Unlike traditional hacking methods, a watering hole attack preys on our tendency to trust friendly websites and platforms. It involves infecting legitimate websites frequented by specific target groups, turning these trusted online destinations into traps with digital dangers.
In this blog, we journey to understand the inner workings of watering hole attacks. We will explore the motives behind these malicious acts, dissect the attack methodology employed by cybercriminals, and shed light on the devastating consequences experienced by unsuspecting victims.

So, let us learn about the watering hole attacks, learning how to identify, prevent, and mitigate this evolving cyber threat. Together, we can navigate the digital landscape with vigilance, safeguarding our online experiences and ensuring a secure future in our interconnected world.
Real-world examples and notable incidents
Operation Aurora
One of the earliest and most well-known watering hole attacks is called Operation Aurora. It happened in 2009 and made headlines for targeting major technology companies like Google, Adobe, and Juniper Networks.
The attackers sneaked into websites that these companies’ employees often visited, and from there, they gained unauthorized access to valuable information, such as intellectual property.
Council on Foreign Relations (CFR) attack
In 2012, the Council on Foreign Relations, a renowned think tank specializing in international relations, fell victim to a watering hole attack. The attackers compromised the CFR’s website, infecting it with malicious code.
As a result, when visitors unknowingly accessed the infected website, their systems became vulnerable to exploitation. This attack aimed to access sensitive information and gather intelligence on global affairs.
Forbes.com
In 2015, the popular business news website Forbes.com became a victim of a watering hole attack. The attackers targeted the website’s “Thought of the Day” widget, which was used by millions of visitors.
By injecting malicious code into the widget, the attackers infected visitors’ systems, potentially gaining access to their personal and financial information. This incident highlighted the vulnerability of even widely trusted and popular websites.
U.S. Veterans of Foreign Wars (VFW) website attack
2019 the U.S. Veterans of Foreign Wars (VFW) official website experienced a watering hole attack. The attackers compromised the website and injected malicious code, which targeted the website’s visitors.
Source: Trend Micro
This attack specifically targeted military personnel and veterans, aiming to gather sensitive information or gain access to their systems. It underscored the risk faced by organizations that serve specific communities or industries.
NATO and Ukrainian Government
In 2017, a watering hole attack was discovered targeting the official website of the NATO Parliamentary Assembly. The attackers compromised the website and injected malicious code, aiming to gather sensitive information from government officials and policymakers visiting the site.
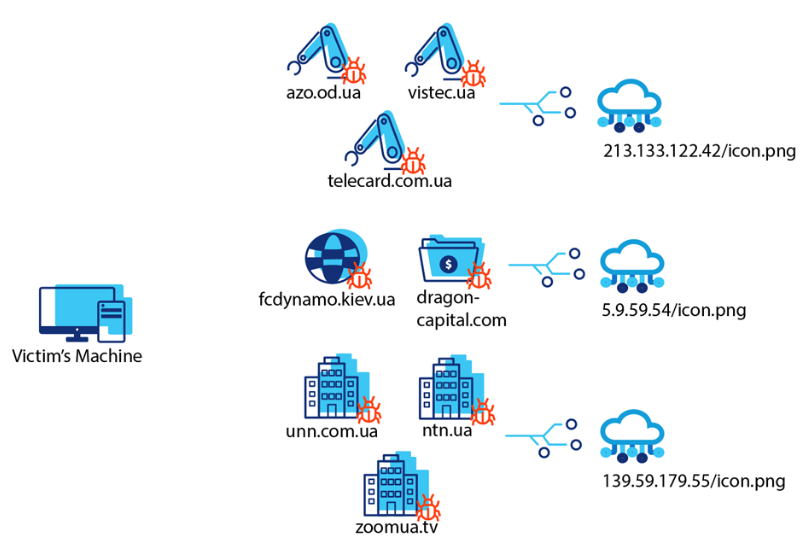
Source: Lumen
Additionally, a similar attack targeted Ukrainian government websites, exploiting the trust placed in these platforms to gain unauthorized access.
Redbanc attack
In 2018, Redbanc, a significant banking network in Chile, fell victim to a watering hole attack. The attackers compromised a corporate website used by Redbanc employees, injecting malicious code into the site.
As a result, the attackers gained access to internal systems and were able to navigate the banking network’s infrastructure. This incident highlighted the potential impact of watering hole attacks on critical infrastructure and financial institutions.
Operation Ephemeral Hydra
Operation Ephemeral Hydra, discovered in 2014, targeted various industries, including aerospace, energy, and defense. The attackers compromised websites related to these sectors and injected them with malware to infect visitors’ systems.
This campaign emphasized watering hole attacks to gain access to valuable intellectual property and sensitive information.
Microsoft Exchange Server attack
In early 2021, a widespread cyberattack targeted on-premises Microsoft Exchange Servers. The attackers leveraged watering hole tactics by compromising legitimate websites commonly visited by Exchange Server administrators.

