Ask most executives about their cybersecurity posture, and they’ll list firewalls, endpoint detection, and maybe zero-trust architecture. But few will mention the discipline that often decides whether those investments succeed or fail: Operations Security (OPSEC).
So, what is OPSEC in today’s business context? It’s the systematic process of making sure adversaries can’t piece together your secrets from the information you leak every day. A competitor learning about your new product from a supplier invoice, a hacker timing their phishing emails to your CEO’s travel itinerary, or an attacker spotting downtime on your public status page, all of these are OPSEC failures.
Originally a military doctrine, OPSEC is now a pillar of enterprise cybersecurity strategy. This guide explains how OPSEC works, why it matters for modern businesses, and how to integrate it into your security program alongside tools like PureVPN White Label.
- What is OPSEC? A five-step discipline that prevents adversaries from exploiting leaked information by identifying, analyzing, and controlling exposure.
- Why it matters: Poor OPSEC causes cyberattacks, compliance failures, revenue loss, and reputational damage.
- The OPSEC cycle: Identify critical info → Analyze threats → Analyze vulnerabilities → Assess risks → Apply countermeasures.
- Examples: Job postings revealing projects, supplier invoices exposing contracts, executives oversharing travel.
- KPIs: Training coverage, OSINT red-team hit rates, supplier compliance checks.
- Industries: SaaS, ISPs, MSPs, fintech—any sector where sensitive info leaks create competitive or compliance risk.
- PureVPN White Label: Pair OPSEC with encrypted VPN tunnels to secure data-in-transit, enforce vendor controls, and generate revenue.
- Bottom line: OPSEC protects what you share. PureVPN White Label protects how it moves.
What Is OPSEC?
OPSEC, or Operations Security, is a five-step discipline that prevents adversaries from piecing together sensitive information by identifying what must be protected, spotting threats and vulnerabilities, assessing risks, and applying countermeasures.
Unlike many security controls, OPSEC isn’t just about firewalls or encryption; it’s about controlling the clues you give away. Think of it as managing your digital footprint so attackers can’t connect the dots.
OPSEC meaning military: In the defense world, OPSEC ensures enemies cannot infer mission details.
OPSEC cybersecurity: In business, OPSEC reduces risks by protecting sensitive operations such as cloud deployments, vendor relationships, and executive travel.
Example
A SaaS startup hiring “Kubernetes engineers for Project Falcon” might think it’s harmless. But a competitor (or hacker) now knows the project’s codename, stack, and development stage. Without OPSEC, your own recruiting post becomes an intelligence leak.
Why Is OPSEC Important?
OPSEC is important because it protects critical information from unintentional leaks, reducing the risk of cyberattacks, competitive espionage, compliance failures, and reputational damage.
Four Dimensions of Risk
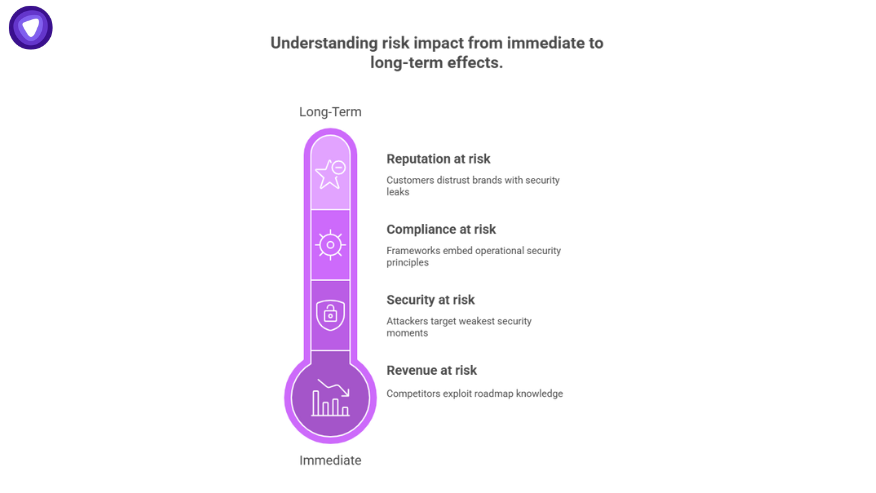
- Revenue at risk: Competitors undercut launches if they know your roadmap.
- Security at risk: Attackers time phishing or ransomware to your weakest moments.
- Compliance at risk: Frameworks like NIST 800-171, CMMC, and ISO 27001 all embed OPSEC principles.
- Reputation at risk: Customers won’t trust a brand that leaks before it secures.
