- IP stresser tools simulate traffic load but are often misused for illegal DDoS attacks.
- Testing your own systems is legal—targeting others without permission is a cybercrime.
- “Free IP stressers” are usually disguised DDoS-for-hire services.
- These attacks lead to business damage—downtime, lost trust, and legal risks.
- VPNs help mask IPs and reduce exposure to such attacks.
- PureVPN White Label lets businesses offer secure, branded VPNs with added revenue potential.
- With DDoS attacks rising, prevention is no longer optional—it’s a business necessity.
If you’re running a business that relies on uptime, whether that’s a SaaS platform, an e-learning app, a streaming service, or even a basic corporate website, you need to know what an IP stresser is.
On the surface, it sounds harmless. These tools are marketed as a way to test server durability by “stress-testing” your IP address with fake traffic.
But here’s the catch: the same tools used to test can just as easily be used to take your services offline. And they are constantly. What started as a way to measure performance is now being sold as a cheap way to launch DDoS attacks.
This blog breaks it all down from what these tools really do to how attackers use them, and how legitimate businesses can protect their networks and reputations. Because pretending IP stressers are just harmless utilities is a mistake companies can’t afford anymore.
What Is an IP Stresser?
An IP stresser is a tool that sends large volumes of traffic to a specified IP address to see how it handles the load. Technically, the purpose is “performance testing.” In reality, most stressers are used to overload systems, not test them.
This kind of traffic spike mimics what’s known as a DDoS (Distributed Denial of Service) attack. When your server is hit with more requests than it can handle, it stops responding to real users.
Stressers are often sold online with dashboards, logs, and support, just like any software product. That’s what makes them so dangerous. They’re accessible. Cheap. And scalable.
“IP stress” is just another way of describing the artificial load created by these tools. It’s not about optimizing. It’s about overwhelming. Imagine thousands of fake users hitting your login page at once. Your server thinks they’re real. It tries to respond. Then crashes.
The worst part? These tools don’t require technical skills to operate. A teenager with a credit card can launch an attack in minutes.
Why “Free” Is a Red Flag?
A quick Google search for “free IP stresser” or “IP stresser free” brings up pages of shady websites offering instant access. Most are illegal or borderline legal services pretending to offer “testing tools.” But what they’re really doing is offering you a way to break the law without making you think too hard about it.
These free versions are also bait. Many collect data from your device, log your activity, or come preloaded with malware. If you’re even browsing these services out of curiosity, you’re probably being watched.
Is It Legal to Use an IP Stresser?
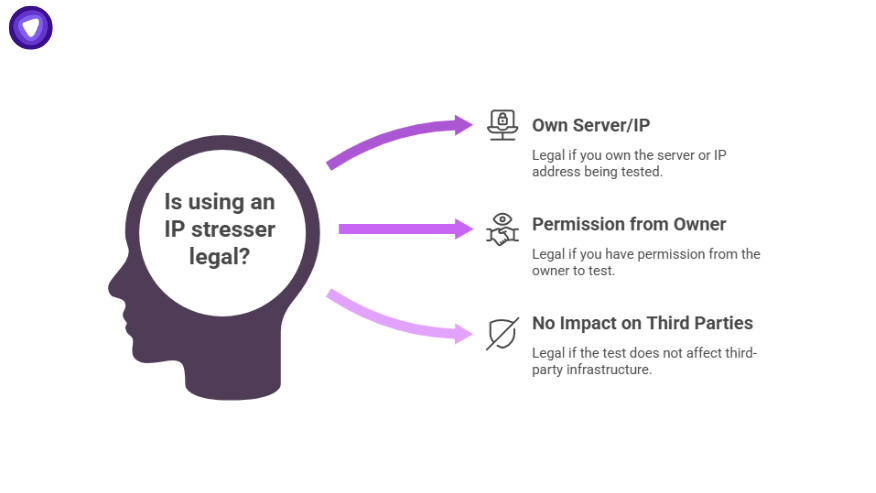
Here’s the key question.
