The dark web is a small but persistent slice of the internet where criminals buy and sell contraband, trade stolen data, and coordinate cybercrime. For years, it felt like a safe place, hidden behind Tor and private cryptocurrencies. But law enforcement agencies worldwide have developed tools and techniques to penetrate and host undercover operations, blockchain analytics, malware and device forensics, and international coordination.
We will discuss how investigators find suspects on the dark web, what’s changed recently, and what defenses criminals now use.
Your email could be compromised.
Scan it on the dark web for free – no signup required.
How the Dark Web Works?
“Dark web” is intentionally hidden from standard search engines and requires special software or configurations to access. The best-known layer is Tor, the Onion Router, where sites use .onion addresses. Darknet markets, private forums, and encrypted messaging services operate there.
Payments are commonly made in cryptocurrencies, historically Bitcoin, though privacy coins such as Monero and off-chain escrow models have become prominent.
What Law Enforcement Needs to Find on the Dark Web?
Investigators aiming to take down vendors, marketplaces, or buyers on the dark web focus on three linked elements:
- Identity attribution — who is behind an account, vendor, or server.
- Communication links — who is talking to whom, on what channels, and when.
- Financial trails and proceeds — how money moves from illicit sales to cash-out points.
A successful case usually combines multiple evidence types: seized servers, identified crypto addresses and chain links, device data, and witness or undercover testimony.
Key Investigative Methods To Expose Dark Web Crimes
Teams rarely rely on a single method; multi-disciplinary correlation is standard to make results accurate.
Human Intelligence and Undercover Operations
Undercover agents and confidential informants still form the backbone of many cases. Investigators create accounts, build reputations on forums, and make test purchases. These operations:
- reveal vendors’ tradecraft and OPSEC errors
- can induce targets into revealing shipping addresses or communications channels
- provide admissible evidence (chat logs, purchase records)
Undercover operations are time-consuming but effective, especially when paired with technical monitoring.
Read: Top Dark Web Sites to explore
Blockchain and Transaction Forensics
Cryptocurrency tracing tools help investigators follow money on the blockchain. They can connect transactions, spot deposits at exchanges, and detect attempts to hide funds through mixers. Even “anonymous” transactions often pass through regulated exchanges, where Know Your Customer (KYC) rules can reveal who is behind them.
Key points:
- Bitcoin transactions are recorded permanently on a public ledger, which makes it possible to map connections.
- Mixers and privacy tricks make tracking harder, but repeated patterns and timing often give clues.
- Privacy coins like Monero are much harder to trace, and many dark web markets now prefer Monero-only payments.
Read: How to check if your email is on the dark web
Recent industry analyses show that crypto-enabled drug sales and darknet market inflows remained significant in 2024, even while patterns shifted. Chainalysis and other firms track these flows and produce metrics that investigators use to triage cases.
Network-Level Analysis and Tor Weaknesses
Though Tor obscures IP addresses by routing traffic through multiple relays, real-world deployments leak metadata:
- Misconfigured hidden services (e.g., improperly configured web servers) can reveal IPs.
- When law enforcement controls or observes both ends of a connection, they can correlate timing and packet-level features to deanonymize users,this is resource-intensive but feasible in targeted cases.
- Unpatched web stacks or plugins running on .onion sites can produce exploits or forensic artifacts.
Europol’s 2024 IOCTA notes Tor remains the dominant access method to the dark web, and that law enforcement continues to exploit operational weaknesses to take down services.
Malware, Device and Memory Forensics
Investigators commonly use malware analysis and device forensics:
- Seized devices: phones, laptops, and servers often contain keys, private messages, or browser metadata that link users to dark web accounts.
- Memory forensics: RAM often holds decryption keys and session tokens that don’t survive power cycles; live forensic techniques can extract them.
- Custom implants and server-side access: In some cases, authorities deploy lawful access tools (exploits or server compromises) to capture sessions or logins in real time.
These methods are powerful but legally sensitive, often requiring judicial oversight and cross-jurisdictional coordination.
OSINT and Link Analysis
Open-source intelligence (OSINT) fills the gaps: correlating usernames, PGP keys, email addresses, shipping patterns, and reused aliases across forums and social media. Graph databases and link-analysis platforms make it possible to identify networks and hierarchies.
Read: How to Access the Dark Web on iPhone
Operational Techniques
Sting operations, honeypots, and platform compromise. Law enforcement sometimes runs honeypot marketplaces or compromises existing marketplaces to harvest user data. Large takedowns often follow long periods of secret infiltration. Combining a platform compromise with blockchain tracing can lead to broad enforcement actions.