Example
In 2024, several organizations were targeted after suppliers posted project details online. Hackers didn’t break in; they just read what was exposed. That’s why OPSEC is important: it closes the gaps technology alone cannot.
The OPSEC Cycle Explained
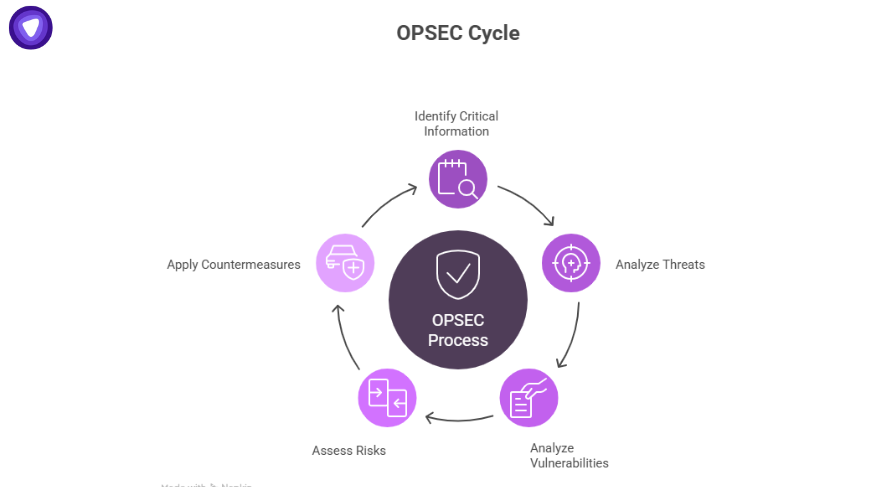
The five steps of OPSEC are: identify critical information, analyze threats, analyze vulnerabilities, assess risks, and apply countermeasures.
Step 1: Identify Critical Information
Every organization should maintain a Critical Information List (CIL). For a fintech, this might include customer PII, trading algorithms, and M&A plans. For an ISP, it could be network diagrams and outage schedules.
Step 2: Analyze Threats
Define who might exploit your information. Competitors? Cybercriminals? Hacktivists? Each threat actor values different types of data.
Step 3: Analyze Vulnerabilities
This is where most organizations stumble. OPSEC vulnerabilities are the weak points adversaries can observe:
- Metadata in documents
- Screenshots on Slack or LinkedIn
- Open cloud buckets
- Public code repositories
Step 4: Assess Risks
Rank exposures by likelihood and impact. A PDF with geotagged metadata might be low risk; a public outage notice could be high risk if attackers can exploit it.
Step 5: Apply Countermeasures
Countermeasures come in three categories:
- Technical: VPNs, DLP tools, access policies
- Procedural: Press release reviews, supplier NDA enforcement
- Behavioral: Staff training on what not to share
How Attackers Exploit OPSEC Failures (OSINT in Action)
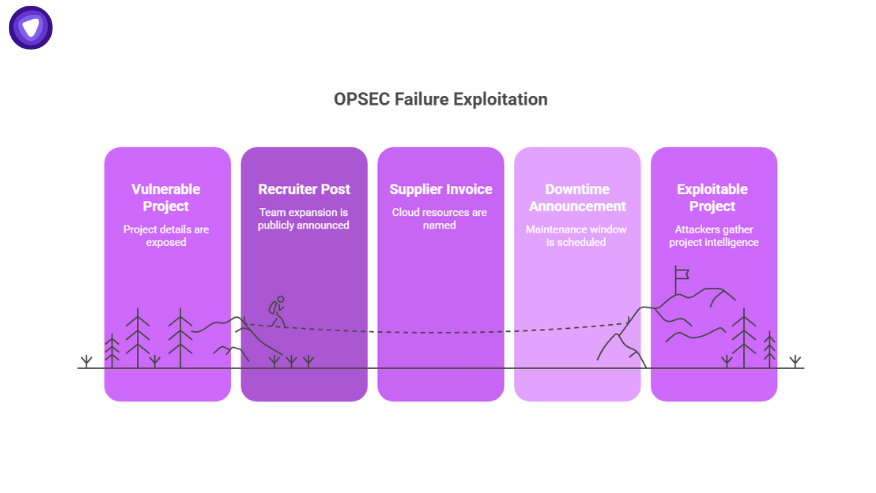
Most guides stop at theory. Here’s how it looks in practice:
- A recruiter posts: “We’re expanding our Falcon project team.”
