Traditional firewalls used to be enough for most businesses. Block or allow traffic, set some rules, and you were covered. But attacks today don’t stop at ports or IP addresses. They hide inside encrypted traffic, exploit applications, and bypass legacy defenses.
This is where Firepower Threat Defense (FTD) comes in. Cisco designed it to merge the familiar ASA firewall foundation with next-generation features like intrusion prevention, URL filtering, and advanced malware defense. Instead of deploying separate tools for firewalling and intrusion detection, FTD combines them into a single unified platform.
If you run a business that handles sensitive data, finance, healthcare, SaaS, you’ll likely run into FTD when scoping out security solutions. And if you’re already a Cisco shop, it’s the logical upgrade path. Let’s break down what it is, how it works, and why it matters.
- Definition: Cisco’s Firepower Threat Defense (FTD) is a unified next-gen firewall image combining ASA firewalling with IPS, malware defense, URL filtering, and VPN support.
- Core Features: Stateful firewalling, Snort 3 IPS, application visibility, AMP malware defense, URL filtering, VPN, and centralized logging.
- Management: Managed via Firepower Device Manager (FDM) for small setups or Cisco FMC for enterprise-scale deployments.
- ASA vs FTD: ASA = classic stateful firewall. FTD = ASA + next-gen capabilities in one platform.
- Configuration: Requires Smart Licensing, policy setup, IPS tuning, and VPN configuration (see Cisco FTD guide).
- Performance: Hardware sizing must account for IPS/TLS inspection; datasheets show reduced throughput when features are enabled.
- Compliance Role: Supports PCI DSS, HIPAA, SOX, ISO 27001, and GDPR through access controls, logging, and VPN traffic encryption.
- Business Takeaway: FTD is both a security upgrade and a compliance enabler.
What Is Firepower Threat Defense?
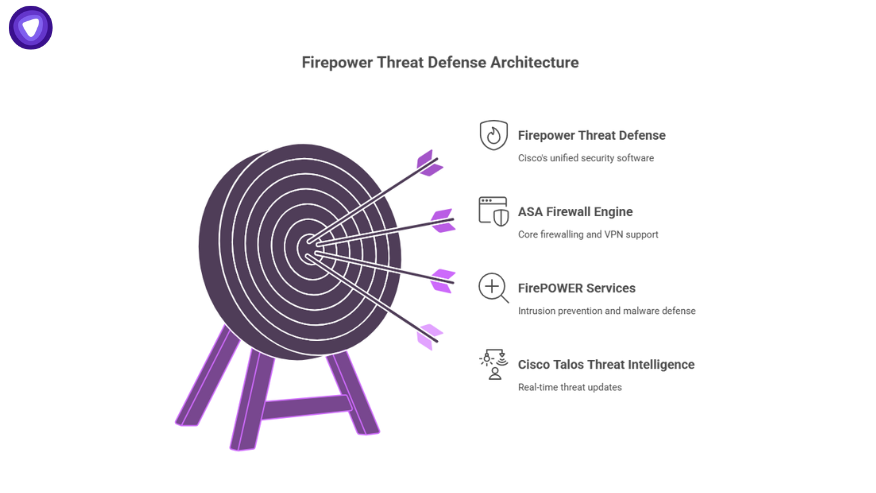
At its simplest, Firepower Threat Defense is Cisco’s unified software image that runs on their next-generation firewall appliances. It combines:
- The ASA firewall engine (stateful firewalling, VPN support).
- FirePOWER services (intrusion prevention, application control, malware defense).
- Cisco Talos threat intelligence for real-time updates.
In other words, you get the old reliability of ASA plus the advanced capabilities you expect in a next-gen firewall.
Firepower Threat Defense (FTD) is Cisco’s next-generation firewall software image that merges ASA firewall features with advanced intrusion prevention, URL filtering, and malware defense, managed through Firepower Management Center (FMC) or Firepower Device Manager (FDM).
This consolidation means businesses no longer have to choose between security depth and management simplicity.
