- Audit automation saves time: White label password managers centralize credential logs, automate reporting, and reduce SOC 2 and ISO 27001 audit prep time by up to 60%.
- Compliance starts with password governance: SOC 2 and ISO 27001 both require evidence of strong access controls, encryption, and policy enforcement, all handled seamlessly by modern password managers.
- Unified visibility builds trust: Centralized dashboards give compliance teams full traceability into user access, policy adherence, and encryption standards.
- Scalable and brand-ready: White label password managers let MSPs, SaaS vendors, and IT resellers integrate compliance features under their own branding with API flexibility.
- PureVPN White Label Password Manager delivers compliance confidence: It provides AES-256 encryption, zero-knowledge security, and automated policy controls, helping teams move from reactive to proactive audit readiness.
Every password your team creates, shares, or stores is part of your compliance story. Yet when audit season arrives, that story often unravels, scattered across spreadsheets, cloud platforms, and forgotten admin accounts. What should be a straightforward proof of control turns into weeks of manual evidence gathering and sleepless nights before auditor reviews.
SOC 2 and ISO 27001 certifications are no longer reserved for big tech companies. Small and mid-size SaaS providers, MSPs, and IT service firms face the same expectations from partners and clients. And one of the most overlooked pillars of these frameworks? Password management compliance.
That’s where a white label password manager quietly becomes a game-changer and an essential compliance tool.
What Are SOC 2 and ISO 27001 Audits?
Both SOC 2 and ISO 27001 are internationally recognized frameworks designed to evaluate how an organization safeguards sensitive data.
- SOC 2 (Service Organization Control 2) audits are based on the Trust Services Criteria developed by the AICPA. They assess whether a company’s security, availability, confidentiality, processing integrity, and privacy practices meet defined standards. The focus is on operational effectiveness and how consistently those controls protect client data.
- ISO 27001, published by the International Organization for Standardization (ISO), establishes a global benchmark for managing information security through a structured Information Security Management System (ISMS). The audit verifies that an organization identifies, mitigates, and continuously monitors information security risks.
In simpler terms, SOC 2 proves you’re doing what you say you do, while ISO 27001 proves you’ve built a repeatable system to keep doing it right. Both demand evidence, and password management is one of the first areas auditors examine.
Why SOC 2 and ISO 27001 Audits Are So Resource-Intensive
Both frameworks demand more than secure logins. They require proof of how access is controlled, monitored, and reviewed.
SOC 2: Focused on Operational Trust
SOC 2 evaluates how effectively an organization protects data under the five Trust Service Criteria: Security, Availability, Processing Integrity, Confidentiality, and Privacy. For password management, the audit typically examines:
- Access provisioning and deprovisioning records
- MFA enforcement and session control
- Encryption standards for stored credentials
- Regular password rotation and monitoring
ISO 27001: Structured Around Continuous Risk Management
ISO 27001 goes deeper, assessing how access control policies are documented, implemented, and maintained over time. Key password-related controls include:
- A.9.2: User access provisioning and review
- A.9.3: User responsibilities for password protection
- A.12.3: Cryptographic controls for password storage
Keeping this documentation consistent across teams, tools, and systems is where most audits start to crack.
Where Most Compliance Teams Lose Time
Even the most disciplined IT departments waste hours gathering fragmented evidence:
- Password logs spread across multiple systems
- Manual exports of credential access reports
- Separate policies for admins and third-party contractors
- Lack of visibility into shared credential use
A 2024 report found that over 62% of compliance teams spend more than half their audit preparation time consolidating access records, a clear sign that manual processes remain one of the biggest compliance bottlenecks.
Each of these inefficiencies delays audit readiness and exposes weak spots. The root cause isn’t just human error, it’s infrastructure fragmentation.
That’s why forward-looking compliance teams are consolidating access management under a single, audit-friendly framework: the white label password manager.
The Compliance Edge of a White Label Password Manager
A white label password manager gives service providers and security vendors a private-labeled platform to manage credentials with full control over branding, user policies, and data architecture.
But beyond branding, its real strength lies in compliance automation.
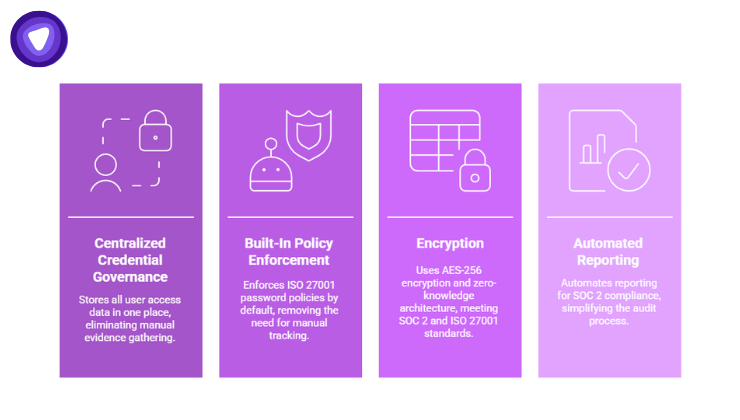
1. Centralized Credential Governance
All user access data, logins, permissions, vault access, and admin actions, is stored in one place. This eliminates the need for manual evidence gathering.
- Every credential has a clear owner.
- Access trails are timestamped and immutable.
- Admins can revoke credentials instantly.
These features directly satisfy SOC 2 password manager requirements related to access traceability and user accountability.
