If you’ve ever run a privacy check on browserleaks.com, the results can be surprising. Without installing anything, it shows exactly what your browser and network reveal to the outside world. For a casual user, that’s interesting. For a business, it’s a security and compliance signal.
Whether you run a SaaS platform, manage corporate endpoints, or handle sensitive customer data, knowing what your browser leaks is part of the bigger network security picture. In this guide, we’ll unpack the common BrowserLeaks test results, explain what each section means, and show what you can do about it.
- What It Shows: BrowserLeaks reveals IP, DNS resolvers, WebRTC endpoints, JavaScript fingerprints, and TLS details.
- Safe Collection: All data comes from standard browser features—no exploitation involved.
- IP Panel Risk: Public and local IPs can enable geo-location, profiling, and identity correlation.
- DNS Leak Detection: Mismatched DNS resolvers indicate VPN or policy bypass risks.
- WebRTC Leak Risk: Can reveal IPs even with VPN if not routed properly.
- Fingerprint Tracking: JavaScript and TLS/JA3 details can create persistent browser/device fingerprints.
- Business Impact: DNS leaks, IP/WebRTC leaks, and stable fingerprints are key threats.
- Prevention: Enforce VPN egress, secure DNS, WebRTC rules, and standard browser builds.
- PureWL Solution: White-label VPN to enforce these protections across all users and devices.
What is BrowserLeaks?
BrowserLeaks is a collection of browser-based tests that reveal the information websites and third parties can gather about you just by loading a page. This includes your public IP address, DNS resolver details, WebRTC endpoints, JavaScript-based fingerprints, and more.
It doesn’t hack or exploit your device. It simply uses built-in browser capabilities and standard network behavior to display what’s already being shared.
Why It Matters for Businesses?
For an individual, leaking an IP or DNS server might just mean targeted ads. For a business, it can be more serious:
- Regulatory compliance issues (GDPR, HIPAA, PCI DSS).
- Increased risk of targeted phishing or fraud.
- Data correlation between sessions, even if cookies are cleared.
- Reputation damage if customer traffic isn’t handled securely.
How BrowserLeaks Works?
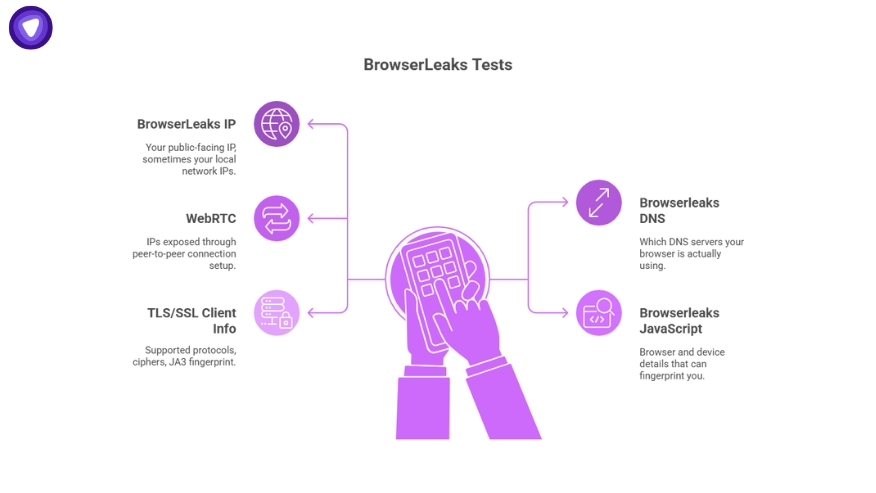
The site runs separate tests for different privacy vectors. Each test focuses on a specific data point. Think of it as multiple panels in a dashboard:
- BrowserLeaks IP – Your public-facing IP, sometimes your local network IPs.
- Browserleaks DNS – Which DNS servers your browser is actually using.
- WebRTC – IPs exposed through peer-to-peer connection setup.
- Browserleaks JavaScript – Browser and device details that can fingerprint you.
- TLS/SSL Client Info – Supported protocols, ciphers, JA3 fingerprint.