Cisco Firepower Threat Defense Features
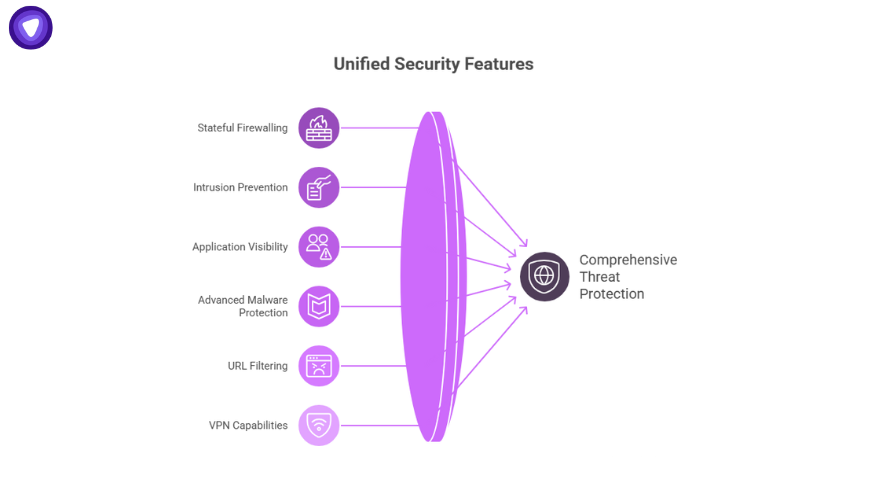
One reason FTD has gained so much traction is the breadth of its features. Looking at the Cisco Firepower Threat Defense datasheet, here are the highlights:
- Stateful firewalling: The core ASA function remains intact, offering robust policy-based access control.
- Intrusion Prevention (IPS): Powered by Snort 3, the engine inspects traffic for known and emerging exploits.
- Application Visibility and Control (AVC): Lets admins identify and block risky apps at the application layer.
- Advanced Malware Protection (AMP): Integrates with Cisco’s Talos intelligence to stop known malware and detect zero-day behavior.
- URL filtering: Blocks malicious or policy-violating websites in real time.
- VPN capabilities: Secure remote access and site-to-site VPNs for hybrid and remote-first businesses.
- Centralized logging and reporting: Key for audits and compliance checks.
These Cisco Firepower Threat Defense features are critical for businesses that must meet regulatory standards like PCI DSS, HIPAA, or ISO 27001. Instead of piecing together multiple products, FTD brings them together under one management umbrella.
What Do FTD and FMC Stand For?
- FTD = Firepower Threat Defense.
- FMC = Firepower Management Center.
The Cisco FMC is the brain of the operation. It provides centralized policy management, reporting, and monitoring for multiple FTD devices. For small deployments, you can manage FTD locally using the Firepower Device Manager (FDM). For large enterprises, FMC is essential.
| Manager | Best For | Pros | Cons |
| FMC | Large multi-device deployments | Centralized policies, advanced reporting | Higher learning curve |
| FDM | Small deployments | On-box simplicity | Limited feature set |
| Cloud-delivered FMC | Hybrid/remote environments | Cloud onboarding, zero-touch setup | Requires subscription |
For enterprises, FMC wins. For SMBs, FDM is often enough.
How Firepower Threat Defense Works?
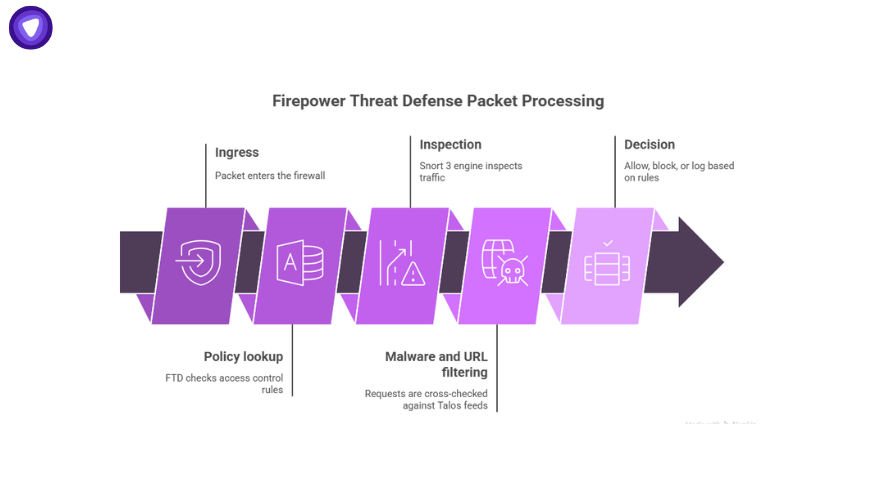
The easiest way to understand FTD is to follow a packet through it.
- Ingress: Packet enters the firewall.
- Policy lookup: FTD checks access control rules.
- Inspection: Snort 3 engine inspects traffic for signatures and anomalies.
- Malware and URL filtering: Requests are cross-checked against Talos feeds.
- Decision: Allow, block, or log based on rules.
This layered inspection lets FTD stop threats at multiple points, rather than relying on simple rule matching.
From a management perspective, policies are pushed down from FMC to each device, keeping distributed networks consistent.
Firepower Threat Defense vs ASA
This question pops up often: What’s the difference between Cisco ASA and Firepower Threat Defense?
- ASA: Classic stateful firewall with VPN and NAT. No IPS or malware defense built-in.
- FTD: ASA features plus IPS, malware defense, URL filtering, and application control.
