Grafana has long been the go-to for engineers, security analysts, and executives who need to visualize data at scale. It’s open-source, flexible, and powerful. But every open door is also a potential entry point for attackers. Enter CVE-2025-4123.
This high-severity flaw exposed thousands of self-hosted Grafana dashboards to account takeovers, session hijacking, and even server-side request forgery (SSRF). For businesses running Grafana behind the firewall, the discovery felt like finding out that the trusted tool in the heart of their infrastructure had a ghost inside it, quiet, hidden, and capable of wreaking havoc if ignored.
In this guide, we’ll break down what CVE-2025-4123 is, how it works, why it matters for compliance and governance, and most importantly, what businesses can do to protect themselves.
- What it is: CVE-2025-4123 is a high-severity XSS flaw in Grafana that allows attackers to load malicious plugins, hijack accounts, and in some cases trigger SSRF.
- Severity: Grafana scored it 7.6 (High); NVD listed 6.1 (Medium), but real-world impact is significant.
- Exploit path: Abuses Grafana’s
staticHandler → redirect → malicious JSchain, leading to session takeover. - Proof of Concept: A working cve-2025-4123 poc has been shared, confirming exploitability.
- Who’s at risk: Self-hosted Grafana users on unpatched versions, especially with anonymous access or unsigned plugins. Grafana Cloud not impacted.
- Fixes: Upgrade to patched “security-01” releases; enforce plugin signing; disable anonymous access; apply strict CSP rules.
- Detection: Watch for unusual
/public/...requests, suspicious plugin loads, and unauthorized account changes. - Compliance impact: Breaches could trigger GDPR, HIPAA, or SOX penalties. Documentation and audits are critical.
- Business lesson: IT compliance isn’t paperwork—it’s protection. Non-compliance costs far more than patching.
What Is CVE-2025-4123?
CVE-2025-4123 is a cross-site scripting (XSS) vulnerability in Grafana’s frontend plugin handler that lets attackers trick users into loading malicious JavaScript. Exploitation can lead to account takeover, unauthorized access, and—in environments with the Image Renderer plugin—SSRF attacks.
The Grafana security team assigned it a CVSS v3.1 score of 7.6 (High). The U.S. National Vulnerability Database scored it slightly lower at 6.1 (Medium). That split has caused some confusion, but make no mistake: if your Grafana instance is exposed, this is not a “medium” issue.
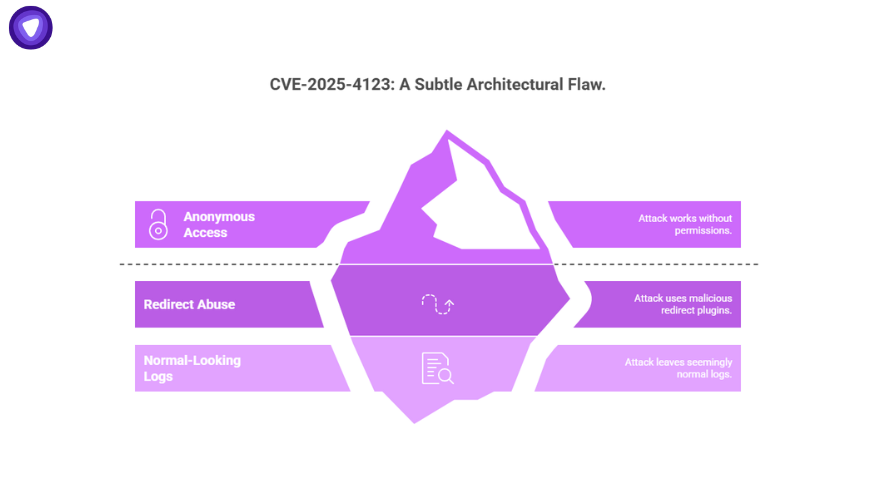
Why It’s Different?
- Works even without editor permissions if anonymous access is enabled.
- Exploit chain involves redirect abuse and malicious plugins—harder for traditional defenses to spot.
- Leaves logs that look almost normal, making detection challenging.
