- The October 2025 Canadian Tire breach exposed data from over 1.3 million e-commerce accounts, revealing how non-core systems can become major security weak points.
- Sensitive information like names, emails, and partial credit card details was exposed, though banking and rewards systems remained secure.
- The company’s fast response contained the incident within 48 hours, but public trust concerns underline the importance of transparent communication.
- Retailers must prioritize data segmentation, zero-trust frameworks, and encrypted remote access to prevent similar breaches.
- Solutions like PureVPN’s White-Label VPN help businesses secure connections, protect customer data, and maintain brand trust in an evolving cyber threat landscape.
When a household brand like Canadian Tire becomes the subject of a major cybersecurity breach, it shakes more than just customer confidence; it challenges the very assumptions many businesses hold about their own digital resilience.
The October 2025 incident exposed vulnerabilities not in a core banking or payment system, but within the company’s e-commerce infrastructure, an environment often seen as safe, yet increasingly targeted by sophisticated threat actors.
This breach serves as a reminder that attackers no longer need to breach a company’s most important networks to cause serious disruption; a single overlooked access point can compromise thousands of customer records.
How the Breach Unfolded?
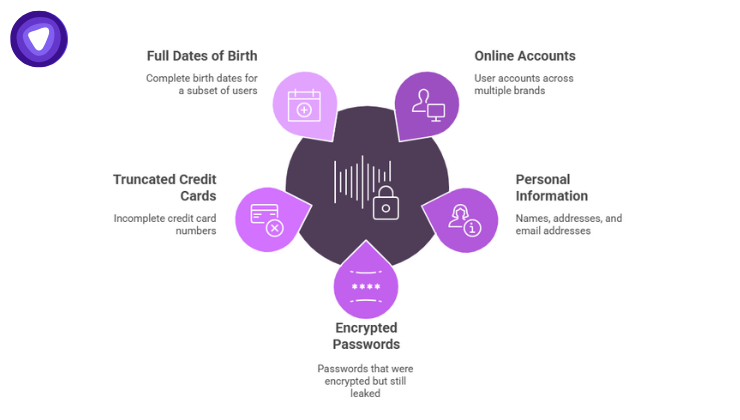
On October 2, 2025, Canadian Tire Corporation (CTC) identified unusual activity in a system tied to its online platforms.
Key findings:
- The compromised database was connected to online accounts under multiple brands, Canadian Tire, SportChek, Mark’s/L’Équipeur, and Party City.
- Exposed information: names, addresses, email addresses, and year of birth.
- Encrypted passwords and truncated credit card numbers (incomplete digits that cannot be used for purchases) were also leaked.
- For under 150,000 users, full dates of birth were included.
- The Canadian Tire Bank and Triangle Rewards systems were not impacted.
The event demonstrates that even secondary databases, not directly tied to financial systems, can become entry points for major data exposures.
Impact Scope and Affected Systems
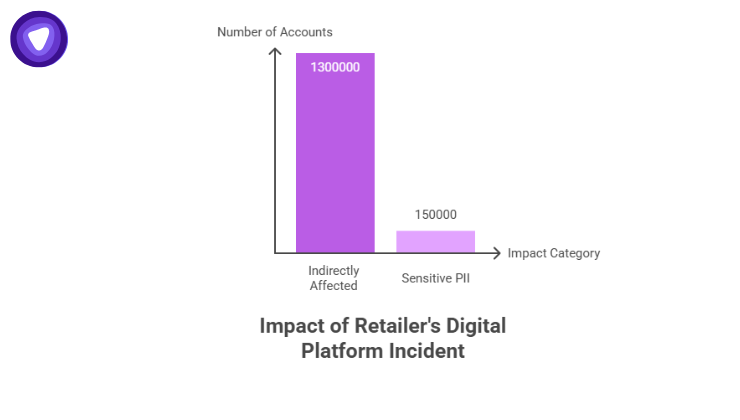
The Canadian Tire data breach 2025 primarily involved e-commerce accounts and not financial systems, but the exposure was still significant.
