Internet Service Providers (ISPs) once focused almost entirely on bandwidth and uptime. That model is breaking. Networks have become prime targets for phishing, malware, and large-scale Distributed Denial-of-Service (DDoS) attacks. Regulators now expect ISPs to do more than provide a connection; they expect proactive protection for subscribers and infrastructure.
This shift is not optional. Churn is increasing where security is weak, and average revenue per user (ARPU) growth is flat across many markets. The ISP cybersecurity that evolves into security providers is better positioned to retain customers, control support costs, and expand revenue.
- Shift in ISP role: ISPs are moving beyond connectivity into full ISP cybersecurity to fight phishing, malware, botnets, and DDoS attacks.
- Threat surge: DDoS attacks rose 25% in early 2024, while supply chain cyberattacks jumped 33%—exposing ISP weaknesses.
- Cost of breaches: Average breach costs hit $4.88M in 2024 and contribute to a projected $23T annual cybercrime bill by 2027.
- Revenue opportunity: Bundling privacy and security tools like VPNs and password managers can grow ARPU and reduce churn.
- Fast go-to-market: PureVPN – White Label lets ISPs launch branded security services quickly without building new infrastructure.
What Is ISP Cybersecurity?
ISP cybersecurity refers to the security measures Internet Service Providers deploy to protect their networks and subscribers. This includes blocking access to malicious websites, filtering phishing emails, stopping command-and-control traffic, and mitigating DDoS attacks before they disrupt customer service.
ISPs now act as a first line of defense:
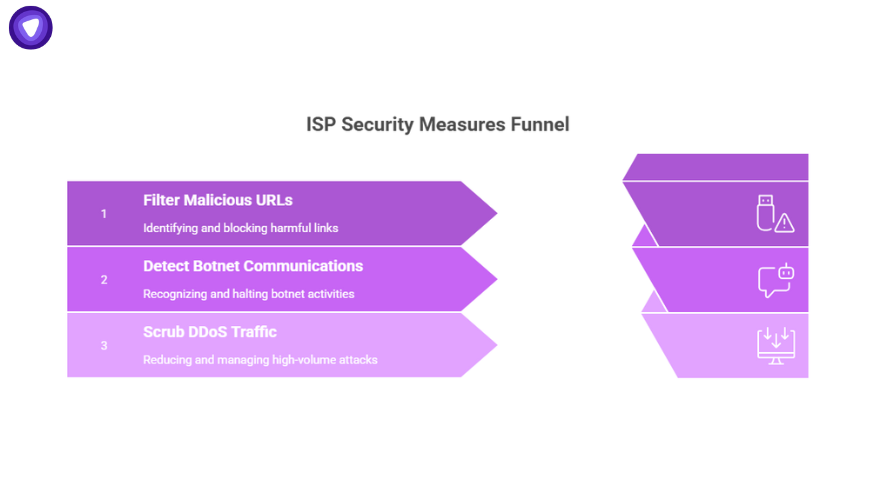
- Filtering malicious URLs and phishing content.
- Detecting and stopping botnet communications.
- Scrubbing high-volume DDoS traffic before it reaches end users.
The Four Types of ISPs and Their Risk Profiles
ISPs come in four common categories, each with distinct security exposures:
| Type of ISP | Core Offering | Key Security Risks |
| Dial-up / legacy | Basic connectivity | Outdated equipment, poor patching, malware relay |
| DSL / cable | Residential broadband | DDoS floods, DNS hijacks, modem firmware exploits |
| Fiber | High-speed enterprise & home | BGP hijacking, large-scale botnet abuse |
| Wireless / mobile | 4G/5G access | SIM swap fraud, signaling attacks, IoT botnets |
Understanding these categories helps providers align protection with their infrastructure.
Why Cybersecurity Is No Longer Optional for ISPs?
ISPs can no longer treat cybersecurity as an add-on; rising attacks, higher breach costs, and stricter regulations now make security a core part of running a network.
