- The TruffleNet attack began with stolen AWS credentials, not malware, allowing attackers to exploit trusted cloud infrastructure for large-scale fraud.
- Over 800 hosts were used to validate and abuse AWS SES accounts, turning legitimate email services into phishing and BEC delivery systems.
- Attackers leveraged automation to test and weaponize leaked credentials, demonstrating how identity misuse now outpaces software exploitation.
- Traditional defenses failed because all activity appeared legitimate, emphasizing the need for strict credential hygiene and API monitoring.
- Secure remote access and network-layer controls, such as PureVPN’s White Label VPN Solution, are essential to prevent credential leaks and enforce trusted cloud connections.
It did not start with malware or a zero-day exploit. The TruffleNet attack began with something far more ordinary: valid credentials. A set of stolen AWS access keys, quietly circulating online, gave attackers the foothold they needed to turn Amazon’s trusted infrastructure into a global fraud operation.
This wasn’t just another phishing wave. It was a coordinated cloud campaign that exploited legitimate services, proving how attackers now think less about breaking in and more about logging in.
The TruffleNet attack is a lesson in modern credential-based warfare: identity is the new perimeter, and once that line is crossed, traditional defenses become almost meaningless.
How the TruffleNet Attack Unfolded?
The TruffleNet attack, uncovered in October 2025, marks one of the most sophisticated cloud-targeted campaigns of the year. These are the main phases of the attack:
Phase 1: The credential breach
The operation began when attackers obtained stolen AWS credentials from exposed repositories, leaked configuration files, or compromised developer accounts. These weren’t admin passwords or brute-forced logins, they were legitimate access keys left unprotected.
With those keys in hand, attackers performed cloud reconnaissance. They started with an innocuous API call to confirm whether the credentials were valid. Next, they asked AWS SES how many emails that account was allowed to send.
Researchers later traced over 800 active hosts across 57 network ranges participating in this activity. Every one of them played a role in validating, testing, or abusing the stolen AWS credentials.
Phase 2: Turning access into infrastructure
Once attackers confirmed which AWS accounts had active SES permissions, they moved to weaponize them. Using those permissions, they set up new email identities, configured DKIM authentication, and began sending out realistic vendor invoices, payment requests, and procurement forms.
Because AWS SES is a trusted email platform, messages from these accounts bypassed spam filters with ease. Recipients saw legitimate headers, verified sender domains, and even authentic SPF and DKIM records. That credibility is what made the TruffleNet attack so effective.
Phase 3: Expanding through automation
What made TruffleNet particularly dangerous was its automation. Attackers built scripts to test credentials at scale, scanning the internet for leaked keys and immediately verifying them. Once a working set was found, it was added to the next phase of the campaign.
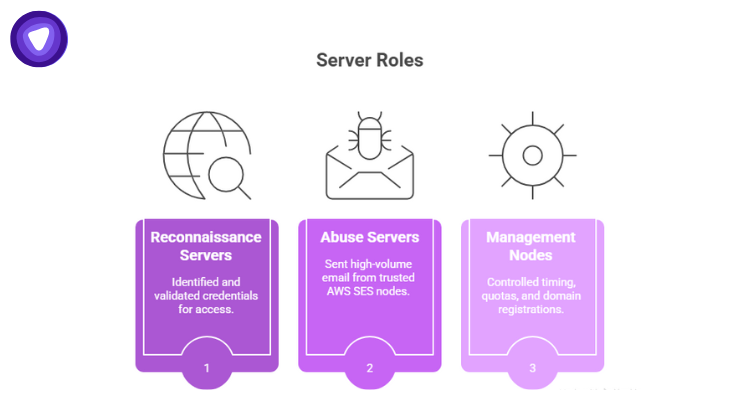
The entire operation moved like a production pipeline:
- Reconnaissance servers identified and validated credentials.
- Abuse servers sent high-volume email from trusted AWS SES nodes.
- Management nodes controlled timing, quotas, and domain registrations.
This wasn’t opportunistic cybercrime. It was industrialized credential abuse.