Reported Impact Summary
- Approx. 1.3 million accounts linked to the retailer’s digital platforms were indirectly affected through exposure or precautionary resets.
- Fewer than 150,000 accounts included full DOBs, which Canadian privacy law classifies as sensitive PII.
- Encrypted passwords used SHA-256 with salts, reducing but not eliminating password-reuse risk.
- The incident was contained within 48 hours, according to company statements.
This scale aligns with 2025’s broader trend: retail and wholesale sectors represented 25% of all reported breaches, highlighting how attackers exploit retail’s large customer databases.
What It Means for Customers and Retailers
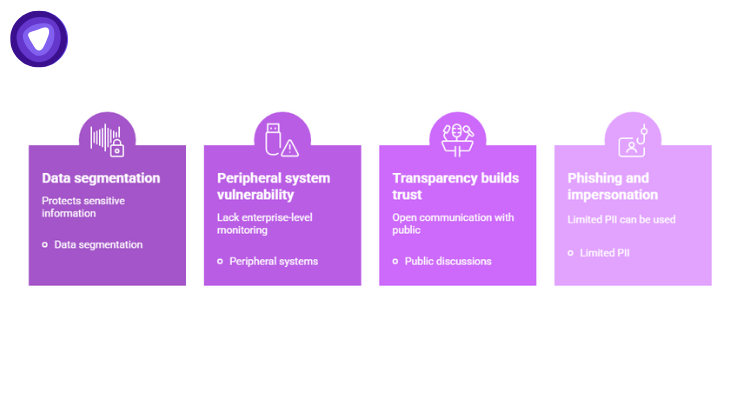
The Canadian Tire breach serves as a reminder that a single incident can have two sides, one affecting individual users directly, and another exposing systemic gaps in retail cybersecurity.
For Customers
- Even limited PII (like name + email + birth year) can power phishing and impersonation scams.
- Credential reuse remains a serious risk, changing passwords immediately is essential.
- Monitoring credit activity and bank statements remains critical even if full financial data wasn’t leaked.
For Retailers and IT Leaders
- Peripheral systems often lack enterprise-level monitoring, a key vulnerability.
- The separation that protected Canadian Tire Bank shows data segmentation works, but consistent enforcement is required.
- Public discussions on Reddit and forums reveal how transparency and timing in incident response shape public trust.
- Preventive investment in network segmentation and access management costs less than post-breach recovery.
The Company’s Response and Public Reaction
Canadian Tire quickly identified and fixed the vulnerability, confirming that no in-store or payment systems were affected. Only customers with full DOB exposure were notified, in compliance with PIPEDA. Public reaction was mixed, some criticized limited transparency, while experts noted the swift response likely minimized impact.
Actionable Steps for Affected Customers

If you’ve used a Canadian Tire e-commerce account, take these precautions immediately:
- Change your password and ensure it’s unique across platforms.
- Enable multi-factor authentication (MFA) where available.
- Monitor bank statements and credit reports for any irregular activity.
- Be cautious of phishing emails claiming refunds or compensation related to the Canadian Tire data breach refund.
- Wait for official contact from Canadian Tire or TransUnion Canada if your data was part of the affected subset.
Quick Summary Table
Key aspects of the data breach explained:
| Aspect | Details |
| Date Identified | October 2, 2025 |
| Affected Systems | E-commerce account database across multiple retail brands |
| Data Types | Names, addresses, emails, birth year, encrypted passwords, truncated card numbers |
| Full DOB Records | < 150,000 accounts |
| Unaffected Systems | Canadian Tire Bank, Triangle Rewards |
| Recommended Actions | Change passwords, enable MFA, monitor activity |
What IT Leaders Can Learn?
