A group called OilAlpha, believed to be connected to Yemen’s Houthi movement, has been involved in a cyber spying campaign targeting organizations in the Arabian Peninsula. They used encrypted messaging apps like WhatsApp to trick their targets and also used shortened URLs. Most of the targeted entities were Arabic speakers using Android devices.
Discussing more about OilAlpha
OilAlpha is the new name given by Recorded Future to two groups known as TAG-41 and TAG-62. The company has monitored these groups since April 2022. TAG-XX is a temporary name given to emerging threat groups.
The reason for linking OilAlpha to the Houthi movement is that they mainly use the infrastructure associated with Yemen’s Public Telecommunication Corporation (PTC) under Houthi control. However, it’s still possible that a third-party compromised the PTC assets. No evidence was found to support this theory.
OilAlpha also used malicious Android apps to spy on delegates involved in Saudi Arabian government-led negotiations. These apps pretended to be associated with the Saudi Arabian government and a humanitarian organization in the U.A.E.
What’s more?
The attack targeted Android users in the Arabian Peninsula because there are many Android devices in the region. OilAlpha also used desktop malware, such as njRAT, in its operations.
“OilAlpha threat actors are highly likely to be involved in espionage activity, as handheld devices were targeted with remote access tools (RATs) like SpyNote and SpyMax. We have also observed njRAT samples communicating with C2s associated with this group, making it likely that OilAlpha has used other malware for testing or attack operations.”
Recorded Future believes that OilAlpha was instructed by the Houthi movement to carry out these attacks. However, it’s unclear if the group is directly affiliated with the Houthis or if they are working as a contractor. Other threat actors, such as Hezbollah from Lebanon or Iraq, or Iranian operators supporting the IRGC, could also be responsible for these attacks.
Android-based attacks
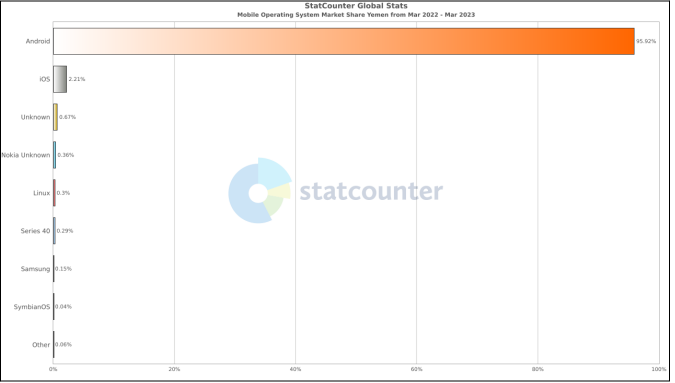
OilAlpha’s emphasis on targeting Android devices is unsurprising given the widespread use of Android technology in the Arabian Peninsula area (1, 2, 3, 4, 5, 6). Based on data from the Statcounter website, Android devices constituted over 95% of all active devices in Yemen from March 2022 to March 2023.
Location attribution
Regarding the Android samples associated with OilAlpha’s malicious activities,the earliest known sample, labeled as “WhatsApp.apk” was uploaded from Yemen starting from April 2021.
Other samples were uploaded from various countries in the Arabian Peninsula, as well as North America and Turkey. While this information might only indicate testing by the threat actors, such geolocation data can contribute to a thorough analysis, especially when it comes to determining attribution and understanding the victims involved.
What could be done to mitigate such attacks?
- Implement strong guidelines and conduct regular training sessions to raise awareness about social engineering and phishing attacks, aiming to detect and thwart such attempts.
- Utilize complex passwords and activate multi-factor authentication (MFA) whenever feasible to minimize the impact of credential theft.
- Social engineering operators often employ “cold-calling” techniques to interact with their targets, which involves contacting them directly through social media platforms or encrypted chats. Stay vigilant for indications of fraudulent or recycled content and make an effort to verify information directly from the original source, if possible.
In the end
It is crucial for organizations to implement robust security policies, including awareness exercises, strong passwords, multi-factor authentication, and vigilance against social engineering techniques. Additionally, comprehensive analysis and geolocation data can aid in understanding attribution and victimology.
By staying proactive and adopting these measures, organizations can enhance their defenses and mitigate the risks posed by such cyber threats.