Source: Microsoft
By injecting malicious code, they could exploit vulnerabilities in the servers and gain unauthorized access. This attack impacted thousands of organizations worldwide, leading to data breaches and system compromises.
Operation Earth Kitsune
Operation Earth Kitsune, uncovered in 2021, targeted organizations distributing COVID-19 vaccines. The attackers compromised legitimate websites associated with these organizations and injected them with malware.
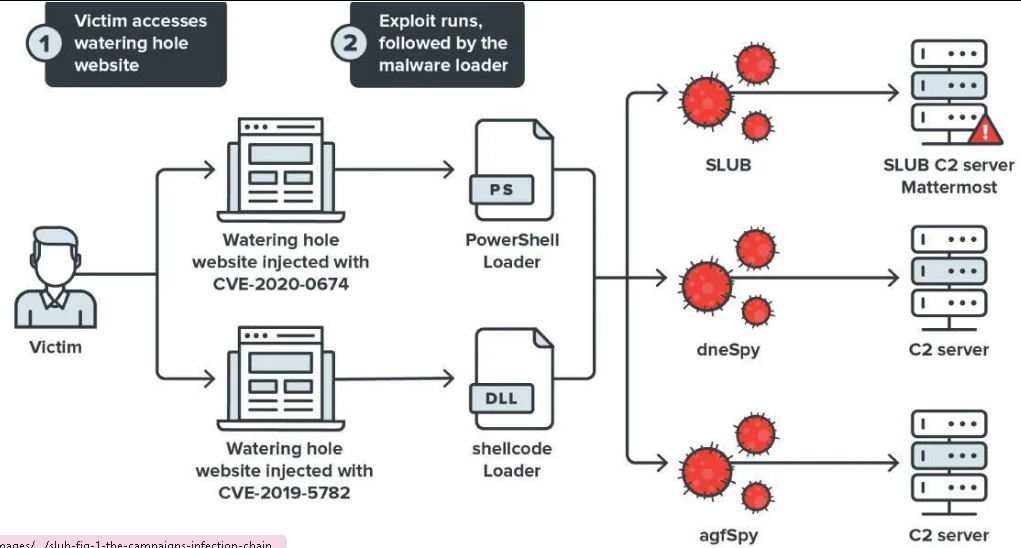
Source: Trend Micro
The objective was to collect information on vaccine distribution plans and potentially disrupt the efforts to combat the pandemic. This attack highlighted the opportunistic nature of watering hole attacks during global crises.
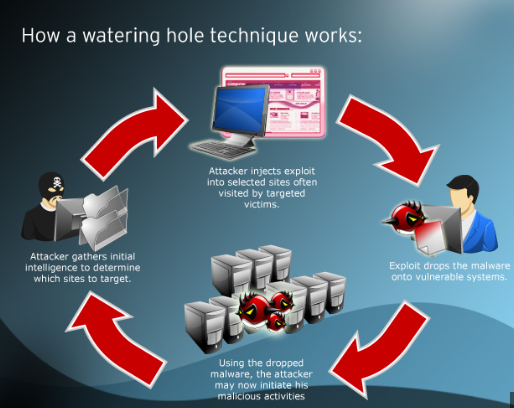
How do they do it?
Step 1: Selecting the targets
Just like a predator carefully selects its prey, attackers choose specific target groups or industries they want to compromise. They study their victims, their online behavior, and the websites they frequently visit or trust.
Step 2: Reconnaissance
Attackers gather information. They search for popular websites among the target group, analyzing their security measures, content management systems, and potential vulnerabilities.
Step 3: Breaking in
Once attackers identify a vulnerable website, they exploit weaknesses such as outdated software, content management system vulnerabilities, or third-party plugins’ flaws to gain unauthorized access.
Step 4: The trap
Now that the attackers are inside the website, they inject their trap—malicious code. It’s like planting a hidden snare in a familiar place. This code is carefully crafted to remain confidential, undetected by standard security measures, and ready to pounce on unsuspecting visitors.
Step 5: Activating the attack
With the trap set, the attackers wait for their prey to arrive. When someone visits the compromised website, the malicious code springs into action. It might exploit vulnerabilities in the visitor’s system or secretly download malware onto their device to gain control or steal sensitive information.
Step 6: The Fallout
Once the attack is successful, the attackers can achieve their goals, including stealing valuable data, gaining unauthorized access to systems, or even launching further cyberattacks.
Are APT and watering hole attacks the same?