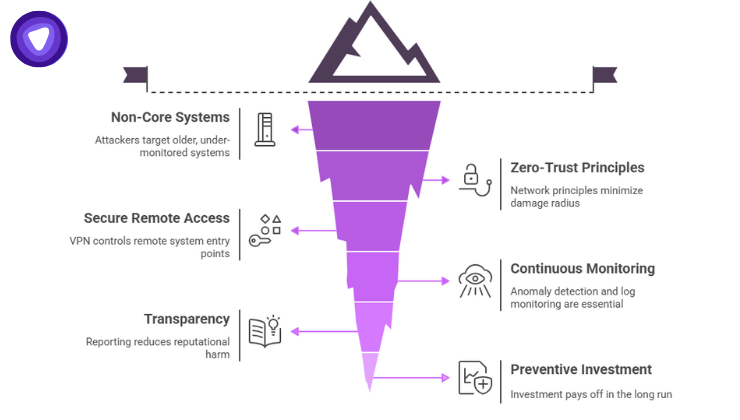
The Canadian Tire data breach 2025 highlights critical lessons for IT and cybersecurity managers:
- Attackers target non-core systems first, especially older or under-monitored ones.
- Zero-trust network principles and data segmentation minimize damage radius.
- Secure VPN or Dedicated IP access helps control remote system entry points.
- Continuous anomaly detection and log monitoring are essential, not optional.
- Transparency in reporting reduces reputational harm and regulatory fallout.
- Preventive investment pays off: Over 300 million individual records have already been exposed globally in 2025, across nearly 800 breaches.
Broader Context: Retail’s Rising Cyber Risk
The Canadian Tire breach reflects a wider retail trend, cyber incidents are rising fast as e-commerce and third-party integrations expand. Credential attacks are up 37% year-over-year, and API-related breaches make up 19% of all retail exposures.
With 64% of consumers less likely to shop after a breach, securing customer data through encryption, segmentation, and controlled access is now essential, not optional.
Long-Term Security Recommendations
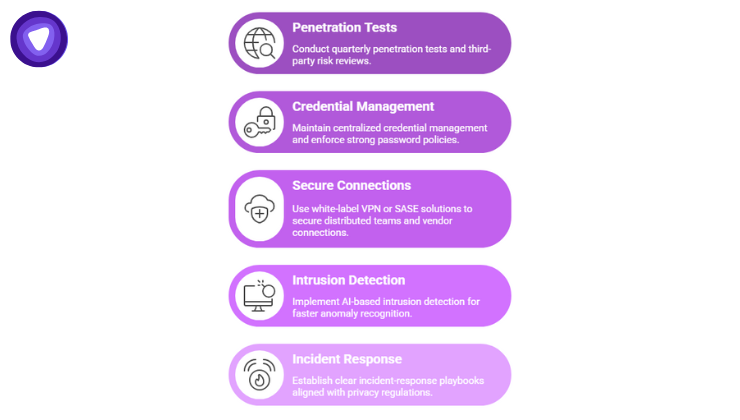
For IT teams and business leaders in retail, this breach should spark long-term architectural changes:
- Conduct quarterly penetration tests and third-party risk reviews.
- Maintain centralized credential management and enforce strong password policies.
- Use white-label VPN or SASE solutions to secure distributed teams and vendor connections.
- Implement AI-based intrusion detection for faster anomaly recognition.
- Establish clear incident-response playbooks aligned with privacy regulations.
How PureVPN’s White-Label VPN Solution Helps
PureVPN’s White-Label VPN solution enables retailers and service providers to strengthen customer trust while adding a new revenue stream. It delivers secure, encrypted connections that safeguard user data across online transactions and backend systems.
With customizable branding, Dedicated IP options, and centralized management, businesses can offer private, secure browsing experiences under their own brand, reducing exposure to credential abuse, third-party risks, and API-based breaches.
Final Thoughts
The Canadian Tire data breach update is more than a corporate incident, it’s a warning sign for every retailer operating online. Protecting digital assets now demands more than compliance checklists; it requires constant monitoring, data segmentation, and secure access control across all systems.
Retailers that integrate solutions like Dedicated IP or white-label VPN access layers will strengthen both internal defense and customer trust. In today’s cyber climate, prevention and transparency are not competitive advantages, they are survival strategies.


