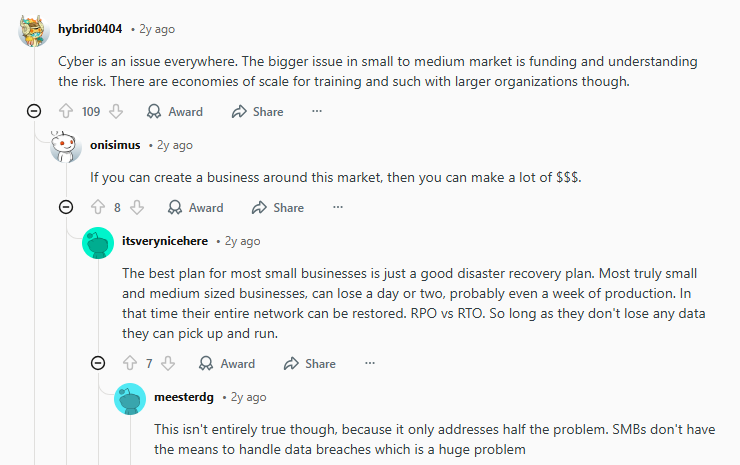
If you run or manage a small or medium-sized business (SMB), chances are you’ve seen this before:
A single admin password. Shared across IT, developers, and sometimes even vendors. Stored in a spreadsheet, Slack message, or someone’s memory.
It works, until it doesn’t. In 2026, shared admin passwords are one of the most common and dangerous security shortcuts SMBs take. While they feel convenient and cost-effective, they quietly introduce risks that can cripple operations, expose customer data, and even lead to regulatory fines.
Let’s break down why shared admin passwords are risky, what can go wrong without a password manager, and how SMBs can fix this without adding complexity.
How Convenience-Driven Access Weakens SMB Security
SMBs often operate under tight budgets, lean IT teams, and fast-moving workflows. Unlike large enterprises, they don’t always have dedicated security staff or complex identity systems. So shared admin passwords become the default because they’re:
- Easy to distribute
- Fast to us
- Simple to manage (at least on the surface)
But convenience comes at a cost, loss of visibility, accountability, and control. According to Verizon’s Data Breach Investigations Report, over 80% of breaches involve compromised credentials, and SMBs are disproportionately affected because attackers know their defenses are weaker.
What Are Shared Admin Passwords?
Shared admin passwords are credentials that multiple people use to access:
- Server dashboards
- Cloud infrastructure (AWS, Azure, Google Cloud)
- CMS platforms (WordPress, Shopify, Magento
- Firewalls, routers, and internal tools
- Password vaults or backup systems
Instead of individual accounts, everyone logs in using the same username and password.
Sounds harmless, but it breaks several core security principles.
Why Shared Admin Passwords Are So Risky for SMBs
When everyone uses the same admin password, you can’t tell who made what change, you can’t track who accessed sensitive systems, and you can’t audit suspicious activity accurately.
If something breaks, or worse, data is leaked, you’re left guessing. This lack of accountability makes incident response slower and more expensive, particularly for SMBs without in-house security teams.
1. One Leak, Total System Compromise
Shared passwords create a single point of failure. If the password is:
- Phished
- Accidentally shared
- Exposed in a breach
- Sent to a former employee
Attackers don’t just get one account; they get full administrative control. IBM’s Cost of a Data Breach Report consistently shows that breaches involving privileged credentials are among the most expensive and damaging. For SMBs, one compromised admin password can mean:
- Website defacement
- Ransomware
- Customer data theft
- Complete operational shutdown
2. Insider Threats (Accidental or Malicious)
Not every breach comes from hackers. Shared passwords make it impossible to protect against:
- Disgruntled employees
- Contractors who leave but retain access
- Accidental misconfigurations
When an employee exits, SMBs often forget to rotate shared admin passwords, leaving a permanent backdoor into critical systems. According to cybersecurity studies, insider-related incidents account for nearly one-third of security breaches, and shared credentials make them far harder to detect or prevent.
