IoT devices have moved far beyond experiments and early pilots. They now control home appliances, monitor patient vitals in hospitals, manage industrial equipment, and optimize logistics routes worldwide. This growth has created an environment where every new connection is both an opportunity and a risk.
The problem is clear: most IoT devices were not designed with strong native security. Default passwords, outdated firmware, and limited computing power leave them vulnerable to interception and unauthorized access. Attackers know this, which is why IoT deployments remain one of the most frequently exploited entry points into larger networks.
A VPN for IoT addresses this problem directly. By creating encrypted tunnels between devices and servers, it shields communications from exposure. For businesses, service providers, and telcos, IoT VPNs are becoming a default layer of protection. They ensure data integrity, support compliance requirements, and build trust with clients who depend on reliable services.
- IoT VPN: Encrypts device communications, protecting them from interception or tampering.
- Why it matters: IoT devices are insecure on their own, making VPNs vital for enterprise deployments.
- Operational benefits: Compliance, secure firmware updates, and centralized fleet management.
- Free VPN risks: Lack reliability, performance, and compliance guarantees—unsuitable for IoT projects.
- Business model: MSPs, ISPs, and telcos can bundle VPN with IoT services to boost ARPU and reduce churn.
- PureVPN – White Label: Enables providers to launch branded IoT VPN services quickly without new infrastructure.
What Is VPN in IoT?
A VPN in IoT secures the flow of data between smart devices and the systems they connect to, typically cloud platforms or enterprise servers. Instead of transmitting data over open channels, the VPN encrypts it end-to-end, ensuring that even if traffic is intercepted, it remains unreadable.
Unlike personal VPNs, which focus on single-user privacy, IoT VPNs are built for scale. They support thousands of devices across geographies, automate certificate management, and provide central control. They also extend protection to edge gateways that manage groups of constrained devices.
Why IoT Devices Are High-Risk Without VPN?
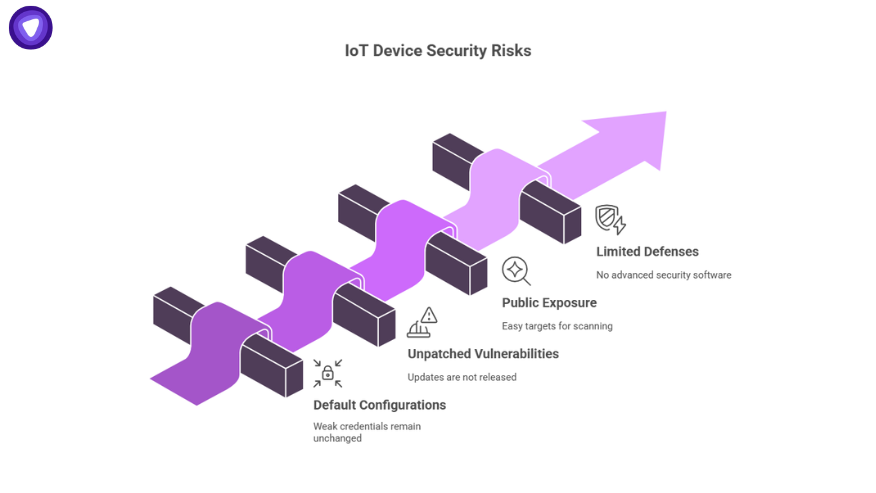
IoT devices expand attack surfaces dramatically. Without VPN, risks multiply across several fronts:
- Default configurations: Many devices ship with weak credentials that remain unchanged.
- Unpatched vulnerabilities: Manufacturers often stop releasing updates, leaving flaws unaddressed.
- Public exposure: Devices connected directly to the internet are easy targets for scanning tools.
- Limited defenses: Constrained CPUs and batteries prevent devices from running advanced security software.
By routing traffic through VPN tunnels, these devices avoid direct exposure, and organizations gain greater confidence that data cannot be intercepted en route.
Should I Put My IoT Devices on VPN?
The short answer is yes. Any IoT device that transmits sensitive information or connects via a shared or public network should operate under a VPN.
A VPN for remote access adds another layer of value. Administrators and technicians can manage fleets securely, run diagnostics, and push updates without opening devices to the public internet. Remote access through VPN becomes critical in industries where downtime is costly and on-site visits are impractical.
