Security programs often invest heavily in firewalls, endpoint protection, and monitoring tools. Yet a determined intruder does not always need to bypass those controls. Sometimes the simplest path is walking through the front door by following someone who already has access.
This tactic is known as a tailgating attack. It is a low-tech but effective form of social engineering that relies on human behavior rather than software vulnerabilities. An attacker positions themselves close to an authorized individual and slips into a restricted area without presenting valid credentials.
For businesses, this type of breach can be as damaging as a digital intrusion. It can result in stolen devices, exposure of confidential data, or compromise of entire systems if the attacker plants malicious hardware inside the network. This guide explains the tailgating attack meaning, its variations, the consequences for organizations, and proven strategies for prevention.
- Tailgating attack: Unauthorized entry by following an authorized person into secure areas.
- Forms: Passive following, active trickery, impersonation, and hybrid physical-cyber tactics.
- Consequences: Stolen data, hardware theft, compliance penalties, reputational loss.
- Prevention: Awareness training, physical access controls, strict policies, hybrid workplace adjustments.
- Business takeaway: Combine strong physical security with encrypted network access. Deliver branded VPN services through PureVPN White Label to protect clients and generate new revenue.
What Is a Tailgating Attack?
A tailgating attack is a type of physical security breach where an unauthorized person enters a restricted area by following an authorized individual without proper identification or access rights.
Tailgating is considered a social engineering attack because it exploits trust, distraction, or social pressure. Employees often hold doors open for colleagues or visitors, creating an opportunity for intruders to slip in unnoticed. Unlike digital exploits that require coding skill, a tailgate attack relies on observation, timing, and psychology.
Common scenarios include:
- An attacker carrying packages to appear harmless
- Someone claiming they forgot their ID badge
- A person wearing a uniform to resemble delivery or maintenance staff
Tailgating Attack Meaning in Cybersecurity
Tailgating is often described only as a physical breach, but its impact quickly extends into cybersecurity. Once an intruder gains entry, they are no longer limited to physical theft. They can connect rogue devices to the network, copy sensitive files, or launch malware directly from inside the perimeter.
This is why security teams refer to tailgating as part of the human side of breaches. Firewalls and intrusion detection systems cannot stop someone who is already sitting at an internal workstation. A tailgating attack can therefore serve as the entry point for a much larger compromise.
In some incidents, attackers have used access gained through tailgating to begin data spooling, where large volumes of data are copied from servers and removed over time. These attacks are harder to detect because the intruder already appears to be inside the trusted environment.
Types of Tailgating Attacks
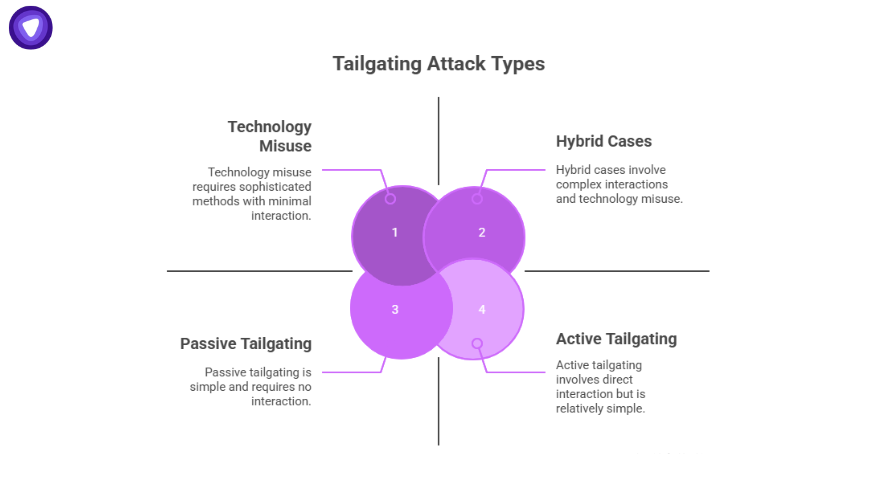
Tailgating can take several forms, depending on how the intruder approaches the target and how much they interact with employees.