| APT attacks | Watering hole attacks |
| APT is known for its advanced techniques and specific targeting of essential organizations. These attacks are highly skilled and well-funded. Read: Routers under APT groups attack. | Watering hole attacks are a special APT attack about deception and trust.Instead of targeting specific organizations directly, the attackers go after popular websites that their desired victims frequently visit and trust. |
| Their goal is to break into the networks of high-value targets, like government agencies or big companies, and stay hidden for a long time.They’re not just after a quick win; they want to gather valuable information, steal data, or cause damage over an extended period. | Once they find a vulnerable website, they sneak in like a stealthy predator and inject malicious code into its code.When unsuspecting visitors come to the compromised website, they unknowingly enter the trap, and their devices become infected. |
Techniques used in watering hole attacks
These are the vulnerabilities exploited in the most recent watering hole attacks:
Website profiling
Attackers study the target group and identify the websites they frequently visit. It’s like observing people’s habits and interests to understand where they hang out online. The technique includes
- Domain name analysis
- WHOIS lookup
- IP Address Analysis
- Web Server Technology Identification
- SSL/TLS certificate examination:
- Content analysis
- Link Analysis
- Traffic analysis
Source: SANS
Vulnerability Exploitation
Once the attackers have identified popular websites, they search for weaknesses or vulnerabilities, like finding a crack in a wall or an unlocked door. They exploit these vulnerabilities to gain unauthorized access. The process might include:
- Remote code execution
- SQL injections
- Cross-site scripting
- Buffer overflow
- Zero-day exploits
- Privilege escalation
- Network-based exploits
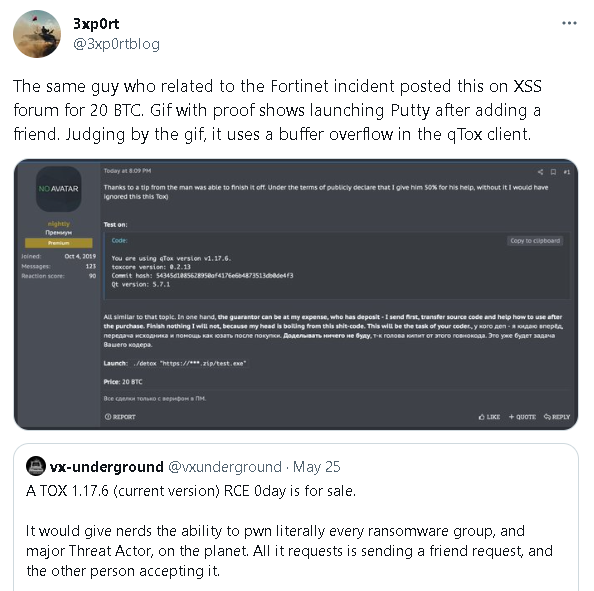
Source: Twitter
Malicious code Injection
The attackers inject their “bad” code into the compromised websites, like secretly planting a trap or a hidden bug. This code lies dormant, waiting for unsuspecting visitors to trigger it. This includes:
- Remote file inclusion (RFI)
- Local file inclusion (LFI)
- PHP code injection
- XML external entity (XXE) injection
- Code injection in file uploads