2. Built-In Policy Enforcement
White label solutions can enforce ISO 27001 password policies such as minimum complexity, rotation frequency, and MFA enforcement by default. Compliance teams no longer need to manually track these configurations.
3. Encryption That Matches Audit Expectations
Modern password managers use AES-256 encryption and zero-knowledge architecture, two benchmarks that auditors immediately recognize as compliant with both SOC 2 and ISO 27001 cryptographic control standards.
4. Automated Reporting for SOC 2 Compliance
Custom audit logs, usage summaries, and access control reports can be exported with one click, transforming days of manual work into minutes.
This kind of SOC 2 compliance automation gives auditors the visibility they need without the usual back-and-forth over screenshots or manual documentation.
Traditional vs. White Label Password Management for Compliance Audits
The difference between surviving an audit and passing it confidently often comes down to how efficiently access data is managed. The table below highlights how a white label password manager streamlines compliance compared to traditional tools.
| Criteria | Traditional Password Management | White Label Password Manager |
| Audit Data Collection | Manual, decentralized reports from multiple systems | Automated logs in a unified dashboard |
| Policy Enforcement | Inconsistent enforcement across teams | Centralized policy control for all users |
| Encryption Standards | Varies by tool and storage location | AES-256 encryption with zero-knowledge design |
| Reporting Time for SOC 2/ISO 27001 | Days or weeks of manual exports | Instant, audit-ready reports |
| Visibility for Compliance Teams | Limited visibility into user-level access | Full traceability and detailed access logs |
| Customization | Locked vendor branding and limited admin control | Full rebranding and customizable compliance rules |
| Audit Readiness | Reactive and fragmented | Continuous, automated, and proactive |
How White Label Password Managers Automate Audit Readiness
The difference between being “secure” and being “audit-ready” lies in evidence.
Unified Audit Trails
Every credential action, from creation to revocation, is logged with time, user ID, and action details. These logs create audit-ready password management records auditors can review without follow-ups.
Role-Based Access Controls (RBAC)
RBAC ensures that employees only see what’s relevant to their role. It supports ISO 27001 security controls under sections A.9.1 and A.9.2, which require clear segregation of duties and least-privilege access principles.
Continuous Monitoring
Automated alerts notify administrators of unusual activity such as mass credential sharing or failed access attempts. This not only strengthens operational security but also provides ongoing proof of risk monitoring, a SOC 2 requirement under the “Security” trust criterion.
API-Based Integrations
Modern white label solutions integrate with SIEMs, IAMs, and SSO providers. This allows compliance data to flow automatically into existing governance systems, creating a holistic view of access control across the enterprise.
The Business Case for Compliance-Centric Password Management
Compliance isn’t just a checkbox; it’s a competitive differentiator.
A 2024 survey found that companies achieving SOC 2 or ISO 27001 certifications closed 33% more enterprise deals on average than uncertified peers.
Another report shows that organizations with centralized password management cut audit preparation time by up to 60%.
For service providers, this translates to faster client onboarding, reduced audit stress, and increased brand credibility.
By deploying a white label password manager, vendors can:
- Offer compliant password storage as part of their own product line
- Strengthen customer trust with transparent access control
- Expand recurring revenue through managed security services
How Compliance Teams Use White Label Password Managers
In both frameworks, the tool becomes a single source of truth for identity-related compliance, bridging the gap between IT, risk, and audit teams.
For SOC 2 Compliance Automation
- Automatically document and export credential access logs
- Apply organization-wide MFA policies
- Maintain verifiable encryption records
- Support auditor reviews with real-time dashboards
For ISO 27001 Audit Readiness
- Implement ISO 27001 password policy templates
- Automate access reviews and certification cycles
- Align with A.9 and A.12 control categories
- Generate on-demand evidence reports
Real-World Application: When Audits Go From Reactive to Routine
A managed IT service provider with multiple client networks previously needed 12–15 days to prepare SOC 2 access evidence. After implementing a white label password manager, the same process now takes under two hours.
Why? Because all credential data, including access history, policy adherence, and cryptographic proof, is instantly accessible through a unified interface.
This shift isn’t just about saving time, it is about building repeatable audit confidence.
Why PureVPN White Label Password Manager Fits This Framework
For service providers aiming to expand their security offerings or strengthen compliance readiness, PureVPN White Label Password Manager delivers a complete foundation for continuous audit alignment. It enables centralized credential control, AES-256 encryption with zero-knowledge security, and automated policy enforcement that directly supports SOC 2 and ISO 27001 requirements.
Its scalable, multi-tenant design suits MSPs, SaaS vendors, and IT resellers, allowing full branding flexibility and seamless API integration. The result is a compliance-ready password management solution that reinforces brand credibility, improves client confidence, and removes the operational burden of building or maintaining an in-house system.
Take Control of Your Password Security
Using strong, unique passwords for every account is essential. A password manager makes it effortless to generate, store, and autofill complex passwords—keeping you safe from breaches.
Bringing It All Together
Audits don’t reward effort; they reward evidence. And the fastest path to reliable evidence is automation.
A white label password manager transforms password oversight from a chaotic, manual process into a streamlined, continuous control system. It aligns password practices with SOC 2 and ISO 27001 expectations, accelerates audit preparation, and proves to clients that your organization treats data protection as a measurable discipline, not an afterthought.
With solutions like PureVPN White Label Password Manager, compliance becomes less about surviving audits and more about demonstrating operational maturity every single day.


