- Build vs Buy: Most teams can build a VPN, but the strategic question is whether it should be owned infrastructure or a leveraged capability.
- Supporting Feature: VPNs in portfolio expansion are supporting features, enhancing existing products, not primary value propositions.
- Hidden Costs: Building a VPN internally carries high costs, ongoing maintenance, compliance risk, and diverts engineering focus from core product work.
- White-Label Advantage: Buying a white-label VPN reduces operational burden, speeds deployment, and preserves internal focus on innovation.
- Decision Framework: Use a checklist to assess differentiation, operational load, compliance exposure, and opportunity cost before choosing build or buy.
Building a VPN isn’t a side project. It requires specialized security expertise, resilient global infrastructure, and continuous operational oversight.
For most teams, the decision comes early: invest heavily in building and maintaining VPN infrastructure, or leverage an existing capability designed to handle that complexity. That choice defines cost exposure, operational risk, and long-term execution.
If you are wondering whether to buy or build a VPN, this guide will help you make the right decision by the end.
What VPN Portfolio Expansion Actually Means?
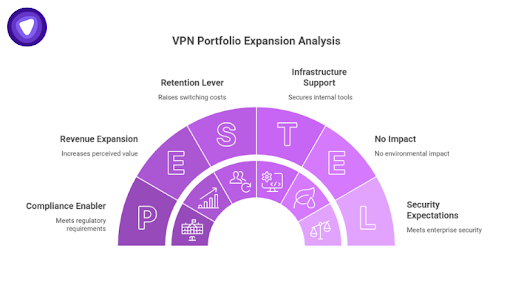
VPN portfolio expansion is often misunderstood as launching a new product line.
In practice, it usually means adding encrypted connectivity to strengthen an existing offering. The VPN is not the value proposition. It is an enabling layer that supports broader business goals.
Common roles VPNs play in portfolio expansion include:
- A bundled feature that increases perceived completeness of a product
- A revenue expansion layer attached to higher-tier plans
- A compliance enabler that removes objections in regulated industries
- A retention lever that raises switching costs for existing customers
These roles show up across multiple industries.
Common scenarios where VPNs are added as part of portfolio expansion:
- SaaS platforms add VPNs to meet enterprise security and access expectations
- MSPs standardize VPN access to reduce client-side support variability
- Connectivity and eSIM platforms encrypt traffic to protect user sessions
- Fintech and data platforms use VPNs to secure internal tools and remote workflows
Across these scenarios, the VPN is supporting infrastructure. It rarely drives purchases directly but enables renewals, upgrades, and procurement approvals. Treating it as primary innovation misallocates resources and weakens differentiation.
The Build Path and What It Really Involves?
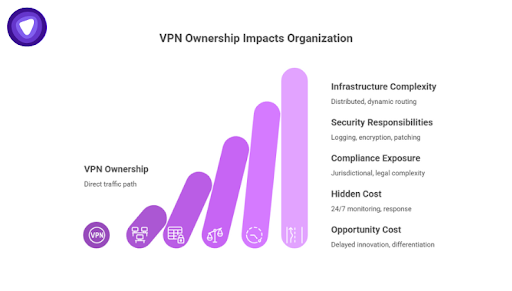
Building a VPN is often framed as a finite project. That framing underestimates the scope of responsibility that begins once the system goes live.
- Infrastructure and Network Complexity
A production VPN requires a distributed infrastructure by design.
At a minimum, this includes server deployment across multiple regions to keep latency within acceptable bounds. Traffic must be routed dynamically to account for congestion, outages, and regional demand shifts. Redundancy planning is required to prevent single points of failure, and failover mechanisms must activate without disrupting user sessions.
These systems cannot be static. As usage grows, traffic patterns change. New regions introduce new network providers. Performance expectations rise. Each expansion increases operational complexity rather than reducing it.
Infrastructure decisions made early tend to persist. Reworking them later is expensive and risky.
- Security and Privacy Responsibilities
Operating a VPN places the organization directly in the path of user traffic.
Key responsibilities include:
- Define and enforce logging policies.
- Manage encryption keys: generate, store, rotate, protect.
- Keep protocols up to date and patched.
- Continuously mitigate threats; VPNs are high-value targets.
- Prevent misconfigurations or outdated components.
- Treat failures as trust failures, not just technical issues.
