- Supply-Chain And Infrastructure Risk: The F5 breach elevates risk for all enterprises using network infrastructure devices.
- Remote Access And Edge Devices: VPNs and edge appliances are under renewed scrutiny due to exposed source code and vulnerabilities.
- Configuration And Implementation Exposure: Some stolen data included customer-specific deployment details, increasing risk of targeted attacks.
- Zero-Day Risk And Patch Urgency: Unknown vulnerabilities could be exploited quickly, shifting focus to proactive hardening.
- Reputational And Operational Fallout: Enterprises may face downtime, remediation costs, and scrutiny if trusted infrastructure vendors are compromised.
When a company renowned for keeping the internet running safely becomes the target of its own catastrophe, the ripple effects reach far. The F5 breach is exactly that kind of wake-up call.
In August 2025 an advanced threat actor gained access to F5’s development environment and exfiltrated portions of the source code for its flagship BIG-IP product line and along with it, information about previously undisclosed vulnerabilities. Over 266,000 devices remain potentially exposed.
For IT managers, especially those responsible for remote access infrastructure, VPNs, and secure gateways, the implications are profound. This blog will unpack the F5 breach, detail what it means for enterprises everywhere, and map what practical steps you should take now.
What Is F5?
F5 Networks is a technology company that provides network services, especially application delivery, traffic management, load balancing, and security appliances that sit at the edge of enterprise and cloud networks. Its BIG-IP product suite is widely used in enterprise environments (including 48 of the Fortune 50 companies).
When you read headlines like “F5 breach”, you’re not talking about a consumer VPN being hacked: you’re talking about the network plumbing that many enterprises use to deliver and secure applications.
Timeline And Key Facts Of The F5 Breach
Here is a clear overview of the F5 breach:
| Date | Event | Why it matters |
| ~ Aug 9 2025 | F5 detected unauthorized activity in its BIG-IP/dev environment. | The breach had been ongoing for an unknown period before detection. |
| Oct 15 2025 | F5 publicly disclosed that source code and details of undisclosed vulnerabilities had been exfiltrated. | Public disclosure triggered wider concern and regulatory action (see CISA below). |
| Oct 15 2025 | Cybersecurity and Infrastructure Security Agency (CISA) issued Emergency Directive 26-01 requiring U.S. federal agencies to inventory and patch F5 devices. | Demonstrates seriousness: the breach is considered an “imminent threat”. |
| Ongoing | No confirmed active exploitation of the stolen vulnerabilities (as of disclosure) but risk remains high. | The absence of detected exploitation is no comfort. |
What Was Stolen Or Accessed?
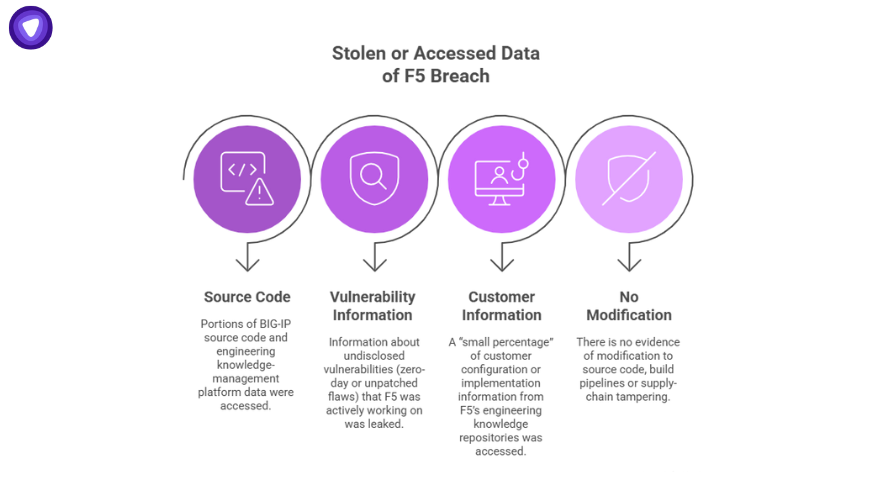
Here is what was accessed or leaked as part of the theft:
- Portions of BIG-IP source code and engineering knowledge-management platform data.