IoT Categories and Where VPN Fits
Here are the categories and the role VPN plays in each:
- Consumer IoT – Smart appliances, wearables, and connected home devices. VPN ensures privacy and secure access for users managing devices remotely.
- Industrial IoT – Factory sensors, robotics, and heavy machinery. VPN protects operational data and maintains uptime against network attacks.
- Infrastructure IoT – Smart grids, transportation, and utilities. VPN provides encrypted telemetry and supports compliance in critical systems.
- Commercial IoT – Healthcare, retail, and hospitality. VPN safeguards sensitive customer and patient information, meeting regulatory standards.
Is Your IoT Fleet at Risk?
Common VPN for IoT Architectures
Different industries use varying architectures depending on scale and constraints:
- Device-to-cloud tunnels: Each device builds a direct encrypted link to the cloud.
- Gateway-based VPNs: Constrained devices connect to a gateway, which manages encryption for the group.
- VPN for server access: APIs, dashboards, and data stores only accept connections authenticated through a VPN.
- VPN SaaS models: Enterprises outsource infrastructure management but retain branding and control of their IoT VPN service.
Beyond Security: Operational Benefits of VPN for IoT
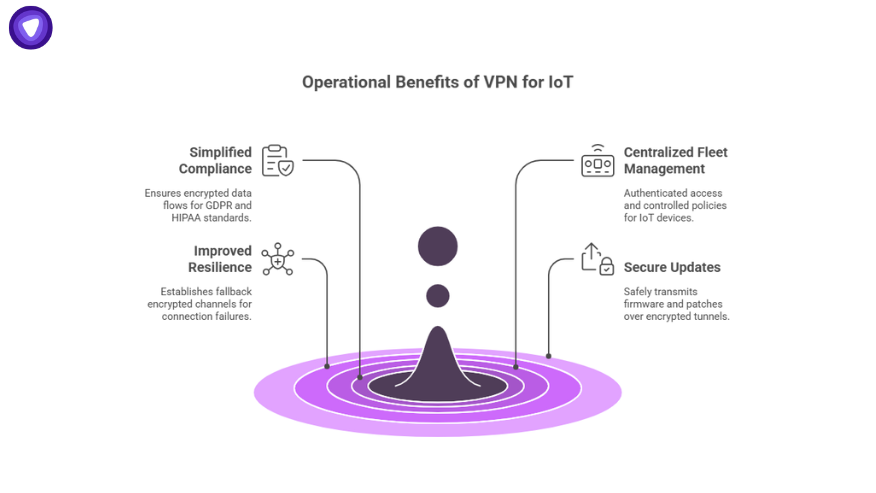
VPNs also bring operational advantages beyond threat reduction:
- Simplified compliance with GDPR, HIPAA, and other standards by ensuring encrypted data flows.
- Centralized fleet management through authenticated access and controlled policies.
- Improved resilience by establishing fallback encrypted channels when primary connections fail.
- Secure updates where firmware and patches are transmitted safely over encrypted tunnels.
Why Free VPN for IoT Is Not a Viable Option?

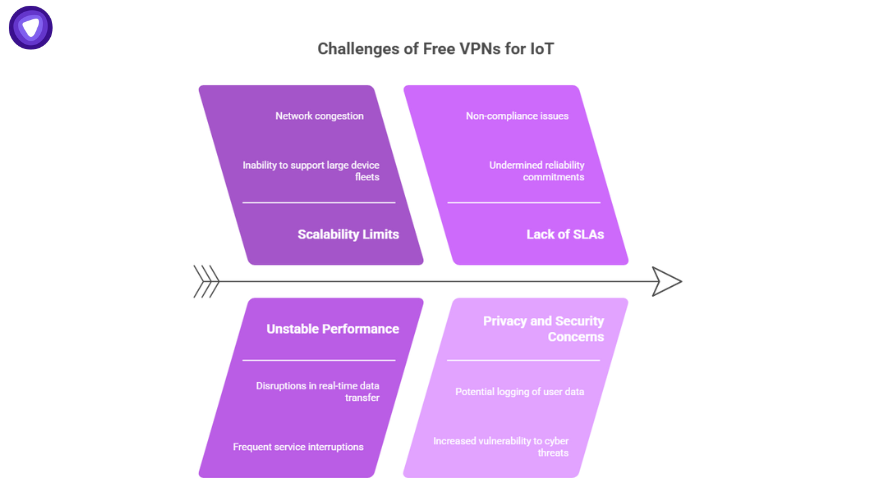
While some organizations test free VPN for IoT services, they quickly encounter challenges:
- Scalability limits make it difficult to support large device fleets.
