Vulnerability teams need faster ways to decide which threats to fix first. Traditional severity scores describe how damaging a vulnerability could be, but they say little about how likely it is to be exploited. The Exploit Prediction Scoring System (EPSS) was built to fill this gap.
Maintained by the Forum of Incident Response and Security Teams (FIRST), EPSS uses machine learning to estimate the probability that a vulnerability will be exploited within 30 days.
Version 4 brings major improvements in data coverage, prediction accuracy, and API performance. These changes make EPSS more useful for businesses managing large attack surfaces and tight patch cycles.
- EPSS Purpose: Estimates the probability that a vulnerability will be exploited within 30 days.
- EPSS v4 Upgrades: Improves model accuracy, expands data sources, adds percentile rankings, and delivers faster API responses.
- Risk Focus: Helps teams prioritize based on likelihood of exploitation instead of only severity scores.
- Calculator Use: Businesses can build an EPSS calculator combining EPSS, CVSS, and asset weights for risk ranking.
- Security Layer: PureVPN – White Label secures the vendor sessions and data flows that carry vulnerability data, preventing breach exposure during remediation.
What is EPSS?
EPSS stands for Exploit Prediction Scoring System. It is a machine learning-based model that predicts the probability that a specific software vulnerability (identified by a CVE ID) will be exploited in the next 30 days.
Each vulnerability receives an EPSS score between 0 and 1. A score closer to 1 indicates higher likelihood of exploitation. Security teams use these scores to prioritize patches, restrict access, or implement temporary controls.
What is EPSS in Cybersecurity?
In cybersecurity, EPSS serves as a prioritization signal rather than a severity rating. Tools such as vulnerability scanners or configuration management systems generate lists of CVEs. EPSS assigns each CVE a probability that attackers will exploit it.
The model uses multiple input features, such as:
- Exploit availability on public repositories
- CVE metadata and publication date
- Code complexity
- Social signals like exploit mentions in threat feeds
- Historical exploitation data from telemetry
EPSS does not scan for vulnerabilities or assign impact ratings. It complements existing severity ratings by indicating real-world threat activity.
What does EPSS score mean?
An EPSS score represents the predicted probability of exploitation within 30 days. It ranges from 0 (negligible chance) to 1 (certain exploitation).
Most known CVEs have extremely low EPSS scores. Only a small percentage exceed 0.5. Security teams typically treat scores above 0.7 as high risk and prioritize them for immediate remediation.
Because EPSS updates daily, a vulnerability’s score can increase rapidly if exploit activity grows. This makes EPSS a time-sensitive signal for patch management.
EPSS Calculator
EPSS Calculator
EPSS Version 4: Core Updates
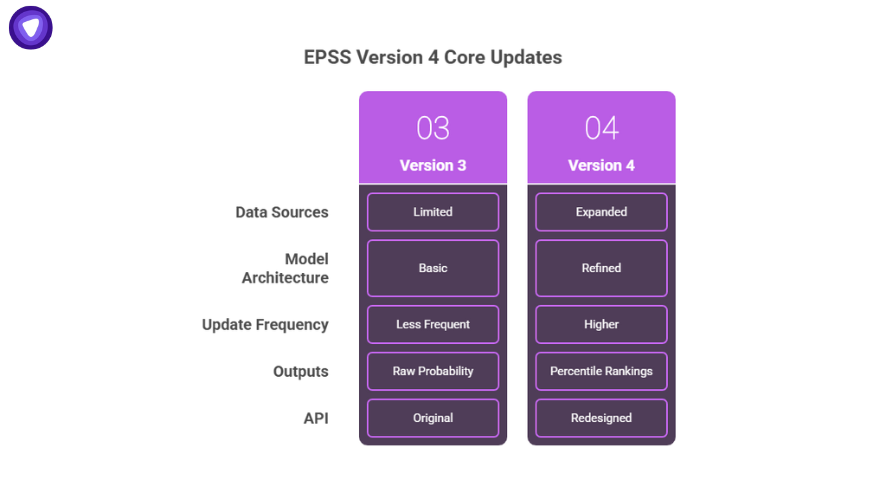
Version 4 introduces several technical improvements over previous releases. The changes improve predictive accuracy, coverage, and integration flexibility.
Expanded Data Sources
EPSS v4 incorporates a broader set of data sources, including:
- Additional exploit repositories
- Malware telemetry feeds from partner vendors
- Broader CVE metadata coverage
- More indicators of weaponization
This expansion increases the number of CVEs that can be scored and improves model confidence on newly published vulnerabilities.
Improved Model Architecture
Version 4 uses a refined machine learning framework that handles nonlinear feature interactions more accurately. It improves prediction precision, reducing false positives and false negatives. Security teams can expect higher signal quality even on low-severity CVEs that show active exploit development.