Think of CVE-2025-4123 not as a single crack in the wall, but as a subtle architectural flaw that attackers can push on until the whole door swings open.
How the Exploit Works?
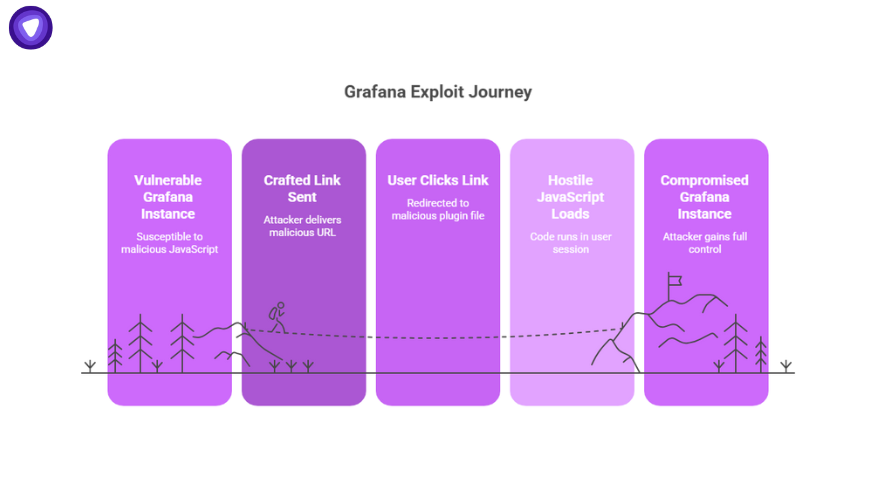
The vulnerability lives in how Grafana’s staticHandler deals with plugin resources. Attackers can manipulate the path traversal sequence in requests to redirect users into loading external JavaScript code. Once loaded, that code runs in the user’s session context.
- Attacker sends a crafted link.
- User clicks, Grafana redirects to a malicious plugin file.
- Browser loads hostile JavaScript.
- Attacker gains control—session tokens, account actions, plugin abuse.
If the Image Renderer plugin is installed, the attacker can pivot to a full SSRF scenario. That means making Grafana send requests on their behalf—potentially exposing metadata endpoints, internal APIs, and sensitive services.
Proof-of-concept exploits were quickly discussed in security circles. A working CVE-2025-4123 PoC confirmed that exploitation is not just theoretical but practical. Once a PoC is out, attackers don’t need to invent their own methods—they can adapt and scale.
Real-World Risks
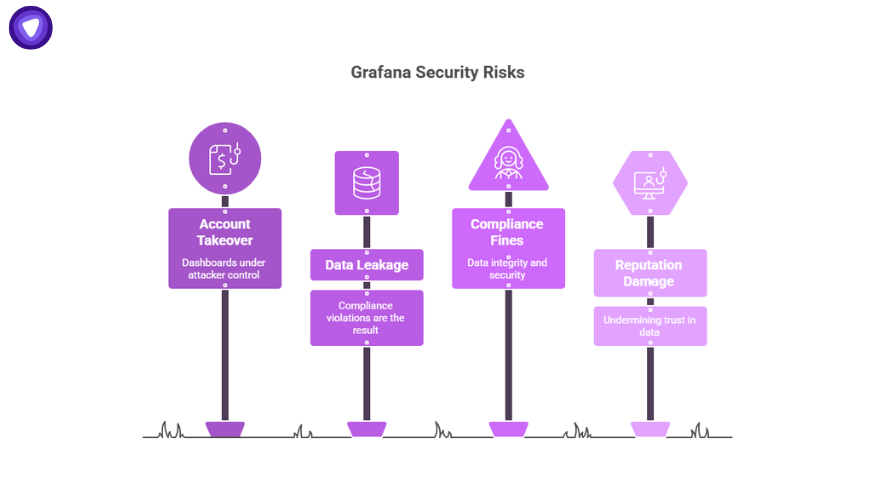
The risk isn’t abstract. Let’s map it to actual business outcomes.
- Account takeover: Admin accounts compromised via XSS can mean dashboards, alerts, and data sources are all under attacker control.
