One false click can cost you millions. It’s not just a warning, it’s a reality. In 2024, ransomware attacked 59% of organizations, according to Sophos “State of Ransomware 2024” .The Medusa ransomware gang is among the most dangerous groups, leading sophisticated phishing campaigns against businesses, educational institutions, and healthcare systems with particular evolving cyber threats.
The key to cybersecurity in 2025 is to understand how the Medusa ransomware gang works and how to protect yourself from it.
This blog highlights how Medusa ransomware gang’s phishing operation works, what tactics are used to entice victims, and how to best protect yourself from being Medusa ransomware gang’s next victim.
Who is the Medusa Ransomware Gang?
The Medusa ransomware group surfaced around the year 2023 and became known for their use of tactics that they call double extortion. It means that your data is not just encrypted with ransomware but they threaten leaking of the stolen files unless a ransom is paid.
This group affiliates launch attacks using RaaS (Ransomware-as-a-Service) business model, meaning cybercriminals rent out ransomware tools to others for a share of the profits. This increases their potential for damage and unpredictability.
How Do Medusa Ransomware Gang Phishing Campaigns Work?
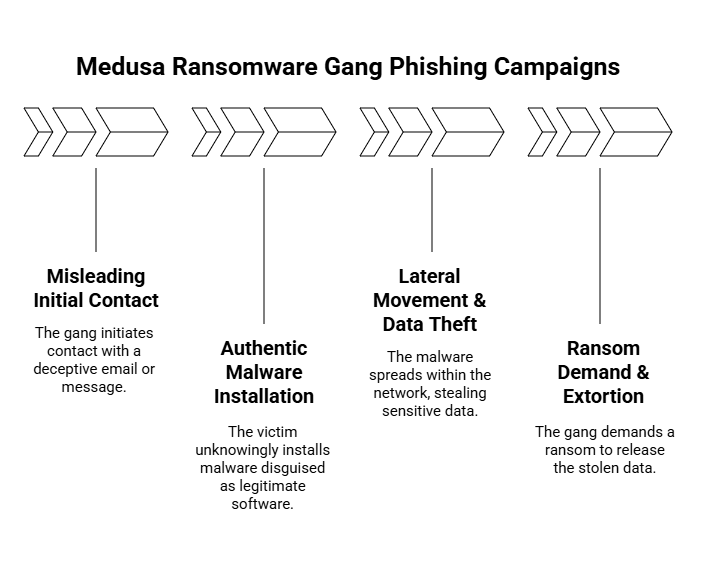
The Medusa ransomware group conducts well-planned phishing campaigns, often involving multiple stages, such as from email to data breach to ransom demand, following these typical steps in their phishing campaigns:
1. Misleading Initial Contact
Attackers send phishing emails, disguised as a legitimate message such as invoices, job offers, or security alerts to lure victims to click on links or download files.
2. Authentic Malware Installation
If the victim opens the document or clicks the link, the link or attached document installs malware like Remote Access Trojans (RATs), keyloggers, or loader programs that outfit the victim’s system with the Medusa ransomware.
3. Lateral Movement and Data Theft
Using the malware to connect and move around the network, the attackers access file servers, credentials, and backup data, stealing sensitive pieces of data in advance of deploying the ransomware.
4. Ransom Demand and Extortion
Victims receive a ransom note asking for cryptocurrency. If the ransom is not paid, Medusa states they will post the victim’s stolen data on their leak site or the dark web.
They Sell Your Data on the Dark Web, Even If You Don’t Pay
Here’s the scary part: the Medusa ransomware gang doesn’t just lock your files and ask for money, they actually steal your data first. And if you don’t pay up? They don’t just walk away. They dump your sensitive information on the dark web for anyone to buy.
That means customer records, internal emails, financial details, employee data, basically, everything you don’t want in the wrong hands, can end up being auctioned off to cybercriminals. It’s a nasty way to pressure victims into paying, but also a secondary income stream for Medusa.
And once your data’s out there? You can’t undo it. It can lead to identity theft, fraud, and long-term reputation damage for your business.
How to Stay a Step Ahead
To avoid ending up in that nightmare:
- Back up your data offline—regularly.
- Use PureVPN to encrypt your remote connections (especially important for remote workers).
- Train your team to spot phishing emails—they’re the #1 entry point.
- Enable multi-factor authentication for everything.
- Keep your software up-to-date to patch security holes.