Browser exploitation
When someone visits the compromised website, the malicious code activates and takes advantage of vulnerabilities in their web browser or its plugins. It’s like finding a weak spot in the armor to penetrate the visitor’s system. It includes:
- Click-jacking
- Man-in-the-browser
- Browser exploit kits(BEKs)
- Drive by crypto-currency mining
- Same-origin policy bypass(SOP)
Drive-by downloads
The malicious code initiates a “drive-by download” without the visitor’s knowledge or consent. It’s like someone secretly slipping something into your pocket without you realizing it. This download may include malware or other malicious software. Here are some examples:
- Malicious Javascript or ActiveX control
- Exploiting browser or Plugin vulnerabilities
- Malvertising
- Compromised websites

Source: Reddit
Also read: Golden Jackal USB infiltration
System exploitation
If the visitor’s system has vulnerabilities, the downloaded malware can exploit them, like finding an open window or an unlocked door. This allows the attackers to gain control over the system or steal sensitive information. This can include all the above methods and more:
- Rootkit and backdoors
- Network sniffing and Man-in-the-middle attacks
- DDos
Source: Reddit
- Password cracking
Lateral movement
Once inside the compromised system, the attackers may explore further, like a thief rummaging through a house, to find other valuable information or move laterally within the network to reach more targets. Here’s what it might include:
- Pass-the-hash
- Credential theft and password spraying
- Exploiting shared credentials
- Remote desktop protocols hijacking
- Pass-the-ticket
- Using remote administration tools(RATs)
Watering hole attacks: Prevention and mitigation
Prevention
Keep your software updated
Remember to update your operating system, web browsers, plugins, and content management systems (CMS) to ensure you have the latest security patches. Attackers can exploit vulnerabilities in outdated software.
Use security solutions
Install reputable antivirus, anti-malware and VPN software on your devices. These tools can help detect and block malicious code or activities, providing additional protection.
Enable automatic updates
Enable automatic updates for your operating system, web browsers, plugins, and other software whenever possible. This ensures that you receive critical security patches as soon as they are available.

Be cautious of suspicious websites
Exercise caution when visiting unfamiliar or suspicious websites, especially those offering free downloads, pirated content, or adult material. Stick to reputable websites that have a track record of security and reliability.
Implement website security best practices
If you own or manage a website, follow safety best practices such as using strong passwords, regularly updating CMS and plugins, implementing web application firewalls, and performing security scans to identify vulnerabilities.
Mitigation
Network Segmentation
Segment your network into different zones or subnets with strict access controls between them. This can limit the spread of an attack and prevent lateral movement within your network.

Source: Cisco
User education and awareness
Train your employees or users about safe browsing habits, recognising phishing attempts, and the risks associated with visiting suspicious websites. Regularly remind them to exercise caution when clicking on links or downloading files.
Web filtering and content inspection
Implement web filtering solutions that block access to known malicious websites or categories of risky content. The content inspection helps identify and block malicious code or scripts.
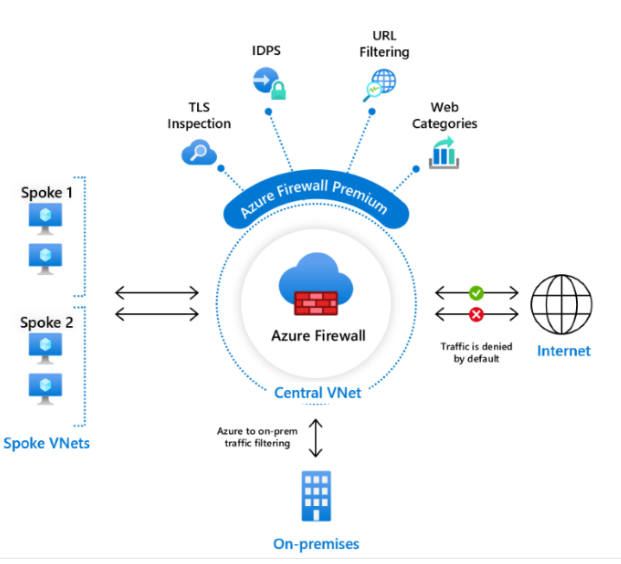
Source: Microsoft
Intrusion detection and prevention systems (IDPS)
Deploy IDPS solutions that monitor network traffic and detect suspicious or abnormal behavior. These systems can help identify and prevent watering hole attacks by raising alerts or blocking malicious activities.