Maintaining these security responsibilities is critical. 48% of organizations have experienced a VPN‑related cyberattack, with many suffering repeated incidents, underscoring persistent risks in traditional VPN security models.
- Compliance and Legal Exposure
VPNs operate across borders by default.
This introduces jurisdictional complexity that many teams underestimate. Data retention laws vary by region, with regulations such as GDPR imposing strict requirements on how user data is collected, processed, stored, and disclosed.
Law enforcement requests follow different procedures depending on location, often requiring documented response workflows and legal review. Enterprise customers may require audits, compliance reports, and formal assurances tied to standards like ISO/IEC 27001 or equivalent frameworks. These requirements extend far beyond the VPN feature itself.
Compliance obligations do not scale linearly. Each new market introduces new constraints, additional documentation, and ongoing audit responsibilities. Achieving and maintaining these certifications is often the most resource-intensive part of operating a VPN, demanding dedicated legal, security, and compliance functions.
Even if VPNs represent a small percentage of revenue, the legal and regulatory exposure applies to the entire organization.
Read more on compliance with relevance to VPNs here.
- Maintenance Is the Hidden Cost
Maintenance is the least visible and most persistent cost of building a VPN.
It includes 24/7 monitoring, incident response, and capacity planning. Client applications must be continuously updated across operating systems and device types. OS-level changes frequently disrupt tunneling behavior, permissions, or network stacks. Traffic spikes demand rapid scaling to prevent degraded performance or outages.
None of this work advances the product roadmap. It exists purely to keep the system stable. In practice, ongoing operational expenses for a VPN provider, including server hosting, bandwidth, software maintenance, and technical support, can easily range from about $23,000 to over $100,000 per month once you account for infrastructure, support teams, security, and compliance costs.
These recurring costs quickly eclipse the initial development effort, making maintenance one of the most substantial ongoing investments in running a VPN.
Read more on how to set up branded VPN apps across all operating systems here.
- Opportunity Cost
Opportunity cost rarely appears in planning documents, but it has real impact. When engineers build and maintain a VPN, they are not building core differentiating features or shipping customer-requested improvements.
They are not refining performance in areas that directly affect user engagement or revenue.
VPNs rarely provide competitive advantage; customers expect them to work reliably and quietly. Excellence is invisible, while failures are highly visible.
Owning infrastructure also slows roadmap velocity. Every system requires ongoing monitoring, security, and documentation. Over time, teams drift toward maintenance work, leaving less capacity to innovate.
The Buy Path and What You Are Actually Buying
Buying a white-label VPN is often called outsourcing, but that misses the bigger picture.
It means leveraging pre-built, enterprise-grade infrastructure with global servers, redundancy, and automated protocol updates. Teams avoid the millions of dollars and months of engineering needed to build and maintain it, while keeping full control over branding, pricing, and user experience.
In the VPN context, the hardest problems aren’t features. They are scale, reliability, jurisdictional coverage, and performance under unpredictable traffic. Enterprise-grade white-label platforms absorb these challenges at the infrastructure level, so partners don’t have to solve them from scratch.
At its core, buying a white-label VPN is about tapping into a proven global network that most teams only encounter after months, or years, of production experience.
Build vs Buy: Side-by-Side Strategic Comparison
The following comparison focuses on dimensions that affect long-term execution rather than initial excitement.
| Dimension | Build In‑House | Buy / White‑Label |
| Time to market | Extended development and testing cycles. Estimates for moderately complex VPN development range from 6–9 months. | Deployment can be measured in weeks once integration begins. |
| Upfront cost | High engineering and infrastructure investment; fully loaded engineering cost often exceeds $96,000/year. | Controlled onboarding cost with predictable budgeting. |
| Ongoing operations | Continuous staffing, monitoring, and tooling required. | Managed externally; updates, patching, and scaling handled by the provider. |
| Security risk | Fully internal responsibility for secure code, protocols, and incidents. | Shared responsibility with a specialized provider. |
| Compliance burden | Direct legal exposure; must adhere to jurisdictional requirements, audits, and data retention laws. | Reduced operational scope; provider handles compliance complexities. |
| Engineering focus | Infrastructure maintenance dominates internal capacity. | Focus stays on product development and customer experience. |
| Scalability | Requires careful planning as traffic and regions grow. | Designed for demand variability and regional expansion. |
| Opportunity cost | Significant; engineering resources diverted from core roadmap. | Limited; internal teams stay focused on primary product goals. |
Why This Matters
Building a VPN internally is not a one-off effort. Distributed systems, global infrastructure, and maintenance overhead create persistent cost and operational burden.