- A supplier uploads an invoice naming Falcon cloud resources.
- The company’s status page announces downtime for Falcon next Tuesday.
From three separate sources, an adversary learns:
- Codename: Falcon
- Tech stack: Kubernetes
- Exploit window: next Tuesday
This is open-source intelligence (OSINT) in action and why OPSEC must be embedded across HR, Legal, Comms, and IT, not just Security.
OPSEC in Cybersecurity Frameworks
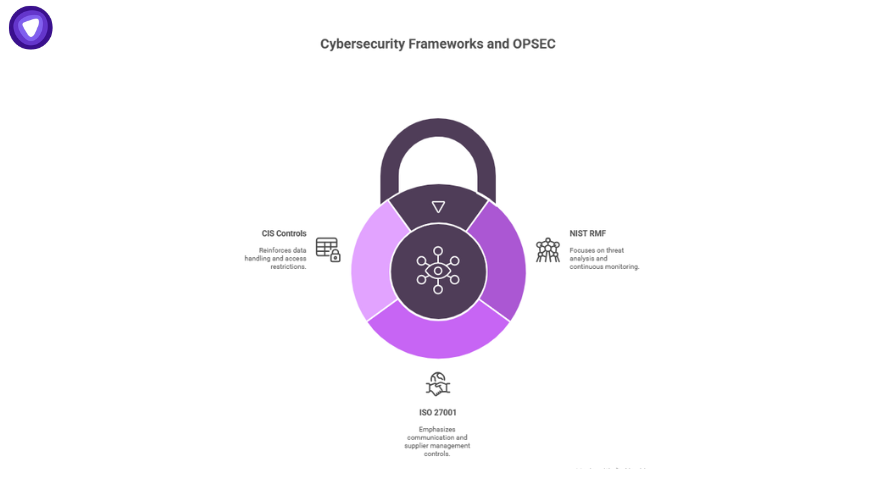
OPSEC integrates into established frameworks:
- NIST RMF: Threat analysis and continuous monitoring align with OPSEC steps.
- ISO 27001: Annex A controls overlap with OPSEC in comms and supplier management.
- CIS Controls: Data handling and access restrictions reinforce OPSEC.
Comparative Table: OPSEC vs INFOSEC vs COMSEC vs Cybersecurity
| Discipline | Focus Area | Example Application |
| OPSEC | Controlling information leaks | Staff training on safe posting |
| INFOSEC | Protecting information systems | Database encryption |
| COMSEC | Securing communications | Encrypting VoIP traffic |
| Cybersecurity | Broad defense of digital assets | Firewalls, EDR, SOC operations |
Operational Security Examples
| Scenario | OPSEC Best Practice | OPSEC Failure Example |
| Product Launch | Announce only after release | Roadmap leaked via job ad |
| Executive Travel | Post updates after return | Tweet itinerary before departure |
| Cloud Maintenance | Announce after completion | Public downtime alert pre-event |
| Social Media Posts | Blur badges & screens | Screenshot reveals internal tools |
Measuring OPSEC: KPIs That Matter
Most organizations ask, “How do we know if OPSEC is working?” Here are practical KPIs:
- Percentage of staff trained in OPSEC awareness
- Number of risky social posts detected per month
- Time to sanitize leaked indicators
- OSINT red-team success rate
- Number of suppliers reviewed for OPSEC compliance
These metrics turn OPSEC from theory into measurable practice.
OPSEC Across Industries
- SaaS: Protect feature launches and bug reports.
- ISPs: Prevent attackers from exploiting outage windows.
- MSPs: Enforce OPSEC across multiple client environments.
- Fintech: Guard algorithms, M&A activity, and investor relations.
Each industry applies the same five steps, but the critical information list (CIL) differs.
Conclusion
So, what is OPSEC in the business world? It’s not a military buzzword; it’s the overlooked pillar of cybersecurity strategy. By applying the five-step cycle, identifying vulnerabilities, and embedding countermeasures, organizations prevent adversaries from piecing together the clues they leak every day.
But OPSEC alone isn’t enough. Even if you control what information leaves your organization, data in transit can still be intercepted. That’s why pairing OPSEC with VPN security is critical.
With PureVPN White Label, businesses can:
- Deliver branded VPN services to secure client communications
- Protect remote sessions and VDI logins with encrypted tunnels
- Meet compliance requirements for data privacy
- Add new revenue streams under their own brand
Pair disciplined OPSEC practices with secure VPN infrastructure. Explore PureVPN White Label to make information control and secure connectivity part of your strategy.


