Whaling phishing is a highly targeted social engineering technique aimed at senior executives and board-level leaders. Attackers impersonate trusted figures such as CEOs or CFOs to extract sensitive data, divert payments, or gain privileged access. These attacks exploit the authority and decision-making power of executives, making them more damaging than general phishing attempts.
Unlike mass phishing campaigns, whaling phishing attacks are built on detailed reconnaissance. Attackers collect public information from press releases, LinkedIn profiles, and company websites to craft convincing pretexts. Executives are often busy, rely on assistants to triage communication, and have authority to bypass standard checks, which makes them ideal targets.
Businesses that fail to protect their executives from whaling phishing face severe risks. A single compromised executive account can result in large-scale financial loss, data exposure, and legal consequences. This article explains how whaling phishing works, how it differs from spear phishing, the methods used by attackers, and the safeguards that can block these attacks.
- Target: Whaling phishing focuses on executives with tailored social engineering schemes.
- Risk Level: More severe than spear phishing, often leading to high-value financial fraud.
- Attack Methods: Uses a mix of email (phishing), SMS (smishing), and calls (vishing) for deception.
- Prevention: Apply technical controls, strict payment policies, and VPN-based secure access.
- PureWL’s Role: PureVPN – White Label safeguards executive connections and reduces attack surfaces.
What is Whaling Phishing?
Whaling phishing is a form of targeted phishing attack that focuses on executives with access to sensitive data and financial authority. While general phishing casts a wide net, whaling phishing is narrow and precise. Attackers research their targets extensively and design emails or messages that mimic real business communications.
What is Whaling in Phishing
Whaling phishing is also known as CEO fraud or business email compromise (BEC). It uses social engineering to trick executives into approving wire transfers, releasing confidential data, or disclosing login credentials. Unlike general phishing, which often contains obvious red flags, whaling phishing messages are grammatically correct, contextually accurate, and based on insider-style knowledge.
Why Executives Are Targeted?
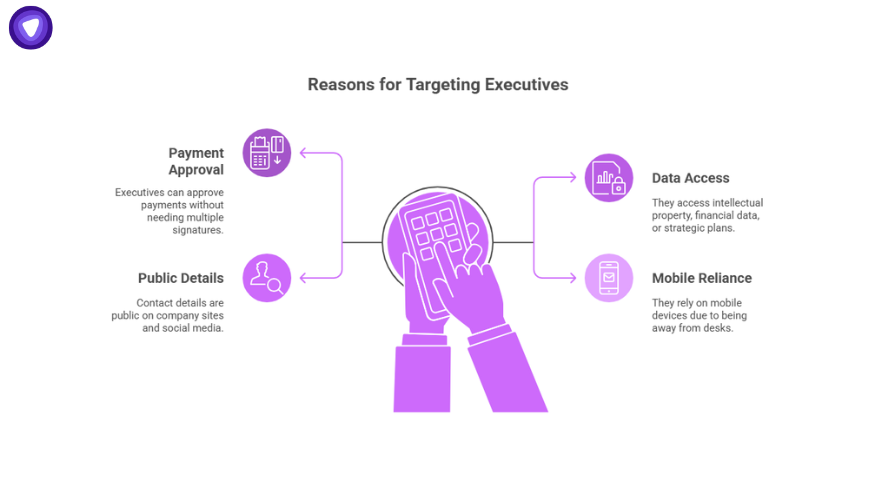
- They have clearance to approve payments without multiple sign-offs
- They store or access intellectual property, financial data, or strategic plans
- Their contact details are public through company sites, press interviews, and social platforms
- They are often away from their desks, which increases reliance on mobile devices and brief message reviews
Whaling phishing attacks exploit the trust and urgency inherent in executive communications.
Spear Phishing vs Whaling
Both spear phishing and whaling phishing are targeted, but they differ in scale, objectives, and risk level.
| Aspect | Spear Phishing | Whaling Phishing |
| Target | Specific employees | Senior executives (CEO, CFO, VP, board) |
| Content quality | Personalized but moderate detail | Highly tailored and contextually accurate |
| Authority level exploited | Departmental | Organization-wide |
| Typical goal | Credential theft, malware infection | Large fund transfers, IP theft, legal exposure |
| Risk impact | Localized compromise | Strategic business compromise |
What is the difference between whaling and spear phishing?
