Your email could be compromised.
Scan it on the dark web for free – no signup required.
You Lock Your Car — But Did You Lock Your Identity?
You’d never drive off with your car unlocked. Yet many leave the virtual doors open to their most sensitive data, without even realizing it. That’s what’s happening right now at Volvo: the automaker’s internal engine wasn’t hacked, but their employees’ data was siphoned off via their HR software vendor.
And now names, Social Security numbers, employment records, and screenshots may be available on the dark web forums. If your name, SSN, or work identity shows up in a leaked file, it won’t matter whose firewall failed — the damage is real.
This edition takes you inside how metadata becomes the hidden weapon, why hackers crave it on the dark web, and how you can check if your own metadata is already at risk.
What’s the News (in Short)
- Volvo North America confirmed its employee data (names + SSNs) were exposed in a ransomware attack on its HR software vendor Miljödata.
- The attack (on Miljödata’s Adato platform) occurred on August 20; Miljödata detected it on August 23.
- It is believed that Miljödata’s breach have touched 870,000+ accounts across multiple organizations.
- Volvo says its own internal systems were not breached, but that doesn’t mean the supply chain damage isn’t crashing in on them.
What Happened — The Timeline & Key Facts
- On August 20, 2025, Swedish HR software vendor Miljödata (which provides HR/workforce systems like “Adato”) was hit by the DataCarry ransomware gang.
- The breach was discovered three days later, and Volvo was notified.
- Volvo North America’s own systems were reportedly untouched; the attackers accessed HR data via the supplier.
- The exposed data reportedly includes first and last names as well as Social Security Numbers (SSNs) for certain employees.
- Volvo has confirmed it will offer identity theft protection/credit monitoring services to affected parties.
- The broader Miljödata breach also allegedly affected over 1.5 million individuals, exposing their names, dates of birth, email addresses, physical addresses, identity numbers, and other personal information.
What Was Leaked (or at Risk)?
Here’s what we know (and what we suspect) was accessed:
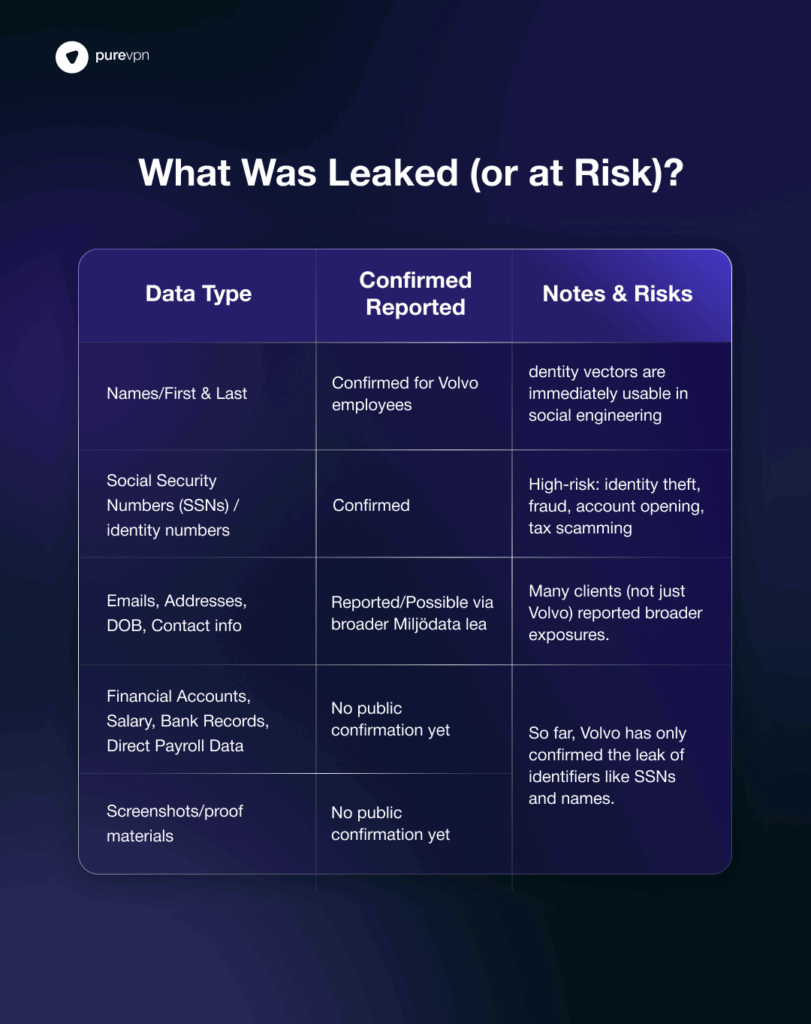
This breach is what one calls a “metaphor leak”— where the thieves didn’t steal the whole car but they grabbed its keys, license plates, and everything that proves it’s your.
