Ever tried to remember whether your Spotify password was BlueP0p! or BluePop2023!? You’re not alone. Password fatigue is the constant burnout people feel from juggling dozens, sometimes hundreds, of logins. It starts as an annoyance and, left unchecked, leads to risky shortcuts: reusing passwords, picking predictable ones, or writing them down where others can find them.
For anyone who cares about privacy, money, or reputation, those shortcuts are mistakes with serious consequences. Find out what password fatigue is, why it’s a problem, and how you can avoid it.
What is Password Fatigue?
Password fatigue is the mental exhaustion and frustration people feel from having to create, remember, and manage dozens (or even hundreds) of passwords across accounts. Because it’s impossible to remember unique, strong passwords for every account, people often fall back on risky shortcuts like:
- Picking weak or predictable passwords
- Writing them down or saving them insecurely
- Reusing the same password across multiple sites
This behavior makes attackers’ jobs easier, fueling credential stuffing, phishing, and account takeover attacks. Password fatigue isn’t just annoying; it’s a real security risk that affects both individuals and organizations.
Why is Password Fatigue a Problem?
Large-scale analyses show billions of leaked credentials: one 2024–2025 study found 19 billion compromised passwords, with about 94% being reused or duplicates, highlighting how widespread reuse still is.
Observational telemetry shows that about 41% of successful human logins involve leaked credentials (Cloudflare), meaning attackers frequently exploit reused or previously leaked passwords.
Industry reports echo this: Verizon’s DBIR consistently flags credential compromise and password-based attacks among top initial access vectors.
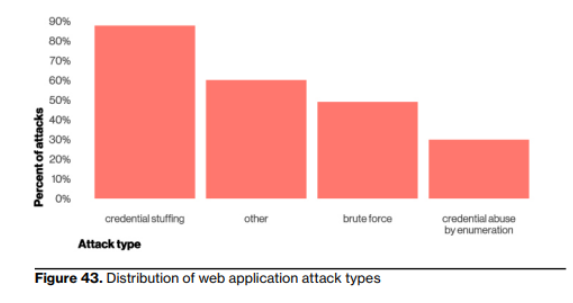
Adoption of password managers is growing but still limited: one recent report found that only 1 in 3 U.S. adults use a manager, leaving most people to rely on risky memory tricks or reuse.
The impact is clear: when attackers can buy or scrape billions of old credentials, reused passwords let them unlock multiple accounts with a single match, multiplying the damage.
Why People Fall into Password Fatigue
Password fatigue doesn’t just happen overnight—it builds up because of how we use the internet and how companies enforce security rules. Here’s why so many of us end up burned out by passwords:
1. Too Many Accounts to Manage
Between work apps, online shopping, streaming services, banking, and even smart devices, the average person juggles dozens of logins. Expecting anyone to remember long, unique passwords for all of them is unrealistic.
2. Frustrating Password Rules
We’ve all seen them: “must include an uppercase letter, a number, a symbol.” Instead of improving security, these rules often push people to create predictable patterns like abcdef! or slight variations of older passwords.
3. Painful Recovery Processes
Forgot your password? Get ready for endless verification emails, security questions you can’t remember, or waiting on IT support. Because recovery can be so slow, people stick to simple, reusable passwords just to avoid lockouts.
4. Belief That Some Accounts Don’t Matter
Many users think, “It’s just Netflix” or “Who cares about this random forum?” and use weak or repeated passwords. The problem is attackers love these accounts as the same password can often be reused to break into your email, bank accounts, or workplace systems.
The Security Risks of Password Fatigue
Password fatigue creates serious security vulnerabilities. When people reuse or simplify their logins, attackers get more opportunities to break in with minimal effort. The ripple effects can be costly for both individuals and organizations.
1. Credential Stuffing and Account Takeover (ATO)
Hackers love reused passwords. With billions of leaked credentials floating around, they simply reuse them across different services until one works. Because reuse is so common, one compromised account can snowball into multiple breaches. Reports like Verizon’s DBIR continue to rank credential compromise among the most common attack vectors.
2. Phishing & Brute Force Escalation
Passwords remain prime targets for phishing and brute force attempts. Microsoft reports thousands of password-based attacks per second globally, meaning any weak or recycled password is essentially an open invitation for cybercriminals.
3. Hidden Operational Costs
For organizations, password fatigue creates a hidden productivity drain. Constant resets and help-desk tickets consume valuable IT resources, while employees stuck in recovery loops fall back on recycled, easy-to-remember passwords just to get back to work.
5 Tested Solutions that Actually Reduce Password Fatigue
Password fatigue is universal, but it hits hardest when security matters most. Here are five proven ways to manage passwords without the hassle:
1) Move Toward Passkeys / Passwordless
Passkeys (FIDO-based) replace traditional logins with cryptographic credentials tied to your device. They eliminate phishing risks, block credential replay attacks, and remove the burden of remembering. Apple, Google, and Microsoft are rolling them out widely, and adoption is growing fast.
2) Use a Password Manager as the Baseline
PureVPN’s Password Manager generates long, unique passwords and stores them securely. This eliminates the need to memorize many credentials and slashes reuse. Despite the benefits, only about a third of adults currently use one, making it one of the simplest high-impact changes you can make.
3) Turn on Multi-Factor Authentication Everywhere
Enable MFA everywhere, and choose an authenticator app or hardware token instead of SMS where possible. Even if your password gets leaked, attackers won’t be able to get in without the second factor.
4) Prioritize and Clean Up Accounts
Start with high-value accounts (email, banking, cloud, primary socials) and protect them with unique passwords, passkeys, and MFA. Less critical accounts can be deprioritized, but never reuse passwords across tiers.
5) Use a VPN on Untrusted Networks
Public Wi-Fi is risky. A VPN encrypts your traffic, reducing the chance of session hijacking or credential theft. It’s not a substitute for strong passwords or MFA, but it’s an extra shield, especially for travelers and remote workers. Stick to a trusted provider like PureVPN as free VPNs often log or resell your traffic.
Wrap Up
Password fatigue is not just a user problem, it’s the predictable result of an internet built on too many logins and burdensome rules. The evidence is clear: credentials are still the top attack target, reuse makes breaches multiply, and billions of leaked passwords circulate online.
The way forward is simpler and safer: adopt passkeys, use a password manager, enable MFA, and protect your logins on the go with a VPN. That’s how you cut risk, save time, and finally escape the cycle of password fatigue.
Frequently Asked Questions
Yes. Password reuse is one of the biggest risks because attackers constantly exploit it. Massive leaked datasets show billions of reused credentials, and credential stuffing attacks succeed precisely because people recycle passwords across accounts.
A VPN encrypts your traffic on untrusted WiFi, preventing on-network sniffing and session hijacking. However, it won’t stop phishing or credential stuffing. Combine a VPN with passkeys/MFA and unique passwords for the best protection.
Frequent password rotation often increases fatigue and reuse. Rotate only when there’s evidence of compromise or when recommended by security teams. Using PureVPN’s Password Manager can also help manage your passwords effortlessly.