Do you think that the dark web is something mysterious, illicit, and best avoided?
When most people hear the term “dark web,” the images that flash through their minds are rarely positive. Headlines scream about drug markets, hackers selling stolen data, or shadowy forums plotting cybercrime.
The very same tools that criminals exploit, like Tor and end-to-end encryption, are the ones that protect those who fight for truth, transparency, and human rights. Far from being just an underground dystopia, the dark web can be a platform for resistance and accountability.
In this guide, we’ll see how the dark web is used for good, empowering whistleblowers, privacy advocates, and everyday people who value freedom.
The Dark Web’s Reputation vs Reality
The dark web has always been a paradox. On one hand, it’s infamous for illegal markets, stolen data, and hacking tools. On the other, it’s a place for privacy, whistleblowing, and free speech. To understand its true identity, we need to look at both sides of the spectrum.
Your email could be compromised.
Scan it on the dark web for free – no signup required.
When you read about the dark web in mainstream media, chances are it’s tied to criminal activity. Marketplaces like Silk Road or AlphaBay once dominated headlines, offering drugs, weapons, or counterfeit documents. Even today, cybercriminals exploit hidden networks to sell stolen data, distribute malware, or launch ransomware operations.
According to a Panda Security report, the dark web sees around 3 million daily users, and nearly 60% of indexed domains are linked to illicit content. This is the side that justifies the dark web’s sinister reputation and why law enforcement agencies prioritize disrupting these ecosystems.

Yet, the dark web isn’t just a criminal marketplace. Hidden among the noise are platforms designed to protect truth and freedom.
- SecureDrop and GlobaLeaks allow whistleblowers to submit documents anonymously to journalists.
- NGOs and human rights organizations host onion sites to stay accessible even in censored regions.
- Privacy-focused blogs and forums educate users on encryption, safe browsing, and digital rights.
Even mainstream privacy tools are part of this ecosystem. Services like P-Mail and Riseup use encryption and dark web access to help you communicate securely without fear of surveillance.
So, which version of the dark web is real? The truth is both. It exists in shades of light and dark. Yes, there are dangerous spaces filled with illegal trade. But there are also progressive, protective corners that empower journalists, activists, and everyday people seeking privacy.
How Whistleblowers Use the Dark Web
Whistleblowing has always been about courage, standing up to powerful forces to reveal wrongdoing. But these brave individuals need more than courage; they need tools that keep them invisible, secure, and impactful. Let’s explore the cutting-edge technologies making that possible today.
SecureDrop & WeDrop: Still Leading the Way
SecureDrop remains the gold standard in secure communication for whistleblowers, and its reputation persists for a reason. This open-source system runs exclusively through Tor, strips metadata, and ensures submissions remain anonymously encrypted. Trusted media giants like The New York Times, The Guardian, and CNN rely on SecureDrop to receive sensitive tips safely. South Africa’s News24 recently adopted SecureDrop in late 2024 to strengthen its whistleblowing infrastructure.
For resource-constrained NGOs or grassroots projects, WeDrop.org offers a lighter alternative: a Tor-based whistleblower server that requires fewer resources to set up and maintain while still ensuring anonymity.
GlobaLeaks: Scaling Anonymity for Governments and NGOs
GlobaLeaks is an open-source framework that makes it easy for organizations, from city councils to national anti-corruption bodies, to create and manage anonymous whistleblowing platforms. It’s built with security at the core (Tor integration, encrypted storage, GDPR compliance) and is accessible even to non-technical administrators.
In 2025, the European Union spotlighted GlobaLeaks as a vital tool for transparency. For instance:
- Barcelona’s municipal government launched “Bústia Ètica” using GlobaLeaks for confidential citizen reporting.
- Italy’s National Anti-Corruption Authority adopted it nationally to let insiders report corruption securely.
Today, GlobaLeaks underpins over 30,000 whistleblowing platforms worldwide, a testament to its scalability and reliability.
CoverDrop & Secure Messaging
CoverDrop, a brainchild of University of Cambridge researchers, takes a clever, stealthy approach: integrate anonymous leaks into everyday news app traffic. Real messages get mixed amongst decoy messages from regular users, making the whistleblower virtually invisible.
