If your business handles sensitive information, data security management is not optional. In 2025, the stakes are higher than ever. Breach costs keep rising, AI-powered attacks test every weak link, and regulators won’t care if you say “we didn’t know.” Yet, a lot of what’s written about data security management stops at theory, not practical next steps.
In this guide, you’ll get a clear sense of what it means to manage data security well, the real benefits of data security, and what practical measures you can put in place starting this quarter. You’ll see sector examples, real risk figures, and a checklist you can grab as your own data security management PDF.
Let’s break this down in a way that helps you act, not just nod along.
What is Data Security Management?
At its simplest, data security management means protecting the confidentiality, integrity, and availability of your business’s data throughout its lifecycle. From how you store customer records to how you handle backups, every piece of data should have controls that limit who can see it, change it, or destroy it.
Secure data management overlaps but goes broader, covering governance, policies, and workflows for all data operations. Data security management focuses specifically on threats and protective measures. When people search “what is secure data management” or “what is data security management,” they’re really asking: how do I keep my information safe from unauthorized access, leaks, or damage?
Why Data Security Management Matters in 2025
Data breaches aren’t slowing down. Last year alone, global breach costs averaged over $4.45 million per incident. Small leaks turn into fines. Unpatched systems turn into ransomware. Supply chain partners can open you up to risks you didn’t see coming.
Strong data security management means:
- Fewer incidents and downtime.
- Lower operational risk.
- Better compliance with laws like GDPR, CCPA, and HIPAA.
- Stronger customer trust.
Put simply, the benefits of data security are not just about compliance — they’re about staying competitive. One breach can cost you more than years of proactive security spend.
Types of Data Security Controls
There are many ways to break this down, but here are five core types of data security controls every team should have on their radar. These match what people often ask: “What are the 5 types of data security control?”
Compliance Controls Checklist
| Check | Control | Example | Status |
|---|---|---|---|
| Encryption | AES-256 at rest & in transit | ||
| Access Control | Role-based, MFA | ||
| Backups | Offsite Encrypted Copies | ||
| Monitoring & Auditing | SIEM, DLP Tools | ||
| Physical Security | Secured Server Rooms |
The Four Core Elements of Data Security
When evaluating your data security management plan, make sure it aligns with the following principles:
| Element | Purpose |
| Confidentiality | Ensures that sensitive data is only accessible to authorized users. |
| Integrity | Prevents unauthorized changes or tampering with data. |
| Availability | Guarantees data is accessible when it’s needed. |
| Accountability | Tracks actions to maintain traceability and responsibility. |
If even one of these fails, your data—and your business—is at risk.
The Data Security Management 7D Model
One reason some teams struggle is they don’t have a step-by-step structure. A simple way to remember the key actions is the Data Security Management 7D framework. Here’s how it breaks down:
Discover
Map where your sensitive data lives — files, databases, cloud apps.
Define
Classify data by sensitivity and compliance requirements.
Document
Create clear policies for handling, storing, and deleting data.
Deploy
Implement controls: encryption, backups, and user access.
Detect
Set up monitoring for suspicious activity, breaches, or policy violations.
Defend
Build incident response plans, patch known gaps, test your backups.
Deliver
Audit regularly and report on data security status to stakeholders.
This isn’t theory. This is the cycle that real businesses run quarterly or even monthly.
Real-World Examples: Sector Spotlights
Healthcare & HIPAA
HIPAA shows us insider threats are as big as external hacks.
Retail & PCI DSS
POS endpoints can be the weakest link in retail security.
Remote Teams
Modern remote setups must lock down data in transit.
Short Use Case Modules
Securing Remote Access for Law Firms
- VPN access prevents exposure during off-site legal research.
- Client confidentiality preserved in every digital interaction.
- Adds jurisdictional privacy by masking IP locations.
GDPR Compliance Support for EU SaaS Businesses
- VPN tunnel ensures encrypted data flows.
- Simplifies user data consent processes.
- Reduces exposure to cross-border data transfer violations.