- Data leakage: Grafana often pulls from databases containing customer data, financial KPIs, or operational metrics. Losing that data equals compliance violations.
- Compliance fines: GDPR, HIPAA, and SOX all require data integrity and security. An exploited Grafana dashboard could count as a reportable breach.
- Reputation damage: A compromised dashboard can alter what executives or clients see, undermining trust in the numbers themselves.
Imagine a financial institution relying on Grafana dashboards for trading oversight. If an attacker injects false data or disrupts alerts, the downstream consequences are enormous.
Who Is Affected?
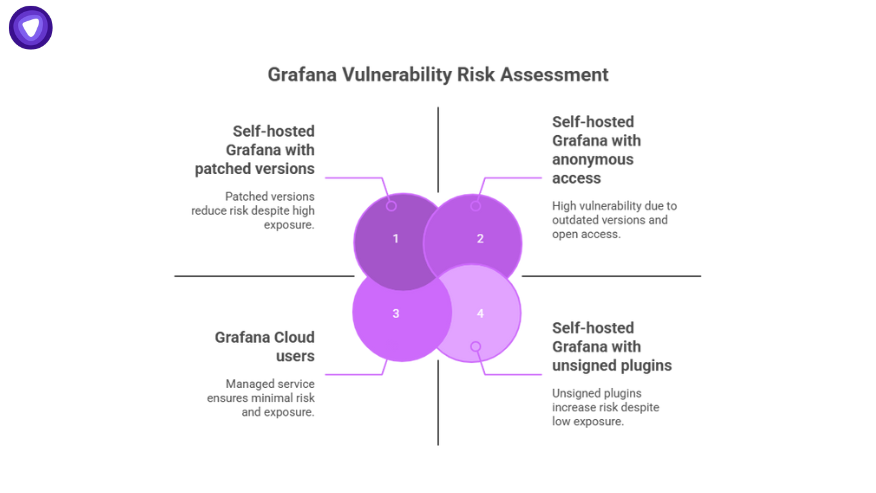
Not everyone is equally exposed.
- Self-hosted Grafana users: Most at risk. All versions before patched “security-01” builds are vulnerable.
- Grafana Cloud users: The vendor confirmed the managed service was not affected.
- High-risk setups: Instances with anonymous access enabled, relaxed Content Security Policy (CSP) headers, or unsigned plugins.
If your Grafana runs inside corporate infrastructure with strict plugin controls, your risk is lower, but not zero. If you expose Grafana to the internet without patches, you’re a target.
Fixes and Mitigations
The number one recommendation is simple: upgrade now. Grafana released patches across all supported branches, including:
- 10.4.18+security-01
- 11.2.9+security-01
- 11.3.6+security-01
- 11.4.4+security-01
- 11.5.4+security-01
- 11.6.1+security-01
- 12.0.0+security-01
Short-Term Hardening
If you can’t patch immediately:
- Enforce plugin signing: Only allow signed plugins. Remove any unsigned plugin exceptions.
- Disable anonymous access: Don’t leave Grafana dashboards open to anyone with a link.
- Apply strict CSP headers: Especially connect-src. Don’t let Grafana load scripts from unknown sources.
- Review the Image Renderer plugin: Decide if you really need it. If yes, monitor and restrict what endpoints it can reach.
Compliance Checklist (for teams under audit)
- Patch to a fixed version.
- Document the patch in your IT compliance audit log.
- Update your IT compliance policy to include Grafana patch cycles.
- Train admins on spotting suspicious plugin activity.
These steps aren’t just technical—they’re compliance evidence. Auditors don’t just ask if you’re secure; they ask if you can prove it.
Detection and Response
If you’re wondering whether you’ve already been haunted by this “ghost,” here’s what to check:
- Access logs: Look for /public/… paths with encoded characters like %3F or backslashes.
- Grafana logs: Unusual username/email changes right after suspicious requests.
- Plugin traffic: Requests to /a/<plugin>/explore that fetch JavaScript from external domains.
Response Steps
- Kill all active sessions.
- Reset admin credentials.
