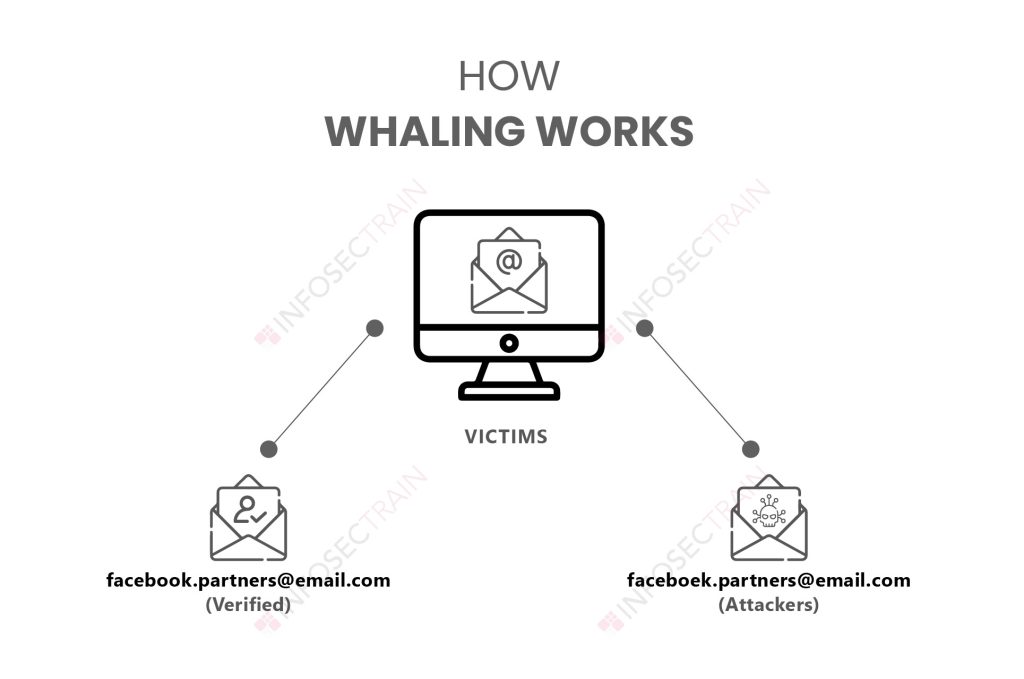
Whaling in cyber security is a form of targeted phishing that focuses on high-ranking executives such as CEOs, CFOs, and directors. Because these leaders hold authority and access to sensitive data, attackers view them as “big fish”hence the term whaling.
According to the FBI Internet Crime Report 2023, losses tied to business email compromise (BEC)—including whaling attacks exceeded $2.9 billion globally. At the same time, 64 percent of organizations say they’ve faced a CEO impersonation attempt in the past year.
In this article, you’ll learn what a whaling attack is, how it works, why it’s so effective, and the steps every business should take to stay protected.
What Is Whaling in Cyber Security?

Whaling is a targeted cyberattack in which criminals impersonate high-level executives such as CEOs, CFOs, or directors to steal money, access sensitive data, or authorize fraudulent transactions. Because these individuals are the “big fish” within an organization, this attack style is known as whaling.
Imagine receiving an email that appears to come directly from your company’s CEO, requesting you to urgently approve a wire transfer for an ongoing merger deal. Everything looks legitimate. This is exactly how a whaling attack convinces victims to act without question.
Unlike generic phishing that targets the masses, whaling attacks are strategically researched and highly personalized. Cybercriminals use real employee names, project details, and authentic-looking emails to trick victims into believing the message is legitimate.
Why Whaling Attacks Are So Dangerous
This section walks you through the psychological, technical, and social factors that make whaling in cyber security one of the most effective cybercrime tactics today.
Psychological Manipulation and Authority Bias
Unlike generic phishing, whaling attacks exploit human emotion. Cybercriminals craft emails that appear to come from a trusted leader often requesting urgent payments or confidential information. Because the message seems authoritative, employees act quickly without verification.
Example: “Please wire $250,000 to our new vendor immediately I’m boarding a flight and can’t take calls.”
Data-Driven Social Engineering
Attackers research targets through LinkedIn, press releases, and company bios to reference real projects and departments. This level of personalization makes a whaling attack nearly indistinguishable from a legitimate email.
Technical Deception and Email Spoofing
Cybercriminals use spoofed domains (e.g., ceo@compaany.com) and forged signatures to bypass trust. Proofpoint’s 2024 Threat Report found that BEC schemes now account for over 50 percent of corporate phishing-related losses many initiated through executive impersonation.
How Whaling Attacks Works
Now that you understand the psychology behind these scams, let’s break down the step-by-step lifecycle of a whaling attack.
This section explains how attackers research, execute, and conceal their operations helping you spot red flags before damage occurs.
1. Research & Targeting
Attackers begin by gathering intelligence on executives combing through LinkedIn profiles, press releases, SEC filings, and company websites.
As one cybersecurity professional on this Reddit thread noted:
“You’d be shocked how much open-source data an attacker can collect in an hour. Titles, email formats, even assistant names all public.”
— u/InfosecLurker, r/cybersecurity
These firsthand observations emphasize how publicly available information can be weaponized. What feels like harmless visibility for branding or networking can serve as a goldmine for attackers preparing a whaling campaign.