Interpreting the IP Test
When you run the IP panel, you’ll usually see two main things:
- Public IP – The address visible to the outside world. This is often your ISP’s IP unless you’re using a VPN or proxy.
- Local IP – Sometimes revealed via WebRTC, showing internal network addresses.
Why it’s important:
- A public IP can be used for geo-location, access control decisions, or blocking.
- A local IP can help attackers profile your network setup.
How to control it:
- Use a corporate VPN that forces all traffic through a controlled egress point.
- Implement a kill switch to prevent fallback to ISP routing if the VPN drops.
- Rotate or fix egress IPs depending on your fraud prevention needs.
Tools like IPleak or the IP section of BrowserLeaks can quickly confirm if your VPN is working as intended.
DNS Leak Tests
The DNS section or DNSleaktest shows which DNS resolvers your system is using to translate domain names into IP addresses. Even if your IP is masked by a VPN, your DNS traffic might go through your ISP, creating a DNS leak.
Why it’s important:
- Reveals your ISP or corporate network to visited sites.
- Allows tracking based on DNS queries.
- Enables censorship or filtering by the resolver.
How to control it:
- Ensure your VPN pushes its own DNS servers.
- Use DNS over HTTPS (DoH) or DNS over TLS (DoT) to encrypt DNS queries.
- Block split-DNS leakage for sensitive queries.
Run the Browserleaks DNS panel to check if your resolver matches your intended configuration.
WebRTC Leaks
WebRTC is a technology used for real-time communications like video calls. It can also reveal IP addresses during the peer discovery process, bypassing some proxy or VPN setups.
Risk factors:
- Public IP exposure even when on a VPN.
- Local IP exposure, which can help correlate activity.
Control methods:
- Set browser policies to route WebRTC over the VPN.
- Use extensions or enterprise settings to block non-proxied ICE candidates.
- Test after changes to avoid breaking legitimate video apps.
JavaScript-Based Fingerprinting
The Browserleaks JavaScript panel reveals a lot: user agent, screen resolution, installed fonts, Canvas and WebGL fingerprints, time zone, language, and more. Each piece may seem harmless, but combined, they can create a unique fingerprint.
Business risks:
- Cross-site tracking without cookies.
- Identifying corporate machines across multiple services.
Controls:
- Use browser privacy modes that reduce fingerprinting entropy.
- Standardize corporate browser builds with uniform fonts and extensions.
- Consider privacy headers and policies for internal applications.
TLS/SSL Client Info and JA3 Fingerprinting
The TLS panel shows which protocols and ciphers your browser supports, along with a JA3 fingerprint, a hash that can identify a specific client configuration.
Why it matters:
- JA3 can be used by detection systems to track or block traffic.
- Outdated protocols or ciphers are a security risk.
Controls:
- Keep browsers and underlying SSL libraries updated.
- Avoid non-standard client tweaks unless required.
- For enterprise traffic, standardize TLS configurations across endpoints.
Reading a BrowserLeaks Report Step-by-Step
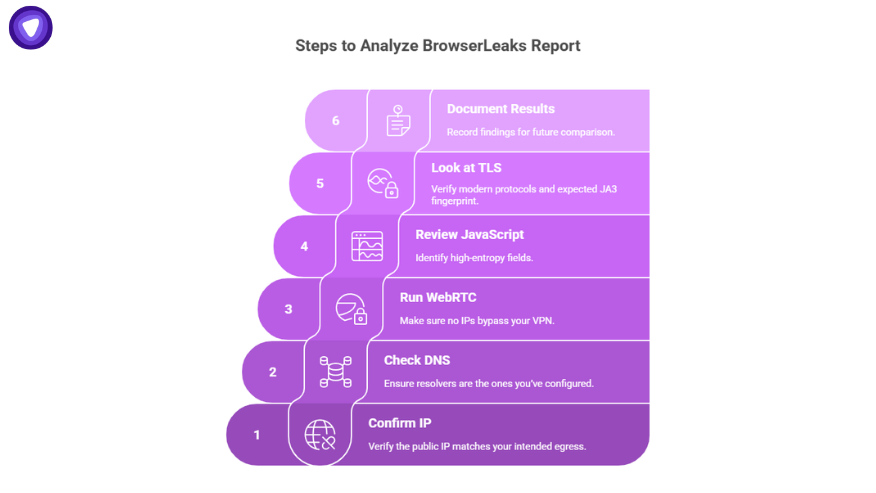
- Start with IP – Confirm the public IP matches your intended egress.