- Unstable performance disrupts real-time data transfer.
- Lack of SLAs undermines reliability and compliance commitments.
- Potential logging raises privacy and security concerns.
Enterprises require predictability and accountability, which free VPNs cannot provide.
How Enterprises Use VPN for IoT Today?

- Logistics companies secure fleet telemetry by routing data through VPN tunnels, preventing interception and route manipulation.
- Healthcare providers rely on VPN for remote access to medical devices, ensuring only authorized staff can connect.
- Industrial operators encrypt factory sensor data and ensure audit trails meet compliance obligations.
Conversations on forums such as VPN for IoT Reddit highlight both successes and frustrations. Common themes include challenges with large-scale deployments and the importance of vendor support in managing certificates, performance, and resilience.
Technical Considerations for VPN in IoT
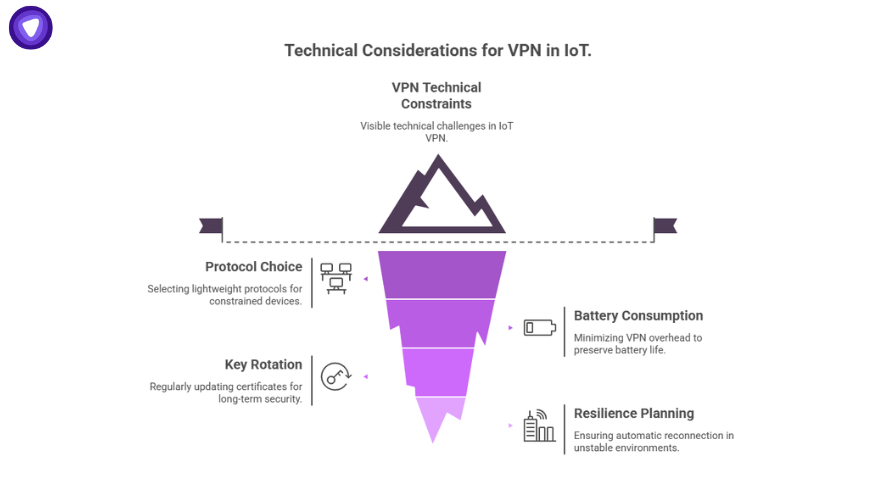
IoT deployments have unique technical constraints that must be addressed:
- Protocol choice: Lightweight options like WireGuard or IKEv2 perform better on constrained devices than heavier IPSec.
- Battery consumption: VPN overhead must be minimized to avoid draining small devices.
- Key rotation: Regular certificate updates are required for long-term security.
- Resilience planning: Devices should reconnect automatically when VPN sessions drop, especially in rural or high-latency environments.
Business Case: ARPU and Customer Retention
From a business perspective, VPN for IoT is not just a cost. It is a revenue opportunity.
By bundling VPN services into IoT connectivity, MSPs and telcos create Contribution Margin Per User (CMPU) gains. ARPU grows without significant additional costs, since VPNs are delivered through existing infrastructure.
For service providers, this bundling improves client retention, strengthens trust, and differentiates offerings in a competitive telecom landscape.
Conclusion
IoT is no longer an emerging technology. It is a foundational part of how businesses operate and deliver value. But with this growth comes significant risk. A VPN for IoT is now a baseline requirement for securing device communications, ensuring compliance, and enabling safe remote management.
For service providers, IoT VPNs represent more than security. They are a business opportunity. By offering PureVPN White Label, MSPs, ISPs, and telcos can launch branded VPN services without infrastructure investment. This strengthens client relationships, improves ARPU, and positions providers as leaders in IoT security.