- Information about undisclosed vulnerabilities (zero-day or unpatched flaws) that F5 was actively working on.
- A “small percentage” of customer configuration or implementation information from F5’s engineering knowledge repositories.
- There is no evidence (according to F5) of modification to source code, build pipelines or supply-chain tampering.
Why The Attack Succeeds?
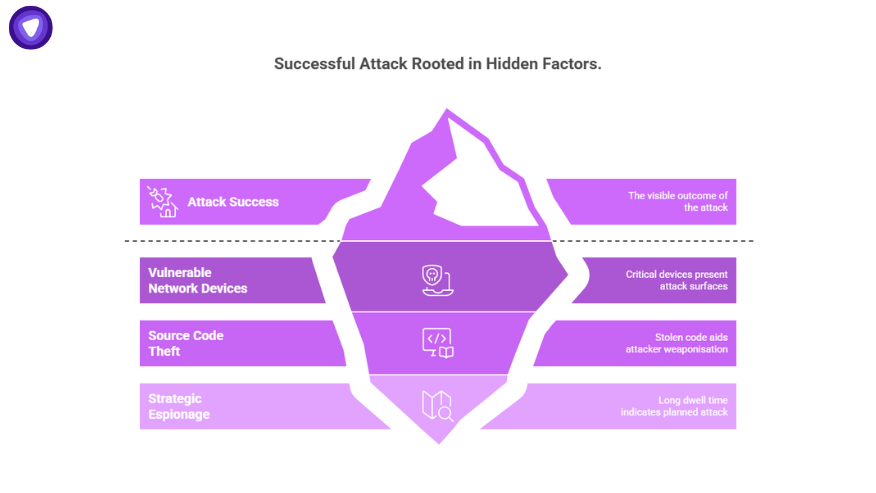
The key factors that make this incident especially alarming:
- Network edge devices like BIG-IP sit in critical positions and manage traffic, terminate TLS, and present attack surfaces.
- Stealing source code and vulnerability details gives attackers a head start for weaponisation.
- The long dwell time of the threat actor suggests this was strategic espionage, not opportunistic.
Why This Matters For Enterprises Everywhere?
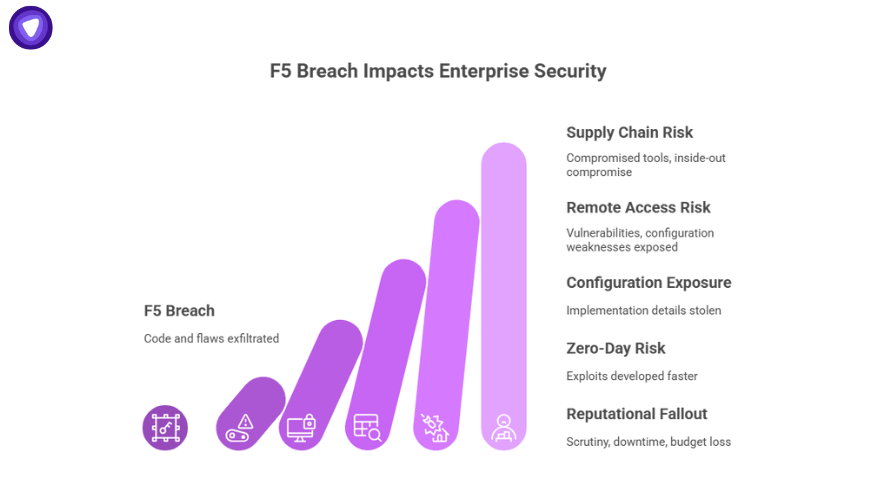
Why should an IT manager running a VPN or secure remote-access solution care about the F5 breach? Because it elevates the risk scenario for virtually all enterprises. Here are the key impacts.
1. Supply-Chain And Infrastructure Risk Escalated
When the tools that enterprises rely on are themselves compromised, the traditional “patch the perimeter” approach is no longer enough.
