Zyxel is cautioning its customers about two severe vulnerabilities in its firewall and VPN products. Attackers can exploit these vulnerabilities without needing authentication.
Both of these security issues are called buffer overflows, and they can lead to denial-of-service (DoS) attacks and remote code execution on vulnerable devices.
Zyxel’s suo moto
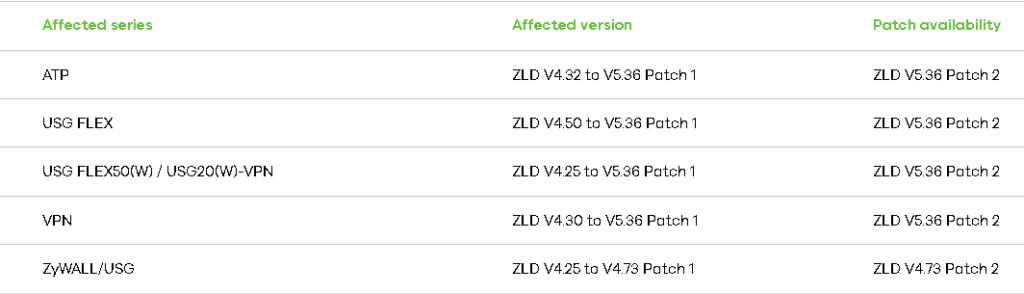
Zyxel has released patches to fix these buffer overflow vulnerabilities in their affected firewalls. They are advising users to install these patches to ensure optimal protection.
- It is strongly recommended that users of the affected products install the latest security updates as soon as possible to prevent hackers from taking advantage of these flaws.
These vulnerable devices are commonly used by small to medium-sized businesses to safeguard their networks and enable secure access to remote or home-based workers through VPNs.
Cybercriminals pay close attention to critical vulnerabilities in such devices because they provide an easy pathway to gain unauthorized access to corporate networks.
Just last week, cybersecurity researcher Kevin Beaumont reported that a command injection flaw, which Zyxel had already fixed in April, is currently being exploited. This flaw affects the same firewall and VPN products as the current vulnerabilities.
In the past, CISA (Cybersecurity and Infrastructure Security Agency) warned about hackers exploiting a remote code execution flaw in Zyxel firewall and VPN devices. They urged system administrators to apply the firmware patches promptly.
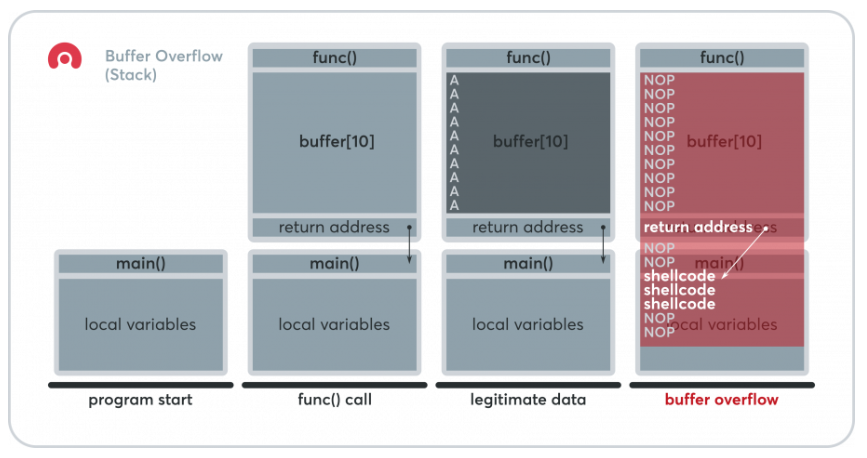
What’s buffer overflow?
Buffer overflow is a type of mistake or weakness in computer software that hackers exploit to gain unauthorized access to corporate systems. It is a well-known vulnerability in software security, but it still happens quite often. This is partly because buffer overflows can happen differently, and the methods used to prevent them are often prone to errors.
Source: Acunetix
The software mistake mainly revolves around buffers, which are sections of computer memory used to store data as it moves between different places temporarily. Buffer overflow, also called buffer overrun, occurs when a buffer’s data exceeds its storage capacity. The extra data spills into neighboring memory locations and causes damage or overwrites the data stored there, but successful exploitation can lead to executing code on the device too.