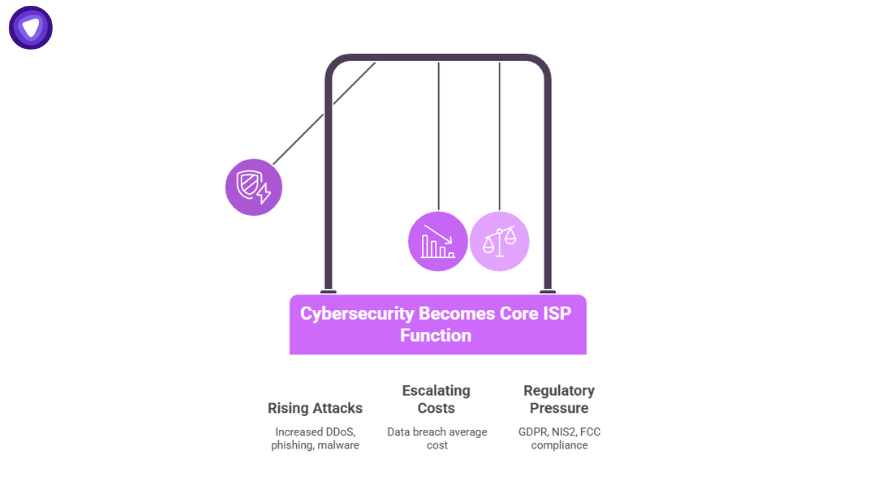
Rising Attack Volume
- According to PureVPN Partners, DDoS attacks increased 25% in early 2024, with multi-vector campaigns aimed at overwhelming ISP networks and degrading service.
- AI-driven phishing and malware campaigns are growing, targeting both infrastructure and end users.
- Supply chain cyberattacks rose 33% in 2024, affecting more than 183,000 customers where ISPs rely on third-party software.
Escalating Breach Costs
- The global average cost of a data breach hit $4.88M in 2024, feeding into a projected $23 trillion annual cybercrime impact by 2027, according to PureVPN Partners.
- These costs pressure ISPs to implement advanced security to avoid SLA penalties, regulatory fines, and churn.
Growing Regulatory & Liability Pressure
- GDPR, the EU’s NIS2, and U.S. FCC rules now expect ISPs to maintain secure infrastructure and protect subscriber data.
- Service Level Agreements increasingly define “duty of care” for cybersecurity.
- Lawsuits against providers after breaches or outages are rising.
Key Cybersecurity Concerns for ISPs
ISPs face a growing set of technical and compliance challenges that threaten both network stability and customer trust.
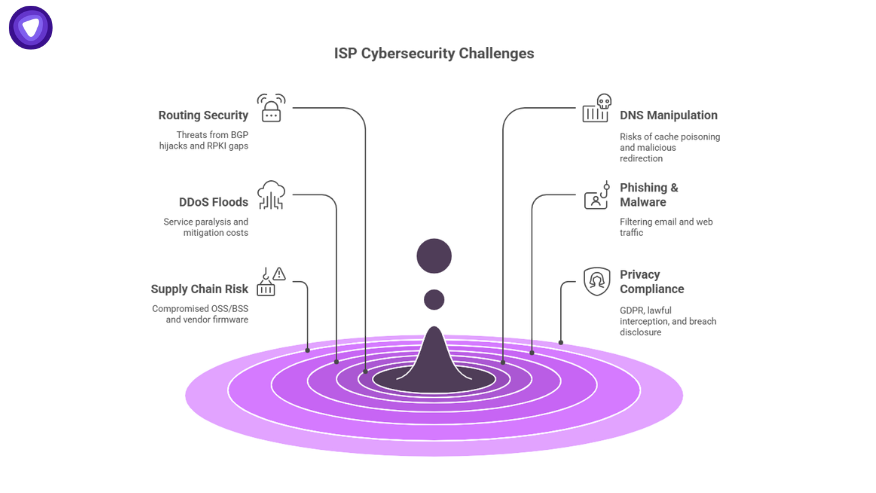
- Routing security: BGP hijacks and incomplete RPKI adoption.
- DNS manipulation: Cache poisoning and redirection to malicious sites.
- DDoS floods: Service paralysis and costly mitigation.
- Phishing & malware: Filtering email and web traffic at scale.