The F5 breach is akin to a software supply-chain event: code and undocumented flaws exfiltrated, which could enable inside-out compromise. Even if your operations don’t use BIG-IP, the ripple effect means threat actors are likely to look for similar targets in network infrastructure.
2. Remote Access, VPNs, And Edge Devices Under Renewed Scrutiny
Many enterprises use VPNs, zero-trust gateways and remote access solutions layered on top of load balancers, SSL/TLS-terminating appliances, and edge WAFs. If an edge device’s code has been stolen, its hosted services could become higher-risk.
Attackers may find previously hidden vulnerabilities or configuration weaknesses. As more work is done remotely, IT managers face the dual challenge of securing modern endpoints and ensuring the edge devices themselves haven’t become threat vectors.
3. Configuration And Implementation Details Exposed
F5 acknowledged that some stolen data included customer-specific implementation or configuration details. That means the attacker might know how some organisations deployed their devices.
If attackers know how you deploy a device, your custom configurations become less of a secret, increasing the success chances of targeted attacks or zero-day weaponisation.
4. Zero-Day Risk And Patch Urgency
With stolen code and internal vulnerability data, the attacker can potentially develop exploits faster than usual.
Organisations must assume that unknown vulnerabilities in vendor products could be exploited, not just known ones. This shifts the paradigm from “patch what’s known” to “harden everything and assume you have unknown risks.”
5. Reputational And Operational Fallout
If a trusted infrastructure vendor is compromised, enterprises using that vendor may find themselves under scrutiny or exposed. Downtime, remediation efforts, device replacement, configuration reviews may cost time, budget and trust.
For IT managers whose priority is “avoid downtime,” this breach is a reminder: prevention and resilience need to outrank mere availability.
The F5 Breach List: What Products And Versions Are Affected
Here are high-level details about what products the F5 breach impacts, and what IT managers should check.
| Product / Area | Risk Status | Action for Organisations |
| BIG-IP (various modules) | The core product whose source code was partially stolen. | Inventory all BIG-IP appliances, ensure they are patched and hardened. |
| F5OS / Appliance Mode | Vulnerabilities (e.g., CVE-2025-61955, CVE-2025-57780) identified. | Check firmware versions, apply vendor patches immediately. |
| Customer Configuration Data | Some stolen repository files included configuration or implementation data. | Review access logs, configuration exposures, restrict privileged access. |
| Supply Chain / NGINX / Distributed Cloud | F5 states no evidence of supply-chain compromise or NGINX codes being accessed. | Still advisable to monitor for any signs of tampering or rogue updates. |
Note: The exact full list of affected versions is vendor-specific and evolving. IT teams should refer to F5’s Security Notification and Continuous Monitoring for new CVEs.
What IT Managers Should Do Now?
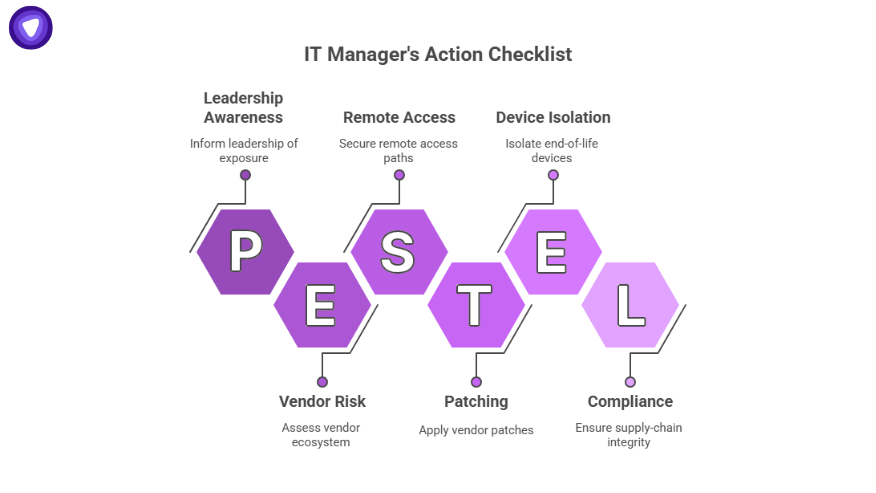
Here’s a practical checklist tailored for IT managers responsible for remote access, security infrastructure, and enterprise resilience.
