- The Martinelli Scam tricks users into clicking fake video or app upgrade links, spreading malware and stealing personal data.
- It resurfaces frequently due to messaging app trust, fear and curiosity triggers, and reuse of old scam frameworks.
- Victims risk malware installation, data theft, account takeover, and spreading the scam to contacts.
- Protection includes verifying messages, installing apps only from official stores, updating OS and apps, limiting permissions, enabling two-step verification, and backing up data.
- PureVPN White Label VPN Solution helps secure remote access by encrypting connections and enforcing device-level security, reducing exposure from targeted scams.
When a message appears claiming there is a video called “Martinelli” that you must not open, it often seems harmless at first. But the resurfacing of the Martinelli Scam proves that even simple-looking messages can carry serious threats. Beyond curiosity, these scams can compromise personal data, contacts, and devices, making awareness essential.
This blog explores how the Martinelli Scam spreads, the risks involved, and practical ways to protect yourself and your organization
What the Martinelli Scam Actually Is
The “Martinelli Scam” is a variant of a longstanding scheme tied to the WhatsApp-Gold hoax and other fake “premium upgrade” messages. In the version that resurfaces, users receive a message claiming that there is a “video called Martinelli” or that an upgraded version of WhatsApp, “WhatsApp Gold”, will give them extra functions. But in reality:
- There is no genuine video titled “Martinelli” associated with official WhatsApp updates.
- The link invites users to download a fake app or visit a malicious webpage, which then installs malware or harvests personal data.
- The vehicle for the scam is social engineering via legitimate-looking messaging channels (often chain messages).
In short, the Martinelli Scam is not about a real video, it’s about tricking people into clicking a malicious link under the guise of “you must watch this/upgrade now.”
Why It Is Going Viral Again
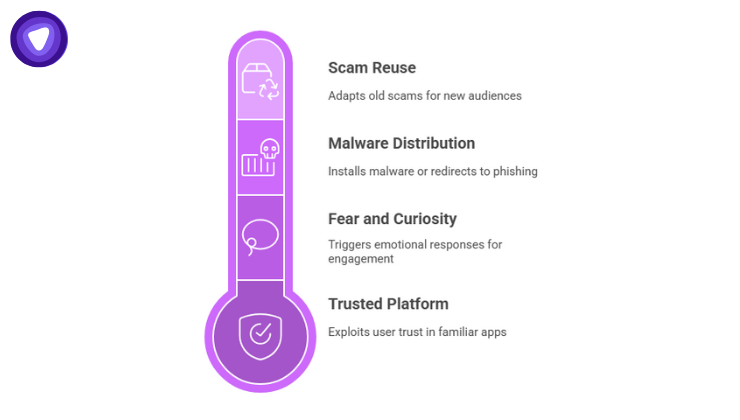
Here are the reasons the Martinelli Scam keeps resurfacing:
1. Trusted Platform Leverage
Messaging apps like WhatsApp have massive adoption, and users often feel safe within a family/friend context. That makes scams delivered through them more effective. For example:
- In Q1 2024 in India, over 43,000 complaints were filed about scam attempts via WhatsApp.
- In 2024 globally, according to Kaspersky, there were 33.3 million mobile malware/adware attacks blocked, about 2.8 million per month.
2. Fear + Curiosity
The “Martinelli” video claim plays on fear (“Don’t watch it”) and curiosity (“What’s this secret video?”). That emotional trigger increases click-throughs.
3. Malware Distribution Efficiency
Once someone clicks, malware can install behind the scenes or redirect to phishing/credential-stealing sites. The fake “WhatsApp Gold” narrative was identified by Action Fraud in early 2019 as back in circulation.
4. Reuse of Old Scams with New Variations
Scam frameworks become templates. The Martinelli/Hollywood-style video threat could be adapted to new countries/languages, making it feel new even if the underlying mechanics are old.
What Victims Face: Risks Beyond a Click
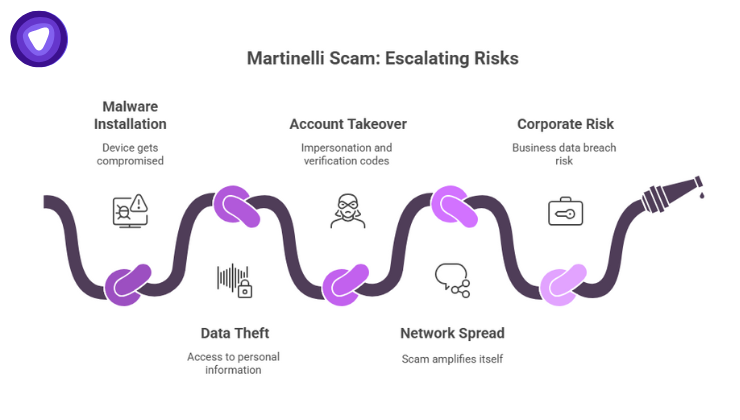
When the Martinelli Scam works, the consequences go beyond annoyance. Key risks:
- Malware installation: The link may prompt you to install a “premium version” of an app or a video player; instead your device gets compromised.
- Data theft or access: Once compromised, the malware can access contacts, messages, photos, or even take over the device.
- Account takeover or credential theft: The attacker might use the device to request verification codes or impersonate you.