- Monitor the dark web for signs your email or credentials are being sold (PureVPN offers a free scan).
Your email could be compromised.
Scan it on the dark web for free – no signup required.
Medusa Ransomware Gang Targets
Medusa ransomware gang phishing campaigns target sectors that have confidential data. An example of high-profile victim of this target includes Minneapolis Public School District, where 100GB of sensitive data was exfiltrated and demanded a $1 million ransom.
They often attack profitable small and medium sized enterprises (SMEs) to access sensitive data with significant digital infrastructure and relying on business continuity.
8 Effective Ways to Stay Safe from Medusa Phishing Campaigns
The utmost priorities to protect yourself from the Medusa ransomware gang are good cyber hygiene and proactive defense strategies. Having proper employee security awareness, utilization of advanced security tools, and keeping systems up-to-date, will help mitigate the risk of being attacked.
Take a deeper look into the effective ways to be safe from Medusa ransomware gang attacks:
How to Protect Against Medusa Ransomware
- Maintain offline backups of sensitive business data in secure, physically separated locations.
- Use strong authentication aligned with NIST standards, including robust password policies and multifactor authentication.
- Regularly update all software, OS, and firmware with the latest security patches.
- Segment your network to limit lateral movement after a breach.
- Monitor network activity and implement endpoint detection and response (EDR) tools to flag suspicious behavior.
- Require employees to use PureVPN for secure remote access.
- Apply the principle of least privilege—grant users access only as needed for their roles.
- Filter network traffic to block packets from unknown or untrusted sources.
Signs of a Phishing Attack
Spotting early warning signs will protect you from falling into the Medusa phishing trap. Monitor these signs to avoid falling victim to Medusa ransomware gang’s tactics.
- Look for strange or urgent emails that pressure you to act immediately.
- Poor spelling, formatting, or grammar are often the signs of a scam.
- Different email address to that of the sender’s address. Look for these small changes in the domain.
- Unexpected attachments or links are the signs of the scam. Avoid clicking or opening them.
5 Things to Do When Attacked by Medusa Ransomware Gang
If you have been affected by the Medusa ransomware gang, time is of the essence to mitigate damage, loss of data, and potential data breach. Below are the five steps you should take as soon as possible to secure your systems and respond appropriately.
- Isolate infected systems from the network right away.
- Notify your IT department, as well as your legal teams.
- Contact cybersecurity specialists, or CERT (Computer Emergency Response Team) for guidance.
- Do not pay the ransom (you need to preserve this option if all others fail and paying the ransom only encourages more attacks).
- Report the attack to the authorities, such as local police cybercrime units or European and International organizations (INTERPOL, Europol).
What are the Common Medusa Ransomware Tactics?
The Medusa ransomware phishing campaigns include aggressive and deceptive tactics to creep into systems and extort victims. Here are the most common ones highlighted:
- Phishing emails are disguised as legitimate emails, used to convince the recipient to take action such as clicking on a link or opening an attachment.
- Double extortion with simultaneous data encryption and the threat of public data exposure.
- RATs (Remote Access Trojans) that infect and then silently/secretly control the infected device.
- The ability to laterally move across networks and access multiple endpoints and escalate attacks.
- Targeted attacks against critical infrastructure like health care, financial services, and education.
- Ransom notes with strict deadlines and escalating threats.
- Leaking victim organizations’ data to leak sites like the Medusa Blog to coerce ransom payment while also harming reputations.
Final Thoughts
The Medusa ransomware gang continues to represent a significant and growing threat through phishing campaigns which are extremely deceptive, and extortion tactics that are quite aggressive. To protect against these attacks, it is necessary to provide your team with training in cybersecurity awareness, perform proper system hardening, and ensure users are aware of what constitutes phishing.
An adequate degree of vigilance consists of; continuous updates, multifactor authentication, and real-time monitoring. Being proactive about this isn’t optional, it is your best form of defense against ransomware.
Frequently Asked Questions
Phishing is a part of cyberattack that reveals user sensitive information whereas ransomware encrypts the data while demanding payment for release.
A Medusa email is a phishing message sent by a Medusa ransomware gang with malicious links or attachments that initiate attacks.
The healthcare industry is the most targeted sector due to sensitive data needed for operational continuity.
Do not open the links or download attachments given in the email, instead report to your IT or security team instantly.