What Made the TruffleNet Attack Different
Most security incidents rely on exploiting software flaws. The TruffleNet attack exploited trust, the trust placed in cloud credentials, identity services, and legitimate infrastructure.
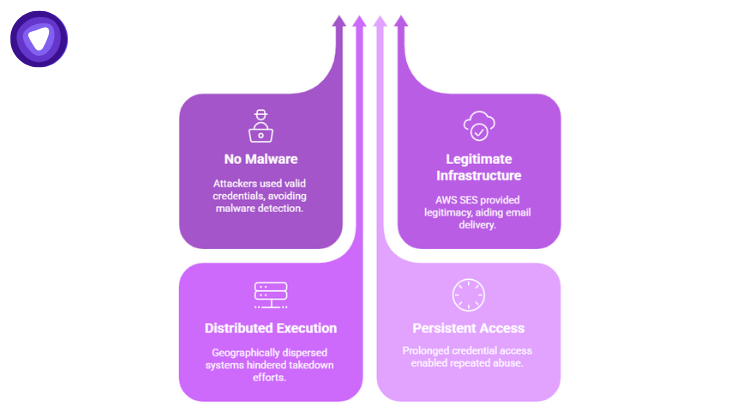
Here’s what separated it from typical cloud compromises:
- No malware was required. Every API call came from valid, authorized credentials.
- Legitimate infrastructure was used. AWS SES handled email delivery, giving attackers instant legitimacy.
- Distributed execution. Hundreds of geographically dispersed systems performed specific roles, making takedown nearly impossible.
- Persistent access. Compromised credentials often stayed active for weeks before detection, allowing repeated abuse.
It showed how attackers no longer need to breach the cloud itself, they only need to borrow its keys.
Why Stolen AWS Credentials are the Perfect Weapon
The appeal is simple: AWS credentials unlock a vast ecosystem. From data storage to compute resources to email infrastructure, one exposed key can open doors across an entire organization.
A recent report found that 33% of breaches involved compromised privileged identities, highlighting just how often identity, not malware, is the first domino to fall.
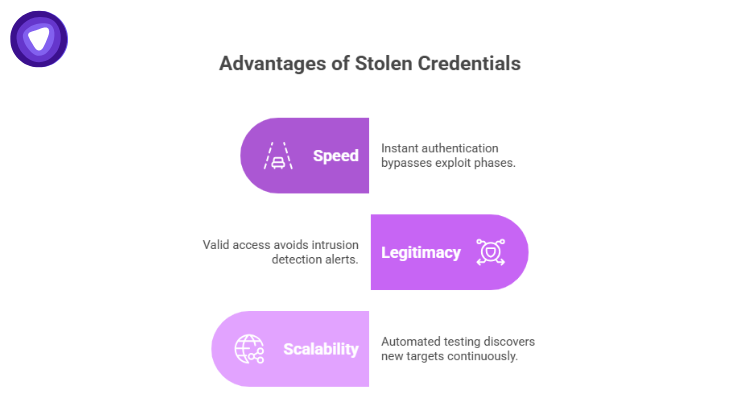
For the attackers behind TruffleNet, stolen AWS credentials offered several advantages:
- Speed: They could authenticate and act instantly, skipping traditional exploit phases.
- Legitimacy: Valid access avoids triggering intrusion alerts that rely on brute force or signature-based detection.
- Scalability: Once automated, credential testing and abuse could operate continuously, discovering new targets around the clock.
It was efficiency, not sophistication, that made the TruffleNet attack so destructive.
The Global Impact
The TruffleNet attack wasn’t contained to one region or industry. Its operators sent fraudulent invoices, supplier updates, and tax forms to companies worldwide, part of a growing wave of business email compromise (BEC) scams.
In one confirmed case, an organization received what appeared to be a vendor payment request from a known supplier domain. Everything about the message looked authentic. But the reply-to field had been swapped with a typosquatted domain ending in “-impactaction.com,” leading payments directly to attacker-controlled accounts.