Tools, Vendors, and Platforms Investigators Use to Track Cyber Criminals on the Dark Web
Law enforcement agencies increasingly rely on commercially developed analytics platforms plus in-house tooling:
- Blockchain analysis vendors: Chainalysis, TRM Labs, Elliptic, CipherTrace, these provide entity clustering, exchange tagging, and risk scores.
- Network forensics suites: packet analysis and traffic-correlation tools.
- Open-source scraping and OSINT tools: for crawling forums and extracting PGP keys or usernames.
- Forensic suites: Cellebrite, Magnet, and vendor tooling for memory forensics, disk imaging, and mobile extraction.
These tools are complemented by legal authorities, search warrants, MLATs (Mutual Legal Assistance Treaties), and partnerships with hosting providers and exchanges.
Recent Results and Trends (2024–2025) Exposing Dark Web
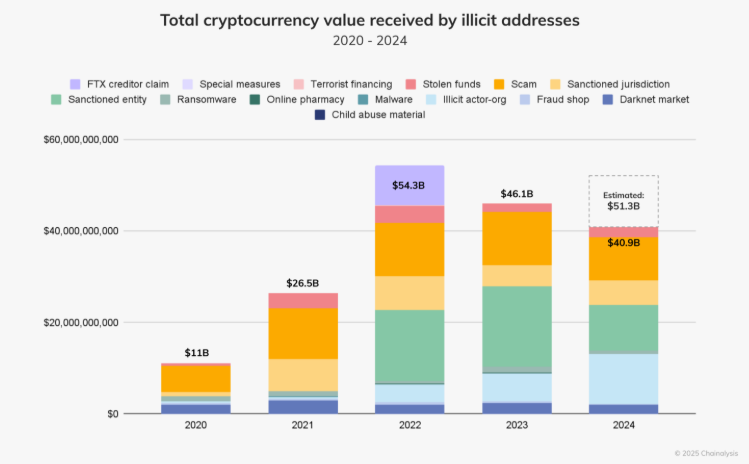
Recent reports give us a sharp snapshot of how the dark web economy is evolving and how law enforcement is striking back. Chainalysis (2024) revealed that illicit crypto addresses pulled in around $40.9 billion, a staggering figure that proves crypto remains the lifeblood of online crime.
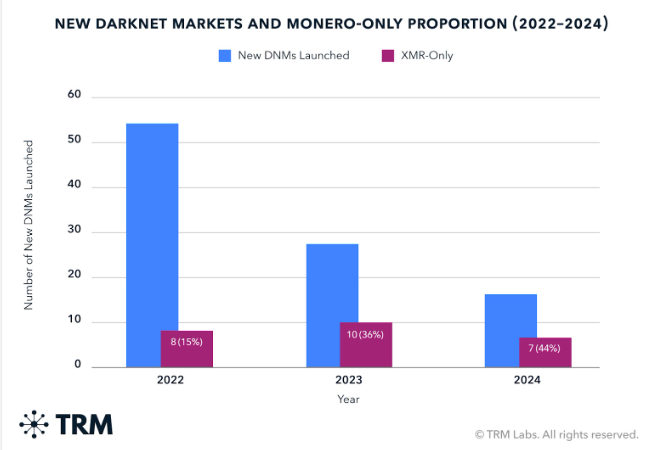
At the same time, TRM Labs and Chainalysis estimate that darknet markets moved $2.0–$2.4 billion in drugs and illicit goods, with a clear shift toward Monero-only payments and off-chain escrow systems, changes that make investigators’ jobs far more complex.
Yet, law enforcement isn’t falling behind: the FBI reported a major multinational operation leading to about 270 arrests, while ICE’s Operation SaboTor netted 61 arrests, along with hundreds of kilograms of drugs, firearms, and millions in cash and crypto.
Adding to that, TRM Labs found that the number of new darknet markets dropped by 42% in 2024, while Monero adoption surged, showing criminals prefer privacy over volume.

What’s the takeaway? While bad actors are upgrading their tactics with privacy coins and encrypted channels, law enforcement is scaling up too, combining advanced tools, intelligence sharing, and international partnerships. The cat-and-mouse game continues, but one truth stands out: nobody is truly untouchable on the dark web.
How to Protect Your Data from Being Sold on the Dark Web
Once your personal information hits the dark web, it spreads fast — and silently. But you don’t have to wait for a breach notification email to know you’ve been compromised.