Whaling phishing focuses on executives and uses highly detailed impersonation, while spear phishing targets mid-level employees and often aims to steal credentials or install malware.
Anatomy of a Whaling Phishing Attack
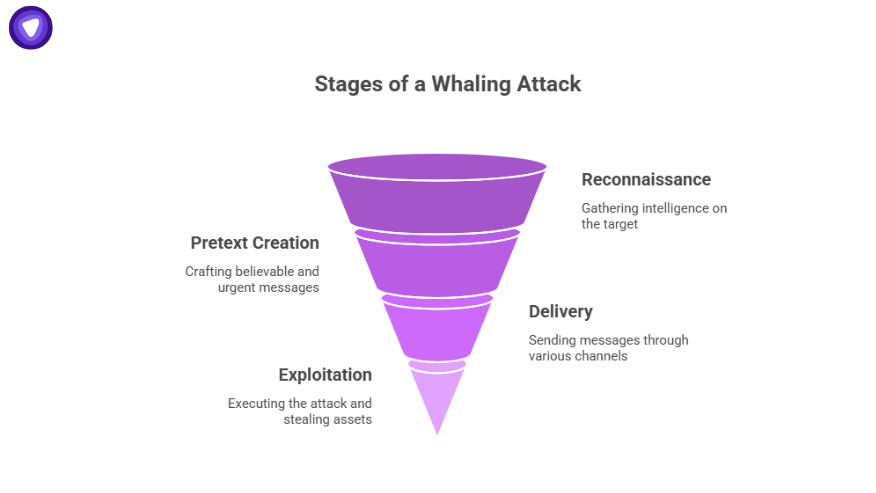
Whaling attacks use social engineering to trick employees and executives into bypassing standard controls. They are usually executed in four stages.
1. Reconnaissance
Attackers gather intelligence about the target executive from LinkedIn, corporate press releases, news articles, and social networks. They study writing styles, contact networks, and business timelines to craft believable messages.
2. Pretext Creation
They register lookalike domains or compromise supplier email accounts. The messages include urgent business language, such as confidential deals, legal threats, or investment deadlines. This urgency overrides normal caution.
3. Delivery
Attackers send the message via email, SMS (smishing phishing), or phone call (vishing phishing). Some campaigns use all three channels, shifting to phone or text if the executive ignores email.
4. Exploitation
Once the executive approves the action, attackers redirect funds, steal credentials, or exfiltrate intellectual property.
What is an example of a whaling attack?
Wire transfer to a new vendor account. Believing it is genuine, the CFO authorizes the transfer, and the funds are stolen.
Types of Phishing
Understanding how whaling fits into the broader phishing landscape is critical for accurate risk modeling.
What are the Four Types of Phishing
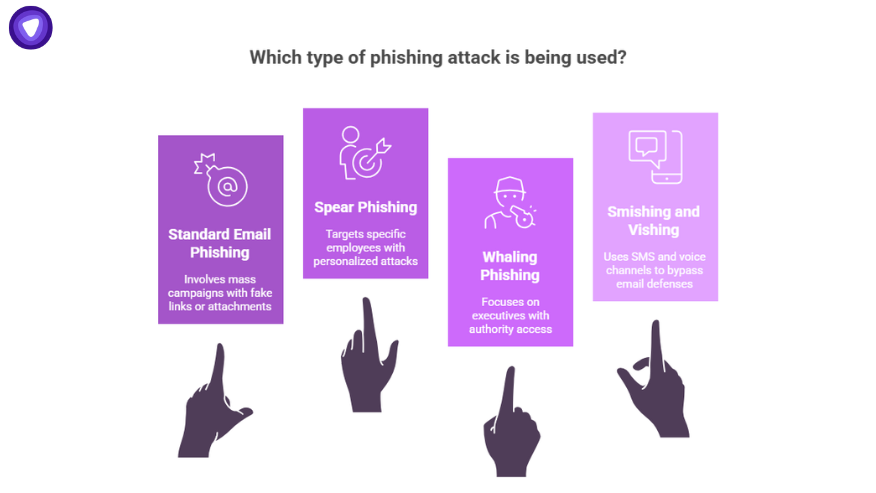
- Standard email phishing: Mass campaigns with fake links or attachments
- Spear phishing: Targeted attacks on specific employees
- Whaling phishing: Focused attacks on executives with authority access
- Smishing and vishing phishing: Attacks using SMS and voice channels to bypass email defenses
Whaling phishing is the most damaging type because it targets decision-makers who can bypass security controls.
