Imagine this: a mid-sized tech company discovers that an employee’s reused password has been leaked on the dark web. Within hours, attackers gain access to sensitive client files. The fallout? Weeks of remediation, lost trust, and a potential seven-figure financial impact. Sadly, this scenario is no longer rare. In 2025, enterprises face over 81% of breaches caused by weak or stolen credentials.
Password management is no longer a purely technical concern—it’s a strategic necessity. The challenge lies not just in enforcing rules but in designing a system that works for employees, IT teams, and leadership simultaneously.
Why Centralized Password Management Matters
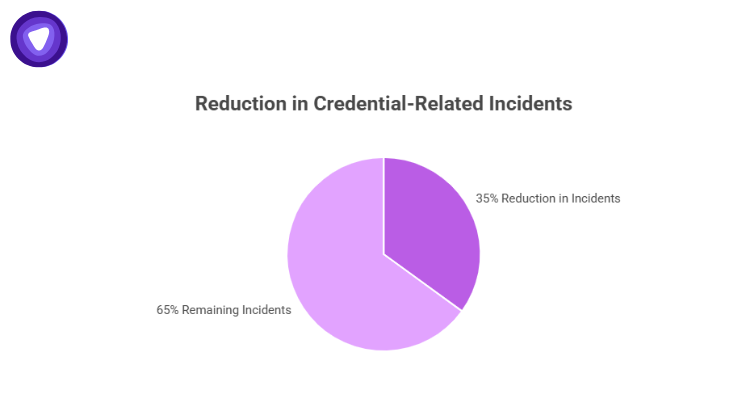
Many organizations still let employees juggle passwords through spreadsheets, sticky notes, or browser memory. It works—until it doesn’t. Centralized password management ensures that credentials are stored securely, policies are enforced consistently, and monitoring is continuous.
A mid-sized enterprise that adopted centralized management saw a 35% drop in credential-related incidents within the first year.
Tip for IT leaders: Don’t treat this as just a “password tool.” Integrate it with your SSO and directory services to automate access controls and enforce policies across every application your team uses.
Building Strong Password Policies That Stick
Long, unique passwords are your first line of defense, but telling employees to “just make it complex” doesn’t work. Human behavior matters. NIST guidelines now emphasize length over forced complexity and discourage arbitrary expiration unless a breach occurs.
Consider this: 60% of employees reuse passwords across accounts, even when warned. Enforcement alone won’t fix it—you need tools that generate, store, and autofill strong passwords.
Integrate your password manager with internal apps via API. This ensures weak passwords are rejected automatically, reducing friction for developers and end users alike.
Multi-Factor Authentication: Not Optional, Essential
Password policies can be perfect, but one compromised password can still lead to a breach. Enter multi-factor authentication (MFA). By requiring additional verification—hardware tokens, mobile push notifications, or biometrics—MFA adds a critical security layer.
Some enterprises initially hesitate due to perceived inconvenience. The reality? MFA can reduce account takeover attacks by 99.9%.
Implementation insight: Start MFA rollout with high-risk users, then expand. Educate teams on avoiding workarounds—like sharing tokens—and track adoption metrics.
1. What is the main benefit of centralized password management?
2. Roughly how much does MFA reduce account takeover risk?
3. Key advantage of passwordless authentication?
4. Why is employee training important for password security?
The Rise of Passwordless Authentication
Passwordless authentication isn’t just a buzzword. The market is expected to exceed $20 billion in 2025.
Instead of relying on a string of characters, users authenticate via hardware keys, biometrics, or mobile devices. Benefits include:
- Lower phishing and credential-stuffing risk
- Streamlined user experience
- Reduced IT support calls for password resets
CTO insight: Implement FIDO2/WebAuthn standards where possible, and always include a fallback method for legacy applications.
Employee Training: Making Security Part of Culture
Even the best technical measures fail without human awareness. Training isn’t a checkbox; it’s ongoing engagement. Simulations of phishing attacks, shadow IT awareness campaigns, and quarterly workshops keep employees alert.
Tip: Make training memorable. Gamify it. Reward teams for reporting suspicious emails. Employees become active defenders, not just users.