Using an IP stresser is only legal if:
- You own the server or IP address being tested
- You have permission to test from the owner
- The stress test does not impact third-party infrastructure
If you’re using a stresser to test someone else’s network, or you didn’t get formal approval, it’s illegal in most jurisdictions. In the U.S., for example, the Computer Fraud and Abuse Act (CFAA) makes it a federal crime to intentionally disrupt someone else’s system.
And law enforcement isn’t just focused on the sellers. They’re tracking buyers too. Operation PowerOFF, led by the FBI and international agencies, shut down dozens of stresser sites and issued hundreds of warnings and arrests.
IP Stresser Legality Checker (Mini Quiz)
IP Stresser Tools Aren’t Just Hitting Big Companies
There’s a myth that only Fortune 500 companies get hit with DDoS attacks. That’s wrong.
Small businesses, SaaS startups, gaming servers, and crypto platforms are regular targets. Why? Because attackers assume you don’t have the budget or skills to stop them.
Even internal apps, like employee dashboards or partner portals, can be knocked offline with an IP stresser tool.
If you accept logins or data traffic, you’re a target.
How DDoS-for-Hire Services Operate in 2025?
Step 1: Payment via Crypto or Telegram
Buyers use anonymous crypto wallets or Telegram bots to initiate an order—no signup, no oversight.
Step 2: Launch Attack from a Web Panel
They select targets, duration, and intensity via a simple dashboard—like configuring a marketing campaign.
Step 3: Botnet Flood Begins
Botnets or spoofed cloud traffic flood the victim’s IP with millions of requests per minute.
Step 4: Downtime Report Delivered
Attackers get automated success metrics—like “site offline for 3 minutes”—to validate the hit.
Let’s stop calling them “testers.” Many IP stresser services are full-blown DDoS-for-hire platforms:
- Subscription pricing (monthly access to launch attacks)
- Attack customization (you choose layer 4 or layer 7)
- Status reports (uptime logs of victim servers)
- Referral programs (yes, some have affiliate links)
Think of it like SaaS, but for cybercrime.
These services are often marketed on Telegram, Discord, and Reddit (via burner accounts). Some disguise themselves as pen-testing tools. Others don’t even try to hide it.
Common Targets of IP Stresser Attacks
- Online retail during sales: Knock out a competitor’s store to gain sales
- Esports platforms: Disrupt live tournaments to hurt reputations
- Cryptocurrency wallets: Force a timeout, redirect traffic elsewhere
- Fintech APIs: Overload endpoints to trigger false alerts or delays
- Edtech and LMS platforms: Hit login pages before exams or deadlines
These aren’t just stunts. They’re business disruptions.
Are You a Target? IP Stress Risk Evaluator
What IP Stresser Attacks Look Like on Logs?
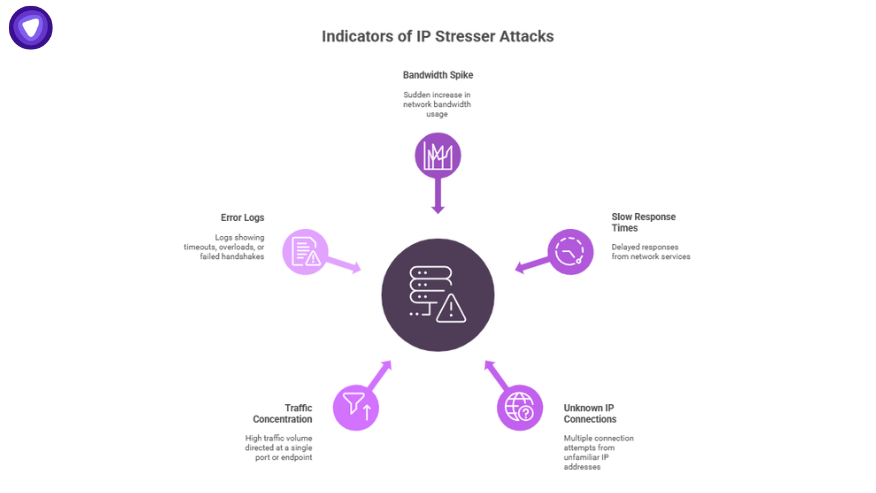
Real-world signs your business is under IP stress:
- Unusual spike in bandwidth usage, often at specific times
- Slower-than-normal response times from a single region
- Multiple connection attempts from unknown IP ranges
- Traffic directed at a single port or endpoint
- Error logs showing timeouts, overloads, or failed handshakes
If you’re seeing these regularly, it’s not a coincidence. Someone is using a tool to hit you repeatedly.
