Most people assume that once their VPN is on, their ISP can’t see anything (not even the VPN itself). However, that’s not how the internet works. While your ISP can’t read your encrypted traffic, it can often recognize patterns that belong to VPN use.
When that happens, some ISPs quietly block or throttle VPN connections. In this blog, we’ll break down how ISPs actually detect VPN usage, why these blocks happen, and how obfuscation helps your VPN activity blend in like ordinary HTTPS traffic.
Why Can ISPs Detect VPN Traffic?
A VPN hides what you’re doing online, but it doesn’t disguise the fact that you’re using a VPN. That’s because encryption protects the contents of your traffic, not the structure of the connection itself. ISPs can still see metadata like ports, packet sizes, and timing patterns, and every VPN protocol creates a distinct “traffic shape” when it connects.
WireGuard, OpenVPN, IKEv2, and other protocols all have unique handshakes and packet behaviors that stand out from normal HTTPS traffic. Even though the data is encrypted and unreadable, the pattern is still visible. This is what allows an ISP to recognize that a VPN tunnel is active without ever breaking the encryption inside it.
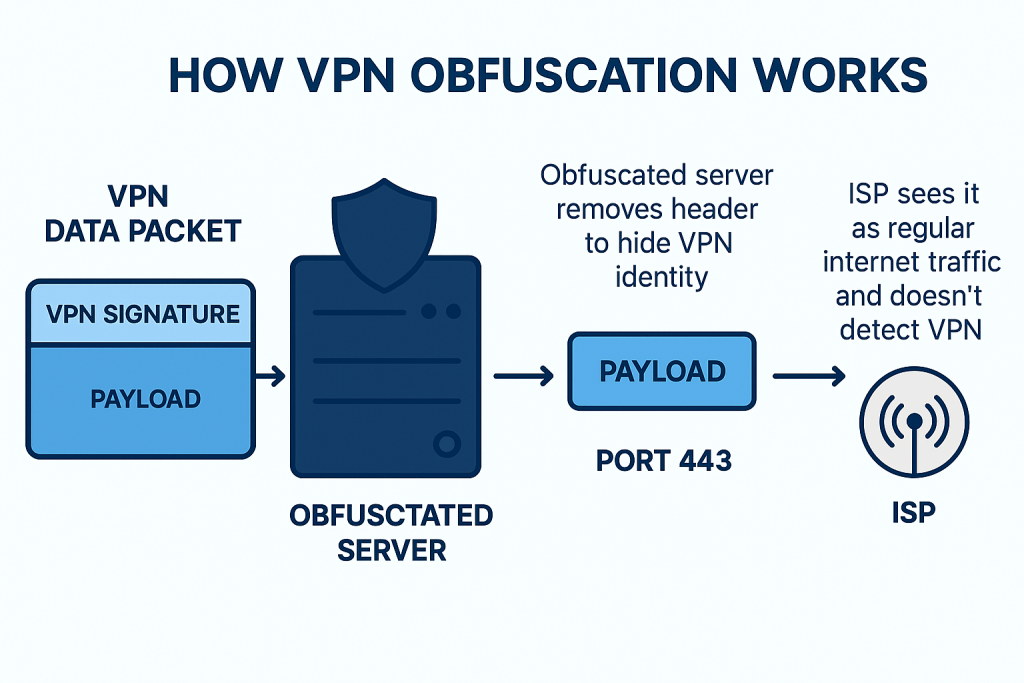
How to Use Obfuscation with PureVPN
Using obfuscation with PureVPN is simple. The app automatically applies it once you switch to the right protocol and connect to a server. Just follow these steps:
- Open the PureVPN app and sign in to your account.
- Go to Settings > VPN > Advanced > Connection Protocol and disable automatic protocol selection.
- OpenVPN appears as both TCP and UDP in the app. Choose UDP for better performance.
- Connect to a server using Quick Connect or by choosing a location manually.
Once you’re connected, obfuscation is applied automatically in the background. For added safety, enable the Kill Switch to prevent any traffic from leaking if your VPN connection unexpectedly drops.
Methods ISPs Use to Identify VPN Activity
ISPs don’t need to decrypt your traffic to tell that a VPN is running. Here are some of their most common detection methods:
Port-Based Detection
Many VPN protocols rely on well-known ports, which makes them easy to spot. WireGuard usually uses UDP 51820, OpenVPN often uses UDP/TCP 1194, and IKEv2 uses UDP ports 500 and 4500. When an ISP sees large amounts of encrypted traffic flowing through these ports, it can reliably assume it’s VPN traffic.
DPI Protocol Fingerprinting
Deep Packet Inspection (DPI) doesn’t break encryption, but analyzes how packets are structured. VPN protocols have signature handshakes, packet sizes, and timing intervals that differ from HTTPS. DPI tools can match these fingerprints and label the connection as a VPN, even though the actual data stays protected.
Traffic Shape and Entropy Analysis
VPN traffic is uniformly encrypted, producing high-entropy packets that look different from everyday web browsing. Normal HTTPS traffic varies more in size and timing, while VPN tunnels often generate consistent, tightly-packed encrypted packets. This traffic shape can reveal that a VPN tunnel is active.