In 2025, this research became real-world tech when The Guardian embedded it into their news app as “Secure Messaging.” It helps whistleblowers reach journalists without raising suspicion, and even authorities who seize the device can’t tell whether the app was used to leak.
Real-World Case Studies Witnessing the Use of Dark Web for Good
In 2024, Nigerian scientist Dr. Lillian Ndidi revealed environmental damage and bribe schemes tied to an oil spill. Facing threats, loss of funding, and travel restrictions, she remained anonymous because of encrypted tools like SecureDrop and ProtonMail, though her case highlights that whistleblowers still need broader protection, including relocation and legal support.
A data scientist uncovered bias in national diagnostic AI models that misdiagnosed women and ethnic minorities. Using a double-masked submission service hosted in Luxembourg, the whistleblower shared code and findings anonymously, leading to:
- The algorithm’s suspension and re-engineering.
- A formal parliamentary investigation.
- Personal safety protection allows them to eventually step forward voluntarily.
Studies show that anonymity on the dark web is not just a convenience, it’s essential for press freedom and safety. For whistleblowers globally, anonymity platforms are the difference between silence and accountability. Researchers stress that tools like SecureDrop, GlobaLeaks, and CoverDrop are critical in safeguarding courageous disclosures.
How Privacy Advocates Use the Dark Web
When oppressive governments block websites and silence dissent, the dark web offers a digital lifeline. Let’s explore how privacy advocates use Tor and related platforms to preserve access to truth, free expression, and human rights.
Censorship Resistance
Authoritarian regimes, from Iran and China to Russia, frequently impose heavy internet censorship. Users in these regions rely on Tor, especially features like bridges and pluggable transports, to bypass these digital barriers.
For instance, during the Mahsa Amini protests in Iran and following Russia’s invasion of Ukraine, Tor usage surged as citizens sought unrestricted information.
Amnesty International even launched its global site as an .onion service in December 2023, making its human rights reporting accessible in countries where its regular website is blocked, empowering users under surveillance to access vital content safely.

Platforms at Work
Several trusted organizations offer dark web services to help activists communicate securely:
- Amnesty International, as covered above, uses its Tor onion site to resist censorship and support human rights accessibility.
- Other major institutions, like the BBC, ProPublica, The New York Times, and Deutsche Welle, run onion versions of their websites, preserving independent journalism in censored regions.
Platforms at Work: Communication Tools
Encrypted communication services play a critical role:
- Riseup, a collective-run platform, provides secure email, chat, VPNs, and mailing lists, tailored specifically for activists and social justice communities. Their services are accessible via Tor for users needing extra privacy protection.
- Proton (Proton Mail, encrypted file storage, calendar) offers onion-based access, ensuring that communication remains private, anonymous, and resistant to surveillance, even when surface web access is restricted.
Beyond censorship circumvention and secure comms, the dark web is a hub for digital safety education. Privacy-aware blogs, encrypted guides, and open-source security resources often operate via onion sites, sharing essential knowledge where open platforms are censored.
Curated directories point users toward safe, verified services, keeping them away from suspicious links and malware. Reports show that the dark web attracts around 3 million daily users, and a large portion of that usage is for legitimate, beneficial activities like secure communication and free speech protection.
The Role of Anonymity and Encryption
When people talk about online privacy, two tools usually come up: Tor and VPNs. They’re often considered complicated, but in reality, they’re the building blocks of safe communication for journalists, whistleblowers, and everyday people who just want to protect their digital lives.
Tor & Onion Routing Explained
Tor bounces your data through several relays, peeling away a layer of encryption at each step. By the time it reaches the destination, no single relay knows both where it started and where it ends.
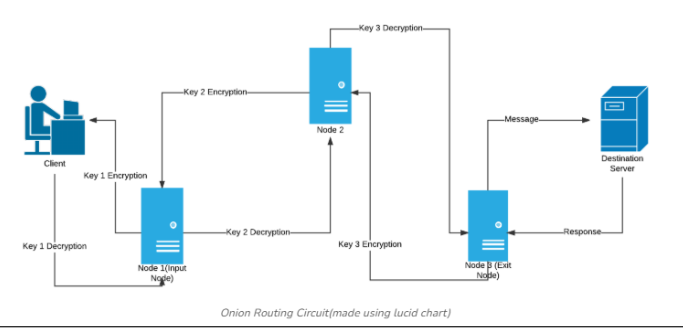
This makes Tor incredibly powerful for anyone needing anonymity, whether it’s a dissident in Russia, a journalist in Myanmar, or just you wanting to keep advertisers out of your search history.