- Check DNS – Ensure resolvers are the ones you’ve configured.
- Run WebRTC – Make sure no IPs bypass your VPN.
- Review JavaScript data – Identify high-entropy fields.
- Look at TLS – Verify modern protocols and expected JA3 fingerprint.
Document the results and compare them over time to detect configuration drift.
What Matters Most for Businesses?
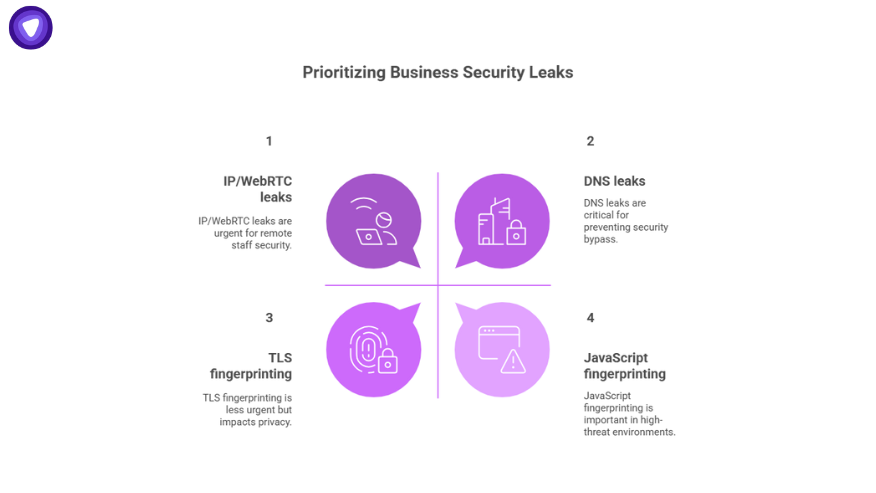
Not every leak is equally urgent. For most corporate environments:
- DNS leaks are high priority—fixing them prevents bypass of your security perimeter.
- IP/WebRTC leaks are next—especially for remote or hybrid staff.
- TLS fingerprinting is a concern for privacy and evasion of certain network blocks.
- JavaScript fingerprinting can be important in regulated or high-threat environments.
How to Fix Common Issues?
- DNS leaks – Use VPN-pushed DNS, enforce DoH/DoT via browser or OS policy.
- IP leaks – Always-on VPN with kill switch.
- WebRTC leaks – Policy-based restrictions or controlled ICE candidates.
- Fingerprinting – Standardized browser builds, privacy extensions, managed configurations.
- TLS risks – Regular updates, disable outdated ciphers.
Business Implementation Playbook
For SMBs:
- Deploy VPN clients with pre-configured DNS.
- Train employees to run periodic checks on BrowserLeaks.
- Use a standard browser build with WebRTC policies.
For Enterprises:
- Integrate leak tests into endpoint compliance checks.
- Monitor DNS resolver logs for anomalies.
- Include BrowserLeaks results in quarterly security reviews.
Metrics to Track
- Percentage of endpoints without DNS leaks.
- Frequency of IP mismatches between VPN and BrowserLeaks tests.
- Stability of JA3 fingerprints across devices.
- Number of WebRTC candidates outside the secure path.
Final Thoughts
Running a BrowserLeaks test shows you exactly what your browser is telling the world. If the results match your security policies, you’re in good shape. If they don’t, you have a clear list of what to fix.
For businesses, the best fix is layered. Proper browser policies plus a VPN that enforces DNS, masks IP, and handles WebRTC correctly. With PureVPN White Label, you can offer your own branded VPN service to customers or staff, ensuring consistent privacy controls at the network level. It’s a way to protect your users, meet compliance, and keep your brand front and center.