Legal vs. Illegal - The Thin Line Businesses Need to Know
| Intent | Legal | Illegal |
| Testing own server | ✅ With permission | ❌ Without permission |
| Renting stresser tool | ✅ If used internally with documentation | ❌ If used on external networks |
| Attacking competitors | ❌ Always illegal | ❌ Criminal charges likely |
| Using “Free” stressers | ❌ Often linked to malware/phishing | ❌ High legal and security risk |
Legal vs. Illegal IP Stresser Use
Best Practice: Always retain written consent (email or signed doc) if it’s not your infrastructure.
Example: Pen-testing your staging environment before launch.
Example: Overloading a competitor’s website to disrupt their service.
Risk: You could get caught in sting operations or end up violating laws unknowingly.
Example: Signing up for a no-verification DDoS tool and targeting a gaming server.
Use case: Cybersecurity training or red team exercises using isolated test environments.
VPNs As A Defensive Measure Against DDoS Attacks
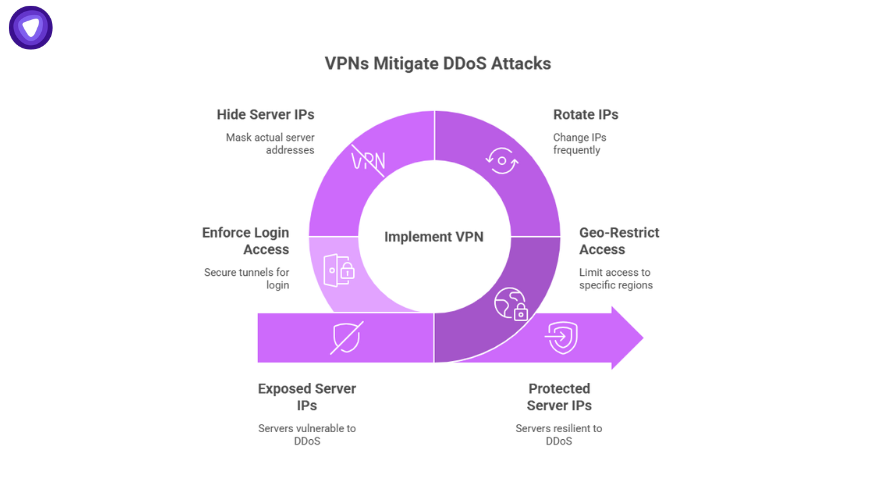
VPNs are not just for user privacy. In B2B environments, they’re a network control layer.
When combined with anti-DDoS strategies, a white-label VPN lets you:
- Geo-restrict access to sensitive endpoints
- Rotate IPs to make targeted attacks harder
- Hide actual server IPs from being publicly exposed
- Enforce login access through secure tunnels only
At PureVPN, our partners use white-label VPNs to give their clients private tunnels to critical tools, CRM systems, databases, and billing platforms. If the public doesn’t see the endpoint, attackers can’t hit it with an IP stresser.