- Spread through your network: Because the link often asks you to forward or share with family/friends, the scam amplifies itself.
- Corporate risk: If the compromised device is used for work or connecting into company resources, this becomes a business-data breach risk.
Spotlight: How It Spreads in 2024-25
Scams like these are a reminder that messaging platforms are among the top channels for cyberattacks. In one 2024 dataset, WhatsApp accounted for approximately 49% of reported scam contacts.
| Mechanism | Description | Why it works |
| Chain message in group chats | A message like “Don’t open the Martinelli video! But if you want the link…” | Leverages peer trust in family/friends |
| Fake app download prompt | “Click here to get WhatsApp Gold with exclusive features” | Fake “upgrade” sense tricks users |
| Link redirect to phishing/malware | Once clicked, device redirected to malicious site or APK | Bypasses normal app-store protections |
| Social engineering follow-ups | After install, permissions asked; code/OTP requested | Humans trusting apps override caution |
How to Protect Yourself from the Martinelli Scam
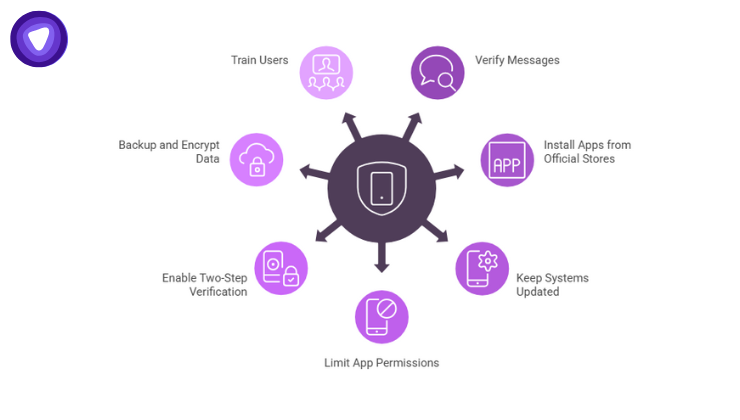
Here are concrete steps to defend against this and similar threats:
Verify Unexpected Messages
- Treat messages claiming there is a “Martinelli video” or “upgrade to WhatsApp Gold” as suspicious.
- Confirm with the sender through a new conversation or call.
Never Install Apps Outside Official Stores
- Legitimate updates to WhatsApp or other major apps come through Google Play Store or Apple App Store, not via unknown links.
Keep OS & Apps Updated
- Mobile malware often exploits outdated systems. In 2024, 1.1 million malicious installation packages were detected.
- Enable automatic updates where possible.
Limit App Permissions
- Avoid granting broad permissions unless absolutely necessary.
- Regularly review what newly installed apps can access.
Enable Two-Step Verification & Account Locking
- For WhatsApp: account > two-step verification > set PIN/email reset.
Backup & Encrypt Data
- Maintain offline or cloud backups of important data.
- Encryption limits exposure if malware gains access.
Train Users & Share Awareness
- Make team members aware that even familiar-looking links can be malicious.
- Devices face around 2.8 million attack attempts per month.
Why Organisations Should Care
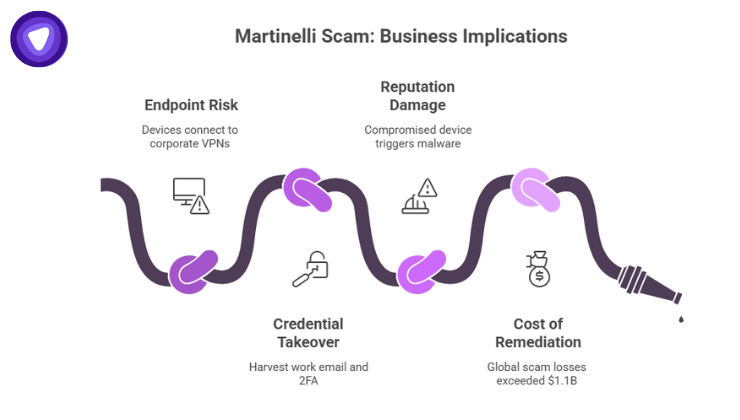
Even if the Martinelli Scam appears targeted at individuals, it has business implications:
- Endpoint risk: Compromised personal devices may connect to corporate VPNs or internal systems.
- Credential takeover: Attackers may harvest work email or 2FA codes via messaging apps.
- Reputation damage: An employee’s compromised device can trigger wider malware outbreaks.
- Cost of remediation: Global scam losses exceeded $1.1 billion in 2024, with malware-enabled scams accounting for $129 million.
How PureVPN White Label VPN Solution Helps
PureVPN White Label VPN Solution provides secure remote-access tools to help mitigate threats like the Martinelli Scam.
It ensures that devices, even if targeted by messaging-app scams, connect to corporate resources through encrypted and controlled channels. PureVPN also enforces device and app-level security policies, reducing exposure from untrusted mobile devices while complementing user training and device hygiene.
Final Thoughts
The Martinelli Scam may seem like a harmless chain message, but it carries genuine risk in the current mobile and remote-access environment. Protecting devices proactively shields both individuals and organizations from what begins as a simple trick and could escalate into data loss or a security breach.