2. Impersonation Setup
Once the target is mapped, attackers move into the impersonation stage registering lookalike domains or compromising legitimate email accounts.
As a user explained in a BEC-focused Reddit discussion:
“We caught a spoofed email that copied our CEO’s footer and used her actual meeting signature line. That tiny detail fooled the first reviewer.”
— u/BlueTeam_Analyst, r/sysadmin
These kinds of peer reports highlight how attention to micro-details like signature blocks or tone can determine whether an attack succeeds or fails. It’s a reminder that verification should go beyond just the sender’s name.
3. Pretexting
In the next stage, attackers craft a convincing pretext a believable backstory that builds trust and urgency.
They might reference current business deals, use real names, or mimic internal workflows to add credibility.
Security professionals on Reddit’s r/phishing community frequently discuss how emotional manipulation and timing drive this phase. One member summarized it succinctly:
“Pretexting is the art of lying with just enough truth. The more real it sounds, the faster people comply.”
— u/Social_Engineer101, r/phishing
These discussions matter because they shed light on the human element of cyber defense showing that even trained professionals can be pressured into acting on a realistic, urgent request.
According to Proofpoint’s 2024 Threat Report, one in every three whaling emails uses language that conveys urgency, authority, or secrecy.
4. Execution
Once the groundwork is laid, the attack moves to execution. The fake “CEO” email might request an immediate transfer, payroll data, or system credentials all under the guise of a sensitive project.
Victims often comply, unaware of the deception until funds or data are gone.
In an Office365 sysadmin thread, one IT professional described a near-miss inside their organization:
“We got an email asking for gift cards for ‘client appreciation.’ It came from our CEO’s name, exact tone and all. If not for the finance team’s verification rule, we’d have lost thousands.”
— u/SOC_Watcher, r/Office365
These firsthand cases reinforce why procedural safeguards like mandatory double-approval for payments are so vital.
The FBI reports that the average BEC-related wire fraud in 2023 exceeded $125,000 per incident, many linked directly to whaling impersonations.
5. Exfiltration
After success, attackers move fast to cover their tracks. Funds are funneled through offshore banks, crypto wallets, or money-mule networks to obscure the trail.
When sensitive data is stolen, it’s often traded or sold on the dark web within 24 hours.
A discussion in r/cybersecurity captured the reality of this speed and complexity:
“We tracked one whaling payout through four crypto mixers the speed was unreal. These aren’t amateurs anymore.”
— u/ThreatIntelOps, r/cybersecurity
Hearing these accounts directly from practitioners helps readers understand that cybercriminals operate with precision and coordination, often faster than financial systems can react.
Real-World Whaling Attack Examples
Here are three true stories that illustrate the scale, tactics, and consequences of real-world whaling attacks even at Fortune 500 levels.
- Snapchat (2016): An HR employee released payroll data after receiving a spoofed email from the “CEO.”
- FACC Aerospace (Austria): A whaling email authorized a €42 million transfer; both CEO and CFO were dismissed.
- Mattel (2015): A fake CEO email triggered a $3 million wire to China recovered only after an international investigation.
These cases prove that even well-secured companies can fall victim when social engineering targets human trust.
How to Prevent Whaling in Cyber Security
Knowing how attacks happen is only half the story now it’s time to learn how to stop them.
This section guides you through practical, high-impact strategies to prevent executive-level scams, from authentication to training and policy enforcement.
1. Implement Multi-Factor Authentication (MFA)
Pair MFA with DMARC, DKIM, and SPF to stop email spoofing and unauthorized logins.
2. Conduct Executive Awareness Training
Executives should learn to question urgent financial requests and verify via a second channel (phone call or Slack message). Run simulated whaling exercises quarterly.
3. Enforce Financial Approval Policies
Require dual authorization for wire transfers or vendor updates. Separation of duties reduces risk.
4. Adopt AI-Based Email Security Tools
Solutions from Proofpoint, Mimecast, and Barracuda analyze behavioral patterns to detect executive impersonation emails before they reach inboxes.
Whaling vs Phishing vs Spear Phishing
| Attack Type | Target | Personalization | Example |
|---|---|---|---|
| Phishing | General users | Low | “Reset your password now!” |
| Spear Phishing | Specific employees | Medium | “Hi John, here’s the invoice we discussed.” |
| Whaling | Executives (CEO/CFO) | High | “Urgent wire transfer confidential project.” |
Final Words
Whaling in cyber security isn’t just another phishing variation it’s a high-stakes form of executive-level fraud that targets trust instead of technology. As attackers become more sophisticated, the best defense is a blend of technical controls, executive training, and strict verification policies.
Stay alert, verify every request, and protect your leaders because in cybersecurity, the biggest fish are always the most hunted.
Frequently Asked Questions
Organizations should deploy multi-factor authentication (MFA), enforce dual approval for payments, conduct executive awareness training, and use AI-driven email protection tools.
Immediately report the incident to your IT department, bank, and the FBI’s IC3 portal.
Change all affected passwords and review access logs for suspicious activity.
Executives have authority to approve transactions, access to sensitive information, and influence over teams making them high-value targets.
Attackers exploit authority bias and organizational trust to succeed.