Preventive Steps to Stay Off IP Stresser Radars
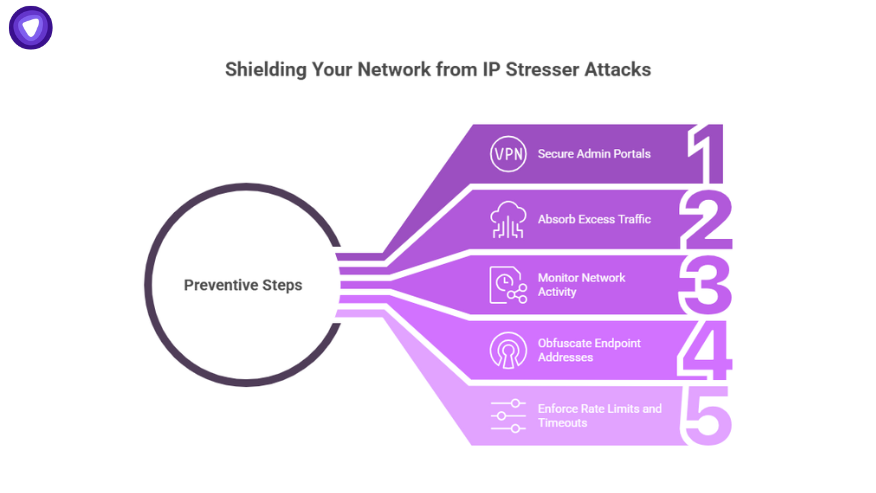
- Don’t expose admin portals publicly. Use VPN-based access.
- Use a CDN or anti-DDoS service to absorb excess traffic.
- Monitor bandwidth and port activity in real time.
- Obfuscate or randomize endpoint addresses when possible.
- Set rate limits per IP and enforce connection timeouts.
What to Do If You’ve Been Targeted?
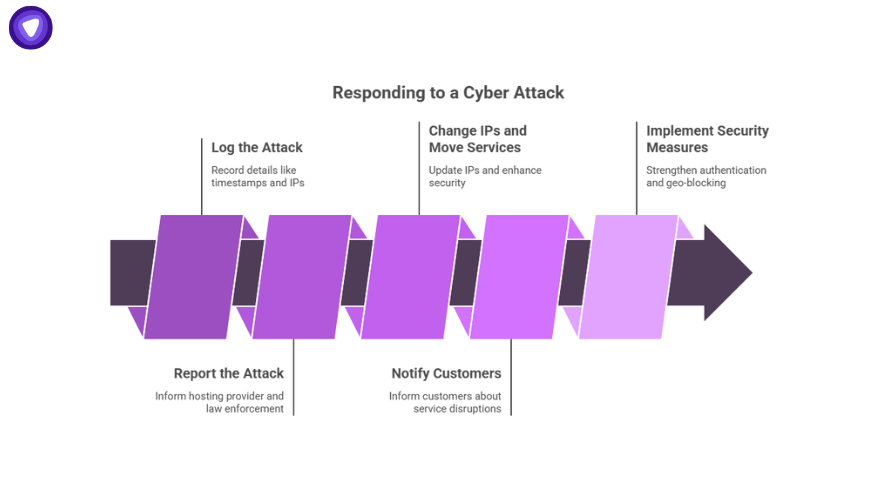
- Log the attack. Keep timestamps, IPs, and payload types.
- Report it. Contact your hosting provider and law enforcement if needed.
- Change exposed IPs and move services behind VPN or proxy layers.
- Notify your customers if the downtime affected them.
- Implement authentication hardening and geo-blocking.
Why Businesses Need to Care About This Now?
Ignoring IP stressers is like ignoring spam in the ‘90s. It might seem minor today—but as these tools become more automated, they’ll be used in everything from ransomware setups to extortion attempts.
Every time your system goes offline, you lose customer trust. You lose revenue. And sometimes, you lose data.
Final Thoughts
IP stresser attacks aren’t a niche threat anymore. They’re a service anyone can buy, use, and automate. That includes your competitors, disgruntled ex-employees, or even bored teenagers.
If your service is publicly accessible, it’s fair game.
But the good news is, you don’t need to reinvent your infrastructure to protect it.
With PureWL’s White-Label VPN platform, you can:
- Shield high-risk portals with IP-controlled tunnels
- Offer your own branded VPN service to clients and teams
- Build DDoS resistance into your product ecosystem
Ready to make your platform harder to target?