- Review plugin inventory; remove anything unsigned.
- Check for SSRF attempts if Image Renderer was enabled.
This isn’t just a patch-and-forget issue. Continuous monitoring is required, especially since exploit PoCs are circulating.
Lessons for Compliance and Governance
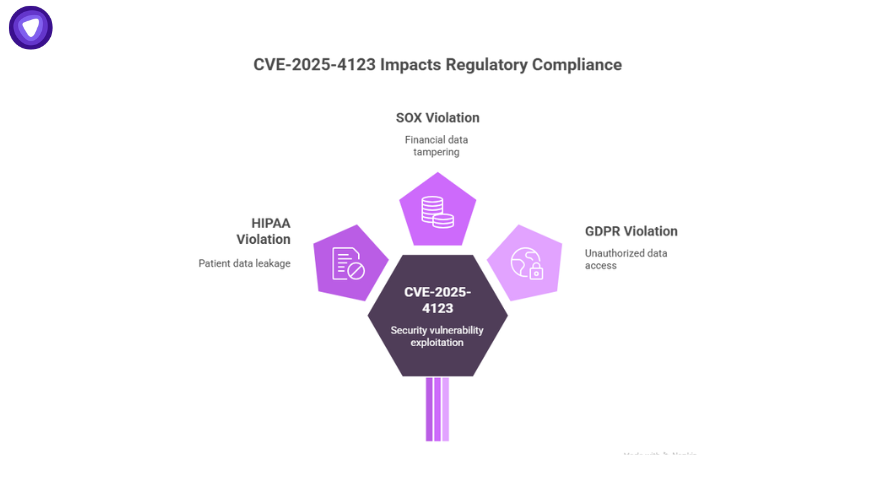
CVE-2025-4123 isn’t just a security problem—it’s a compliance problem.
- HIPAA: Patient dashboards that leak data must be reported.
- SOX: Financial dashboards with tampered integrity put you at risk of violations.
- GDPR: Any exfiltration or unauthorized access to EU personal data requires breach notifications within 72 hours.
For organizations, this vulnerability is proof that compliance frameworks aren’t paperwork. They demand controls, monitoring, and proof that you can respond quickly. Non-compliance fines are often larger than the cost of fixing the issue.
The Role of Vendors and Partners
Very few businesses manage IT compliance entirely in-house. Many rely on managed service providers, VARs, or consultants to oversee patch management, monitoring, and audits.
For those partners, CVE-2025-4123 is a moment to demonstrate value:
- Run patch management programs.
- Offer compliance checklists tied to vulnerabilities.
- Package VPNs, monitoring, and compliance tools together as revenue streams.
Turning Security Incidents Into Compliance Wins With PureVPN White Label
Most major frameworks, from HIPAA to ISO 27001, require encryption of data in transit. Grafana dashboards often involve sensitive connections: to databases, APIs, and cloud platforms. If those connections aren’t encrypted, you fail compliance even if the app itself is patched.
This is where PureVPN White Label adds real value. Partners, MSPs, and resellers can:
- Offer encrypted VPN solutions to protect data moving between users and dashboards.
- Help clients satisfy compliance frameworks that demand secure communication.
- Build recurring revenue by packaging VPN access with compliance services.
For resellers, CVE-2025-4123 is a case study in why VPNs and compliance go hand in hand. Encryption reduces attack surfaces, satisfies auditors, and reassures clients.
Conclusion – Don’t Let the Ghost Linger
CVE-2025-4123 is more than just another bug report. It’s a reminder that self-hosted dashboards, no matter how trusted, can hide vulnerabilities with serious consequences.
The fix is straightforward: patch, harden, monitor, and document. The risk of ignoring it? Account takeovers, compliance fines, and reputational loss that no business can afford.
For enterprises, IT leaders, and resellers alike, this vulnerability is proof that compliance is strategy, not paperwork. And with partners like PureVPN White Label, it’s possible to protect data in transit, meet compliance obligations, and add new revenue streams.
Don’t wait for the ghost to show itself in your logs. Patch now, monitor continuously, and make compliance part of your business growth plan.


