Virtualisation technology leader VMware has issued critical security patches to address vulnerabilities in its Aria Operations for Networks product. The identified flaws pose a significant risk to businesses as they can be exploited for remote code execution attacks.
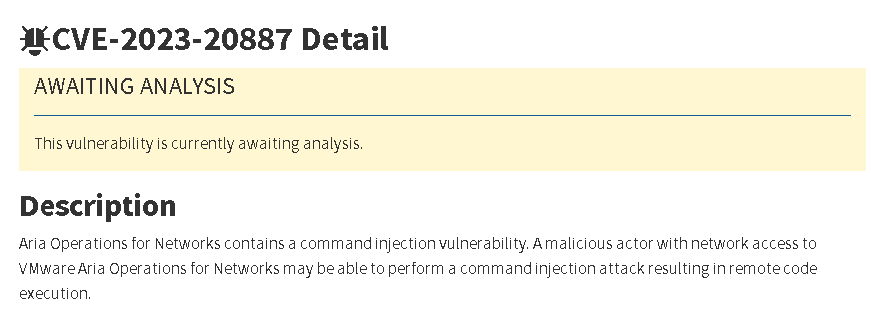
In its advisory, VMware highlighted three vulnerabilities of critical severity affecting the network and application monitoring tool. A command injection issue (CVE-2023-20887) with a CVSSv3 base score of 9.8/10 is of concern. This vulnerability enables a malicious actor with network access to VMware Aria Operations for Networks to carry out a command injection attack, leading to remote code execution.

Source: NIST
Let’s discuss this further
Previously known as vRealize Network Insight, VMware Aria Operations for Networks is utilized by enterprises to monitor, discover, and analyze networks and applications, thereby establishing a secure network infrastructure across various clouds.
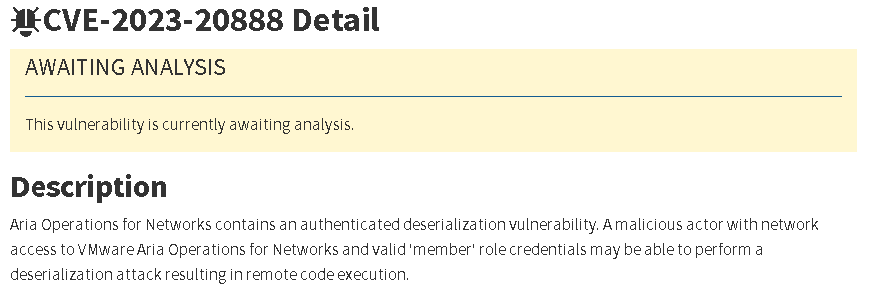
VMware also addressed an authenticated deserialization vulnerability (CVE-2023-20888), which permits a malicious actor with network access and valid ‘member’ role credentials to execute a deserialization attack, ultimately resulting in remote code execution. This particular bug has a CVSSv3 base score of 9.1/10.
Source: NIST
Furthermore, VMware patched an information disclosure flaw (CVE-2023-20889), enabling a malicious actor with network access to VMware Aria Operations for Networks to execute command injection attacks, exposing sensitive data.
Looking forward
It is crucial for organizations to promptly apply these patches to mitigate the risks associated with these vulnerabilities and ensure the security of their network infrastructure.