Passive Tailgating
An attacker waits for someone to open a secure door and slips in quietly. No interaction is needed; the success depends on remaining unnoticed.
Active Tailgating
The attacker engages directly, often asking for help. Common examples include pretending hands are full with packages or asking an employee to hold the door. This form exploits social pressure and politeness.
Disguised Entry
Here, attackers impersonate delivery staff, cleaners, or contractors. Uniforms, fake badges, or props are used to appear legitimate. Employees often assume they are supposed to be there and allow access.
Technology Misuse
In some cases, attackers rely on borrowed or cloned access cards to piggyback through doors. They do not bypass security themselves but follow someone who has already authenticated.
Hybrid Cases
Modern examples show attackers entering buildings to connect rogue USB drives, install small devices that capture keystrokes, or plant Wi-Fi access points. This blurs the line between a physical breach and a tailgating attack cyber scenario.
Tailgating vs. Piggybacking
Tailgating and piggybacking are often used interchangeably, but they are not identical. Both involve unauthorized entry, but the difference lies in the awareness and intent of the person granting access.
- Tailgating: The attacker slips in without the knowledge of the person ahead.
- Piggybacking: The attacker gains entry because someone knowingly allows it, often believing they are being helpful.
A clear understanding of the distinction helps organizations refine training and policies.
Comparative Table: Tailgating vs. Piggybacking
| Aspect | Tailgating Attack | Piggybacking Attack |
| Awareness | Employee is unaware an intruder has followed | Employee knowingly allows entry |
| Attacker Approach | Passive following or subtle positioning | Direct request for help or permission |
| Common Scenario | Slipping in behind an employee through a secure door | Claiming to have forgotten a badge and asking for entry |
| Security Weakness | Exploits inattention | Exploits trust and willingness to assist |
| Preventive Measures | Monitoring, sensors, strict entry policies | Employee training, no exceptions to access rules |
Consequences of a Tailgating Attack
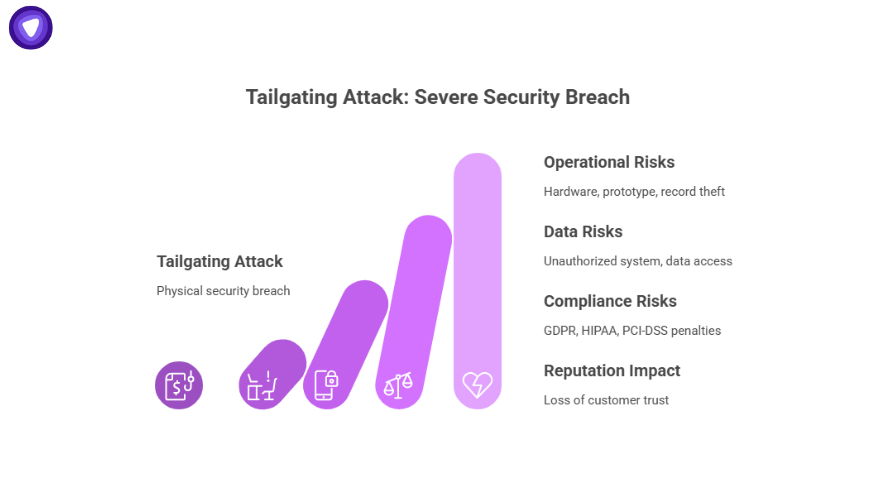
A tailgating attack appears simple, but the results can be severe. Once inside, the intruder has the same access as any other person in the facility.