- Supply chain risk: Compromised OSS/BSS and vendor firmware.
- Privacy compliance: GDPR, lawful interception, and breach disclosure.
These are now standard cybersecurity concerns for ISPs planning their 2025 roadmaps.
From Bandwidth Seller to Security Provider
Flat ARPU and expensive support have made pure connectivity less profitable. According to PureVPN Partners, ISPs that added branded security products saw lower churn and higher contribution margin per user (CMPU). This happens because secure networks generate fewer helpdesk tickets and fewer breach-related complaints, while add-on services create new revenue.
Practical Security Services ISPs Can Offer
| Service | Customer Value | ISP Impact |
| DDoS mitigation | Keeps businesses and gamers online | Reduces SLA penalties |
| Secure DNS & content filtering | Blocks phishing & malware | Cuts infection-related support |
| IoT network isolation | Protects smart homes & SMB devices | Lowers abuse complaints |
| White-label VPN | Encrypts traffic & protects privacy | Raises ARPU with minimal cost |
| Branded password manager | Reduces credential theft fallout | Locks in subscribers |
| Endpoint protection | SMB security | Adds B2B upsell revenue |
ARPU and Profitability Metrics
ISPs track Contribution Margin Per User (CMPU):
CMPU = (ARPU × Gross Margin %) – Support Cost Per User
According to PureVPN Partners, bundling privacy and security services like VPN and password management can improve CMPU more effectively than price increases, because they add revenue without raising network delivery costs or support complexity.
Selecting Security Vendors for ISPs
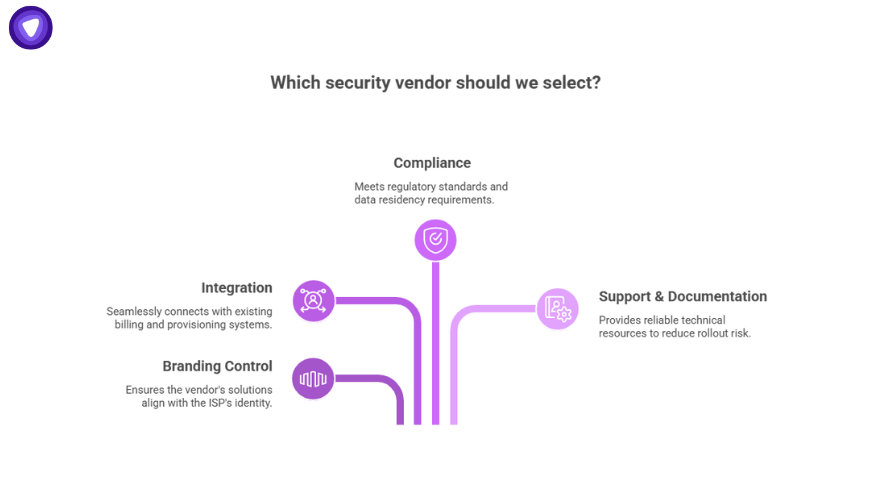
Here are the features that you must look into before selecting security vendors:
- Branding control: Apps and portals must reflect the ISP’s identity.
- Integration: APIs and SDKs should tie into billing and provisioning systems.
- Compliance: SOC 2, GDPR readiness, and clear data residency options.
- Support & documentation: Reliable technical resources reduce rollout risk.
Transform From Connectivity Provider to Security Leader
PureVPN White Label helps ISPs launch security services under their own brand:
- VPN apps with AES-256 encryption and zero-knowledge architecture.
- Password management solutions that customers can trust.
- Developer-ready APIs and SDKs for quick billing and provisioning integration.
This approach adds subscriber-visible value without requiring ISPs to build and maintain security infrastructure from scratch.
Conclusion
ISPs face rising cyberattacks, stricter regulations, and expensive breach fallout. Pure connectivity is no longer enough; ISP cybersecurity is now part of the core business. Offering branded security services such as VPNs and password managers can increase ARPU, reduce churn, and improve profitability.
PureVPN White Label lets ISPs add these services quickly, meeting customer expectations and strengthening the bottom line without heavy development or infrastructure costs.