3. Password Reuse Amplifies the Damage
In many SMBs, the same admin password is reused across:
- Hosting
- Internal tools
- Analytics dashboards
This creates a domino effect. If one service is breached, attackers can credential-stuff their way into everything else. Without a password manager enforcing unique, strong passwords, SMBs unknowingly multiply their risk.
4. Compliance and Legal Nightmares
Even small businesses are now subject to data protection laws like:
- GDPR
- CCPA
- HIPAA
- PCI DSS
Most modern data protection regulations expect businesses to do three basic things:
- Control who can access sensitive systems
- Hold individual users accountable for their actions
- Maintain clear audit trails showing who accessed what and when
Shared admin passwords fail on all three counts. If regulators uncover shared credentials after a data breach, SMBs can quickly find themselves dealing with serious consequences, including heavy fines, legal action, and long-term damage to customer trust.
For many small and medium-sized businesses, that kind of fallout isn’t just disruptive, it can be enough to shut the business down entirely.
Why SMBs Avoid Fixing the Problem
If shared admin passwords are so risky, why do SMBs still use them?
- They Believe Password Managers Are Too Complicated
This used to be true. But modern password managers are:
- Cloud-based
- Easy to deploy
- Designed for non-technical teams
Most integrate directly with browsers, apps, and operating systems, often requiring less effort than managing spreadsheets or manual sharing.
- They Think: We’re Too Small to Be a Target
This is one of the most dangerous myths in cybersecurity. Attackers actively target SMBs because:
- They have weaker defenses
- They rely on shared credentials
- They’re less likely to detect breaches quickly
Automated attacks don’t care about company size. If your admin password is weak or reused, you’re fair game.
How a Password Manager Fixes Shared Admin Password Risks
Once SMBs recognize how risky shared admin passwords can be, the next question is obvious: what’s the safer alternative? This is where a password manager changes the game.
- Individual Access Without Friction
A business-grade password manager allows:
- Unique logins for every user
- Role-based access (admin, editor, viewer)
- No need to reveal the actual password
Employees can log in securely without ever seeing or copying credentials.
- Instant Revocation When Someone Leaves
Instead of changing passwords everywhere, you simply:
- Disable the user
- Revoke their access instantly
No downtime. No forgotten systems. No lingering access. This is a game-changer for SMBs with high staff or contractor turnover.
- Built-In Audit Trails
Password managers maintain detailed access logs that clearly show who accessed specific accounts, when the access occurred, and from which location. This level of visibility is critical for quickly investigating security incidents, meeting compliance and audit requirements, and strengthening internal security practices over time.
Instead of guessing or relying on assumptions, SMBs get clear, actionable insights into how their systems are actually being used.
- Strong Passwords, Automatically
Password managers generate and store long, random, and unique passwords. No more reused admin credentials. No more human memory failures.
Some even flag weak or compromised passwords, helping SMBs stay ahead of breaches instead of reacting after the damage is done.
A Smarter Way Forward for SMBs To Stay Secure
Modern password managers, particularly those designed with privacy and business use in mind, offer SMBs:
- Secure credential sharing
- Zero-knowledge encryption
- Centralized control
- Simple onboarding
When paired with secure connections and privacy-first tools, they become part of a broader security foundation that doesn’t overwhelm small teams. This is why many SMBs are now treating password managers not as nice-to-have, but as core infrastructure, similar to antivirus or backups.
Wrap Up
Shared admin passwords may feel like a shortcut, but for SMBs, they’re a liability waiting to explode. They remove accountability, increase breach impact, violate compliance standards, and make insider threats invisible.
But using a password manager restores control, visibility, and security, without adding operational headaches.
Frequently Asked Questions
The biggest risk is total system compromise. If the password is leaked or misused, attackers gain full administrative access with no accountability.
In modern security practices, no. Even temporary sharing should be replaced with secure, role-based access through a password manager.
Most business password managers cost far less than the average cost of a single security incident, which can run into tens or hundreds of thousands of dollars.
No, but it is quite the opposite. They reduce login friction, eliminate password resets, and remove the need for insecure sharing methods.
Reputable password managers use zero-knowledge encryption, meaning even the provider can’t access stored passwords. This makes them far safer than spreadsheets or emails.