Neutral research shows that complexity in distributed systems increases both development time and ongoing management effort, even after launch.
By contrast, white-label solutions allow teams to focus on product innovation and customer experience while leveraging mature infrastructure already built for scale and security.
Opportunity Cost and the Part Most Teams Ignore
Opportunity cost rarely appears in planning documents, but it has real impact. When engineers build and maintain a VPN:
- They are not building core differentiating features or shipping customer-requested improvements.
- VPNs rarely provide competitive advantage; they are expected to work reliably and quietly.
- Infrastructure ownership slows roadmap velocity; every system must be monitored, secured, documented, and defended.
- Teams risk becoming maintenance-focused, diverting attention from strategic initiatives.
“Every system you own becomes a system you must defend.”
This means that internal VPN projects carry hidden tradeoffs. Time and resources spent on maintenance are time not spent on innovation or market-facing improvements.
Even small infrastructure decisions compound, creating persistent operational drag that can slow product evolution, delay feature launches, and reduce the team’s ability to respond to competitive pressures.
Recognizing these costs early allows leadership to evaluate whether owning a VPN aligns with strategic priorities or simply shifts focus away from what truly drives business growth.
When Building Does Make Sense?
Building a VPN is appropriate when ownership directly aligns with strategic differentiation rather than serving as a supporting feature. Common scenarios include:
- Core business is networking or VPN technology: VPN capabilities are central to the product, not just an add-on.
- Unique protocol innovation: Products require performance or protocol-level features that cannot be abstracted.
- Regulatory requirements: Full control over infrastructure and data paths is mandated by law or compliance frameworks.
- Teams with global infrastructure expertise: Existing capabilities reduce marginal cost and operational risk.
In these cases, ownership is strategic. Partial investment or incomplete infrastructure exposes the team to operational risk without delivering a meaningful advantage.
When Buying Is the Strategic Move?
Buying a VPN is the strategic choice when execution efficiency outweighs infrastructure ownership. It is ideal for organizations where VPNs are supporting features rather than core differentiators. Key scenarios include:
- Speed-to-market matters: Deployment and integration can happen quickly without waiting for in-house development.
- VPN is a supporting feature: The VPN enhances the product but is not central to differentiation.
- Limited security engineering bandwidth: Internal teams cannot dedicate the required resources for continuous protocol updates, patching, and threat mitigation.
- Desire to bundle VPN with other services: Security can be offered as part of a broader solution rather than a standalone product.
- Need for predictable costs: White-label solutions provide stable onboarding and operational expenses.
In these situations, the focus is on preserving internal capacity, maintaining roadmap velocity, and embedding secure connectivity without taking on unnecessary operational burden.
Decision Framework Checklist
Use this checklist to guide internal alignment and clarify whether to build or buy a VPN. Each question highlights a strategic tradeoff:
- Is VPN functionality central to differentiation or supportive?
- Do we want to operate global infrastructure indefinitely?
- Are we prepared for jurisdictional and compliance exposure?
- Will this decision accelerate or slow product delivery?
- Are customers requesting this now or only hypothetically?
- Does this investment compound over time or create drag?
After completing this checklist, leadership can clearly see where internal resources are best allocated.
If multiple answers indicate ongoing operational burden or slow roadmap velocity, it signals that a white-label solution could preserve focus, reduce risk, and accelerate strategic outcomes.
This ensures the VPN decision supports long-term goals rather than becoming a maintenance distraction.
Final Thoughts
Both building and buying a VPN are valid. The real decision should be based on strategic clarity, not technical confidence. VPNs are mature infrastructure, and rebuilding them rarely adds advantage when they serve as a supporting feature.
White-label VPN platforms provide a solved execution layer, shifting the differentiator to how security is integrated and delivered within your product. PureVPN White Label VPN Solution removes operational burden while enabling portfolio expansion, letting teams focus on core priorities instead of infrastructure maintenance.
The next step is not deciding whether a VPN can be built. It is deciding how it fits into cost models, product architecture, and long-term strategy, the point where durable outcomes are determined.