Think of ASA as a sturdy lock on your front door. FTD adds cameras, alarms, and motion sensors—security for today’s threats.
Cisco is gradually steering customers away from ASA toward FTD. While ASA still receives updates, FTD is the future.
Deployment & Configuration Essentials
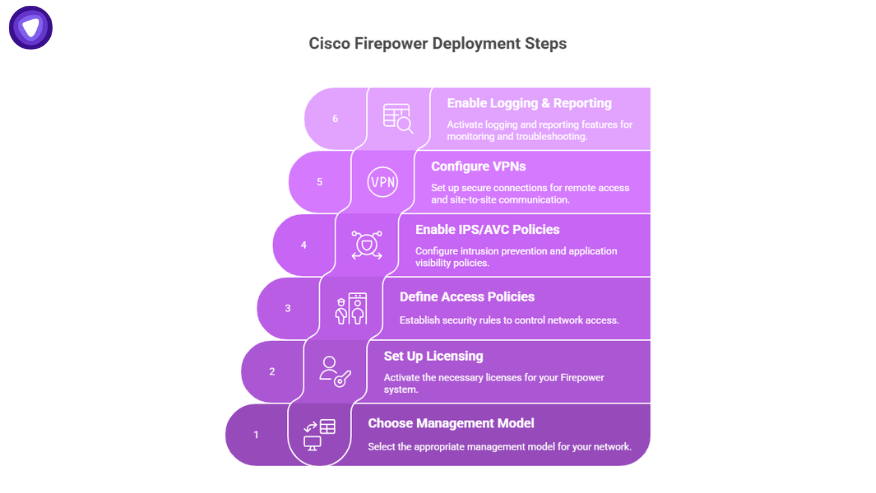
The Cisco Firepower Threat Defense configuration guide lays out deployment workflows. At a high level:
- Choose your management model: FDM (local), FMC (centralized), or cloud-delivered FMC.
- Set up licensing: Cisco Smart Licensing or Smart Licensing Satellite for air-gapped environments.
- Define access policies: Start with default deny, then build granular rules.
- Enable IPS and AVC policies: Tune Snort 3 rules for your environment.
- Configure VPNs: Remote-access and site-to-site.
- Enable logging and reporting: Critical for audits and troubleshooting.
Common pitfalls include licensing errors, performance drops with SSL decryption, and upgrade blockers when configurations are stale. Document everything—you’ll thank yourself during audits.
Performance and Sizing Considerations
Performance depends heavily on enabled features. An FTD 3100 series might hit multi-gigabit throughput in firewall-only mode, but enabling IPS and TLS decryption will reduce capacity.
That’s why the Cisco Firepower Threat Defense datasheet is essential during procurement. It provides tested numbers for each appliance under different feature sets.
Pro tip: Always size for worst-case throughput (all features on). It’s better to oversize hardware than discover bottlenecks in production.
IT Compliance and Governance Implications
Modern businesses don’t just deploy security tools to keep hackers out. They deploy them to pass audits and meet customer expectations.
Firepower Threat Defense plays directly into compliance requirements:
- PCI DSS: Protects cardholder data with segmentation, logging, and intrusion prevention.
- HIPAA: Ensures healthcare data integrity and confidentiality.
- SOX: Provides audit trails and access control for financial reporting.
- ISO 27001 / GDPR: Addresses encryption, monitoring, and risk management.
The ability to generate logs, enforce VPN connections, and block malicious content helps tick compliance boxes. But more importantly, it creates evidence—something every auditor looks for.
Extending Protection Beyond FTD With PureVPN
Cisco FTD handles the perimeter and internal segmentation well. But businesses also need to secure data in transit across remote workers, branch offices, and SaaS applications. That’s where VPNs step in.
With PureVPN White Label, resellers and MSPs can:
- Provide enterprise-grade VPN encryption under their own brand.
- Help clients meet compliance standards like HIPAA, ISO 27001, and GDPR.
- Bundle VPN with firewall deployments for a complete compliance package.
- Build recurring revenue through VPN subscriptions.
Think of it as closing the loop: FTD secures the network edge, while VPN encryption secures traffic everywhere else. Together, businesses get a stronger compliance posture and end-to-end protection.
Conclusion
Firepower Threat Defense isn’t just another firewall. It’s Cisco’s answer to the reality that threats now hide in applications, encrypted traffic, and zero-day exploits. By merging ASA with NGFW features, Cisco gives businesses a tool that protects, reports, and helps satisfy compliance requirements.
For IT leaders, FTD is both a security upgrade and a compliance enabler. For resellers and service providers, pairing it with PureVPN White Label creates a compelling offering: firewalls that protect the edge, and VPNs that protect the workforce.
The lesson is clear. Modern networks need layered defense, not single-function tools. FTD is a strong layer, but businesses that add VPN encryption complete the picture.