PureVPN’s Dark Web Monitoring acts as your digital watchdog. It continuously scans underground marketplaces, breach forums, and leaked credential dumps for any trace of your email, passwords, or identity markers.
The moment it detects your information on the dark web, you get an instant alert — giving you a head start to reset passwords, freeze accounts, or secure your identity before damage is done.
Challenges and Countermeasures Used by Criminals
Investigators are chasing a moving target because criminals keep upgrading their tactics.
1. Privacy Coins like Monero
Monero hides transaction details, making it much harder to track money directly on the blockchain. Many markets now only accept Monero, but once funds are converted into other coins or cashed out through exchanges, investigators can still find clues.
2. Mixers and Chain Hopping
Criminals often use tools like mixers or cross-chain swaps to jumble and move money between different cryptocurrencies. This muddies the trail, but investigators sometimes uncover links by looking at timing patterns and repeated behaviors.

3. Stronger Operational Security (OPSEC)
Instead of being careless, many criminals now use separate devices for each task, hardware wallets to store funds offline, “burner” phones for short-term use, and private forums that require invites. This makes it harder for simple mistakes to give them away.
4. Moving off Marketplaces
To stay under the radar, some sellers avoid big darknet markets and shift deals into encrypted messaging apps or direct person-to-person transactions. This strips away the marketplace data that investigators usually rely on.
How Dark Web Investigations Scale into Arrests and Seizures
A workflow from detection to arrest is somewhat like this:
- Detection — OSINT, tip-offs, or blockchain alerts identify suspicious addresses, marketplace activity, or vendor listings.
- Assessment — analysts score risk, look for KYC links, and try to link crypto flows to known exchanges or services.
- Infiltration/operational contact — undercover agents engage vendors/buyers to confirm identities or trade patterns.
- Technical exploitation — investigators seize servers, exploit software vulnerabilities, or use lawful hacking where permitted.
- Forensics & link analysis — device seizures and chain analysis provide linkage evidence.
- Legal steps & coordination — warrants, MLATs, and joint operations lead to arrests and asset seizure.
- Prosecution — evidence is presented, often combining blockchain analytics, seized devices, and undercover testimony.
This explains why takedowns often occur after long, multi-jurisdictional investigations.

What Steps Security Teams and Policy Makers Can Take to Enforce Better Investigation?
Security teams and policy makers both play a crucial role in strengthening dark web investigations. Together, these steps can be a strong step against evolving cybercrime.
For Corporate Security Teams
- Monitor for leakage: stolen credentials and internal documents often surface on dark web forums. Active scanning and threat intelligence subscriptions reduce response time.
- Prepare to produce evidence: preserve logs and transaction histories; they’re often required by law enforcement during investigations.
- Work with vendors: blockchain tracing providers and digital risk-intelligence vendors can give early warning on compromised data.
For Policy Makers & Public Defenders
- Balance privacy and enforcement: policies must protect legitimate privacy while enabling lawful investigative techniques with strong oversight.
- Support cross-border cooperation: the most effective operations involve coordinated international action, legal harmonization, and fast MLAT processes.
- Invest in forensic capacity: memory forensics, blockchain tracing, and digital evidence management require funding and training.
Frequently Asked Questions
Yes, Bitcoin is public. Investigators use clustering and exchange KYC records to link addresses to individuals. Privacy techniques can delay or complicate the link but often do not make it impossible.
Monero is designed for privacy and is much harder to trace than Bitcoin. However, operational mistakes, exchange interactions, or off-chain behavior can still expose users.
They usually follow lengthy infiltration, technical exploits, or server seizures, blockchain tracing, and international law enforcement coordination, combining undercover operations and forensic evidence.
Yes, coordinated operations have achieved major takedowns and arrests in 2024–2025. Still, new markets and privacy technologies mean the fight continues.
Preserve evidence, document systems compromised, notify law enforcement and affected customers as required, and use digital risk monitoring to track and mitigate exposure.
Wrap Up
Tracking criminals on the dark web is a technical, legal, and organizational challenge. If you’re a security leader, monitor dark web exposures, invest in forensic readiness, and partner with trusted intelligence vendors. If you’re a policymaker, ensure that awful oversight and cross-border cooperation remain priorities.
If you are an individual who knows the value of data in this age, then keep your data, identity and location safe. Switch to PureVPN and completely manage your online identity.