IP and Server Reputation Checks
Some ISPs maintain lists of IP ranges known to belong to VPN providers. When your connection jumps from a residential IP to a data-center IP associated with VPN servers, the ISP may flag it as VPN usage. This method doesn’t require any packet inspection as it’s purely based on known server ranges.
Geographic and Routing Anomalies
When your connection suddenly shifts from a local residential IP to a data center IP in another region, it creates a clear routing change that isn’t typical for normal browsing. ISPs can see this jump in path and destination, and combined with encrypted traffic, it becomes another strong indicator that a VPN tunnel is active.
| Detection Method | What the ISP Looks For | Why it Works |
| Port-Based Detection | Traffic on known VPN ports (e.g., 51820, 1194, 500/4500) | Many VPN protocols use predictable, widely recognized default ports |
| DPI Protocol Fingerprinting | Handshake patterns, packet structure, timing signatures | VPN protocols have unique fingerprints that differ from normal HTTPS |
| Traffic Shape & Entropy Analysis | Uniform, high-entropy encrypted packets | VPN tunnels produce consistent packet sizes unlike regular web traffic |
| IP & Server Reputation Checks | Connections to IP ranges tied to VPN data centers | ISPs can match traffic to known VPN server networks without DPI |
| Geographic & Routing Anomalies | Sudden jumps from local IPs to distant server routes | Instant location changes reveal traffic is being relayed through a VPN |
Common Reasons ISPs Sometimes Block VPNs
ISPs don’t always interfere with VPN traffic, but when they do, it’s usually due to one of these reasons:
Abuse Prevention
VPN servers are frequently used for bot activity, scraping, spam, credential-stuffing, and other automated attacks. Since much of this traffic originates from data center IPs, some ISPs limit or slow connections that match known VPN patterns to reduce network abuse and protect their infrastructure.
Regulatory or Compliance Requirements
If you’re in a country that imposes censorship, telecom rules restrict or monitor encrypted tunnels that can bypass government filtering. ISPs may block specific VPN protocols or ports to comply with local laws, avoid penalties, or prevent customers from routing around content or censorship controls.
Network Management and Traffic Shaping
Heavily encrypted traffic is harder for ISPs to classify and prioritize. During congestion, some providers throttle or deprioritize high-entropy flows, including VPN tunnels. That’s because they can’t distinguish whether the traffic is streaming, gaming, or bulk downloads, making it harder to manage overall bandwidth.
Content and Licensing Restrictions
Some ISPs enforce regional agreements tied to streaming platforms, live broadcasts, or gaming networks. Blocking VPN traffic helps prevent users from bypassing location-based licensing rules, especially when it comes to markets where content providers require ISPs to limit cross-border access.
What Happens When Your ISP Blocks a VPN
When an ISP interferes with VPN traffic, the results rarely look like a clear “block.” Instead, the symptoms show up as connection failures, odd behavior, or sudden instability. Here are the most common signs:
- The VPN won’t connect: The initial handshake packet never reaches the VPN server because the ISP silently drops it. The client keeps retrying until it times out, making it seem like the server is offline even though the traffic is being stopped upstream.
- The VPN connects but nothing loads: Some ISPs allow the handshake but block or throttle the encrypted packets that follow. The app says “connected,” yet websites and apps fail to load because no data is actually passing through the tunnel.
- Certain VPN protocols stop working: An ISP might block WireGuard but leave IKEv2 untouched, or throttle OpenVPN over UDP while TCP still works. This selective filtering often confuses users into thinking the VPN is malfunctioning.
- Speeds drop only when the VPN is on: Instead of blocking the tunnel, some ISPs slow down high-entropy encrypted traffic during network congestion. Regular browsing feels normal, but VPN traffic becomes slow or unstable.
- Apps or login systems start failing: Dropped or delayed encrypted packets can break services that expect stable, uninterrupted connections. Banking apps, SaaS tools, and corporate logins may trigger repeated verification prompts or fail entirely.
How Does Obfuscation Hide Your VPN Usage?
Obfuscation makes your VPN traffic harder for ISPs to classify by removing the clues they rely on. It does that by:
Disguising VPN Handshakes
VPN protocols have highly identifiable handshakes. Obfuscation reshapes or wraps these handshakes so they no longer resemble any known VPN protocol. To an ISP’s filtering system, the initial connection appears to be a normal TLS request rather than a VPN tunnel forming.
Modifying Traffic Patterns
VPN traffic usually has consistent, tightly packed encrypted packets. Obfuscation introduces variation in packet size, timing, and structure, breaking the predictable traffic shape that DPI systems flag as VPN usage, so it behaves more like everyday browsing.
Using Standard Web Ports
Obfuscated servers often route traffic through port 443, the same port used by almost every secure website. Since ISPs can’t block or throttle 443 without breaking the internet for their customers, obfuscated VPN traffic passes through without triggering protocol-based filters.
Altering Metadata
Deep Packet Inspection analyzes how packets are framed and structured, not the encrypted payload. Obfuscation modifies this metadata so it no longer matches known VPN fingerprints, allowing the tunnel to pass as regular encrypted web traffic.
Final Word
ISPs can sometimes detect (and even block) VPN traffic, but that doesn’t mean you have to deal with failed connections or unstable speeds. Obfuscation removes the visible patterns that reveal a VPN and makes your traffic look like regular HTTPS, helping your connection stay smooth even on restrictive networks.