Detecting Whaling Phishing Signals
Whaling phishing attacks are designed to appear authentic. Technical detection requires analyzing metadata, message behavior, and language.
Technical red flags
- SPF, DKIM, or DMARC failures
- Mismatched display name and sender domain
- Recently registered domains resembling internal domains
- Abnormal “reply-to” or forwarding rules
Behavioral red flags
- Requests for urgent payment or confidential data
- Communication outside business hours or during executive travel
- Messages asking to bypass established procedures
Analytical controls
- Correlation rules in SIEM platforms
- Keyword-based finance mailbox monitoring
- AI-based linguistic models to detect urgency and payment patterns
Early detection reduces the risk of exploitation and limits potential financial loss.
Preventing Whaling Phishing
Preventing whaling phishing requires a layered defense combining technical, procedural, and human-focused controls.
Technical Controls
- Enforce DMARC, SPF, and DKIM on all email domains
- Require MFA for executive accounts and finance systems
- Limit executive access to critical systems through VPN-only connections
- Use endpoint protection and MDM on all executive devices
Process Controls
- Implement dual approval for wire transfers and vendor bank changes
- Require vendor identity verification via independent callback numbers
- Maintain auditable payment change logs
- Create allowlists for trusted vendors and executives
Human Controls
- Deliver targeted phishing simulation training for executives and executive assistants
- Restrict public exposure of executive email addresses
- Provide training on smishing phishing and vishing phishing to build awareness of multi-channel threats
Whaling phishing exploits trust. Restricting single points of failure blocks that path.
Executive Risk Surface: Home and Travel
Executives are vulnerable outside the corporate perimeter. Many whaling phishing campaigns begin with reconnaissance on personal networks.
- Home networks: Often lack enterprise-grade firewalls and monitoring
- Family devices: Shared networks increase exposure to malware
- Travel devices: Public Wi-Fi can enable session hijacking or traffic interception
Protective measures
- Force all executive traffic through corporate VPN connections
- Require hardware security keys for login
- Enforce mobile carrier PINs to resist SIM-swapping
- Remove unnecessary personal data from public profiles
A compromised home or travel device can give attackers a foothold into corporate systems.
Response Plan and Legal Impact
Even strong defenses can fail. A clear response plan is essential to reduce losses and meet compliance requirements.
Immediate actions
- Contact the bank to attempt a wire recall
- Freeze vendor records in ERP systems
- Lock and monitor affected executive accounts
- Preserve email headers, logs, and transaction details as evidence
Regulatory steps
- Notify cyber insurers within required time windows
- File an IC3 complaint if financial fraud occurred
- Coordinate with legal teams for contract, privacy, or GDPR obligations
A tested response plan can convert an incident into a contained event rather than a systemic crisis.
Business Impact and ROI Framing
Whaling phishing attacks are financially destructive. According to FBI IC3 data, business email compromise (BEC) losses exceeded $2.9 billion in a recent year, with many incidents traced to executive-targeted fraud.
Beyond immediate financial loss, victims face legal liability, regulatory penalties, and reputational damage. Vendor relationships, client trust, and share prices can suffer long-term consequences.
Investing in executive-targeted security controls such as VPN-only access, dual payment approvals, and targeted training reduces this risk. These measures cost far less than even a single whaling incident.
Conclusion
Whaling phishing attacks exploit trust, urgency, and executive authority. They bypass traditional filters and target the individuals who hold the keys to company finances and strategy.
PureVPN – White Label helps organizations secure executive access by providing encrypted VPN tunnels, multi-factor authentication, device posture checks, and session logging. It enables businesses to deliver a fully branded VPN platform to their executives, contractors, and vendors, reducing the chance of account compromise or data interception.