Why Tor Matters in Real Life
Tor isn’t just for “hackers in hoodies.” It’s backed by organizations like Amnesty International and the ACLU as a lifeline for human rights and free expression. They’ve publicly stated that Tor is essential for protecting sources, whistleblowers, and citizens living under censorship.
That’s why outlets like The Guardian, The New York Times, and ProPublica even run Tor-powered sites. They want whistleblowers and readers in blocked countries to safely access their reporting.
The Risks & What Research Shows
Of course, Tor isn’t perfect. Researchers are constantly finding both strengths and weak points.
Duplicate Content Problem
A recent arXiv study found that 82% of Tor hidden sites are duplicates or mirrors. In other words, the dark web isn’t as big as it looks; lots of sites are just clones of each other. That doesn’t make Tor unsafe, but it does mean its ecosystem is often misrepresented.
IoT Devices Under Attack
The TORCHLIGHT project revealed something more concerning: criminals use Tor to hide attacks on smart devices (IoT). Over a year, researchers analyzed 26 terabytes of traffic and discovered 45 vulnerabilities, including 29 zero-day flaws, affecting 12.7 million devices in 148 countries. That’s everything from baby monitors to smart fridges being targeted via Tor.
Selective Deanonymization (Seldom)
To address abuse, another group of researchers introduced Seldom, a system that allows conditional deanonymization. It is like a “break glass in case of emergency” switch, if someone is using Tor for serious crimes, their anonymity could be lifted, but only under strict oversight and logged transparently on a public ledger.
Future-Proofing Tor: Innovations Ahead
Projects like VaulTor aim to make Tor safer for legitimate users. It creates “vault overlay nodes” that help prevent deanonymization attacks on hidden services, without hurting regular anonymity.
This matters because as governments and criminals try to exploit weaknesses, the Tor community is also innovating to stay one step ahead.
Where a VPN Fits Into the Picture
You’ve probably noticed by now that Tor is powerful, but not bulletproof. It keeps your browsing anonymous by bouncing traffic across multiple relays, but it has some weak spots you shouldn’t ignore.
Why Tor Alone Isn’t Enough
Even if your activity is hidden, your internet provider can see that you’ve connected to the Tor network. In some countries, that’s enough to raise suspicion, or even trigger surveillance.
Remember the last relay in the Tor chain? That’s called the exit node, and it’s the point where your encrypted traffic finally reaches the internet. If the site you’re visiting doesn’t use HTTPS, the exit node could technically monitor your activity.
This doesn’t mean Tor is unsafe, it just means you need another layer of defense, and that’s where a VPN comes in.
- A VPN hides your real IP address before your traffic even touches Tor.
- Your ISP only sees you’re connected to a VPN, not Tor.
- If an exit node is compromised, your traffic is still protected by the VPN’s encryption.
The best practice? Connect to your VPN first, and then launch Tor. This setup is called Tor over VPN, and it’s widely recommended for journalists, whistleblowers, and privacy-conscious users.
Which VPN to Use Over Tor?
Not all VPNs are built the same. For Tor users, you want a service that prioritizes privacy without sacrificing speed. That’s where PureVPN fits perfectly:
- Hides your activity from your ISPs and other surveillance.
- Change your IP address to stay safe when you’re on hotel, airport, or café networks.
- Stops shady exit nodes and dark websites from sneaking in trackers.
- Gets real-time alerts of data leaks through dark web monitoring.
- Controls how your data is exposed across social platforms.
With 6,000+ high-speed servers worldwide, PureVPN also ensures you won’t suffer the lag many Tor users complain about.
Conclusion
For years, the dark web has been portrayed as a shadowy space filled with crime and chaos. And yes, that side exists. But there’s another story tool, it is a tool of empowerment. It’s where whistleblowers can hold the powerful accountable, where journalists in repressive regimes can publish without fear, and where privacy advocates can keep the flame of digital freedom alive.
So the next time you hear “dark web,” don’t just picture crime. Plus, always try to keep your identity secure. If you decide to access the dark web, use a VPN, Tor, and prudence to never share your personal details on any platform across the internet.