Patchwork to look for
Zyxel’s latest patch addresses the following problems:
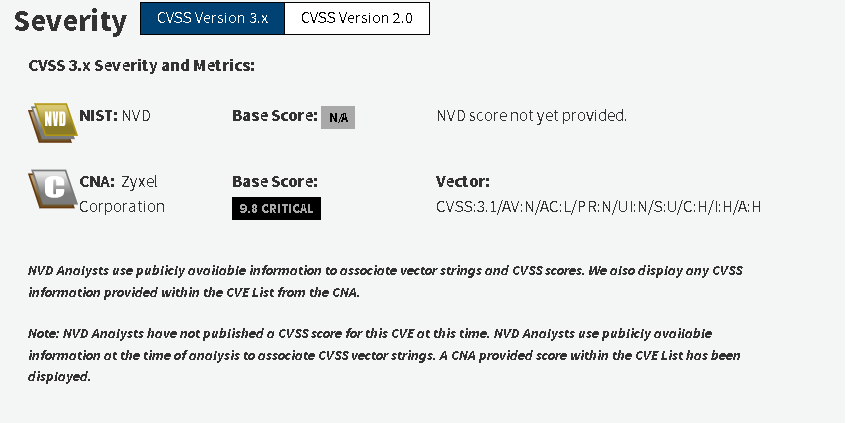
CVE-2023-33009: A buffer overflow vulnerability in the notification function of certain Zyxel products. This allows attackers without authentication to execute code remotely or cause DoS conditions. (Critical severity with a score of 9.8)
Source: CISA
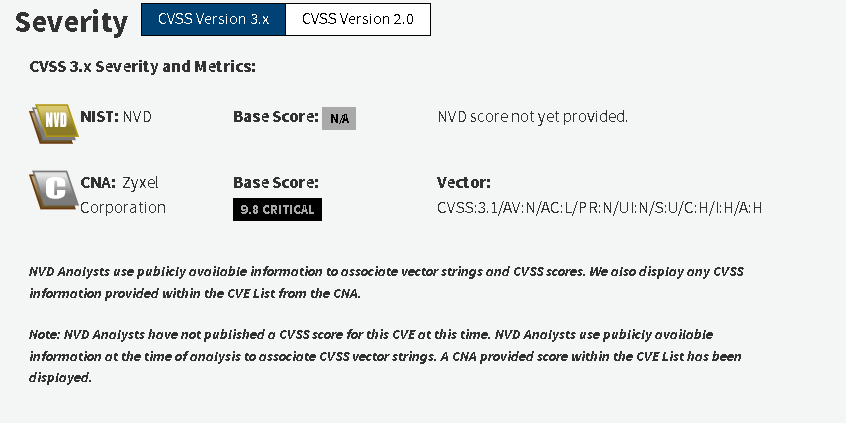
CVE-2023-33010: A buffer overflow vulnerability in the ID processing function of certain Zyxel products. This allows attackers without authentication to execute code remotely or cause DoS conditions. (Critical severity with a score of 9.8).
Source: CISA
Source: Zyxel
Working to prevent buffer overflow
Preventing buffer overflow errors is similar to preventing many other vulnerabilities. The key is to be cautious of user input. Regarding buffer overflow vulnerabilities, developers need to check the input length before using functions that could potentially cause an overflow.
However, we’re all human, and it’s not uncommon for developers to forget this important rule. Even code reviewers might overlook such errors. That’s why, in the C language, it’s safest to avoid certain functions that can lead to buffer overflow vulnerabilities: printf, sprintf, strcat, strcpy, and gets.

Unfortunately, the base C language offers only one secure alternative:
- fgets (to be used instead of gets). Different platforms have their non-standard implementations. For instance, the Microsoft C version includes sprintf_s, strcpy_s, and strcat_s. The best practice on Linux/UNIX systems is to prohibit unsafe functions and promote using the Safe C Library.
Source: Wallarm
- use a compiler extension employing canaries. Canaries are particular values the compiler places on the stack between the buffer location and control data. When a buffer overflow occurs, the canary is the first to be corrupted, allowing for immediate corruption detection. Several compiler extensions, such as StackGuard and ProPolice, incorporate canaries.
Overall, it’s essential to be cautious about user input, avoid unsafe functions, and consider utilizing compiler extensions that offer additional protection against buffer overflows.
Pledge not to be vulnerable
Developers can significantly mitigate the risk of buffer overflow vulnerabilities and enhance software security by implementing preventive measures and adhering to secure coding practices. Software developers, code reviewers, and organizations must prioritize identifying, remedying, and preventing buffer overflow vulnerabilities to safeguard sensitive data and protect against unauthorized access.



