Researchers at FortiGuard Labs encounter a file name or email subject that grabs their attention. Recently, they came across a file that referred to a military research organization in India and a nuclear missile still in development.
This file was intended to distribute malware that shared characteristics with the APT (Advanced Persistent Threat) group called “SideCopy.” This particular group has been active since at least 2019 and has aligned its targeting with the objectives of the Pakistani government.
Going in details
The SideCopy APT group employs similar Tactics, Techniques, and Procedures (TTPs) and occasionally utilizes the same infrastructure as another threat actor group based in Pakistan, the “Transparent Tribe.”
Some reports suggest that it may be a subsidiary of the Transparent Tribe. “The name “SideCopy” is said to have been chosen because the infection chain they use was copied from the well-established Indian threat actor group SideWinder, likely as an attempt to make attribution more challenging. While SideCopy primarily focuses on Windows platforms, reports indicate that they have also deployed malware to compromise Mac and Linux machines,” researchers at FortiGuard.
Mode of operation
SideCopy’s utilization of DRDO-associated decoys for malware distribution was previously highlighted by Cyble and the Chinese cybersecurity company QiAnXin in March 2023 and once again by Team Cymru just recently.
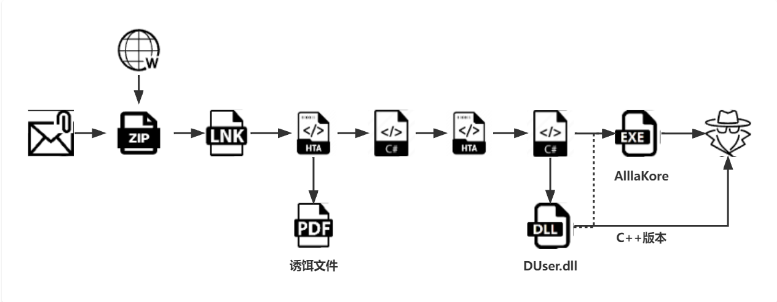
Courtesy: QiAnXin
Interestingly, identical attack sequences have been observed to load and execute Action RAT and a publicly available remote access trojan known as AllaKore RAT.
The most recent infection process documented by Fortinet is no different, leading to the
- deployment of an unspecified variant of RAT that can communicate with a remote server and initiate additional payloads.
This development indicates that SideCopy has persisted in conducting
- spear-phishing email attacks that employ social engineering tactics related to the Indian government and defense forces, aiming to deliver a wide range of malware.
Further examination of the Action RAT command-and-control (C2) infrastructure by Team Cymru has identified outbound connections originating from one of the C2 server IP addresses to another address, 66.219.22[.]252, which is geolocated in Pakistan.
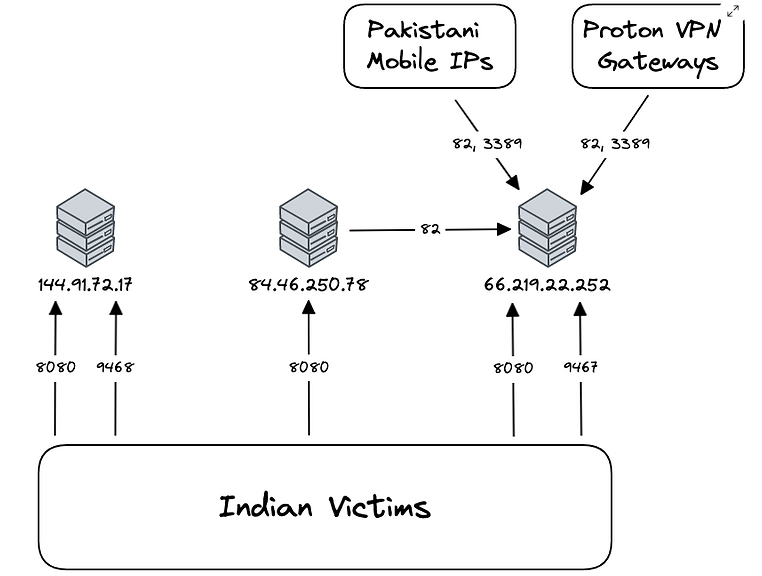
Source: Team Cymru
Final words
APT groups like SideCopy are committed to targeting governments and defense forces, but there is no exception that they can not target small organizations or individuals. Exercise caution is the best thing we can do while interacting with emails. Updating and maintaining a good security alignment is what’s required.









