. It’s a real network investment. But once it’s running — paired with a proven white-label platform — you unlock stable site-to-site links, remote access for clients, and a business that grows without daily fires to put out.
Ready to scale smarter?
A properly configured EdgeRouter plus a rock-solid PureVPN White Label backend? That’s the combo that keeps your customers online — and keeps your brand trusted when others fail.