Who’s Behind It?
- The DataCarry ransomware group is claiming responsibility for the Miljödata breach (the vendor through which Volvo’s data was exposed), with double-extortion tactics: steal data first, then encrypt.
- DataCarry is relatively new on the scene (first observed May 2025) but has quickly adopted a classic double-extortion style: steal data, then encrypt and demand ransom.
- They demanded ~1.5 BTC (~USD $165,000).
- They threatened to publish the stolen data on the dark web/Tor leak site if demands aren’t met; some stolen files already show up in disclosed posts.
Miljödata & the Supply-Chain Breach Pattern
Miljödata provides HR systems — including absence tracking, workforce management, and rehabilitation workflows — for many organizations. Because their systems operate across clients, one breach can become a mass exposure event.
In this case, the attacker group DataCarry claimed responsibility and threatened to publish exfiltrated files to the dark web. Some proof materials have already surfaced.
Why This Breach Stings
- Identity Theft Goldmine: Names + SSNs = identity weapons. Attackers can fabricate accounts, open lines of credit, or commit tax fraud. Attackers don’t need your password—they already have your identity.
- Proof = Leverage: Screenshots or sample files published by hackers make it believable; they prove they had access. That raises potential extortion (publish more or sell, phishing, or secondary leaks.
- Metadata as Bait: Internal directories, roles, HR metadata, system paths, and user IDs leaked in proofs let attackers impersonate attacks convincingly.
- Dark Web Resale & Cross-linking: Once this data hits criminal forums, it’s resold in bundles, cross-referenced with other leaks (credential stuffing).
- Supplier Domino Effect: Miljödata serves municipalities, universities, and many firms. So the breach is a wide net; attackers use Volvo’s leak to target other organizations that use the same supplier.
- Phishing on Steroids: Expect scams referencing HR details (“your benefits package”, “SSN verification”, “payroll issue”) using real, accurate personal data.
What to Do Right Now (Your Defense Checklist)
- Run PureVPN’s Dark Web Exposure Scan — You can scan your email address for free using Dark Web Exposure Scan (already linked above) to see if it appears in any known breaches or leaks on the dark web. It works even if you’re not a user of PureVPN — so anyone can check if their critical personal identifiers are exposed.
In less than 30 seconds, you’ll learn:
- If you are exposed
- How severe is the compromise
- How recent was the leak
- How many breaches include your account
2. Monitor your credit & identity — set fraud alerts, review tax records, watch for unfamiliar accounts.
3. Change & strengthen passwords — especially for any systems linked to HR, payroll, or employee portals.
4. Enable MFA everywhere — particularly for internal tools, email, and HR systems.
5. Be wary of phishing — scammers will use leaked personal data (name, SSN, role) in messages/emails to impersonate legitimate internal HR or security teams.
6. Demand vendor transparency — if you work for or are a partner of affected orgs, ask them which HR systems/data were impacted, and whether vendor audits have been updated.
7. Stay skeptical of ‘HR’ emails — if someone contacts you referencing benefits, SSN, or personal data, double-check via known internal contacts.
What’s Next
Volvo’s breach shows a harsh truth: even if your own systems are locked tight, your people’s data can be stolen via someone else’s weak link. Expect more proof dumps, more dark web listings, and aggressive phishing or identity fraud attempts targeting affected employees.
Those impacted should already assume they’re in the crosshairs. Stay alert. Verify every email or call. Change your credentials. And if you haven’t yet, run that Dark Web Exposure Scan so you know whether your identity is already on the chopping block.
Because sometimes the darkest leaks don’t come from your firewall—they come through your vendor.
📬 Why Subscribe?
Every week, we cut through the noise and bring you the breaches that matter, the tactics behind them, and the steps you need to protect yourself — all in a conversational, no-fluff format.
If you don’t want to be the last to know when your personal data hits the dark web, subscribing is your safety net.
👉 Stay ahead, stay secure, stay subscribed.
Note: This edition of Dark Web Digest is based on publicly available information as of Sept 30th, 2025.