Operational Risks
- Theft of hardware, prototypes, or paper records
- Disruption of critical operations if devices are tampered with
Data Risks
- Unauthorized access to systems, leading to data spooling
- Installation of malware that compromises networks over time
Compliance Risks
- Exposure of personal data may trigger penalties under GDPR, HIPAA, or PCI-DSS
- Fines and reputational harm if regulators determine security controls were inadequate
Reputation and Financial Impact
- Customers lose trust after reports of preventable breaches
- Loss of intellectual property that affects competitiveness
- Costs associated with forensic investigation, remediation, and insurance disputes
Legal Implications of a Tailgating Attack
Tailgating is not only a security failure but also a legal risk. When an intruder gains unauthorized entry and causes damage, organizations may be held accountable for insufficient controls.
Data Protection and Privacy Laws
- GDPR and HIPAA: Unauthorized access to personal health or customer data can result in regulatory fines.
- PCI-DSS: If cardholder data is accessed through physical compromise, non-compliance penalties apply.
Liability for Loss
- Companies may be responsible for stolen intellectual property if access policies were weak.
- Insurance providers may dispute claims if physical security measures were inadequate.
Duty of Care
- Employers have a responsibility to provide a safe environment. Tailgating that leads to theft, sabotage, or harm to staff can expose businesses to civil claims.
Legal implications make clear that tailgating is not a minor incident. It can create long-term financial and reputational consequences that extend far beyond the immediate breach.
How to Prevent Tailgating Attacks?
Tailgating attacks can be stopped with a combination of awareness, technology, and policy. No single measure is sufficient; layered defense is essential.
People-Focused Measures
- Build a human firewall with regular training
- Encourage employees to challenge or report unfamiliar individuals
- Reinforce a zero-tolerance culture: no “holding the door” exceptions
Technical Measures
- Turnstiles, mantraps, and secured entry doors
- AI-based video analytics to detect multiple entries per card swipe
- Tailgating detection alarms and automated logging systems
Policy Controls
- Enforce strict badge usage
- Escort rules for contractors, visitors, and deliveries
- Access audits to ensure policies are consistently applied
Table: Tailgating Security Controls
| Category | Examples of Controls | Objective |
| People | Training, reporting procedures, human firewall | Reduce social engineering success |
| Technology | Turnstiles, sensors, AI video, alarm systems | Detect and block unauthorized entry |
| Policy | Badge enforcement, visitor escorts, regular audits | Ensure compliance and accountability |
Tailgating in the Age of Hybrid Work
The modern workplace blends traditional offices, shared spaces, and remote environments. This flexibility has increased productivity but also introduced new security risks.
Shared Offices and Coworking Spaces
Organizations using shared facilities face higher tailgating risks. Multiple tenants, contractors, and delivery services pass through the same doors, making it harder to monitor who belongs and who does not.
Hybrid Staff Movement
With employees rotating between office and remote work, attackers exploit confusion about who is authorized. Security staff may hesitate to question unfamiliar faces if they believe they belong to the extended workforce.
Expanded Attack Surface
Once inside, intruders can target unattended devices, connect rogue hardware, or access sensitive printouts left in shared spaces. These actions often bypass digital security tools entirely.
Businesses must adapt their tailgating security measures to this new reality by combining strict physical controls with awareness training tailored to hybrid environments.
Conclusion
A tailgating attack is one of the simplest yet most damaging forms of social engineering. It bypasses firewalls, intrusion detection systems, and encryption by targeting the one weakness every organization has: human behavior. Once inside, an attacker can steal devices, access sensitive files, or plant malicious hardware that enables larger cyber intrusions.
Businesses cannot afford to treat tailgating as a minor inconvenience. It carries financial, legal, and reputational risks that can affect long-term viability. Preventing it requires a layered approach: awareness training that builds a human firewall, technical safeguards such as turnstiles or sensors, and policies that enforce accountability at every entry point.
Yet physical security is only part of the solution. Once an intruder reaches internal systems, data in transit becomes the next target. This is where PureVPN White Label creates value. By offering your own branded VPN, you secure communications, protect SaaS and VDI logins, and build customer trust while generating new recurring revenue streams for your business.