Source: PurpleSec
Incident response planning to
Develop an incident response plan to define the steps to be taken in case of a watering hole attack. This includes isolating compromised systems, notifying relevant stakeholders, conducting forensic analysis, and restoring affected systems from clean backups.
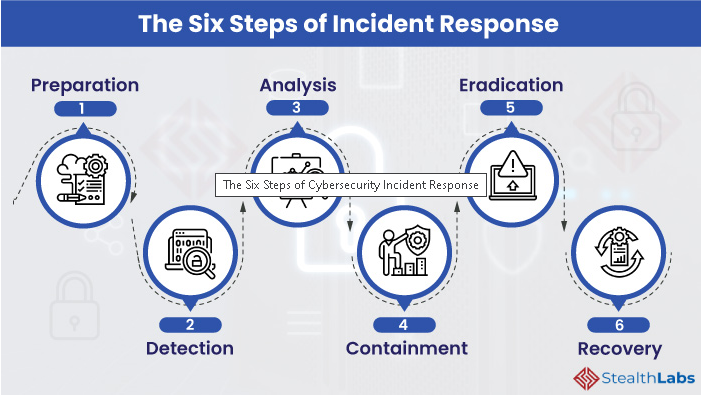
Source: StealthLab
Threat intelligence
Subscribe to threat intelligence services or utilize open-source intelligence (OSINT) to stay informed about emerging watering hole attacks, known malicious websites, and indicators of compromise (IOCs). This can help proactively protect your systems and users.

Source: Fortinet
What to do if you are under a watering hole attack?
Here’s what you should do if attacked by any of the attacks mentioned above.
Incident response plan
Have a well-defined incident response plan in place to guide your actions in the event of a watering hole attack. The plan should outline the steps to be taken, the responsibilities of team members, and communication channels to notify relevant stakeholders.
Isolate compromised systems
Isolate compromised systems from the network to prevent further damage and minimize the attack’s spread. Disconnecting affected devices can help contain the impact and prevent attackers from accessing or controlling other systems.
Source: Netskope
Forensic analysis
Perform thorough forensic analysis to understand the nature and extent of the watering hole attack. Gather evidence, such as logs, network traffic data, and system snapshots, to aid in investigating and identifying the attacker’s entry points and techniques.

Wintapix malware: Using kernel drivers and rootkits
Patch and remediate
Investigations address the vulnerabilities that allowed the watering hole attack. Apply security patches, update software and plugins, and fix any misconfigurations or weaknesses in your systems to prevent future episodes.
Communication and reporting
Notify relevant stakeholders, including senior management, IT teams, and law enforcement, if necessary. Maintain clear communication channels to inform all parties about the incident, actions taken, and any potential impact on data or operations.
Report here.

Enhance security controls
Learn from the incident and enhance your security controls accordingly. This may involve implementing additional layers of security, conducting security awareness training, or reassessing your risk management practices to prevent similar attacks in the future.