Protecting Client Data for Marketing Agencies
- VPN prevents tracking of client account credentials.
- Keeps analytics and ad platform logins safe from IP fingerprinting.
- Clients trust agencies with more sensitive project data.
Common Security Measures to Implement
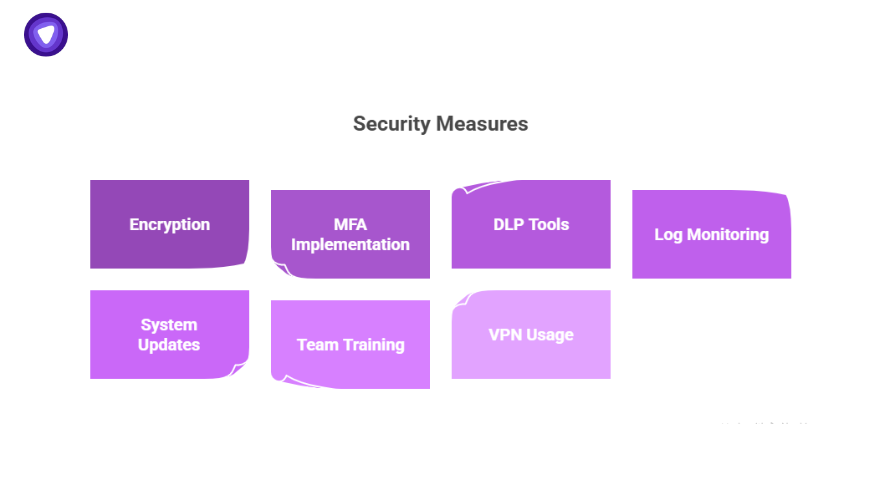
Here’s a shortlist every founder, CTO, or IT lead should have live by end of quarter:
- Encrypt everything — files at rest, backups, and emails if possible.
- Run MFA — stop 90% of brute force attacks.
- Use DLP tools — prevent sensitive info from leaking via email or file shares.
- Check logs weekly — detect unauthorized changes early.
- Update systems — patch known exploits ASAP.
- Train your team — human error remains the biggest risk.
- Use trusted VPNs — for remote and site-to-site traffic.
DIY vs Managed vs White Label
Here’s how your approach to data security management can stack up.
| Aspect | DIY Setup | Managed Service | PureVPN White Label |
| Encryption | Self-configured, risky | Standard, partial | Full-stack, tested |
| Exit IP Rotation | Manual | Varies | Automatic, region-aware |
| Remote Team Support | Mixed device security | Limited | Unified secure tunnels |
| Cert/Key Management | Manual rotation | Limited automation | Automatic, audit-ready |
| Compliance Backstop | Your responsibility only | Shared | Compliance-ready logs & support |
Risk, Cost, and Hidden Breach Impact
Hidden Breach Cost Calculator
Most breaches don’t show up as headline news. They show up as:
- Chargebacks when clients lose trust.
- Refunds when service gets blocked.
- Fines when data leaks violate GDPR or CCPA.
- Lawsuits when clients claim “gross negligence.”
Your real cost isn’t just fixing a breach. It’s the business you lose while recovering. Strong data security management prevents that nightmare.
How to Choose a Good Data Security Solution?
Before you jump in with any vendor, ask:
- Do they rotate exit IPs and certs automatically?
- How fast do they patch known vulnerabilities?
- Is there a clear compliance workflow?
- Can they scale with you?
- Do they back up what they promise with real audits?
PureVPN’s White Label backbone was built for MSPs and brands who don’t want to gamble on DIY. You get tested infrastructure, stealth fallback, and a no-logs architecture your customers can trust.
Stay Connected & Learn With Us
Join our growing community and connect with peers who build secure networks and resell privacy tools worldwide.
Final Thoughts
Most teams don’t have time to build their own secure backbone from scratch. With PureVPN White Label, you get region-aware IP pools, stealth fallback modes, audit-ready logs, and a no-logs policy — without the daily patching headaches.
You focus on your clients. We keep your traffic private and stable.