Key Findings from the TruffleNet Campaign
These are the main findings from the attack:
| Threat Element | Observed Behavior | Security Implication |
| Credential Source | Leaked AWS keys from GitHub, code archives, and developer systems | Poor secret management practices remain a primary risk vector |
| Reconnaissance Activity | Over 800 hosts validating credentials via AWS APIs | Highly distributed infrastructure reduces traceability |
| Abused Service | Amazon Simple Email Service (SES) | Trusted cloud infrastructure used for large-scale phishing and fraud |
| Primary Attack Outcome | Business Email Compromise (BEC) and vendor payment fraud | Financial and reputational loss for affected companies |
| Detection Challenge | API calls appeared legitimate | Traditional intrusion systems often failed to flag activity |
Lessons for IT Leaders and Cloud Administrators
The TruffleNet attack is a wake-up call for organizations relying on cloud infrastructure, especially those supporting remote or hybrid teams. Protecting cloud accounts now requires as much discipline as protecting physical networks once did.
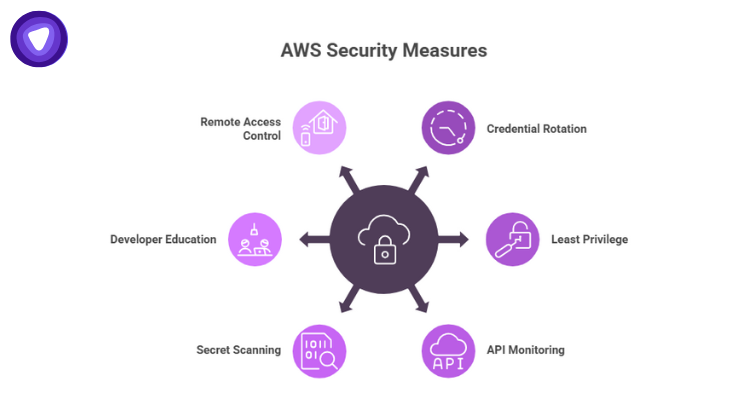
Here are the immediate lessons:
- Rotate credentials regularly. Any static access key is a liability. Use short-lived tokens wherever possible.
- Apply least privilege. Most compromised keys in TruffleNet had permissions far beyond their intended scope.
- Monitor for unusual API calls. Requests like GetSendQuota or CreateEmailIdentity can indicate SES abuse attempts.
- Use secret scanning tools. Automated detection of exposed AWS keys in repositories or logs can prevent exploitation.
- Educate developers. A single overlooked environment variable can trigger massive exposure.
- Segment remote access. Limit who can reach production credentials from outside the corporate network.
The Role of Secure Remote Access in Prevention
While TruffleNet operated at the cloud level, many credential leaks originate from endpoint mismanagement and insecure remote access. Developers or contractors logging into cloud dashboards from unprotected networks often become the weak link.
In hybrid or globally distributed setups, ensuring that every remote connection to the cloud is secure and traceable is critical. This is where network-layer controls complement cloud-layer security. A compromised laptop shouldn’t equal compromised credentials.
Strengthening Cloud Identity with PureVPN White Label VPN Solution
This is where network security meets identity protection. A white-label VPN solution gives organizations control over cloud access without adding complexity.
PureVPN White Label VPN Solution enables businesses to create encrypted, authenticated tunnels for remote teams and contractors accessing sensitive cloud systems, routing AWS and development traffic through verified VPN endpoints for complete visibility.
It allows service providers and MSPs to deploy a VPN under their own brand while ensuring encrypted sessions, controlled access to AWS, centralized IP management, and reduced credential theft risks. By combining network-level protection with identity hygiene, organizations ensure credentials are only used from trusted, authorized endpoints.
Final Thoughts
The lesson is clear: the TruffleNet attack wasn’t a failure of AWS or cloud computing. It was a failure of control, of knowing who is connecting, from where, and with what level of privilege. The future of cybersecurity belongs to those who treat identity and network access as inseparable parts of the same defense.