Integration With Existing IT Infrastructure
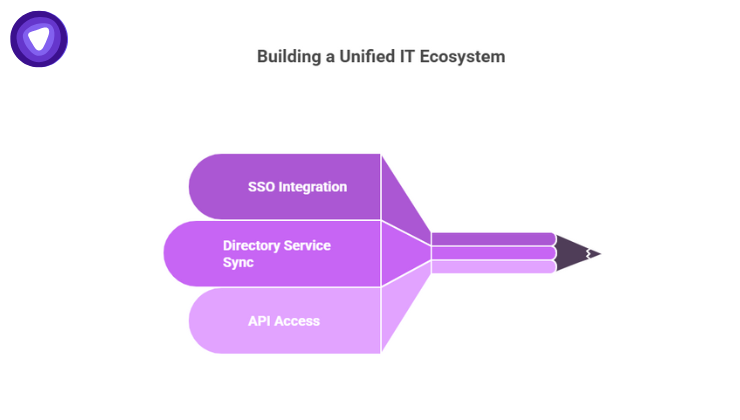
A password manager that doesn’t play well with your existing IT stack is worse than none at all. Integration ensures security measures don’t slow down productivity.
Considerations:
- SSO integration to streamline login across applications
- Directory service sync for automated account provisioning/deprovisioning
- Robust API access for custom workflows and automation
Build vs. Buy: Password Management Solutions
Enterprises often debate: build in-house or adopt a SaaS solution? Here’s a concise comparison:
| Feature | Build In-House | Buy SaaS Solution |
| Implementation Time | Months | Days |
| Maintenance | High, requires IT resources | Included in subscription |
| Security Updates | Manual | Automated |
| Scalability | Limited by internal team | Easily scales |
| Cost | High upfront, unpredictable | Predictable subscription |
| Integration | Custom APIs required | Prebuilt SSO & LDAP |
Monitoring and Auditing: Proactive Defense
Monitoring isn’t just about compliance—it’s about spotting weak links before they break. Automated alerts on failed login attempts, unusual access times, or password reuse can prevent a breach from escalating.
Enterprises with automated monitoring detect 45% more security incidents early.
Calculating ROI: Why Password Management Pays
Some executives see password management as a cost center. In reality, it’s a risk-reduction investment. Consider:
- Average breach cost: $10M+
- Reduced IT support tickets
- Increased operational efficiency
- Avoidance of regulatory fines
A small investment in a robust password management solution often pays for itself in breach prevention alone.
Future Outlook: Staying Ahead of Threats
The cybersecurity landscape evolves rapidly:
- AI-powered attacks detect weak credentials faster than ever
- Blockchain-based authentication offers tamper-proof identity verification
- Quantum-resistant encryption is the next frontier for enterprise security
Forward-looking enterprises pilot these technologies early, ensuring they’re prepared for the threats of tomorrow.
PureVPN White Label Password Manager: Enterprise-Ready Security
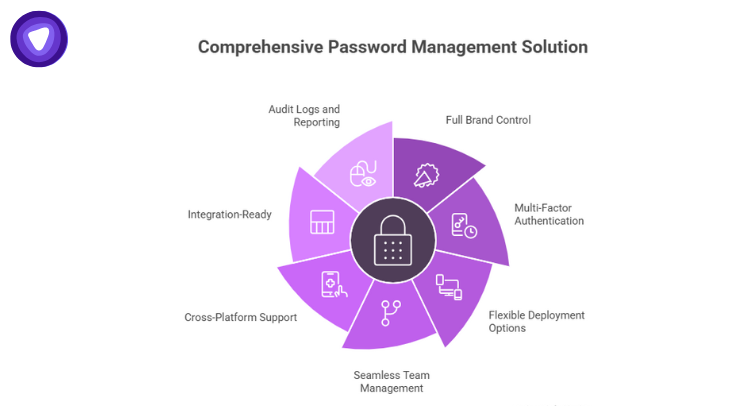
PureVPN White Label Password Manager delivers end-to-end enterprise security with:
- Encryption for stored and transmitted passwords
- MFA support for critical accounts
- Seamless integration with SSO, Active Directory, and APIs
- User-friendly interface for effortless adoption
By adopting PureVPN White Label Password Manager, organizations streamline credential management, minimize risk, and scale securely—without burdening employees or IT teams.
Conclusion
In 2025, password management isn’t optional—it’s strategic. By combining centralized management, strong policies, MFA, passwordless options, employee training, monitoring, and future-ready technologies, enterprises protect sensitive assets while improving operational efficiency. Thoughtful implementation, paired with solutions like PureVPN White Label Password Manager, ensures that security becomes a business enabler, not a bottleneck.