Inventory And Visibility
- Identify all devices and services from F5 (or similar edge/appliance vendors) across your environment: physical, virtual, cloud.
- Determine which are reachable from the Internet, have management interfaces exposed, or are end-of-life or unsupported.
- Map critical remote-access paths that depend on these devices (VPNs, load balancers, SSL/TLS termination).
Patching And Hardening
- Apply all vendor-released patches immediately, especially those addressing the newly disclosed vulnerabilities (e.g., CVE-2025-53868, CVE-2025-61955).
- For any device with a publicly accessible management interface, consider taking it offline or restricting access until you can confirm its secure configuration.
- Employ multi-factor authentication for all administrative access, privilege separation, and least-privilege enforcement.
- Remove or isolate devices that are end-of-life, unsupported, or cannot be updated.
Monitoring, Threat Hunting, And Segmentation
- Increase logging and monitoring of these devices, especially for unusual access or configuration changes. F5 provides a threat-hunting guide which may be worthwhile.
- Segment your network such that edge devices have limited lateral access. If one is compromised, the blast radius is contained.
- Regularly review configuration drift, log anomalies, and external scanning activity targeting your edge infrastructure.
- If you use VPNs or remote access services layered on top of these appliances, treat them as potential weak links and validate no unmanaged dependencies.
Vendor And Supply-Chain Risk Management
- Assess your vendor ecosystem and determine how many suppliers have access to sensitive network appliances.
- Require that vendors provide assurance of supply-chain integrity (code signing, build-pipeline auditing).
- Maintain an “assume breach” mindset. Even trusted vendors can be compromised, so critical systems must be resilient.
Communication And Incident Readiness
- Inform leadership that the F5 breach increases your organisation’s exposure, especially in remote-access and edge infrastructure.
- Update your incident-response plans to include scenarios where vendor-source-code exfiltration and unknown vulnerabilities are used by threat actors.
- Conduct tabletop exercises that include edge-device compromise or vendor-supplied component risk.
Rethinking Remote Access Security After The F5 Breach
As enterprises shift toward distributed workforces, IT managers are adopting remote-access and VPN solutions with an eye on reducing complexity while improving security. In that context, the F5 breach highlights a practical point: the simpler and more transparent your remote-access architecture, the fewer unseen dependencies you have.
A streamlined solution that provides secure connectivity without requiring complex layering of multiple appliances becomes especially appealing. With one trusted system you can reduce the number of devices that need constant patching, hardening, and monitoring, thereby shrinking your attack surface.
How PureVPN White Label VPN Helps Businesses Strengthen Remote Access?
The PureVPN White Label VPN solution offers a practical answer to the challenges revealed by the F5 security incident. It allows organisations to create their own branded VPN service with complete administrative control and secure access management.
With dedicated IPs, team controls, and centralised dashboards, IT managers can easily monitor and manage remote access without relying on multiple third-party network appliances.
By consolidating remote access under a trusted, simplified platform, businesses reduce their dependency on vulnerable edge devices and complex vendor ecosystems. PureVPN’s infrastructure ensures end-to-end encrypted connectivity and consistent performance for distributed teams, enabling enterprises to maintain control, visibility, and peace of mind in the aftermath of incidents like the F5 breach.
Final Thoughts
The F5 breach has exposed a hard truth: even infrastructure vendors that power large portions of the enterprise landscape are vulnerable, and those vulnerabilities can ripple out to you.
For IT managers tasked with keeping remote teams connected and data secure, the path forward is clear: assume exposure, inventory your dependencies, harden your edge, patch relentlessly, and simplify where possible. Your organisation’s resilience depends on it.