Higher Update Frequency
Scores now refresh more frequently throughout the day. This allows security teams to respond to shifting exploit activity faster than before. Daily CSV files and streaming feeds are available for bulk use.
New Percentile Outputs
EPSS v4 provides percentile rankings in addition to raw probability. This makes it easier to benchmark a vulnerability’s exploitation risk against the entire CVE dataset.
Updated EPSS API
The EPSS API has been redesigned for faster response and better query handling. It supports batch CVE lookups and delivers both score and percentile values. This enables integration into security dashboards, vulnerability management systems, and ticketing workflows.
EPSS vs CVSS
| Aspect | EPSS (Exploit Prediction Scoring System) | CVSS (Common Vulnerability Scoring System) |
| Purpose | Predicts the likelihood a vulnerability will be exploited in the next 30 days | Measures the potential impact/severity if a vulnerability is exploited |
| Score Range | 0 to 1 (probability) | 0 to 10 (severity) |
| Focus | Real-world exploit activity and threat probability | Technical severity, exploit complexity, and environmental impact |
| Data Inputs | Exploit feeds, telemetry, CVE metadata, threat intelligence | CVE metrics (attack vector, complexity, privileges, impact metrics) |
| Update Frequency | Updates daily (dynamic) | Static unless rescored manually |
| Use Case | Prioritize which vulnerabilities are most likely to be exploited soon | Prioritize which vulnerabilities are most damaging if exploited |
| Limitations | Does not measure impact or business context | Does not reflect real-world likelihood or exploit trends |
| Example | CVSS 6.0 + EPSS 0.85 → moderate severity, high probability | CVSS 9.8 + EPSS 0.01 → severe impact, low probability |
| Best Practice | Combine EPSS with CVSS and asset criticality to drive risk-based patching | Combine EPSS with CVSS and asset criticality to drive risk-based patching |
Understanding the EPSS Scale and Thresholds

EPSS scores range from 0 to 1. Most CVEs have scores below 0.1, and only a small fraction exceed 0.7.
Average operational ranges observed across datasets:
- EPSS > 0.7 → Prioritize for immediate patching
- EPSS 0.3–0.7 → Address within short maintenance cycles (7–14 days)
- EPSS < 0.3 → Monitor and defer unless on critical assets
Because scores fluctuate daily, teams should automate the retrieval and evaluation of EPSS data. This ensures they do not miss score increases caused by new exploit releases.
Real-World Use Cases for EPSS v4
Security teams across sectors are applying EPSS to make vulnerability management more targeted.
Common use cases:
- Patch triage: Use EPSS to rank thousands of backlog vulnerabilities, eliminating low-risk noise.
- MSP prioritization: Managed service providers use EPSS scores to assign patch deadlines across multiple client networks.
- DevSecOps planning: SaaS teams identify high-likelihood library vulnerabilities and schedule updates in early sprint cycles.
- Incident response: Use EPSS to assess which unpatched CVEs on compromised systems are most likely to be exploited next.
A financial services firm reduced its patching backlog by 60% after adopting EPSS-driven prioritization. Previously, teams spent weeks patching low-severity CVEs with no known exploitation. After integrating EPSS into their ticketing system, they focused only on vulnerabilities scoring above 0.7. Mean time to patch dropped from 45 days to 12 days, and system downtime during patching decreased by 35%.
EPSS v4 makes these outcomes more achievable by improving predictive accuracy and data freshness.
Common Misconceptions and Limitations
- EPSS does not measure severity. It measures likelihood of exploitation only.
- EPSS does not replace asset context. Teams still need to weigh business impact and exposure levels.
- High EPSS does not mean active exploitation is guaranteed. It signals high probability, not confirmation.
- False positives and false negatives exist. Some vulnerabilities with high EPSS do not get exploited, and some low-score ones are exploited. EPSS reduces this gap but cannot eliminate it.
For best results, teams should combine:
- EPSS scores for probability
- CVSS scores for severity
- Asset value for business impact
This produces a complete risk-based view for patch planning.
Secure Vulnerability Workflows with PureVPN
PureVPN White Label provides encrypted tunnels, multi-factor authentication, device posture checks, and session logging for all vendor and remote access. You can brand the VPN as your own security product and integrate it directly into your vulnerability management platforms.
This ensures that every EPSS-driven action, from patch orchestration to third-party remediation, runs inside an encrypted environment. It reduces the legal and operational exposure of handling vulnerability data across distributed networks.
Conclusion
EPSS Version 4 improves how security teams target high-risk vulnerabilities, reducing backlogs through accurate, real-time scoring.
However, EPSS alone cannot protect the sensitive data driving these decisions. That data moves across scanners, dashboards, vendors, and contractors—paths attackers can exploit.
PureVPN White Label closes this gap by providing encrypted VPN tunnels, MFA, device checks, and session logging under your own brand. It safeguards every connection handling vulnerability data, preventing interception and compromise.


