An unidentified cyber threat actor has been detected employing a malicious Windows kernel driver in attacks that appear to be targeting the Middle East since at least May 2020.
According to Fortinet Fortiguard Labs, the malware, named WINTAPIX or WinTapix.sys, is believed with little certainty to be associated with an Iranian threat actor.
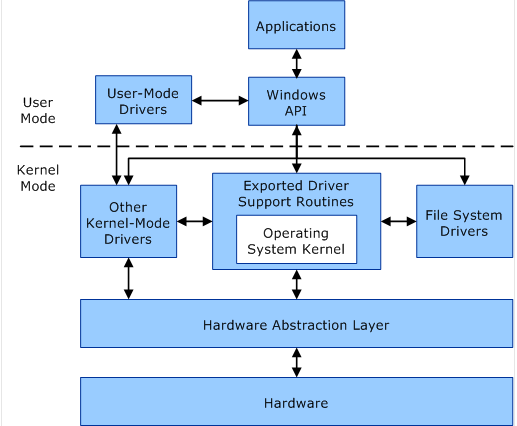
Working order of WinTapix.sys
Essentially functioning as a loader, WinTapix.sys’s primary objective is to
- generate and execute the next attack phase by utilizing a shellcode, as security researchers Geri Revay and Hossein Jazi stated in a recently published report.
“Fortinet’s analysis of samples and telemetry data indicates that the campaign’s primary focus is on Saudi Arabia, Jordan, Qatar, and the United Arab Emirates. However, no conclusive evidence currently links the activity to a known threat actor or group.”
- By employing a malicious driver that operates in kernel mode, the attacker aims to circumvent or disable security mechanisms, thereby obtaining deep-rooted access to the targeted system.
- To clarify, these drivers operate within the kernel memory, granting them the capability to perform various operations, including modifying critical security mechanisms and executing arbitrary code with the highest privileges.
Consequently, this provides a covert means to infiltrate the system further, establish persistence, and execute additional payloads or commands as part of a multi-stage attack orchestrated by the threat actor.
What could you do?
Driver Signature Enforcement is a crucial security measure to mitigate the risks posed by malicious drivers, which ensures that only Microsoft-signed drivers can be loaded onto the system. Microsoft also maintains driver block rules to safeguard against known vulnerable
drivers.
Anomaly of execution
- WinTapix.sys possesses an invalid signature, indicating that the threat actor must first load a legitimate yet vulnerable driver to initiate WINTAPIX.
- Once successfully loaded into the kernel, WinTapix.sys is configured to inject an embedded shellcode into an appropriate user mode process, executing an encrypted .NET payload.
- Additionally, WINTAPIX incorporates a shellcode created using the open-source Donut project. It establishes persistence by modifying the Windows Registry, enabling it to load even when the system is booted in Safe Mode.
- The .NET malware has backdoor and proxy functionalities, allowing the threat actor to execute commands, carry out file downloads and uploads, and act as a proxy to facilitate data transfer between two communication endpoints.
Finding the origin
The researchers note that Iranian threat actors are known to exploit Exchange servers to deploy additional malware, suggesting the possibility of this driver being employed alongside Exchange attacks.
Furthermore, the compilation time of the drivers coincides with periods when Iranian threat actors were exploiting vulnerabilities in Exchange servers.
These developments come at a time when the ALPHA ransomware group, also known as BlackCat or Noberus, has been observed utilizing a malicious signed driver to evade security defenses and remain undetected for extended durations.
The driver in question, ktgn. sys, is an updated version of POORTRY, which is signed using a stolen or leaked cross-signing certificate, as revealed in a report by cybersecurity firm Trend Micro.
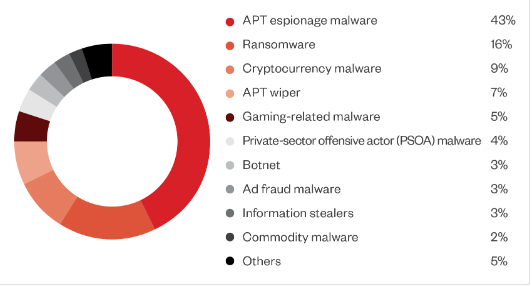
Source: Trend Micro
POORTRY is a Windows kernel driver with capabilities to terminate security software. It was previously disclosed as being used by ransomware groups and a threat actor known as UNC3944, also identified as Roasted 0ktapus and Scattered Spider.
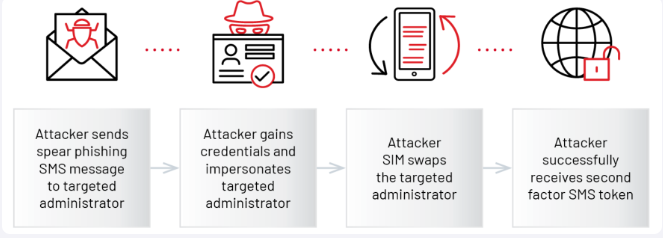
Source: Mandiant
Trend Micro highlights that “malicious actors actively seeking elevated privileges within the Windows operating system employ techniques that counter the enhanced protection offered by endpoint protection platform (EPP) and endpoint detection and response (EDR) technologies.”
These malicious actors often possess sufficient financial resources to acquire rootkits from underground sources or purchase code-signing certificates to develop their own.
Conclusive recommendations: Detection and removal of rootkits
To identify such a hook, we must load a driver that scans the main functions table in the associated driver and compares each pointer to the address range of the driver’s module. If a pointer falls outside this range, another module will likely hook it. It’s relatively straightforward to detect.
However, there are other techniques for hooking significant functions. Some rootkits don’t modify the address in the table itself but instead alter the assembly instructions at the beginning of the function to redirect to the hooking module. This method is known as an Inline hook.
To remove an IRP hook, you need to locate the original address of the significant function and replace the modified address in the table with the correct one. This action effectively eliminates the filter and leaves the rootkit vulnerable. It’s crucial to ensure the restoration process is executed seamlessly (in an atomic manner) to avoid any potential Blue Screen of Death (BSoD) issues.