Source: Twitter
Technology and Solutions to watering hole attacks
Technology has come a long way in helping us address and protect against watering hole attacks. Let’s look at some of the advancements that have made a difference:
| Threat intelligence IBM X-force ExchangeCisco TalosMcAfee Global | We now have advanced tools that gather and analyze massive amounts of threat data. These tools help us detect and respond to watering hole attacks by keeping us updated on the latest threats and indicators of compromise. |
| Artificial Intelligence (AI) and Machine Learning Sci-kit LearnTensorFlow | AI and machine learning have transformed cybersecurity. These technologies enable systems to learn from past incidents and identify patterns that indicate a watering hole attack. They can recognize abnormal activities and block malicious code injections in real time. |
| Improved Web Application Firewalls (WAFs) Mod SecuritySophos XG Firewall | Modern WAFs have become more powerful and sophisticated. They analyze web traffic, looking for signs of a watering hole attack. They can detect unusual behavior, match attack signatures, and learn from past attacks to stay ahead of the game. |
| Behavioral Analytics Google AnalyticsAmplitude | We now have tools that analyze user behavior and system activities. By understanding what’s expected, they can flag any unusual actions indicating a watering hole attack. This helps us spot suspicious website access, data theft attempts, or strange network communications. |
| Stronger Network Traffic Monitoring and Intrusion Detection Systems (IDS) SnortPalo Alto Networks Next-Generation Firewall (NGFW) | Monitoring network traffic has become more effective in detecting watering hole attacks. These systems examine network packets, track traffic patterns, and use intelligent algorithms to identify signs of an attack. They’ll raise an alarm as soon as they spot anything suspicious. |
| Better Vulnerability Management Tools Tenable NessusQualysBeyondTrust Retina | Identifying vulnerabilities has become easier with automated scanning tools. They help us find weaknesses in software components, allowing us to patch or address them before attackers can exploit them in a watering hole attack. |
| Enhanced endpoint security solutions Symantec CrowdStrike FalconCarbon Black | Protection for individual devices has improved too. Advanced endpoint security tools can now analyze behavior, learn from past incidents, and prevent malware downloads. They closely monitor activities, detecting any signs of trouble and providing real-time threat information. |
| Efficient threat hunting and incident response platforms IBM ResilientFireEye HelixAtlassian Jira | Platforms designed for threat hunting and incident response have made our lives easier. They gather security event data from various sources, allowing us to proactively search for threats, investigate compromised systems, and orchestrate effective responses. |
Concluding thoughts: Embrace the cyber attacks but fight them back
We need to acknowledge the harsh reality of cyberattacks and their potential harm. Rather than letting fear consume us, we must take a proactive stance and fight back against these malicious acts. Watering hole attacks remind us of the importance of trust and caution in our digital interactions.
There is no substitute for prevention. We must remain vigilant and invest in effective detection and response mechanisms. By leveraging advanced tools like threat intelligence, behavioral analytics, and machine learning, we can spot unusual patterns and activities that indicate a watering hole attack. This allows us to respond swiftly, minimizing damage and protecting our users.
Recognizing the role technological advancements play in our fight against cyberattacks is imperative. Artificial intelligence and machine learning algorithms have greatly improved our ability to analyze large amounts of data, identify suspicious behavior, and enhance overall security.
Cyber attacks must not discourage us. By embracing the challenge, equipping ourselves with the right tools, and fostering a culture of cybersecurity awareness, we can stand up against these attacks. This will create a safer digital environment. We can build a resilient and secure online world for ourselves and future generations.
Frequently Asked Questions
Watering hole phishing is like a sneaky trap set by hackers. They target websites or online platforms that people frequently visit and trust. Instead of directly attacking individuals, hackers infect these trusted websites with malicious code. Once the malware is on our devices can steal our data, such as login credentials or credit card information.
It is a social engineering attack. The attacker tries to create a pretext to get you hacked. They use communication channels like text messages, phone calls or customer care representatives and develop stories to obtain personal information that they use to exploit.
No, it is not. Whaling attack targets high-level executives to extract data for a phishing attack later. Watering hole attacks involve compromising websites and platforms. The purpose of both is deceit, but the technique used differs.
The attacker may use many tactics, including malicious website codes, exploit kits, website cloning, zero-day exploits, etc.
The attacks made before the software developers and administrators become aware of them are called zero-day attacks. The impact is severe because of no prior knowledge about the vulnerability or attack.
The term refers to intelligent ways to exploit the trusted website. This could be described in detail in the blog above.
Watering hole attacks are challenging to locate, but there are some ways to do so. These include
– Unusual behavior of the targeted website
– Unusual network traffic
– Detection by security software
– Additional permissions prompts
Supply chain attacks target the software supply chain of specific organizations. They do not directly target the website or platforms. The difference between a supply chain attack and a watering hole attack is the initiation of the attack.
In June 2022, AccessPress, a company that develops WordPress plugins and themes, was targeted by hackers. The hackers
– Uploaded malicious code to the company’s plugins and themes
– Users downloaded and installed the malicious plugins and themes
The main goal is to get access without detection. They are specialized hackers who work diligently for data exfiltration, intellectual property theft, espionage and surveillance, sabotage, lateral movements, etc.
APT attacks are carefully designed planning attacks. They involve advanced technology, long-term planning,targeted approach, insider knowledge and expertise to deploy attacks successfully.
APT stands for Advanced Persistent Threat. The term takes its name because it uses advanced technology, has a long-term focus and hits the target on point. These attacks remain hidden for a long time and are difficult to detect.
It is a challenging task to detect APT attacks. Due to their stealthy nature, they go undetected, but some strategies might help:
– Network traffic analysis
– Endpoint monitoring
– User behavior analytics
– Incident response planning
