Researchers have shared detailed information about a commercial Android spyware called Predator, sold by the Israeli company Intellexa (formerly Cytrox). Google’s Threat Analysis Group initially discovered a predator in May 2022. It exploits vulnerabilities in the Chrome web browser and Android operating system.
Uncovering Predator’s arsenal
The spyware, delivered through a component called Alien, can
- secretly record phone calls, messages, and contacts from various apps, including Signal, WhatsApp, and Telegram.
- It can also hide and prevent applications from running when the device restarts.
Alien is not just a loader but also sets up the necessary capabilities for Predator to spy on victims. It bypasses Android’s security features to execute commands from Predator, making it versatile and dangerous.
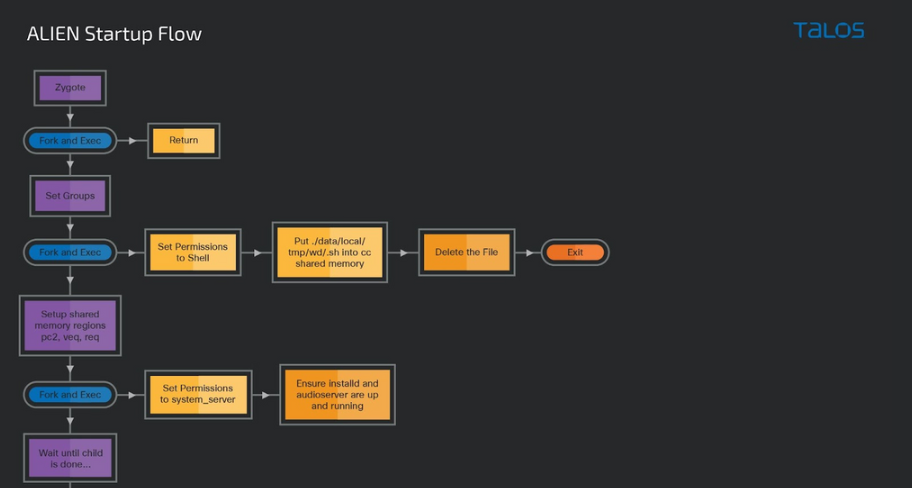
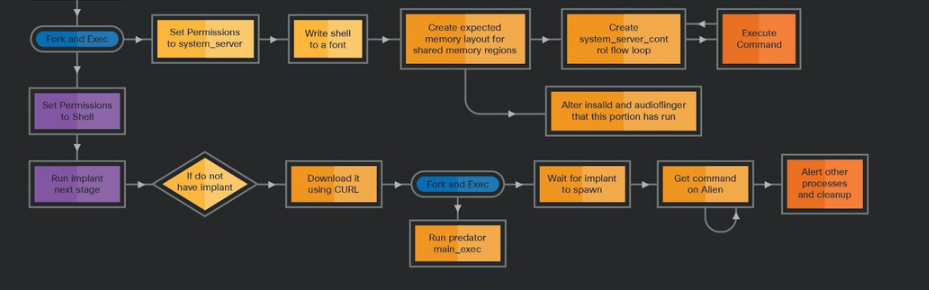
Source: Talos
According to Google: “We assess that these campaigns delivered ALIEN, a simple Android malware in charge of loading PREDATOR, an Android implant described by CitizenLab in December 2021. ALIEN lives inside multiple privileged processes and receives commands from PREDATOR over IPC. These commands include recording audio, adding CA certificates, and hiding apps.”
Predator and Alien exploit security loopholes in Android, with Alien being loaded into a core Android process called Zygote. It downloads and launches other spyware modules, including Predator, from an external server.
“The zygote64 and system_server call chains are the ones that do the most work, while the installed call chain sets up the file structures for the other portions of the spyware. Each of these call chains sets up a process structure used to intercept specific ioctl commands, where the spyware uses the functionality of that process to abuse the SELinux context to grant different functionality to the other methods.”
It’s unclear how Alien is initially activated on an infected device, but it’s suspected to be loaded
- through exploits
- can execute commands from Predator,
- allowing it to evade certain security features of the Android framework.
Predator and its capability
Predator’s Python modules enable it to
- steal information, surveillance, remote access, and run arbitrary code
- add certificates and explore directories on specific device models.
However, some essential pieces of the spyware puzzle are still missing, such as the main module called tcore and a privilege escalation mechanism known as kmem. These components might include features like geolocation tracking, camera access, and covert spying on victims.

Source: Talos
In recent years, commercial spyware like Predator has seen increased use by threat actors. While it’s meant for legitimate purposes, it has been misused to surveil dissidents, activists, journalists, and others.
Know more about commercial spyware.
Folding it up
The revelations surrounding spyware, such as Predator and Pegasus, underscore the urgent need for robust regulations, oversight, and accountability measures to safeguard individuals from unwarranted surveillance. Balancing legitimate security concerns with protecting fundamental rights is highly important.
As technology continues to evolve, governments, technology companies, and civil society must collaborate and establish effective frameworks that address commercial spyware’s ethical and legal challenges. This includes promoting transparency, ensuring informed consent, and developing strong cybersecurity measures to safeguard against malicious exploitation.
Also, international cooperation and information sharing among stakeholders are essential to mitigate the risks associated with the proliferation and misuse of these powerful surveillance tools. By collectively addressing the threats posed by commercial spyware, we can work towards a safer digital environment that respects privacy, upholds human rights, and fosters trust in the digital age.









